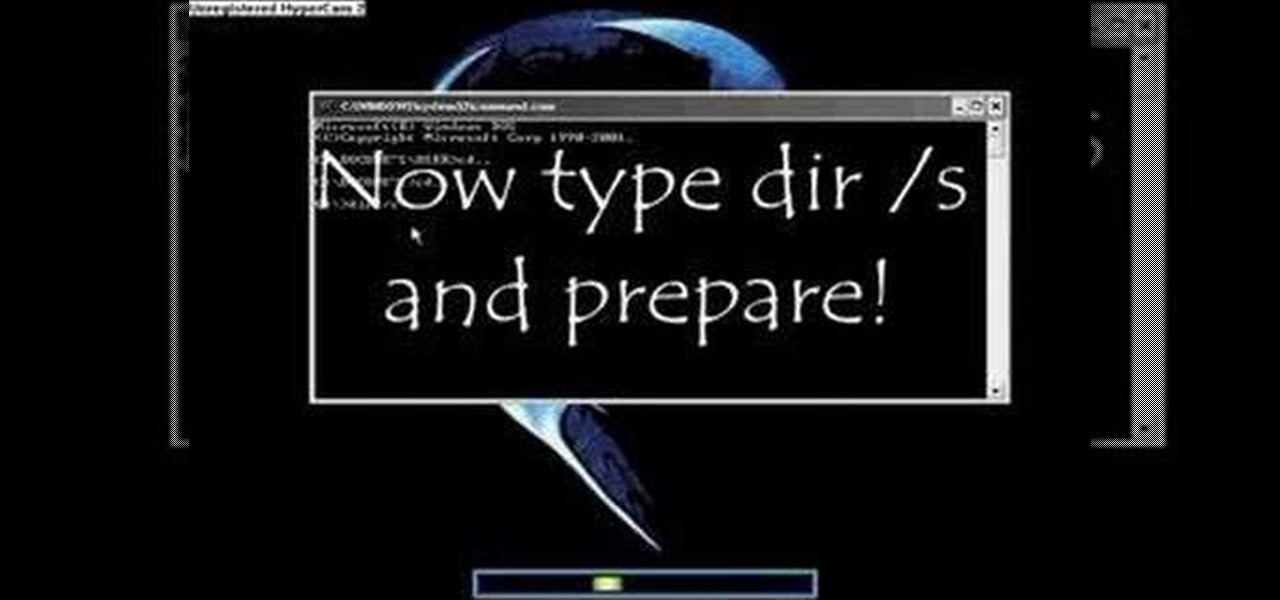
DOS may be a distant memory for most computer users at this point, but for many it will always be the first thing that pops into their head when they ponder PC computing. Nowadays, the only time most people see anything that even looks like DOS is if they're playing old PC games in a shell or something has gone very, very wrong with their computer. With this prank, you can make your friend believe that the latter has happened to them! All you do is open the DOS command program (Windows XP or ...

Watch this video series to learn how to make the base shell, terrain, trees, bushes, tufts of grass, and cast plaster rocks for a fantasy landscape diorama.

How to make deviled eggs while avoiding common mistakes

During Easter, everybody stocks up on the eggs because dying eggs is a great Easter activity. But there's something else you can try… dying and marbling. Watch this video recipe to learn how to dye and marble Easter eggs. A new twist to Easter eggs.

Here is another fantastic Pakistani recipe. Prawn biryani is a dish of prawns, rice and seasoning made in a Pakistani style. These prawns are sure to be full of flavor with lots of colorful seasonings and vegetables all cooked together.

Learn how to crack open a coconut. Release this tropical treat from its hard-as-a-rock shell without needing a machete.

Whether you’re a professional DJ or simply a vinyl enthusiast, knowing how to install a fresh needle will help protect your music.

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.

We're the ultimate foodies, but when it comes to preparing shellfish we get more than a little intimidated. Requiring heavy duty shell removal using knives and knick knacks that look like they belong in a doctor's office, the task is usually one who choose to skip.

How to make Italian pasta salad

This instructional video demonstrates how to make a strawberry pie. She starts with a frozen pie shell. Let the pie crust thaw for about 10 minutes. To make it look homemade, pinch the fluted edges so they are not perfectly even. Next, poke holes all over the bottom and sides of the crust with a fork. Bake the plain pie crust in a 350 degree oven for about 15 minutes. To prepare the filling, put 1 cup of sugar and 1 cup of water into a pan on the stove, mix 2 tablespoons of cornstarch with a ...

Watch this video to learn how to prepare an easy lobster appetizer. Your guests will gobble them up in no time! Ingredients four (1 lb) lobsters six cups mesclun (baby greens) one cup lobster stock one shallot, peeled and finely diced cup vinaigrette one tsp fresh lemon juice Freshly ground white pepper to taste Fine sea salt to taste one bunch fresh chervil for garnish Preparation Cut shelled claw meat into inch wide strips. Cut the legs and shell that covers the tail meat. Cut the tail meat...

Paula shares her chocolate pecan pie recipe with chocolatier Max Brenner. Follow along and learn how to make this decadent dessert. This cooking how-to video is part of Paula's Best Dishes show hosted by Paula Deen. What happens when America's favorite southern cook opens up her kitchen to family, friends, viewers and the best home cooks in the country? It's anyone's guess! Paula Deen is cooking up something new as she rescues viewer recipes, shares stories and traditions with friends and str...

Your bird will love eating this nutritious snack. Follow along in this bird cooking how-to video to learn how to make birdie bread. Birdie bread is a fun recipe that is great for both you and our pet bird.

If you love coconuts, coconut water or even coconut meat, you should know how to open one up. This HowTo video tutorial shows you an easy way to open a coconut without making a mess.

While some people might like Thanksgiving because of the food, seeing family, or another wholesome reason, many of us also enjoy saving big on the items we've been eyeing all year. Take iPhone cases, for example. Speck, Insignia, even Apple all make cases that can put a dent in your wallet. A good Black Friday deal can mean a shiny new case for your iPhone and some extra dollars in your pocket.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Kali Linux is known as being the de facto penetration-testing Linux distribution but can be a pain to use as an everyday OS — even more of a pain if that means carrying around a second laptop or the constant frustration of using the finicky Wi-Fi on virtual machines. But there's another option: installing a Kali subsystem on your Windows computer as a convenient compromise.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Greetings fellow students! I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers"

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!

There are a million (okay, slight exaggeration) ways to peel an egg, and countless numbers of tips, tricks, and hacks that are supposed to make that deviled egg appetizer you agreed to make for the party an absolute snap. More often than not, though, experiences vary... and pock-marked, greyish-yolked boiled eggs find their way into your collection whether you like it or not.

Greetings fellow hackers. This tutorial is about creating "safe" passwords. This is different from strong passwords. Safe passwords is just creating a password that is not used by someone else or colleague, my definition. But how do you prevent something like this from happening? Of course you won't ask your friend if s|he is using the password you are about to create. Before I show you some of my tele-psychic powers like Professor Xavier, you might want to read this for advice on creating "s...

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

I'm sure that many of us have heard of that nasty Shellshock vulnerability, but not very many people know how to exploit it. Try these few tricks on vulnerable websites!

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

For some strange reason, not all variants of the Samsung Galaxy S6 and S6 Edge have a menu option for changing the backlight timeout for their capacitive keys. According to user reports, only the AT&T variant of these phones has such an option.

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

A salad can mean everything from fruit to meat and everything in-between, but it never means finger food. Forks are required. So that means that even though salads are versatile, delicious, and customizable, they are hell at cocktail parties. How do you hold your glass and take a bite of your salad at the same time? It's awkward.

Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method.

Icebox cakes are some of the most satisfying, easy desserts to put together. This version made out of ice cream sandwiches takes the cake, literally, because the layers are almost pre-made for you. Simple and pretty when cut and served, it will be love at your first creamy bite. Depending on whether you want a layer of chocolate crunchies in your ice cream sandwich cake or not, this could be either a two-ingredient ice cream cake or a four-ingredient one. If you don't need the crunchy layer, ...

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

If you grew up dying eggs for Easter, you've no doubt used or at least seen those boxed kits that turn your eggs neon colors. Admittedly, they're easy—just plop a dye tablet into some water, dunk the eggs, and wait for them to dry.

Ice cream and cupcakes all in one? Count us in. Give your friends a special treat this holiday season by serving them up these chocolate ice cream filled cupcakes. A sturdy chocolate shell holds a cupcake that's filled to the brim with ice cream, then topped with a dollop of whipped cream.

Love brownies but in desperate need of a new and interesting way to serve them to your friends and family? Then look no further than this food video.

We know dolls are supposed to be children's toys, but there's something about them that scares the living daylights out of us. Maybe, just maybe, it's those lifelike eyes that appear almost too real to be fake? That seem to follow us as we move around the room? Okay, maybe we've seen a few too many horror movies, but you have to admit there's just something off about dolls.

In Fallout: New Vegas, you will eventually end up having to check out the other factions and tribes in the game. One of them happens to be the Boomers over at Fort Nellis Air Force Base, a clan of old vault dwellers who took over the base and have been making use of their heavy artillery to keep intruders away.

Shucking an oyster is something we usually leave to our significant other to do (Sharp knife combined with a supertight oyster shell opening? BAD idea for someone with sausage fingers). But after watching this video we're convinced it's easier than we think.

What?!? A pie without baking? That's right, and you'll learn the recipe for this no-bake blueberry pie in this video. You'll need 3/4 cup of water, 3/4 cups of sugar, 3 tbsp of cornstarch and a pinch of salt. Mix it all together and put it on the stove. When the mixture dissolved, add 3 cups fresh blueberries. Bring it up to a boil and cook them into a thick sauce. Next, add a tbsp lemon juice and another 3 cups of blueberries. Also, add 4 tsp butter. Stir it, cook it until it's to your prefe...









































