Many Android utilities use Android Debug Bridge, or ADB for short, to send commands from a computer over to your phone or tablet. This enables such utilities to run terminal commands that, in some cases, wouldn't be possible on Android without root access.

If you missed out on Black Friday this year, you've got a second chance at saving some big bucks on apps, mobile devices, HDTVs, and other tech. See below for all of the hot Cyber Monday deals from Amazon, Apple, Google, Microsoft, and other online retailers. This list will be continuously updated throughout the day, so bookmark it to stay up to date on all the of Cyber Monday discounts.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

It's that time of year when high school students say goodbye the their past four years of coddling, ready to enter the "real world" and the next chapter of their lives—college.
It was the star of the show, but now that Android L has been released for preview to Nexus 5 and Nexus 7 owners, there's a lot that Google didn't tell us about their latest mobile operating system, rumored to be called Lollipop.

You can read at 500 words per minutes. Don't believe me? Here, see for yourself. This amazing technology comes from the startup Spritz, and they're ready to unleash it onto the smart device world, starting with the Samsung Galaxy S5 and the Galaxy Gear line of smartwatches.

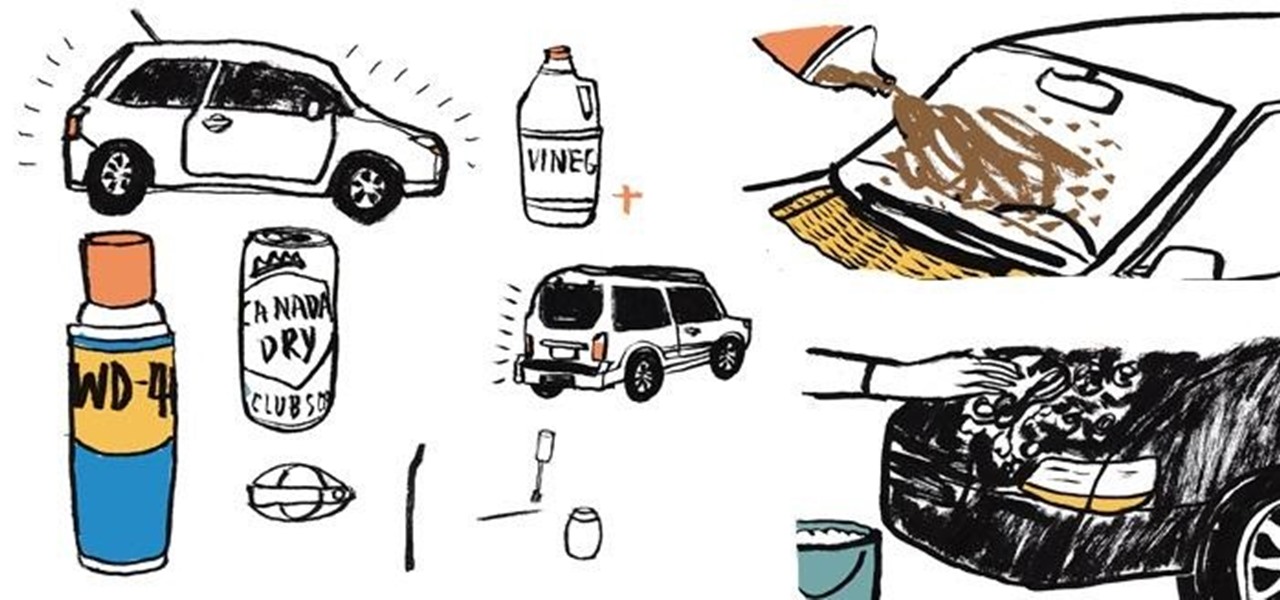
Ever see those cars so covered in dirt, dust, and grime that someone writes "Wash me" on it using their finger? Well, for those cars' sakes, as well as cases less extreme, a word of advice: procrastination is not a solution — it can only compound the problem. Self-cleaning cars are the stuff of the future, not the present, and your car needs attention now.

There is something special about a secret knock. It gets you into secret super villain meetings and is a surefire way to test for rotating bookcase passages. Secret knocks usually work with an intimidating drug lord and for policeman listening at the door for the correct pattern of raps.

In this video you will learn how to change out the hard drive to get even more storage capacity from your Sony Playstation 3. The PS3 takes any 2.5 serial ATA hard drive, which is your basic laptop computer hard drive. To switch this out begin by looking at the base of your PS3, here you will see a cover with the label "detach this cover to remove hard drive". Remove this cover with a flat head screwdriver to reveal the hard drive. You will see 3 screws on the hard drive, use a Philips head s...

Want to land an exciting new job, get that promotion, or simply become more productive in 2021? Project and quality management are invaluable, transferable skills that will improve your efficiency in almost any industry. Right now, "The Premium 2021 Project & Quality Management Certification Bundle" is on sale with an amazing 98% off the regular price of $4,400, for just $45.99.

PirateBox is a great way to communicate with others nearby when cellular and Wi-Fi networks aren't available. With it, you can anonymously share any kind of media or document and even talk to one another by voice — without being online. However, it needs a Raspberry Pi, which is more expensive than ESP32 boards, and if you only need a text-based chat, there's a much simpler option.

I think we all like the idea of getting paid games for free with minimal effort. Typically, though, anything claiming to help you do that is either illegal or a scam. But there are actually quite a few no-fuss methods that can get you paid games without going too far out of your way. From checking notifications to discovering hidden offers, you might have something waiting for you.

Your phone's keyboard is one of the most commonly used apps. Whether you're typing out status updates, sending private messages, or just bombarding everyone in sight with as many emoji as you possibly can, you probably couldn't get by without a good keyboard app.

With the growing list of products Apple offers, the number of devices connected to your Apple ID can get quite extensive. Having all those devices connected to your Apple ID helps you keep track of them, but when it comes time to part ways with an Apple TV or Apple Watch, those devices can still be attached to your Apple ID. In some cases, this could affect the overall security of your account.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

In a disturbing turn of events, Uber has been tracking oblivious iPhone users even after they removed the application from their phone. Two years ago, the situation escalated to such an extent that CEO Travis Kalanick earned a slap on the wrist from Apple mogul Tim Cook.

Google has a lesser-known Android app called Device Assist that might just be one of the most useful programs the company has ever published. It offers interactive guides and general tech support for Android, plus it can diagnose your device and help you fix any issues it finds.

Apple just showed off iOS 9 and its new features at WWDC 2015, including multitasking support for iPads (finally!), a new Low Power Mode to save battery, local area search and transit directions in Maps, a highly improved "Proactive" Siri, a better Spotlight search, new apps, and so much more.

Anyone who has rooted their Android device has likely used a tool called Android Debug Bridge, better known as ADB, at some point during the process. For most, that is their only interaction with the ADB, but to be a true Android power user, you need to really know the tools at your disposal.

Apple just unveiled iOS 8 at the Worldwide Developer's Conference, and it has a lot of exciting features to play around with. Unfortunately, it won't be available to the public until this coming fall—but that doesn't mean you can't get it right now.

PRL, or Preferred Roaming List, basically tells your phone which towers to connect to first. Changing PRLs can improve reception and data speeds, and in some cases even give you access to corporate/test towers.

If you've ever used your iPhone's hidden Field Test mode to view your signal strength in decibel-milliwatts, locate the tower you're connected to, or find out the radio frequency in use, you no longer have to dig through all of the confusing-looking data every time you need to check. Apple updated Field Test's interface in iOS 15, and one improvement gives you more control of the Dashboard.

Smartphones are vital travel companions. While you're on the go, they connect you with loved ones back home, help you find tickets and passes for tourist attractions, and make it easy to find your way through foreign roads — but even the most powerful smartphone could use help from travel accessories.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

The Pixel 3a came out of nowhere and flexed its muscles to show the industry that you can have a great phone without a hefty price tag. Since Pixel smartphones are first-party devices straight from Google, you can be sure you'll have root access one way or another. For right now the method used to get your Pixel 3a rooted will take a few steps, but they go by real quick.

So, you've lost your Apple TV remote. Maybe it's busted. What are you supposed to do now? You could go out and buy a new one, but they're expensive if you have a newer Apple TV with a Siri Remote, and wouldn't you rather spend that money on a movie? You might be without a working dedicated remote, but you likely have the next best thing already in your pocket.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

While there are over 100 cool features iOS 12 has to offer, there are some things Apple has made more annoying on iPhones or just has not addressed yet.

Apple released the third beta of iOS 12 for developers on Tuesday, July 3. The update comes exactly two weeks after the release of the second developer beta, which introduced a variety of fixes as well as new issues, and just one week after the release of the public beta. Public beta testers received this iOS 12 update on Thursday, July 5, labeled as public beta 2.

Apple released the iOS 11.2 update for the iPhone to the masses early morning on Dec. 2, and here are all the new features and important bug fixes you need to know about.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

Are you interested in video editing, but have no background in it? Are you looking to put together a short from some clips you've shot, but don't know where to start? You could use iMovie, an application that comes free with every iPhone, but then what would you do on Android? There must be a universal solution that works across both iOS and Android to let you work however and wherever you like.

As augmented reality becomes more and more integrated into the mainstream, people have been wondering the future of AR is going to look like. Jay Samit has a pretty clear idea.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

If you have a HoloLens, you can now control the lighting throughout your home or office via holographic controls using the free Hue Lights app in the Windows Store. The app, made by California-based AfterNow, works with the Philips Hue colored lighting system and is much more polished than the prototype we saw in January.

New releases of iOS are always pretty exciting. I remember the anticipation buildup of iOS 7 before it was announced at WWDC 2013, as it was expected to be a complete game changer compared to previous versions—and it was.

Hello fellow Nullbytiens, today we will be talking about IRC again (if you haven't read OTW's post about head over there now)and more specifically about using 1 nickname with multiple devices or IRC clients.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.