The long-awaited Apple Watch is ready for retail, with pricing and availability announced at Apple's Spring Forward event. Each of the three variants—Apple Watch Sport, Apple Watch, and Apple Watch Edition—will be available in two sizes, 32mm and 44mm, with preorders beginning on April 10th and the retail launch on April 24th. The Watches will initially be available nine countries: Australia, Canada, China, France, Germany, Hong Kong, Japan, the United Kingdom, and the United States. You'll b...

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

In recent years, Hollywood has taken a shine to hackers, with hackers appearing in almost every heist or mystery movie now. This can be both good and bad for our profession. As we know, whichever way Hollywood decides to depict our profession is how most people will perceive it.

Bottled water is a rip-off. Not only is it pretty much the same stuff that comes out of your tap for free, but plastic bottles are rarely recycled and thus account for a huge amount of the waste that's overflowing our landfills. Next Up: Water Bottles You Can Eat

A lot of people rely on the date on the packaging to tell them when food has gone bad, even with eggs, but the sell-by dates are often somewhat arbitrary and are not expiration dates. If you've been tossing your eggs based on the dates on your carton—you could be wasting perfectly good food.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

Welcome back, my rookie hackers! A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

Have you ever had scrambled eggs covered in chocolate syrup? If you have—you need some help. Seriously. If you haven't, it's probably because it sounds absolutely repulsive. I know there's the whole salty and sweet thing, but that can only go so far.

Clam chowder is a flavorful soup that is a great starting course or a whole meal in itself. You can make make a pot of this wonderful seafood dish at in the comfort of your own home and have enough to use for several meals.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

In recent days, I've twice talked about brining the Magic Leap One out into the world with me to test its mobile capabilities. But you may have been wondering how I carried the device with me. Did I just stuff my brand new $2,300, hard to obtain device in a backpack and hit the road? Hardly.

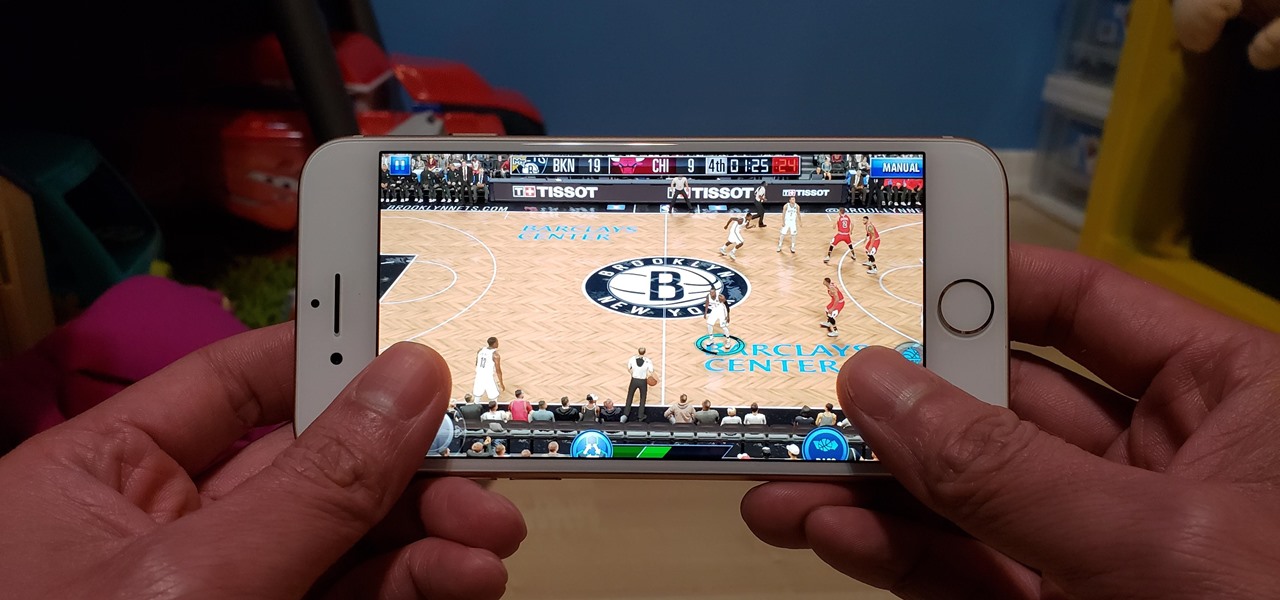
NBA 2K18 has been out for the iPhone for months, but its $7.99 price tag put it out of reach for many mobile gamers. There's light at the end of the tunnel now, as a free-to-play version is in the works as a soft-launch in New Zealand. If you can't bear the wait, you can play the free NBA 2K Mobile right now in any country.

On Friday, game developer PreviewLabs released the first online multiplayer game for the Microsoft HoloLens.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

Pennies may only be worth $0.01, but if you want a coin with everyone's favorite donut-eating dad on it, you're going to need to shell out a little bit more.

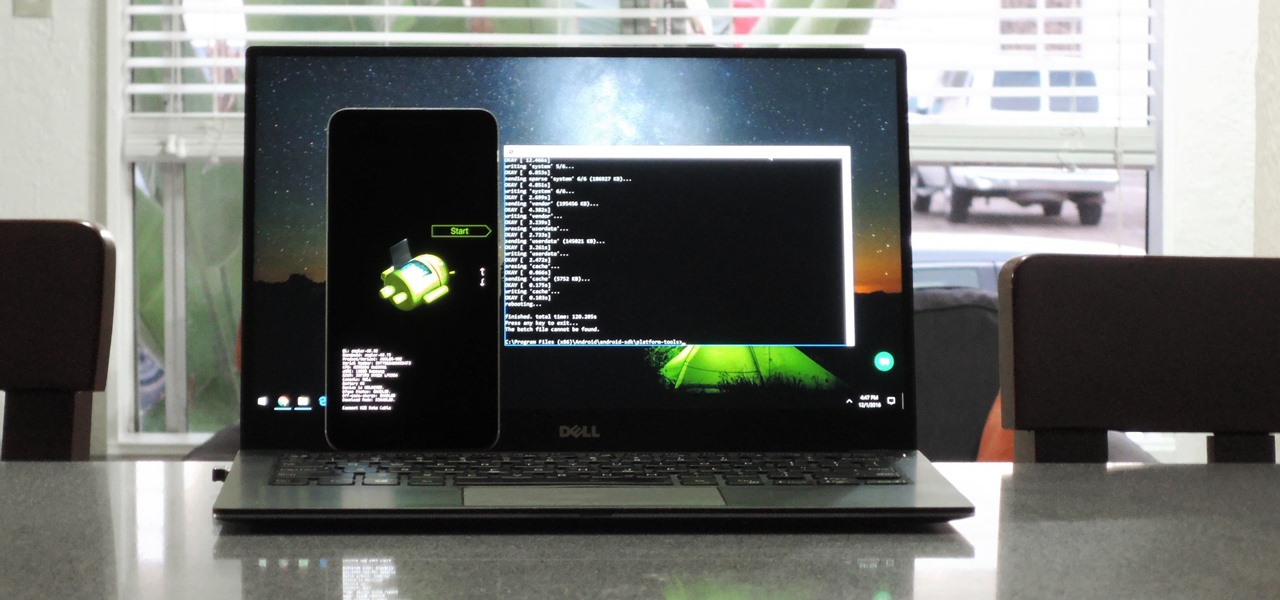
If your phone has an unlocked bootloader, you can use Fastboot commands to flash factory images. That may sound like a bunch of technical jargon, but when it comes down to it, this is the best method for updating a rooted device, fixing a bricked phone, reverting to stock, or even getting new Android updates before everyone else.

Windows Insiders running Build 14971 of Windows 10 in the Fast Ring can now look for the "Windows Holographic First Run" app to check to see if their PCs are up to the task of running Windows Holographic. It won't detect your VR headset yet, but at least you'll be able to see if your computer will be compatible.

YouTube won't let you play videos in the background on Android without paying for YouTube Red, so if it's your primary source for streaming music, and you don't want to shell out $9.99/month, you'll just have to take matters into your own hands. The simplest solution to this problem would be to download MP3s straight from YouTube for offline playback, but in the past, this hasn't exactly been easy on a mobile device.

Even for an avid egg enthusiast, a popular dish like scrambled eggs can get tiresome if it's on repeat in your breakfast rotation. For an unusual way to add some oomph to your œufs, consider adding a squeeze of lemon to your scramble. Read on to understand why this seemingly odd suggestion will boost your eggs' flavor.

Several Samsung phones have a feature that turns the screen black and white when the battery is getting low. This takes advantage of the AMOLED display in these devices, because unlike red, green, and blue pixels, no battery power is used to display black pixels on this type of screen.

Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

I have gotten comments from my last tutorial on not being able to do anything because of a lack of a monitor. In order to address this problem I'm gonna show you how to connect and control the Rasberry Pi through a SSH client on Linux, Mac, Windows, and Chromebook computers. This will probably we a long tutorial so please bear with me. Anyway, lets get to work.

OK, In my last Tutorial we made a Server for sending Instructions to a Client. This time we will build the Client. Fire up your favourite Python environment and get the Code here.

Surprise desserts (aka peekaboo desserts) are a gorgeous way to celebrate anything, whether it's a birthday, new baby, or just a brand new day. You can pretty much hide anything you want inside: candy, a cool design, and even other desserts. To help inspire you, try one of these fun-filled desserts out for a special, photo-worthy occasion. Then get creative and try out your own ideas (and make sure to share them with us when you're done).

Though you can use the Social Engineering Toolkit to clone websites, this way is much more customisable.

Summertime calls out for desserts that are easy to assemble and don't require heat. Voilà: crème de menthe grasshopper pies. They are minty, fresh, and cold, and are very easy to whip together with marshmallows and a microwave.

Google's Chrome browser is evolving into a very powerful platform. Not only can it be used to view your favorite website or mirror tabs to your Chromecast, but now that it has an App Engine, more powerful tools can be run within Chrome.

3D printing is getting closer and closer to becoming an everyday reality—which means revolutionary things are going to start happening for the home cook. Already there's a 3D printer that can produce edible tailored fruit and the Foodini, which can print full meals, including spaghetti and burgers. However, neither are available for purchase, and most likely won't be within reach of the average cook for years.

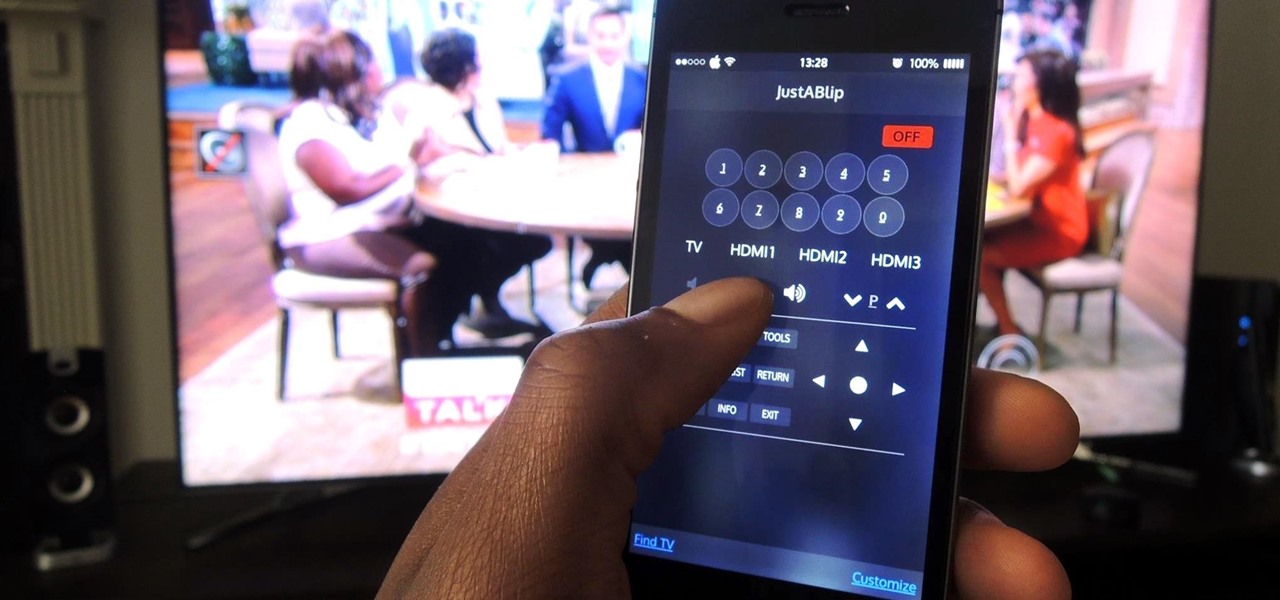
After I traded in my Samsung Galaxy S5 for an iPhone 5S, the one feature I truly missed was the Smart Remote app. My television remote was broken and the S5 saved me from, you know, actually having to get up and change the channel.

Apple Pay has been available to use in stores, as well as in select apps and websites, ever since its first appearance in iOS 8.1. Now, with iOS 12, there are currently 13 different iPhone models that support Apple Pay functionality without the use of an Apple Watch, and the list of partnered stores that accept Apple Pay has only grown. Here's our always-up-to-date list to keep you in the know.

I love cheap, nutritious food: lentils, rice, toor dal, and other beans and grains. Even popcorn. The only problem is that they usually come in floppy plastic bags that make measuring ingredients more difficult. I usually open up one corner of the bag only to have everything come spilling out all at once whenever I try to pour out measured amounts.

There are plenty of times when we need to charge our phones but don't have access to electricity. Whether the power is out do to storms, you're camping and run out of juice, or you're in a Tom-Hanks-like Castaway situation, it's important to have a charged phone in case of an emergency.

Hello everyone, this how-to is for all the people who love to make videos, but don't necessarily have the cash or willpower to shell out on an expensive mic., or simply are looking for an easier option.

The in-fighting between the major US carriers just got a little more interesting. In July of last year, T-Mobile introduced their JUMP! plan, letting customers upgrade their devices after just six months, up to twice a year. Buy a device, split up the price into monthly payments, and pay an additional $10/month to enroll in the service.

There have been hundreds of reports of users hearing a grinding noise when they place a disc into their brand new Xbox One video game consoles. To prove it, here is an awesomely sad compilation of Xbox One owners having the issue.

Rooting your Samsung Galaxy Note 2 grants you access to system files, giving you the ability to change things on the device that you normally wouldn't be able to. Sounds great, right? There's just one problem. How in the hell do you manually change those system files?