Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.
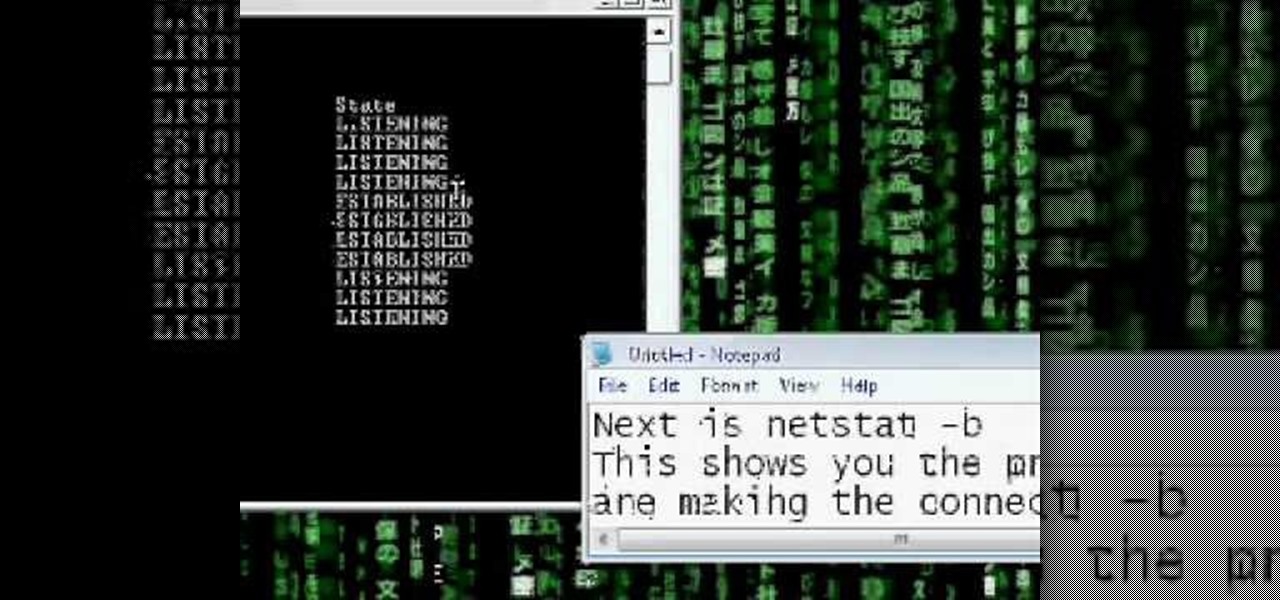
Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.
When people fire weapons in movies, there is often a shot of the shell-casings leaving the gun and flying through the air. Sometimes we get to follow them all the way to the ground, leaving us with a sense of loss at the firing of the weapon. This video will show you how to model and animate some shell casings falling to the ground and smoke trailing them in 3D Studio MAX and Photoshop, utilizing Reactor physics, particle flow, space warps, and all sorts of other fun 3DS MAX tools.

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my original script can download files, upload files, make changes to registry, create user accounts and more. I'm sure you could do it on your own too.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection between the attacker and the victim open to allow the attacker to continuously manipulate the victim's browser. XSS Shell works by setting up an XSS Channel, an AJAX application embedded into the victim's browser, that can ob...

Want to see whether your PC is being accessed by hackers? Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

Enabling SSH On Your Mac Server How To Use Your Mac As A Server.

In this how-to video, you will learn how to shuck an oyster using the hinge method. First, you must have cleaned oysters, oyster knife, a small towel, and a glove. The oyster has a flat top shell and a bottom shell. The hinge is where you will be inserting the knife. Place the oyster top side down on a flat surface. Insert the tip of the knife into the small hinge opening. Use force to push it in. Clean the knife and then pry it open. Slide the knife across the top shell towards the abductor ...

Lets create a blanket from scratch using only the wavy shell stitch. This crochet how-to video is an example of how to crochet a blanket out of the wavy shell stitch only using three colors. Go as large as you need to and as big as you want with the crocheted blanket. The colors and size is up to you so get creative and start crocheting.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Detailed demonstration of Shell design which can be used as edging or part of a crochet pattern. The second video shows you how the second row of a shell stitch looks.

This video illustrate us how to properly shuck an oyster. Here are the following steps. Step 1: first of all take oysters and oyster sucking knife.

This video shows how to make Cascos de Guayaba con Queso Crema (guava shells with cream cheese). Ingredients: 1 15 oz. can of Guava Shells, and 1 15 oz. package of low-fat cream cheese. To make Cascos de Guayaba con Queso Crema (guava shells with cream cheese): Drain Guava Shells. Remove Guava Shells from syrup and put it into plate. Add 1 teaspoon cream cheese into each Guava Shell. Lightly drizzle syrup over top of Guava shell with cream cheese.

In this video, we learn how to paint your favorite sports team logo on a racing shell. First, you will take your shell and trace out the logo on it with a Sharpie marker of your choice. Use tape to cover the areas that you don't want marked, so the lines come out cleaner and straighter. After you have done this, paint the logo onto the racing shell with small brushes and your choice of paints. Leave the tape in place until all of the paint has dried. Then, remove the tape from the shell and y...

This video shows you how to shuck an oyster using an oyster knife. First, wear a metal mesh glove, used for protection, in case you slip-in and cut yourself, on your left hand. Then take the oyster shell on your left hand and pick the knife on your right hand. Then point the knife tip towards the shell, dig it and jiggle it in between the shell, and then grab the oyster from the wedge and twist the knife till the upper and lower parts of the shell are separated from each other. Once the two p...

In this crochet tutorial, learn ho to make a shell with a 3 double corchet. For this pattern stitch, the shell will consist of 3 double crochet, meaning that it takes 3 chains to make 1 shell of the pattern stitch.

Spring time means soft shell crabs. In this cooking how to video tutorial Mark Bittman, from the New York Times, demonstrates how to cook pasta with soft-shell crabs. Watch and prepare yourself for a delicious pasta and soft shell crab recipe brought to you by the dining section of the New York Times.

Watch this video to learn how to install and use iR Shell. iR Shell is a mod for the Sony PSP. The link for downloading is http://www.psp-hacks.com/file/1292

Planning on starting a Taco Tuesday tradition with your family? Then don't try to weasle your way out of keeping the meal healthy by purchasing premade taco shells. Usually these taco shells are made from refined, overprocessed flour that has very little nutritional value.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

Peeling never got anybody anywhere when it comes to hard-boiled eggs. The little chunks of shells always stick to the white surface of the egg, and they're really hard to get off without rinsing in water. But, there's a ninja trick that mixed martial artist Miguel Torres has for you, and it's peeling without really peeling. You knock off the shell at the top and bottom of the egg, that's all the "peeling" you'll be doing. Then you grasp the hard-boiled egg in one hand, put your lips to the to...

Were hermit crabs named after hermits or hermits named after hermit crabs? Either way, we know that hermit crabs are major homebodies. Like, to the point that they almost NEVER leave their homes to come out unless they're visiting another shell...their future shell, that is, when they get too big to fit their former shell.

Don't have the extra cash to spend on a shell case to protect your iPod? In his ongoing duct tape tutorial adventures, DuctTapeStuff reveals a cheap way to make a shell case for your iPod out of duct tape and a few minutes of your time.

In this video, we learn how to draw a cartoon turtle. Start by drawing a circle with two large circles inside of it for eyes and a head. Next, draw a long neck for the turtle leading into a small shell. Make the bottom of the shell flat and a small tail sticking out of the back. Next, draw four feet coming from the bottom, then shade the back feet. Draw scales onto the shell, then draw a cute smile onto the turtle. Next, draw toes onto the feet and you will be done with your cute turtle. you ...

In this video, Bill Dewey will show you the best way to shuck an oyster. You should have a knife and a glove so you will not cut yourself. Place the oyster on your glove hand. Keep the pointed side towards you. Take the knife and place it into the hinge. Twist the knife until you hear the hinge pop. Keep the knife against the top shell and scrape against the top towards the muscle. Now, open it up and cut the oyster from the bottom shell. Keep the liquor from moving off the shell. Now the oys...

In this video tutorial, viewers learn how to peel and devein a shrimp. Users will need a deveining tool. Insert the tool along the shrimp's backside away from the legs and push it towards the tail. The tool will remove both the shell and vein in one motion. If users don't have this tool, they can use a small knife or fork. Now run cold water over the shrimp meat to remove all traces of the shell and vein. This video will benefit those viewers who enjoy cooking and would like to learn how to r...

This video demonstrates how to shell, devein, and butterfly shrimp. For this, you will need a paring knife or a pair of kitchen shears and large shrimp.

Turn your kitchen into a science lab with this egg-tastic science experiment, which turns a shelled raw egg into a bouncing translucent ball. It's one of the simplest tricks of all time, and all you need is a raw shelled egg and some vinegar.

This video is a quick tutorial on how to custom paint an XBox shell to make yours stand out from the crowd.

There's no better way to improve your ability to ice masterpieces of cupcakes and cakes than to simply practice. And the tip presented in this cake decorating video is indispensible. Using a #21 tip (called an open star tip), you'll learn how to ice a shell border.

In this tutorial, we learn how to make a simple shell necklace with your kids. To make this, you will need: a sea shell, a hot glue gun, and a necklace string. First, tie your string into a knot at the end of it. Next, grab your shell and apply glue with the hot glue gun to the inside base of it. Now, press the knot that you just made onto the glue in the shell. Let this set up until the glue is completely dried, and you're finished! You can apply more glue to the top if you want a more secur...

You might think cooking guava shells is a complicated task, but this video from Cooking For Bimbos will prove you wrong. You will be taken through the process step-by-step, starting with pre-heating the oven and taking the shells out of their can. Along the way, you will hear tips for how to make the shells tastier, what to pair them with, and more. So what are you waiting for? Watch this simple tutorial and you'll be on your way to preparing a delicious guava shell based meal in no time.

Clam Shell end tips, or knot covers, are normally used when you are stringing pearls or other beads on silk or nylon thread. They cover the knots on the ends of the thread so they can't be seen.

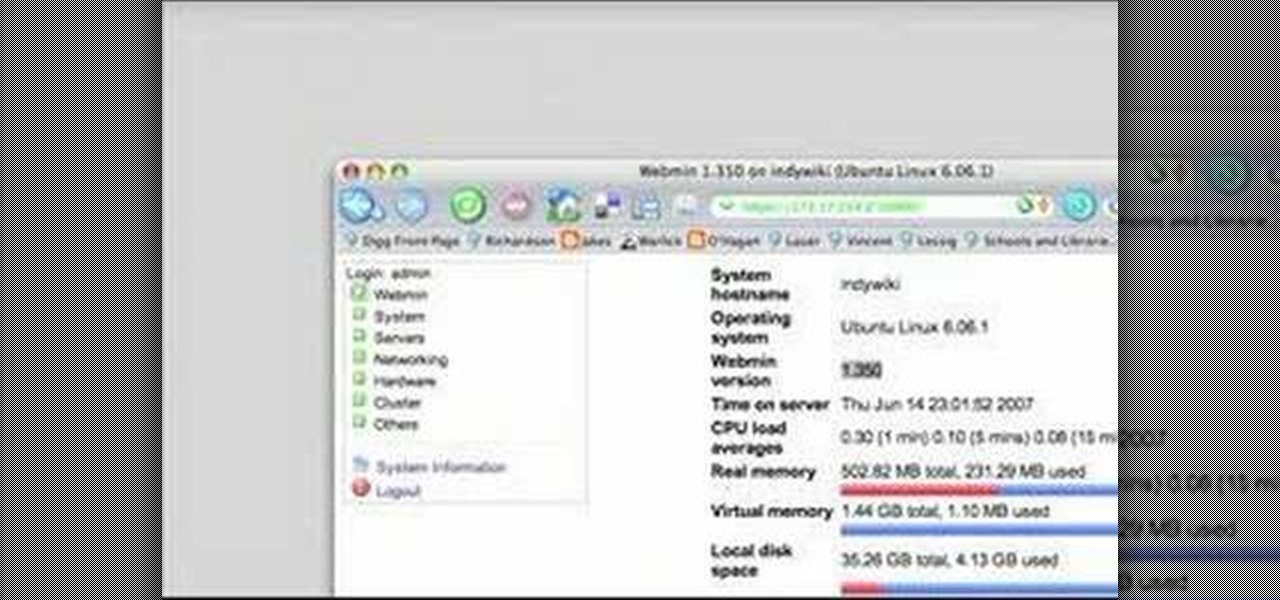
In this video you'll learn how to log in to Webmin, a web-based Unix administration interface, which will allow you to manage your serve with a web browser. Watch this video tutorial to learn how to control your server with a web browser and the Webmin interface.

In this video you'll learn how to download Webmin, a web-based Unix administration interface, which will allow you to manage your serve with a web browser. If you're interested in running the Webmin interface, then watch and follow along.