Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft Security Bulletins.

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

Tired of the same old snacks? This cheeky treat will be sure to shock your guests. Although, we might not consider ants as a regular food source, they are edible. Plus, anything tastes good with butter and garlic.

The egg is an incredible compact, nutrition, protein and fat all in one prepackaged unit. This video will show you how to boil an egg using a strainer basket in your boiling water to heat steam your eggs as an alternative to regular boiling.

Life is too chaotic to be organized all the time, but little steps in the right direction make things easier overall. File folders keep paperwork from spiraling out of control. Spice jars take the clutter out of cabinets. Storage totes keep basements neat and tidy. But to find what you're looking for faster, you need a label maker.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

Some investors play the short game, placing their bets on industries that show the quickest return on their investment, and, in the augmented reality space, that means the enterprise sector.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

Bloatware remains one of the biggest problems with Android, especially when tied to a carrier. Removing bloatware usually requires you to take extreme measures like rooting. Unfortunately, the Galaxy S10 falls under this annoying umbrella, but there's an easy workaround.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

Augmented reality gaming company Niantic Labs is now instigating conflicts between Pokémon GO players, but it's not as bad as it sounds.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.

The Daily Prophet, the enchanted newspaper from Harry Potter lore, is no longer the sole source for magical moving printed photos.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

A funny thing happened on the way to the release of the virtual reality epic Ready Player One — augmented reality grabbed a major piece of the spotlight. Specifically, Microsoft's HoloLens.

It is finally happening. After not having a major update since August of 2016, HoloLens owners everywhere will soon get a number of new features added to their devices. At least if they are members of the Windows Insider program.

It's long past time to face the facts: farts are funny. The first fart joke dates back nearly 4,000 years to the ancient Sumerian people. References to flatulence were also found in ancient Greece within the works of Aristophanes. (More like Aristo-fannies, am I right?) A standard in practical jokes, the whoopie cushion debuted way back during the time of the Roman Empire.

Google's new Pixel 2 and Pixel 2 XL have a new camera mode called "Motion Photos." As the name implies, it's quite similar to Apple's Live Photos feature or HTC's Zoe before it. For every picture you take, a few seconds of video footage from before and after the shot was taken will be embedded in the file, which gives you two ways to relive that moment.

One of the best features in Super Mario Run is a multiplayer race that lets you test your skills against other players. Toad Rally, as it's called, pits you against other players in a battle for Toads. The more Toads you collect, the easier it is to build your kingdom and collect more rewards on your Android or iPhone.

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

Wound infections don't usually enter the blood and become systemic, spreading the infection throughout our bodies, and there's a good reason for that: Our bodies actively work to prevent it, according to research that discovered a new use for a protein first discovered decades ago.

While it is easy to create and maintain your compost pile, you can enjoy it more knowing a few basic tips.

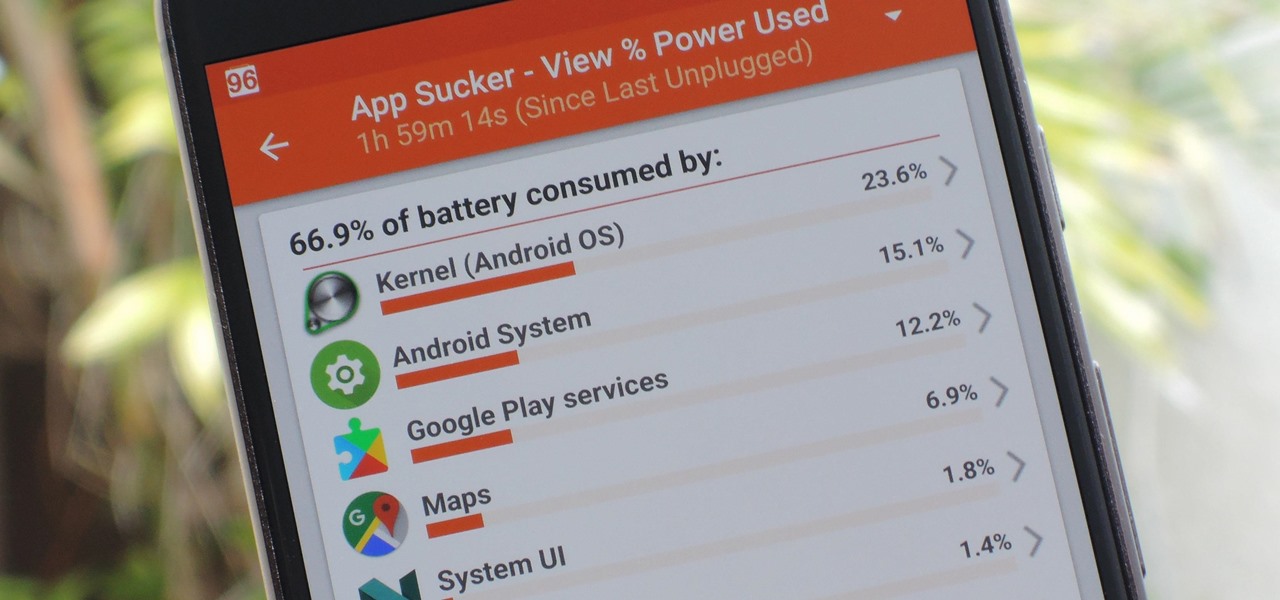
Figuring out exactly which apps on your phone are eating through resources and battery life can be a difficult task. Though some information can be found in Android's battery menu, the charts and graphs provided here pale in comparison to what's offered by the GSam app. If you configure this app properly, it provides deep insight into battery, CPU, and data usage.

We know your time is valuable to you, so starting this week — and continuing every Wednesday — we are going to release weekly Dev Reports that quickly highlight important news and updates that augmented and mixed reality developers should know about.

Sony has upped the ante for the promotion of Smurfs: The Lost Village, which was released on April 7 in the US, with a mixed reality experience via Microsoft's HoloLens.

Samsung's new personal assistant, Bixby, is making its debut on the Galaxy S8 and S8+. In addition to taking voice commands and performing visual searches, a new Hello Bixby feature predicts what you might want to do next with an integrated home screen feed. All of these features look nice, but if you're not ready to shell out at least $750 for a new phone, you'll be glad to know that Hello Bixby just leaked.

If anyone has every told you that they see music they listen to, they have synesthesia. It's a fascinating neurological phenomenon where people experience crossed responses to stimuli, and no one knows exactly how common this is. A rough estimate claims that one in every 5,000 to 100,000 people is a synesthete, but it could be far more common or rare. Nobody really knows.

Even when no one is in your kitchen, it is crowded. The refrigerator, sink, and counters are all covered with microbes that are just hanging around. They are inadvertent remnants from the raw chicken you used in that recipe last night, brewing a bacterial cocktail in your Nespresso machine, or just growing their merry little colonies on your leftovers.

As a commercial and potentially consumer product, one might assume it very unlikely to see the Microsoft HoloLens in the military marketplace. And that assumption would be completely wrong. One company from the Ukraine is currently working on using the mixed reality head-mounted computer for 360-degree vision inside armored tanks. If a tank crew could see the entire battlefield there are in, they would likely have a better chance of accomplishing their mission and avoiding damage. Tanks are l...

Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking.

As we reported first here on Gadget Hacks, the Google Pixel and Pixel XL have unlockable bootloaders, with the exception of models purchased from Verizon. This means that once the TWRP custom recovery is installed, you can flash ZIPs and even root your device in a few taps—as long as you unlock the bootloader beforehand.

If you spend weekend mornings sadly turning your omelet attempts into scrambled eggs rather than enjoying a perfectly flipped omelet, reach for a resealable plastic bag. Using a ziplock bag to make an omelet is not only foolproof, it's the perfect solution to cooking for a crowd, where you can make everyone's customized omelets at the same time. How cool is that?!

We used to saunter into the grocery store and gaze longingly at the pre-made roasted chickens, wistfully thinking of things we could do with the golden fowl if only we didn't already have dinner plans.

Hello guys, I recently made a how to about whatsapp but the problem with that script is that it is way to long and you need to copy and paste it so many times so I made a new one that works just fine and is more easy to use lets get into it (Here Is How The Code Supposed To Look)