
How To: Peel a Hard Boiled Egg in Seconds
We all know getting hard boiled egg shells off can be a pain. I've done how to peel a hard boiled egg the cool way. I now present to you how to peel it in seconds.


We all know getting hard boiled egg shells off can be a pain. I've done how to peel a hard boiled egg the cool way. I now present to you how to peel it in seconds.

Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock:

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Hard-boiled eggs are such an amazing snack, but there's nothing quite so frustrating as trying to get all the shell off without damaging the egg underneath. I've ended up with many a sadly pitted and pockmarked egg that somehow doesn't taste quite as good as when it emerges all white and smooth.

Anyone who has rooted their Android device has likely used a tool called Android Debug Bridge, better known as ADB, at some point during the process. For most, that is their only interaction with the ADB, but to be a true Android power user, you need to really know the tools at your disposal.

Video: . The macho and easy way to make golden eggs. How to scramble eggs inside their shell useing a drill. AKA Fuwatoro Eggs.

Check out this informative video tutorial from Apple on how to set up iChat to text, video or audio chat with friends. iChat is an application that's part of every new Mac. It lets you stay in touch with friends and family in fun innovative ways.
Check out this informative video tutorial from Apple on how to do more with the Sidebar in the Mac OS X Finder. Learn about the Sidebar devices, the Sidebar shared, the Sidebar places, and the Sidebar search for. Mac OS X. It's what makes a Mac a Mac.
Check out this informative video tutorial from Apple on how to use the basics of the Mac OS X Finder. Learn about the Finder basics, the Sidebar, view buttons, and Quick Look. Mac OS X. It's what makes a Mac a Mac.
Check out this informative video tutorial from Apple on how to organize your Mail in Mac OS X's Mail. See how to sort messages with rules, create smart mailboxes, and comlpletely organize your mail. Mac OS X. It's what makes a Mac a Mac.
Check out this informative video tutorial from Apple on how to use the basics of Mac OS X Mail. See how to set up mail with your email accounts, compose messages, add attachments, view attachments with Quick Look, and search through Mail. Mac OS X. It's what makes a Mac a Mac.
Check out this informative video tutorial from Apple on how to use Mac OS X Mail to its fullest. See how to filter out junk mail, use data detectors, and view RSS feeds in Mail. Mac OS X. It's what makes a Mac a Mac.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

There may be no other crustacean with as many names as the crawfish: crayfish, crawdad, crawdaddy, mudbug, Florida lobster, spiny lobster, rock lobster, and freshwater lobster (to name a few). But no matter what you call it, there's no denying that it's a popular delicacy in the South and beyond.

If you remember last time, we successfully uploaded picture with a small hidden PHP command executer embedded in it onto a server. Now, our goal is to take this a step further and get an interactive shell. To do this, we need to upload another file that either binds a port for us, or connects back. For this tutorial, we will use a Python reverse Meterpreter shell.

Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house.

This tutorial shows you how to make spell packets. It's designed for NERO, but many larps use the same rules. All you need is a square of natural fiber cloth (like cotton), some birdseed (or rice or crushed walnut shells or any biodegradable matter) and a rubber band.
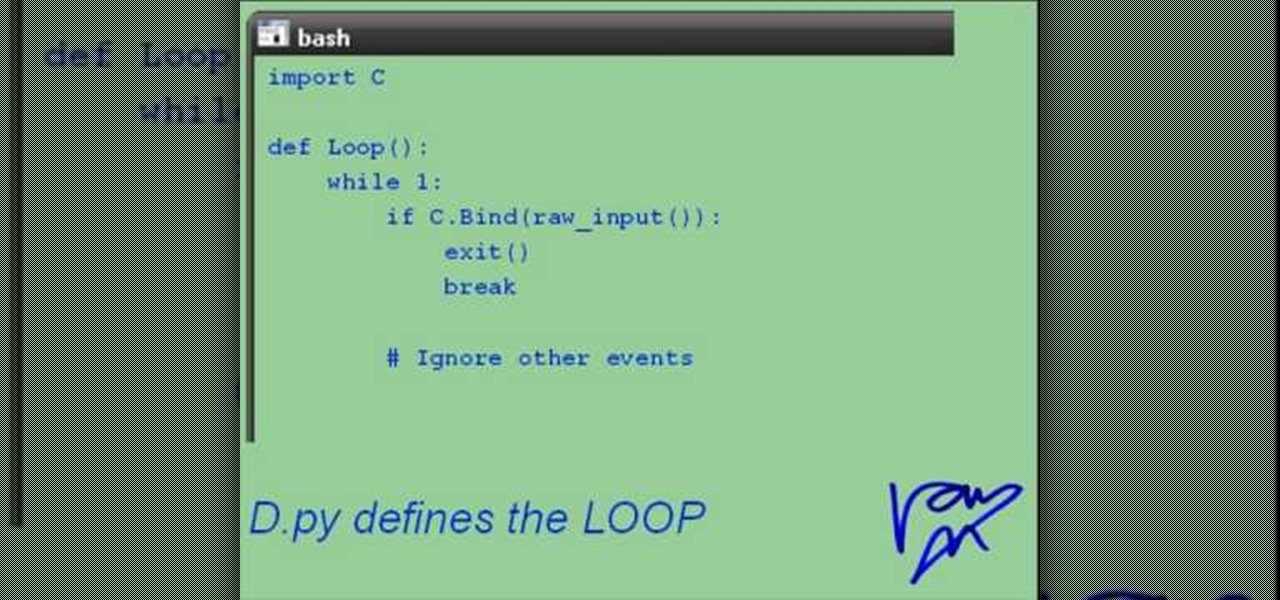
If you're interested in learning a general purpose, high-powered programming language, Python might be the way to go. In this installment from his video tutorial series dedicated to programming in the Python programming language, you'll learn what's necessary to create an interactive program from a Linux shell. To get started programming with Python, take a look!

This HowTo video is a cooking demonstration that is loaded with fresh veggies, mixed with a Thai yellow curry sauce and served over shell pasta. This recipe is ready in just 10 minutes with this easy to follow recipe. All the ingredients your need for this Thai dish are: cooking oil, red pepper, green pepper, zucchini, squash, onions, baby corn, asparagus and Gourmet Curry Simple Yellow Curry ( or your favorite yellow curry sauce).

With this how-to, you'll learn how to mount an SSH server on your Mac as part of the file system. The key is a third-party program called MacFuse, which is available, free of charge, through Google Code. To get started running SSHFS, or the secure shell filesystem, on your own Mac, take a look!

Enjoy a special Valentine's Day treat from Rob "Riki Tiki" Roy and Bottom's Up. You will need vodka, dark creme de cacao, Kahlua, Magic Shell, and a Hershey's Kiss. Mix up a sweet chocolate martini by following along with this video cocktail-making tutorial.

Tired of frying, boiling, scrambling and deviling eggs? Smoke them on a BBQ grill. Johnny O shows how to smoke eggs in the shell, and make smoked caramelized bacon to go with them. Watch this video cooking tutorial and learn how to smoke eggs and carmelize bacon for a barbecued breakfast.

This video will show you how to apply makeup to your whole face for a new look in the mornings, as well as how to apply eyeshadow for a brown smokey eye look. This smokey eye can be updated at night for a more chic makeup look for going out.

With their hard shells, lobsters aren't the easiest crustaceans to eat. Here, a chef shows you how to open a lobster and locate its sweet, succulent meat.

Very basic beginner video of some things you can do starting with a glass disc. In this video I show how to make flower petals, leaves, sea shells, and wings.

Dave shows you what scale (hard shelled insects) looks like and explains how to get rid of it.

Have trouble peeling those hard boiled eggs? This video will show you how to put a crack in the egg and blow the whole shell off. Audio is rough so pay attention.

Acorn squash is a delicious and filling low calorie vegetable. Learn how to choose, cut, and bake acorn squash. Ingredients needed are acorn squash, butter, brown sugar, maple syrup and a dash of salt.You can eat it right out of the shell, or spoon it out into a bowl. You can mash the squash with a fork right on the bowl and enjoy.

In this video, Dan the Lobster Man instructs on how to make "Campfire Lobster Tails." Dan starts out with two New Zealand coldwater tails. First, he instructs us to quarter some lemons. To open the tail, take the tail and push down on it - you should hear the shell crack. Take a pair of lobster shears and cut in the middle, breaking the tail a little more, and slice down the middle of the meat. Take the melted butter and pour it on the middle. Squeeze some lemon juice in there as well. Butter...

Trying to stay away from carbs but love starches? Why not try some spaghetti squash instead of all that pasta? Spaghetti squash is easy to prepare and can be garnished just like you would with pasta or potatoes.

Start off with a pre-made chocolate pie shell. Next soften some vanilla ice cream. Make sure the ice cream is not super runny but not frozen either. You will want to be able to stir it. Next add one cup of sifted dirt. Making sure you have taken out all the rocks and twigs. Mix it thoroughly with the ice cream. Put half of the mixture into your pie shell. We then want to add the surprise layer. Add those twigs, leaves, and small stones that got sifted out earlier. Top it off with the rest of ...

In this how-to video, you will learn how to choose a proper bicycle helmet. They are the most important safety equipment a cyclist owns. Picking the right helmet starts with understanding what a helmet consists of. The micro shell is the thin tough layer that covers and protects the interior of the helmet. It absorbs the impacts of the helmet. The adjustable retention system consists of 2 straps. The chin strap goes across your chin and the other goes across the back of your head. The vents a...

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

One of the most exciting things as an ethical hacker, in my opinion, is catching a reverse shell. But often, these shells are limited, lacking the full power and functionality of a proper terminal. Certain things don't work in these environments, and they can be troublesome to work with. Luckily, with a few commands, we can upgrade to a fully interactive shell with all the bells and whistles.

This is a step by step video tutorial on how to make this beautiful hemp choker necklace with macrame knots such as alternating square knots, alternating half hitches, braids, and cowrie shells. Enjoy!!

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.
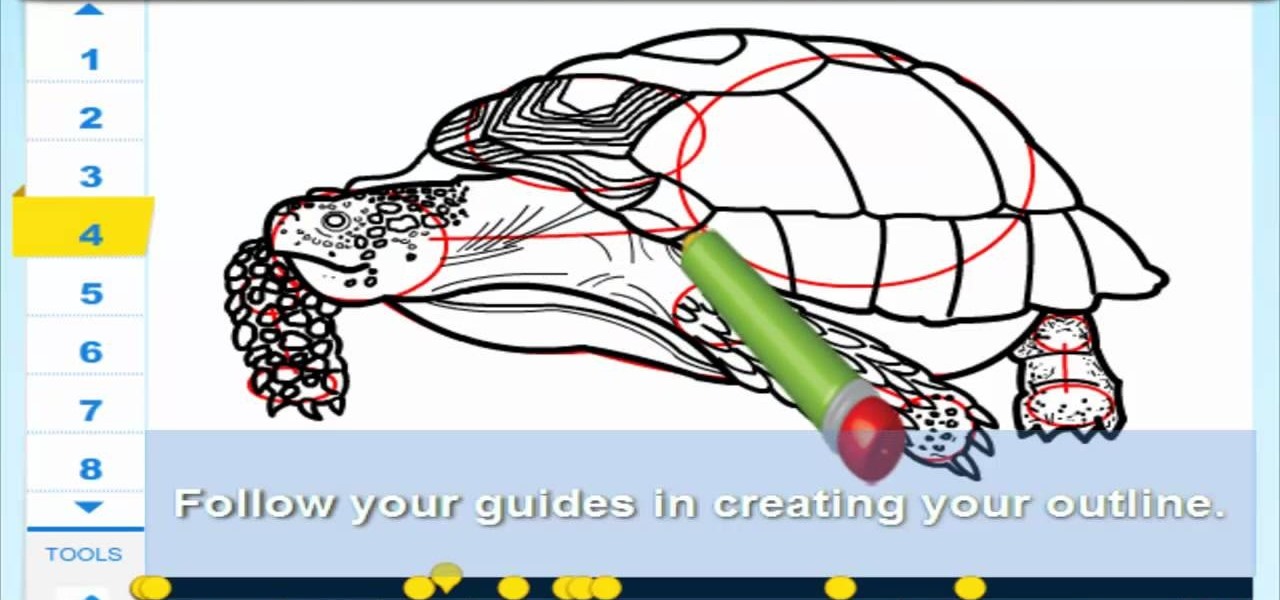
Tortoises are shielded from predators by a shell. They are generally reclusive animals. Learn How to draw a Tortoise. For the full tutorial with step by step & speed control visit: how to draw.