Wheat is not just for eating, it is a great substance to make glue to paste different types of shells. These shells by the way are not seashells. In a pan and in a bowl put an equal amount of water in each. For example, if you have 1 1/2 cups of water in the pan; put 1 1/2 cups of water in the bowl. You are going to bring the water in the pan to a boiling temperature and you are going to add flour to the water in the bowl and dissolve it. The consistency of the flour and water should be that ...

To really appreciate quiche, you need to like the versatility of the dish, and if done right, a quiche can be the prefect breakfast, lunch or dinner meal for the entire family. Even a Sunday brunch. This quiche will please any crowd. Check out the recipe for this delicious asparagus, mushroom and fontina quiche from Chef Hubert Keller.

Don’t wait for Cinco de Mayo to enjoy a Mexican meal – tacos are a tasty addition to any table any time.

Clara's Great Depression Holiday Special! Recipe:

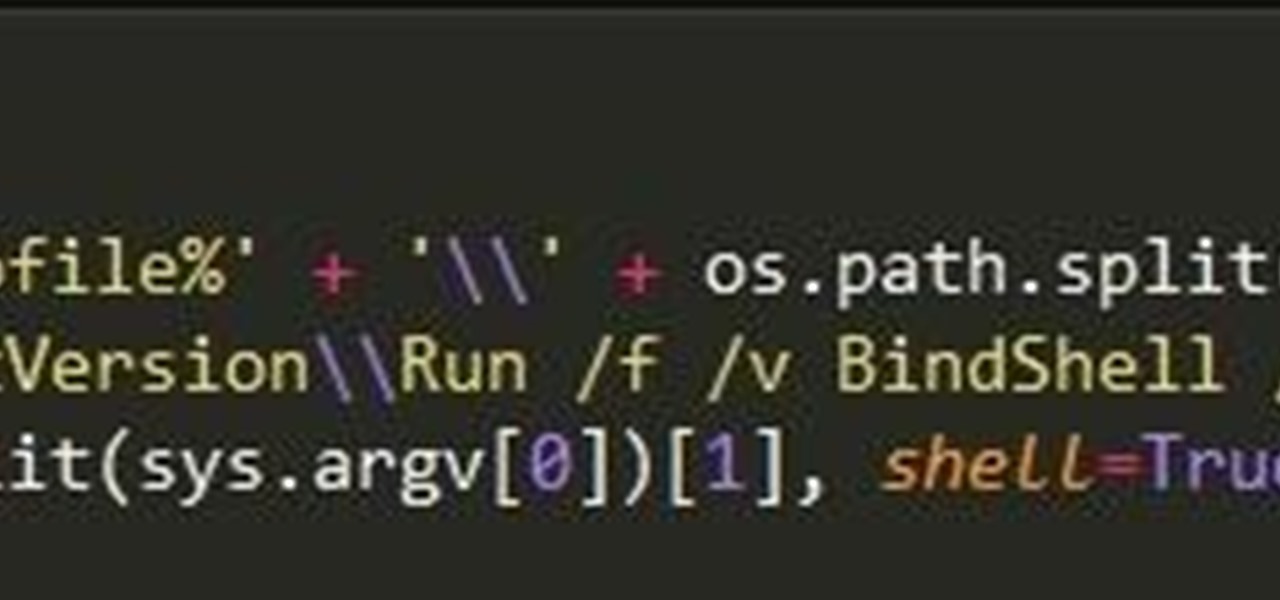
With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

You may have caught our prior list of excellent egg hacks. Well, we've rounded up 10 more awesome tips and tricks to perfect your egg game. Check 'em out below.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

When you start planting something, you will need to nurture and grow a seed. You can plant a seed in a small pot and transfer it later, or you can save yourself the mess and trouble and try the tips in this video. In this tutorial, learn how to plant seeds in an eggshell! Eggshells make great little planters and the best part is - they're biodegradable so instead of repotting your seedling you can just plant the whole egg in the ground!

Prepare the eggs by rinsing off the shell under running water to remove any loose dirt or germs. Crack the eggs into a plastic or glass bowl, drain the shells, and put the empties into the trash bin. Rinse your hands after handling the shells and raw egg yolk. Season the eggs with a mixture of lemon-pepper seasoning and salt. Add a teaspoon of water to the eggs.

Got a craving for banana cream pie? Make it yourself at home! Banana cream pie is a timeless classic. Here's how to make the perfect balance of bananas and pudding at home.

Edamame are immature whole green soybeans—the only vegetable with a complete protein that’s similar to animal protein. And because they’re actually kind of fun to eat, they’re an excellent snack. . . and pretty tasty with beer, too. They are cheap and good for you. Learn how to make edamame.

Craving some classic Italian recipes? Then watch this cooking how-to video tutorial to learn how to make a stuffed pasta shells. Stuffed pasta shells are also known as Manicotti and they are simple to make.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

For many of you, the carving fork only comes out at Thanksgiving as an essential turkey-slicing aid. Perhaps you pull it out of the knife block to slice up the occasional roast. But the carving fork (also known as kitchen fork) can be used for many more tasks around the kitchen, and some of the more unusual involve your favorite shellfish.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

Hi guys, I'm gonna keep this short because I got assignments and a lot of notes to study and also other how-tos and forums to reads. lol...Since I'm keeping this short...no story time just scenario. And I want to thank n3stor for giving me the idea to post this.

Bad news first: It's not out yet, but it's coming really soon. The premise for the game is this:

The other day I was doing the math on roughly how many eggs I eat each year. I estimated about 500. That's a lot of eggs. And, subsequently, that's a lot of eggshells to throw in the trash.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

During Thanksgiving, cooks, who are often limited by time and oven capacity, must choose between classic Thanksgiving side dishes like mashed potatoes and more interesting, novel ones like Italian stuffed pasta shells. Have both a classic dish and a new one by checking out this video.

Often in creating crochet patterns, crocheters will pick natural objects with natural symmetry or a pretty shape, like shells and blueberries, to be the inspiration for a new crochet pattern.

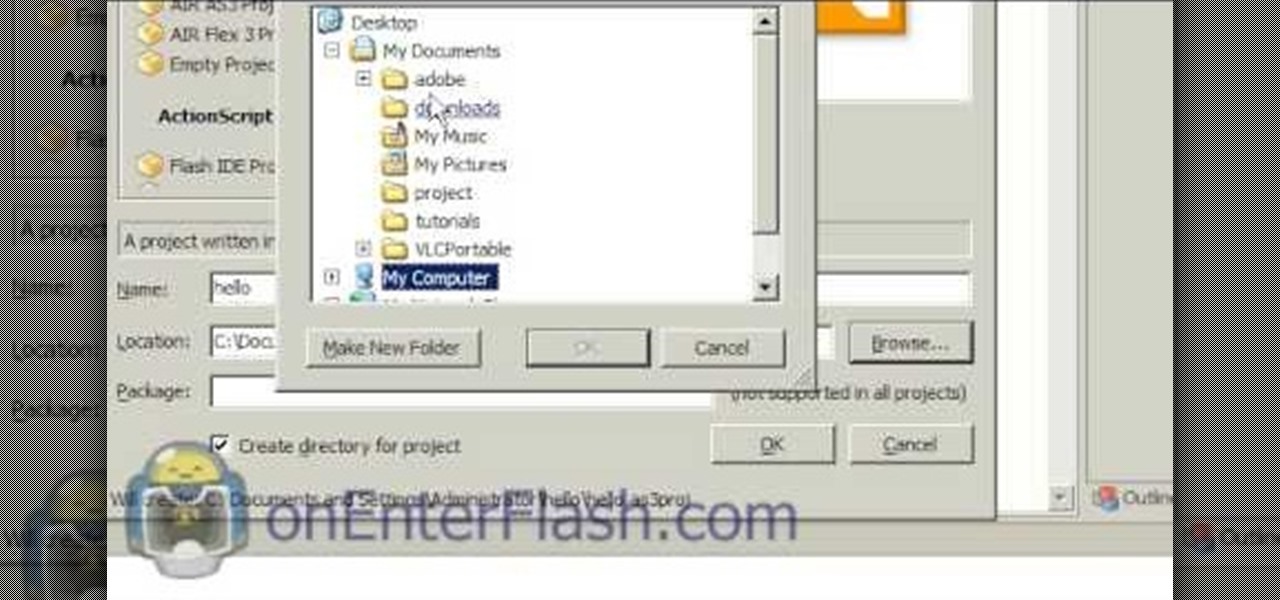
Flash development software can be very expensive stuff to come by, but it need not be. This video will teach you how to install and get started using FlashDevelop and Flash SDK together to edit Flash without having to shell out for the Flash IDE.

Here's how to get egg whites like a pro. Quit worrying about getting egg shell specks in your whites. This is a tutorial specific to beating the eggs. Don't over beat your eggs. You want to go from foamy to soft peaks to stiff peaks.

Like the crab that symbolizes them, Cancers can be a little soft-shelled at times, so woo these sensitive souls cautiously. Learn how to use astrology advice in dating, by watching this how-to dating video. Pick up tips on making a relationship with a Cancer work. Here a hint, do something nice for a Cancer when you suggest an activity for the both of you to do.

Getting into the inside of a coconut can be tough but this episode will show you an easy and quick way to crack open a coconut. Leave the tools in the garage. Forget about trying to cut the shell. All you need is a sturdy kitchen knife and a flick of the wrist.

No, we're not lying. But before you try and tear a plain old penny in half, you should probably watch this video first or you may hurt your fingers. While ordinary pennies are very, very difficult to rip, if you get rid of the zinc core you are left with only the thin copper shell, which is itself very easy to tear apart.

Watch balloon twister Michael to learn how make a balloon Ninja Turtle. First, make the shell. It is a little complicated but the video is slow and makes it easy to learn.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

If you've been watching the latest USA TV Series Mr Robot, you will have seen the Raspberry Pi used by Fsoeciety to control the HVAC system. OTW covers this very well here with his take on setup they may of used.

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Do you love figs but don't love how the fruit's shell sometimes pinches and irritates your lips and tongue when you eat it? Then take a gander at this video to learn how to consume figs without any bodily injuries.

A Lampare, or aerial fireball shell, is a really cool pyrotechnics device that basically allow you to use a cartridge to launch a fireball into the air. This video will show you how to make a 3" Lampare out of black powder fuel and a Napthalene / charcoal mix. Dry fuel is safer and lasts longer than liquid fuel, so study up!

Use this clever technique to remove an uncracked shell from your eggs that lasts a long time and can be used for a ton of craft and Easter projects. You will learn how to use a store-bought egg blower to blow your eggs the easy way and save the insides to cook with. Have fun!