After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

It's been little over a month since the official release of LG's latest flagship phone, the LG V20. Despite a few minor hiccups, the V20 has been attracting attention from all over for being an amazing phone. But like with most Android phones, there's no better feeling than rooting and taking complete ownership of it.

How do you safely store your augmented, virtual, or mixed reality headset when you're not using it? Cybust hopes you're willing to shell out $89 to display it like a sculpture around your house.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

There are few kitchen tools as elusive as the oyster knife. Many people—even seafood lovers—don't own one. If you do own one, it probably gets used so infrequently that it gets sent to the very back of the shelf where it proceeds to get lost. Then you accidentally find the knife once a month when you don't need it, but can't for the life of you find the sneaky little thing when you do need it.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

When I first received my HTC One M8, I was in love with the 5-inch screen size, but the icons and font just seemed too big, wasting valuable screen real estate. Phablets, like the Samsung Galaxy Note 4, have only slightly larger screens, but don't seem to have this problem since manufacturers lowered the device's DPI, or dots per inch.

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by developing your scripting skills.

Eggs are one of the most versatile foods imaginable. They can be cooked in tons of different ways, eaten for breakfast, lunch, or dinner, and go with just about anything. Most of us have hard-boiled and scrambled eggs before, but have you ever thought about combining the two? That looks pretty good, doesn't it? But it's not exactly the kind of scrambled and hard-boiled eggs combo I'm referring to. And thankfully, this isn't what I'm talking about either... No, even though balut may look like ...

In this sports how-to video, Farmington HS boys basketball coach Shane Wyandt and team demonstrate the shell four defense drill. The shell four drill is an effective way of training for basketball. Follow along with this video demonstration and improve your game with this drill.

If you've ever seen something called ThinkPoint Antivirus on your computer, you have gotten one ofhte most widespread and infectious fake antivirus malware programs out there. To get it off your PC, follow the instructions below, or watch this video for an alternate method if this one doesn't work.

If you're a God of Mount Olympis, you may want to leave town, because Kratos is still angry in God of War 3 for the PS3. Killing Gods and defiling women are just a couple of his his hobbies. The other is treasure hunting. And in this IGN Strategize video, you'll find the locations of all ten Godly Possessions in God of War III. The Godly Possessions are more than just conversation pieces. Each has a special power you'll be able to use after beating the game once. You'll also get a gold trophy...

Yes, the Droid X from Motorola can be rooted, and yes, you can do it at home. Just make sure you follow the directions precisely. If you succeed, you'll have a completely rooted smartphone. eFuse doesn't matter. If you want to expand your options on Verizon Wireless's Droid X, then you just have to take a chance… use this video in conjunction with the links and description below.

If you're a serious diver, especially anywhere cold, then your dry suit is probably a near and dear friend. If something goes wrong with it, you may think that you need to pay someone a lot of money to fix you baby. But no! They're actually pretty easy to fix yourself. This video will show you how to fix the neck seal on an OS Systems drysuit yourself with just some spare parts that you can order from the manufacturer.

Cloth is an essential part of almost any 3D modeling project involving people. This video will show you how to properly use the cloth modifier in 3D Studio MAX to create the waving, tarnished American flag shown in the thumbnail. This tutorial does NOT feature Reactor, the in-program physics engine included with 3DS MAX, only the actual 3D Studio MAX cloth modifier.

In this video, we learn how to make shrimp fried rice. You will need leftover rice, shrimp, ham, onion, cilantro, red pepper, celery, garlic, green onion and frozen peas. First, take the shells off the shrimp and de-vein them. Then, chop up your vegetables and ham. Now, add water to your left over rice until it starts breaking up. Grab a walk and put it over high heat and add canola oil to the bottom. Add in your onions, peas, celery, garlic and red pepper and shallots in the wok and cook unt...

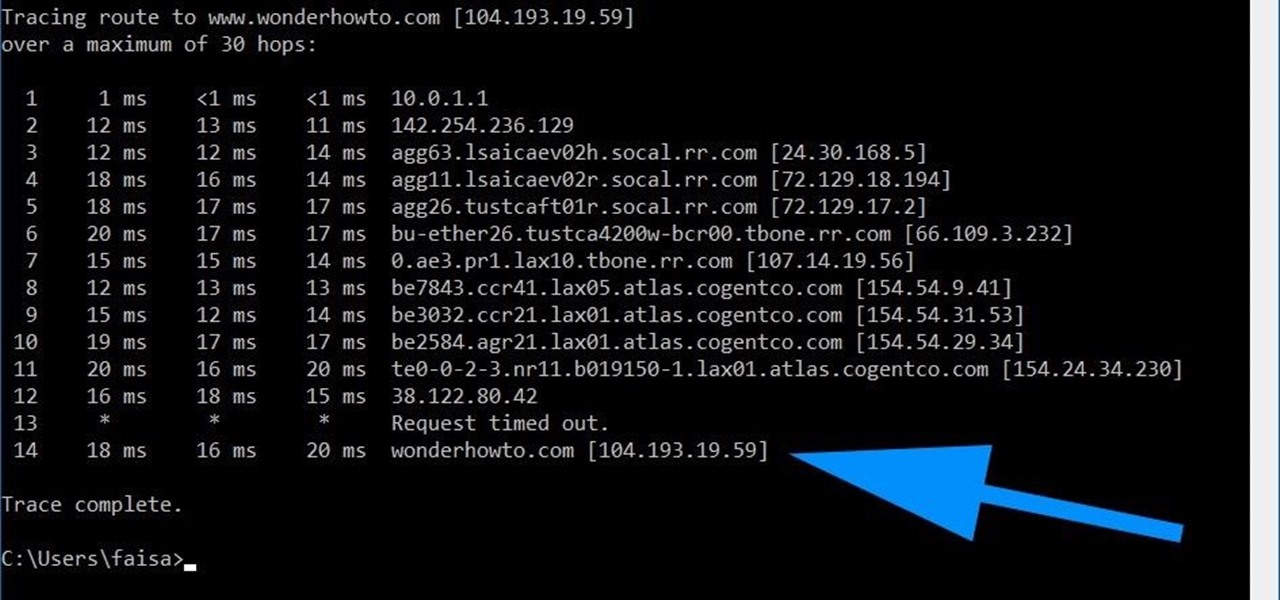
Using a simple trace trick, you can easily look up the IP address and its location for any website. This method uses a command line command to first find the IP address of a given website, and then uses a free online tool to get that IP's location.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

This vid is on how to paint an radio controlled shell and how to do some basic effects. Use the liquid masking method of Bob Dively and see how to use airbrushes, such as Iwata. You can use this method with any paint from Pactra to Spaz Stix, and any color of black, blue, purple, green, yellow, silver, chrome, etc.

Here's another demonstration on how to combine harmony and melody into a self-contained solo piece. This time you'll be playing "Pearly shells" on the ukulele.

Watch this video to learn some of the fundamentals of crocheting. It will show you how to crochet the shell stitch. Create beautiful objects with this popular stitch.

Check out this video from Berkleemusic.com and watch as Berklee professor Paul Schmeling explains how to master the toughest jazz standard with ease and improve your left hand technique by utilizing shell voicings to represent chords in the left hand.

Ian Ozsvald shows how the powerful, interactive python shell IPython can be combined with the Python debugger to provide a powerful debugging environment.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

When it comes to hacking guides, most are written from the perspective of a Linux user. There are a few outliers, but it's mainly Linux, which leads to the idea that Linux is the only OS that's viable for hacking. This couldn't be further from the truth. A properly set up Apple machine can do quite a bit of heavy lifting.

When we tell folks how often we use apple cider vinegar, they are baffled and bewildered. "I've had a bottle sitting in my pantry for 10 years," is the response we encounter most. And "I never use it!" Some have never even used apple cider vinegar at all in their lifetime, believe it or not.

Let's set the scene: you're at home, it's late in the evening, and you have a hankering for those deliciously decadent chocolate-wrapped squares of ice cream goodness. You could drive to the store and pick up the usual pack of Klondike Bars in the ice cream aisle... or, you can easily make these babies in the comfort of your own home with only three ingredients for a fraction of the cost—in any flavor you want! The choice is obvious. So, without further ado... Ready, set, Klondike!

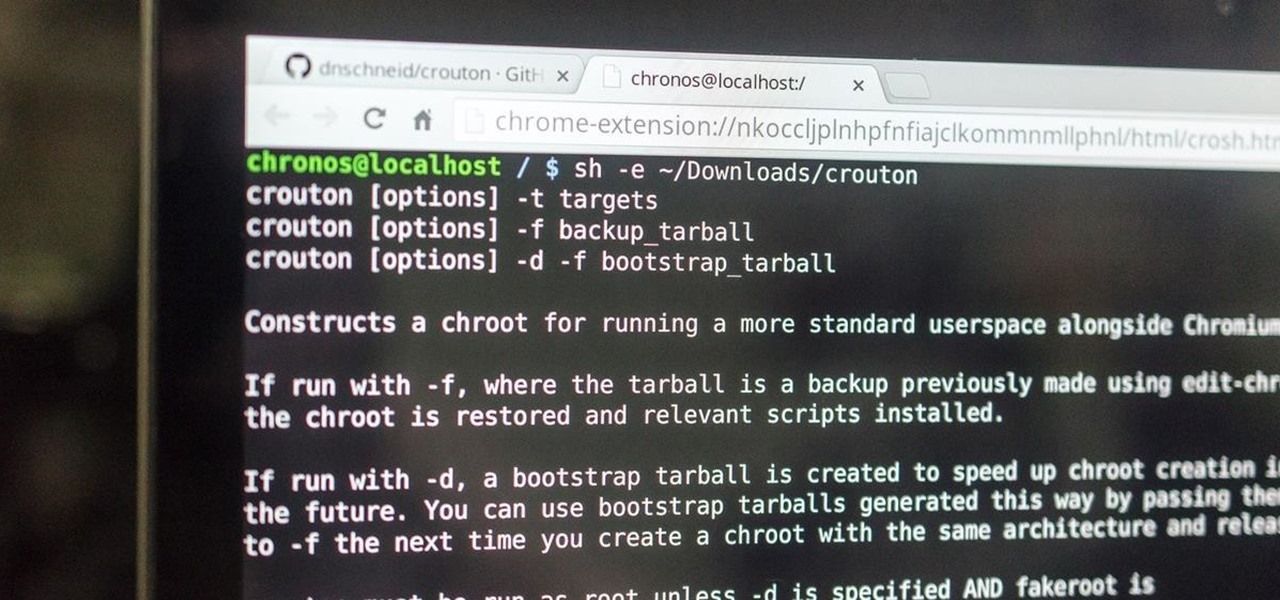
This is my first how-to for this site so feel free to let me know if I can somehow improve! Inspired by the great Jailbroken iDevice and Rooted Android PenTesting tutorials I decided to share how I use my Toshiba Chromebook 2 with Kali Sana.

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

Learn how to make decorative seasonal napkin holders for all four seasons in this free video series on entertaining and dinner crafts.