In this installment from the Unorthodox Hacking series of Internet security tutorials, you'll learn how to get a shell on a Microsoft SQL Server (or SQL Server Express.) See how easy it is to obtain a shell in a Microsoft SQL database with this how-to.
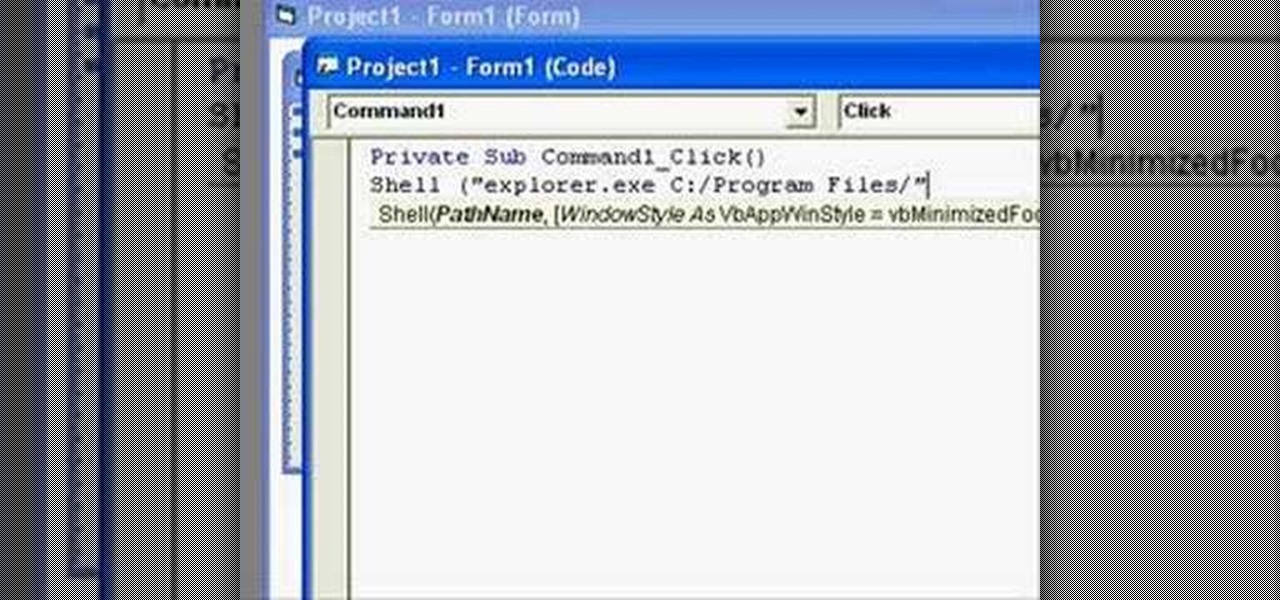
In this clip, you'll learn how to use the shell function to use the shell function to open folders. Whether you're new to Microsoft's popular event-driven program language & IDE or a seasoned developer merely looking to improve your chops, you're sure to find benefit in this free Visual Basic programming lesson. For more information, including a complete demonstration and detailed, step-by-step instructions, take a look.

This wavy shell crochet pattern uses three colors to make the design look complex and random. Actually it's quite simple. There are only two rows in this wavy shell crochet pattern. One row alternates between a few standard stitches and half pinwheel shape. The second row is completely plain. Try out this crochet project to achieve satisfying results.

Crochet a shell variation with tips from this how-to video. Watch in slow motion before you skip over to the next shell.

Of course, you'll want other people to be able to interact with your program. Linux sets up a command shell automatically, but if you're programming with Python on a Windws machine, you'll need to do it manually - and this video shows you how.

This is a great gift for a baby - crochet a small afghan for them! This tutorial shows you how to use the slanted shell technique, and has been designed for use by those who prefer to use their left hand to crochet.

It's winter time, and Christmas is coming up. What better gift than a warm, handmade hat? This tutorial shows you how to crochet the darling shell cap, an easy and attractive hat. It has been specially designed for left handed crocheters.

In this video we learn how to crochet a shell beanie hat. There are a total for seventeen rounds to make this beanie hat. Start out with a chain one and then single crochet in the starting loop. Continue to do this throughout the round and then join in the beginning single crochet. For the next round, you will single crochet and then create shells in the hat. Start out with round three, where you will start with a double crochet and then join the half double crochets with the beginning. When ...

In this video we learn how to make a soft shell crab dish. First, start making the sauce with white wine, honey, peppercorns, lemon juice, and heavy cream. Let this reduce and then start another skillet with chopped onions, red peppers, green peppers, and olive oil. Add in some chopped celery and then add these to some cooked cubed potatoes. Then, add in some mayonnaise along with some cooked bacon and pepper. Sprinkle in some salt and horseradish then mix all of this up and place in the frid...

Fried tuna? Pasta shells? Count us in. Combining our favorite comfort foods (fried anything and delicious carbs), this pasta dish is wonderful for serving at your dinner table after everyone's had a long day and wants to relax with a delicious, warm meal.

Hey crochet junkies, looking to try something new? In this video tutorial, learn how to crochet an adorable cluster shell. For written instructions, you can visit Crochet Mania's blogspot here.

This video is presented by Coco Joe from CocoJoesCoconuts. The video starts by demonstrating the technique for getting the coconut water from young coconuts. Coco Joe first uses a coconut opening tool by inserting it into the top part of the coconut and prying off the very top of the coconut. Next, he inserts the coconut opening tool directly into the top of the coconut resulting in a nice round opening. Joe then demonstrates the same technique with a 3 inch pocketknife. Finally, Joe demonstr...

Learn how to crack an egg so that you can preserve the shell in simple steps. First take an egg and a butter knife and you have to make a hole at its top. To make the hole gently tap the top of the egg to make a crack. Now insert the knife in the crack and peel its top out. Pour the egg yolk in a container and rinse the shell several times with hot water. Spray an anti-bacterial spray to kill any germs in it and let it dry for sometime with its hole facing downwards.

Place slip knot on hook. Hold yarn taut with 2 sets of 2 of fingers placed about 1½” apart, with tail in other hand. Create loop that crosses over bottom of 1st strand with loop toward right side. Fold loop over main strand going past tail. Insert hook below at tail strand. Pull up a loop using main strand for this loop. Pull 2 ends of yarn taut while leaving slip knot on hook. In 1st chain work 1 single crochet. Skip 2 chains; work 1 double crochet in 4thchain. Picot stitch by chaining 3 & a...

Materials Needed: - Use a Size K Crochet Hook - 2 strands of 4 Ply Yarn Round 1: Start with the Chain 4, then join and wrap. Pull a loop up. Work 12-Full Size Half Double loops through the loop. Then join in the beginning Half Double crochet. Round 2: Start with a chain (1 loop). then work 2-Half Double crochets, in each stitch around for a total of 24-Half Double crochet on round 2. At end of round 2 join in beginning Half Double crochet. Round 3: Start with a chain (1 loop). Do 1-Half Doubl...

Cracking an egg is a simple task once you have the technique down, so check out this video. Keep the shells out of your food!

In this installment from the Unorthodox Hacking series of Internet security tutorials, you'll learn how to get a shell on an Oracle database. To see how to pop a shell from within Oracle or even perform a port scan from the database itself, watch this hacking how-to.

If you're interested in learning a general purpose, high-powered programming language, Python might be the way to go. In this installment from his video tutorial series dedicated to programming in the Python programming language, you'll learn how to set up your bash shell for programming in Python.

Egg yolk mixed with your egg white? Bits of shell in your egg yolk? Here's an efficient and nearly foolproof way to separate whole eggs. With an added bonus...you get to play with your food! Watch this how to video to learn a great way to separate eggs.

With this video tutorial and with help from a little black powder, you'll know all you need to make small can shells for some awesome aerial fireworks.

The Catherine's Wheel is a great technique to add to your crocheting repertoire, and it's easy to learn as it's just a variation of the more basic round shell stitch. Learn how to crochet the Catherine's Wheel pattern by watching this handicraft how-to video.

Improve crocheting skills by creating solid motifs. This how to video is a crocheting tutorial that shows how to create a three sided solid motif. Crochet several of them, bind them together and create larger handmade projects. Learn these basic stitches by following along with these simple step by step instructions.

This video will walk you through the beginning to end on painting a RC (radio controlled) vehicle shell. Everything that you need to know on how to paint a shell is on here, from shaker cans (spray paint) to airbrushes. I use a Iwata by the way and a harbor freight air compressor. The paint used in this is Pactra silver and black. The airbrush paint is Spaz Stix candy apple green, blue, dark blue, and white. The lightning effect came out pretty well in my opinion, but you be the judge.

This shell embed soap is perfect for summer beach houses no matter where you live. And, it's very easy to make.

Learn how to teach your players the basics of defensive positions with the help of this great defensive shell basketball drill.

This is a tutorial for using the multi-replicate function in Bryce to create organic-looking shapes (shells, horns, elephant trunks, etc.)

Follow these crochet guidelines to start a wavy shell pattern crochet blanket. This pattern is only a two row pattern. You can use three colors to make it appear unique and interesting. The beginning is the most difficult part, but once mastered, this crochet pattern is deceptively simple.

Shell-covered pots are such beautiful decorations for the summer, bringing the beach into (or directly outside of) your home even if you live inland. They add a gorgeously breezy oceanic touch to your plants.

Julissa Roberts shows how to shuck an oyster. She shows us how to determine whether the oyster is safe to eat, how to shuck the oyster, and then one way to prepare a plate of oysters. If you don't properly check the oyster, and clean it, you could get a mouth full of sand, or get an oyster that smells like rotten fish. To check whether the oyster is good, smell it, it will smell like rotten fish if it's bad. Then tap the oyster on something solid, if the oyster is dead, it will sound hollow, ...

Ming Tsai with Simply Ming explains some shrimp basics. When you prep shrimp, you have to de-vein it, and you have to take the shell off. First cut off the head. Take a knife and slice sideways through the shell. Take out the vein, then get 3 bowls of water and add salt to 2 of them. After de-veining, put the shrimp in the first bowl of water. Keep adding shrimp until you get about a half pound of shrimp, or however much you wish to cook. Then peel the shrimp, and put it into the second bowl....

This video demonstrates the method of deveining shrimp: i.e. removing the digestive tract from the shrimp. The digestive tract runs along the back of the shrimp. For this, you will need large raw shrimp, a knife,

As most of you know, I am a strong advocate for using Linux for hacking. In fact, I would go so far as to say that you cannot be a hacker without knowing Linux well. I laid out various reasons for this in my "Why Every Hacker Should Know & Use Linux" article, and I even have a lengthy, continuing series on Linux Basics to help those new to Linux master it.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

This is a method for making a native American free point spear using a bamboo stick, bamboo strips and some commonly found items. First take a sea shell and make a hole in it. Make the hole using a pointed stone and pierce an opening in the shell. Make the hole such that the shell fits the bamboo. Now the bamboo has to be split in half and for this you have to find a common stone which has a sharp edge on one side to split the bamboo. This is a common stone found anywhere. Now you have to tak...

In this tutorial Mike Lively of Northern Kentucky University shows you how to get started with Wireshark. Wireshark is a network protocol analyzer for Unix and Windows. It is used for network troubleshooting, analysis, software and communications protocol development.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

It's 2017—new year, same us. We vow to keep scouring the net for the best how-tos and feature the makers and doers who create mind-blowing projects.

When a craving for crunchy tacos hits, it's undeniable. Don't Miss:

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!