I've already showed you how to magically unlock your Samsung Galaxy S3 with the simple wave of a hand, but why stop there? Sure, you could go out and purchase a Samsung Galaxy S4 so you have Air Gestures that let you control the lock screen, SMS, sound, wireless, and more.

When it comes to Easter, I usually dig plastic eggs with money or chocolate inside but hard-boiled eggs shouldn't be missing from the party. And simple hard-boiled eggs won't do. You need to decorate them because we all know bunny eggs are extravagant. What's even better than bunny eggs, though? Spider-bunny eggs.

On Thursday, March 14th, Samsung unveiled their new Galaxy S4. With it came a slew of new features, but what does that mean for us S3 users? Unless we're willing to shell out big bucks for the full retail version, most of us S3 owners (at least in the states) will not be eligible for upgrades until next year.

I loved the Gold Rush unit back in third grade. We went up to the American River and panned for gold, and my panning skills balled above all. I got like three tiny pellets. Of course, it was all fool's gold, aka pyrite, but it was still pretty legit. And this was before wearing gold chains was cool—or not.

I think part of the reason why I don’t eat more vegetables or fruits is because there's always a process—a simple one, but a process nonetheless. Having to wash my fruits and veggies is just flat out annoying. I just want to eat them, not take a shower with them.
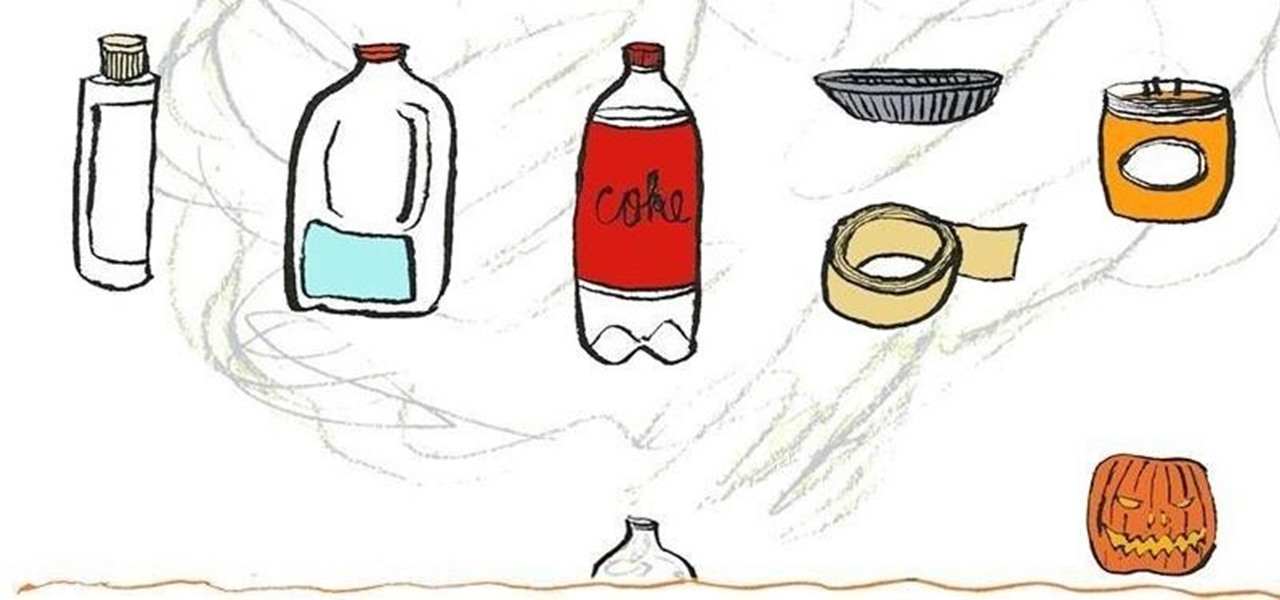
Need to add some spooky ambient fog to your super-scary Halloween party? Rather than shelling out money for a fog machine you'll probably only use once a year, make a trip to the nearest drug store and pick up a bottle of glycerin, a gallon of distilled water, a 2-liter bottle of cola, a disposable mini-pie tin, and a big candle in a jar.

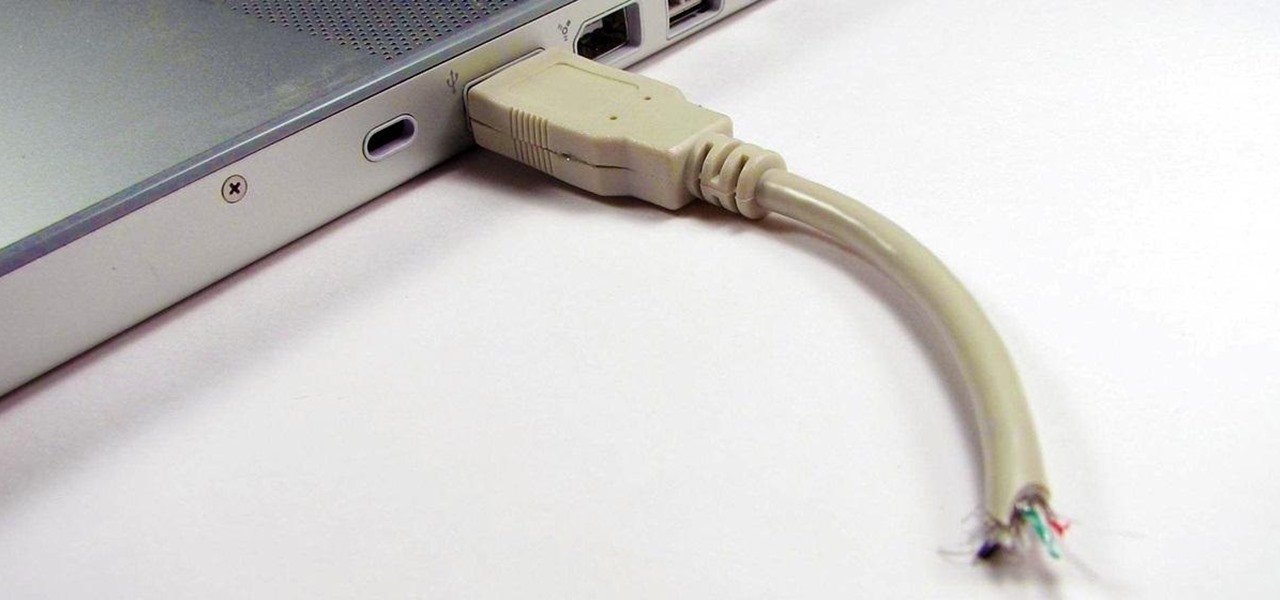
Having a flash drive is more or less a must, but the biggest downside is that they often get stolen, and it's not hard to figure out why. They're small, so they easily fit into pockets, and a lot of people store valuable information on them. Want to pretty much guarantee no one takes yours? Disguise it as a broken USB cable like Windell Oskay of Evil Mad Science Labs so it just looks like a piece of junk to would-be thieves. The materials are pretty simple: a flash drive (the smaller the bett...

With the release of Windows 8 right around the corner, if you plan on buying it (or just want to see what it's all about), it's a good idea to take advantage of the free trial before you shell out any money. If you're an Apple user who doesn't have a deep-seated disdain for Microsoft products, this tutorial will show you how to install the Windows 8 preview to try it out on your MacBook. First things first, you'll want to download the Release Preview on Microsoft's website (make sure to save ...

I am a man who enjoys a good cup of crap. Not just any crap, but the kind that makes the Seattle coffee-snob inside of me feel all warm and happy as if the sun were out (which of course it isn't.) It's the kind of crap that has traveled through the intestinal tracts of a nocturnal marsupial, cutely called a Civet. It's the kind of fermented brew that everyone should lay their lips on at least once.

Our server is primarily a fun server, so we don't often get huge, epic builds of amazingness. And yet that's exactly what we've got with Mgabrys's build, the Portland. Or, more specifically, Zeppelin City OR-2019 "Portland".

Flavored oils are amazing. They add a new flavor and depth to dishes not possible with plain oil. Most unfortunately, however, flavored oils almost always come with a hefty price tag to reflect their deliciousness and to capitalize on the general cluelessness of the public.

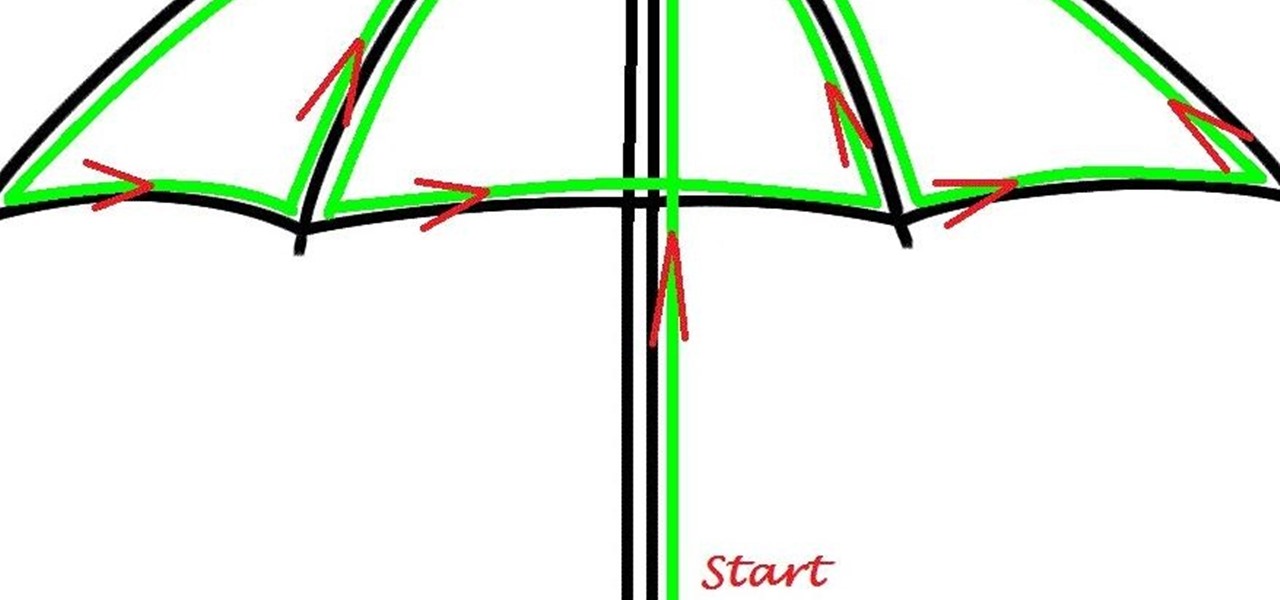
Here's a children's umbrella lined with neon green EL wire. It's definitely an easy and fun project for kids to do with their parents, and more importantly, it keeps the little mischiefs safer if they're out and about on rainy days.

It is one of the easiest method to make a basic macrame hemp bracelet. First get out your hemp twine, if you do not want to use hemp there is a wide variety of colored cord you can chose from, the thicker the cord the bigger your bracelet. Cut off two long strands and take one strand, fold it in half and loop it over a rounded stick such as a paint brush or pencil. Do the same to the other strand. Now, you have the four strands hanging down. Take the right strand, pull it over the two inner s...

If your cray fish or crawfish has tiny tiny worms crawling over the shell, watch this how-to video to fix the problem.

Gather your hoop and supplies. Wrap the suede evenly around the entire ring. Wrap it either eight or sixteen times, depending upon your preference. Glue the ends to the hoop. Secure them with a clothespin until the glue dries. Make the web. Tie the nylon string to the suede. Make eight knots evenly dispersed around the ring. Keep the thread taunt between knots. Make a second row. Place each knot "between" the knots of the previous row. Continue in this manner until a small hole remains in the...

Did you know Kali 1.0.8? You probably did, and you probably know about the EFI boot option that has been added.

The man in the video shows us how to peel an egg open in 5 seconds by slamming the egg down on the counter (not to hard but at a sufficient speed) and rolling it for a bit then peeling it off with ease. As shown with the comments on the video's page, this task is not as simple as the title states. It takes a lot of practice to crack the egg just right without smashing it, but if done correctly, gets you that perfect, out of the shell, hard-boiled egg. This video teaches you that practice make...

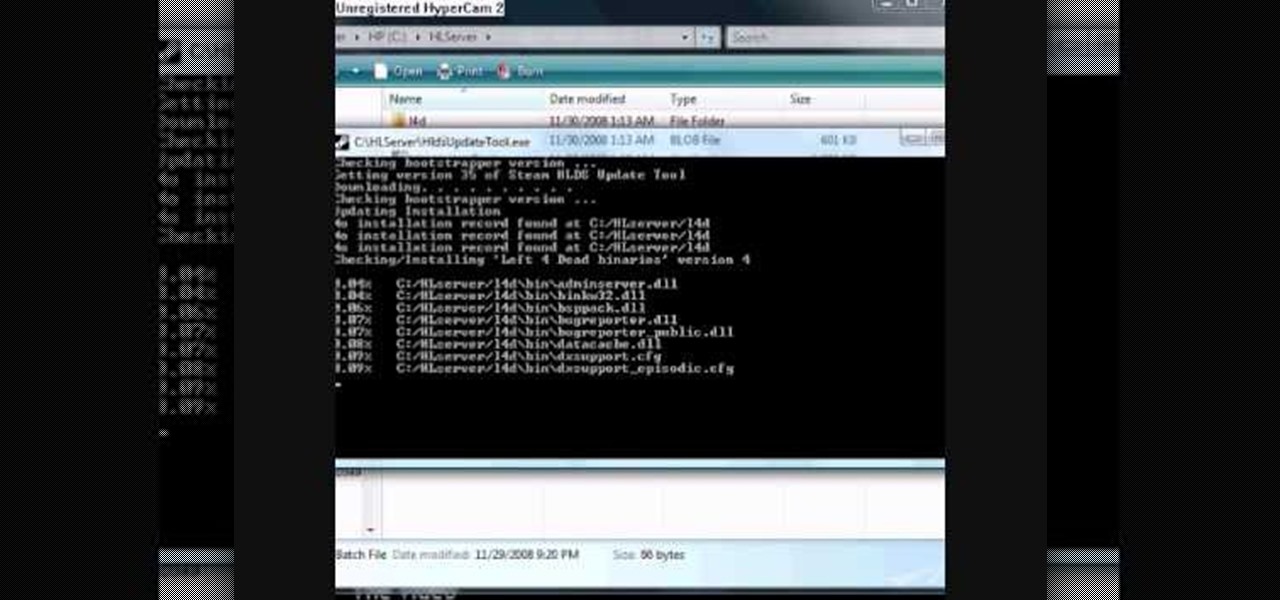
If you don't want to shell out the money to rent a dedicated server in order to host a Left 4 Dead game server, follow this tutorial on how to create one on your home computer. Keep in mind that if you intend on letting other people play it, you will need a fast connection to prevent lag.

Those smooth oval shells just seem to jump right out of your hands. When an egg hits the floor it is a gooey mess but not need to use an entire roll of paper towels trying to pick up the pieces. Cover with salt and the mess and be swept up after only a few minutes.

This interesting video is subtitled with instructions on how to make a Kawasaki rose origami. 1) Make mountain fold and 2 valley folds, as indicated, along guide lines.

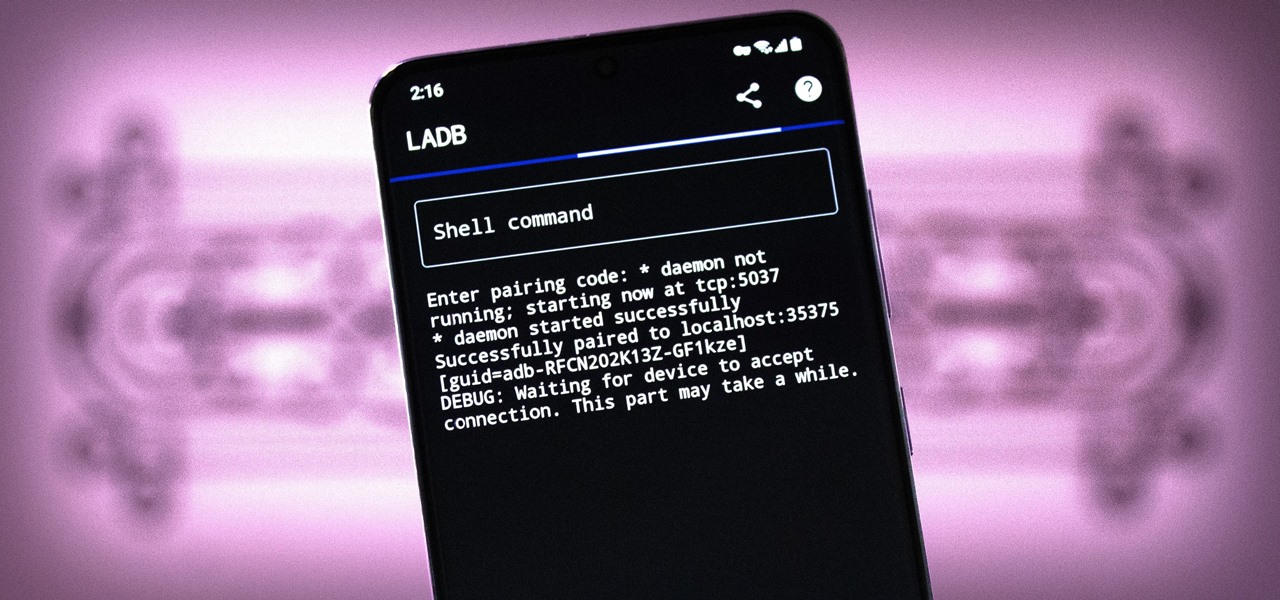
There are three tiers to Android customization: things you can do by default, things you can do with ADB, and things you can do with root. While root is still pretty tricky to get, ADB mods just got a lot easier.

GTFOBins and LOLBAS are projects with the goal of documenting native binaries that can be abused and exploited by attackers on Unix and Windows systems, respectfully. These binaries are often used for "living off the land" techniques during post-exploitation. In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line.

One of the most promising avenues of attack in a web application is the file upload. With results ranging from XSS to full-blown code execution, file uploads are an attractive target for hackers. There are usually restrictions in place that can make it challenging to execute an attack, but there are various techniques a hacker could use to beat file upload restrictions to get a shell.

The internet has undoubtedly changed the way we work and communicate. With technological advances, more and more people can collaborate on the web from anywhere in the world. But this remote-friendly environment inherently brings security risks, and hackers are always finding ways to exploit systems for other uses.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

If you installed Android 9.0 Pie, you might have enjoyed trying out some of the new features in the latest version of Google's OS. However, change isn't always a good thing, so you might be wishing you could downgrade back to Oreo right about now. Good news — you can.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting for newbies to get down, and that's where Punchabunch comes in.

We're almost there to completing the setup of your Mac for hacking! Now that we have Git and Homebrew under our belts, it's time to take on something fairly easy, but very important for our hacking needs.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...

If you've been using Windows 10 for a while, you already know that Microsoft incorporated lots of new features into it. So you're probably familiar with Cortana (the new voice assistant), the Edge browser (their replacement for Internet Explorer), the newly resurrected Start menu, and all of the other big changes.

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.

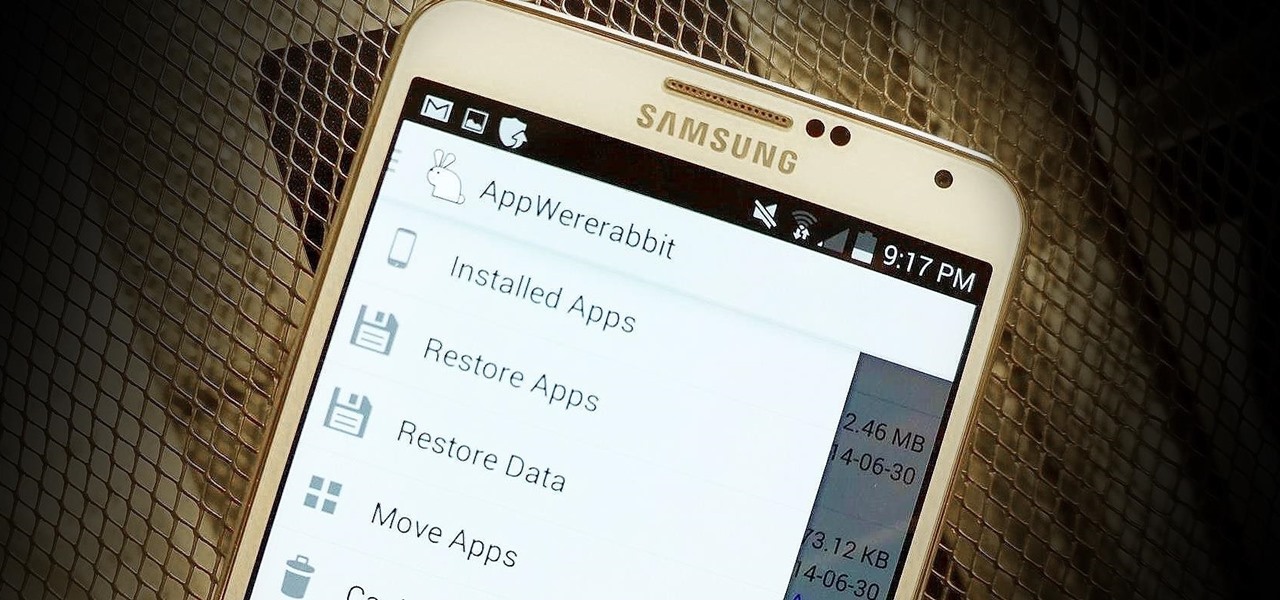
There are over 60-something Android apps cluttering my app drawer. While I'm constantly on the look out for new mods and apps to install, the default way of managing them is cumbersome and just feels unintuitive. I mean, who on Earth would wants to individually manage each app on their device?