With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.

When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Facebook, only one should be used as the other will share your phone number with the world, a huge privacy concern.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

After first being announced at Mobile World Congress 2018, the ASUS ZenFone 5Z will finally be coming to the US. Deemed an iPhone X clone by some, there is more than meets the eye when it comes to this flasghip. While it is similar to the iPhone X, in some ways, it improves on the design.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Earlier this month, when Apple announced at WWDC that iOS 12 would include an augmented reality tape measure called Measure, iPhone watchers seemed impressed by the new addition to the company's AR arsenal. Well, just a couple of weeks later, on June 19, it appears that Google remembered it had its own Measure app as well.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

Apple's goal with iOS 12 is to smooth out the problems with its famously flawed predecessor. Of course, change isn't for everyone, and by iOS 11.4.1, Apple had a pretty stable thing going. If you're not digging all the bugs and new features included in iOS 12, here's how to downgrade your iPhone back to iOS 11.4.1.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

Super Bowl LII will bring millions of football and non-football fans together to watch the big game on the big screen. But without a cable subscription, this process can be a little daunting. Luckily, the Google Play Store and the iOS App Store offer a few ways to accomplish this — no cable contract required.

For years, PuTTy has reigned supreme as the way to establish a Secure Shell (SSH) connection. However, those days are numbered with the addition of the OpenSSH server and client in the Windows 10 Fall Creators Update, which brings Windows up to par with macOS and Linux's ability to use SSH natively.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

Apple just unveiled a red iPhone and iPhone 7 Plus, dubbed the iPhone 7 (PRODUCT)RED Special Edition, to commemorate the ongoing global fight against AIDS. Apple fans the world over are sure to swarm in and gobble up the initial stock shortly after the new color is released at 8:01 a.m. (PDT) on March 24, 2017, so we'll go over some tips to help you secure a red iPhone before it's sold out.

Kodi, formerly known as XBMC, is one of the most versatile media players available. With it, you can play virtually any internet and media file in a large variety of formats, and it can be used on practically every single operating system out there, including iOS 10. Kodi, an open-source software, was originally designed to connect to your TV so you could control your media from up to ten feet away, and the core functionality still shines today. All of this is what makes Kodi so popular today...

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

Gas stations may be convenient for travel snacks, but the cost of shopping there sure can add up. If you're looking for easy, on-the-go snacks that fit into your travel budget, look no further. We've got 12 kid-friendly, portable food ideas you can make before leaving on your journey. You'll be amazed by how much money and time you will save with these satisfying travel snacks.

At this point, you probably think that you've read everything there is to read about different ways to prepare eggs. There are the usual ways (scrambled, soft-boiled, hard-boiled/steamed/baked, sunny-side up, poached, the "overs") and the more unusual ways (in clouds, crispy poached, deviled, golden hard-boiled), but this way tops them all.

Fresh, homemade pasta definitely beats the dried stuff from the store. However, most of us aren't usually in the mood to knead dough for 10 minutes... or to clean up a sticky, doughy, floury mess afterward.

Windows 10 is the most cloud-oriented version of Windows to date—yet, while this means you get some nifty new features, it also means some of your personal data is being shared with Microsoft's servers.

You send out a lot of emails, but probably get very few responses. How can you be sure those emails are even opened?

Unless your work clothes require dry cleaning, you probably only go to the cleaner a few times a year. And for those few items in your closet for which you do, you have to then find the time and extra budget to make a trip all the way to the cleaners and back again. In the end, it can be quite the hassle.

You know what's awesome? You own a Nexus. That means, with Google's blessing, you have easier access and control over your device than other manufacturers allow. You can really dig in and do some interesting things if you root.

The airline is not your friend. It will do anything it can to gouge your dignity, time, and most of all, money. One of the biggest scams to get a few extra bucks out of you are those dreaded baggage fees. If the lines, security, "random" screenings, and unwanted fondling aren't bad enough, you have to pay them to check your bags (which, most of the time, is done poorly). Flying truly is the most inconvenient way to travel.

If you can't find the remote for your Android TV or Google TV, don't like using its voice control feature, are sick of using the directional pad to type, or can't get it to work at all, use your smartphone instead. Using your iPhone or Android phone as a virtual remote control can be more convenient, easier to use, and more helpful than the original remote, so it's definitely worth trying out.

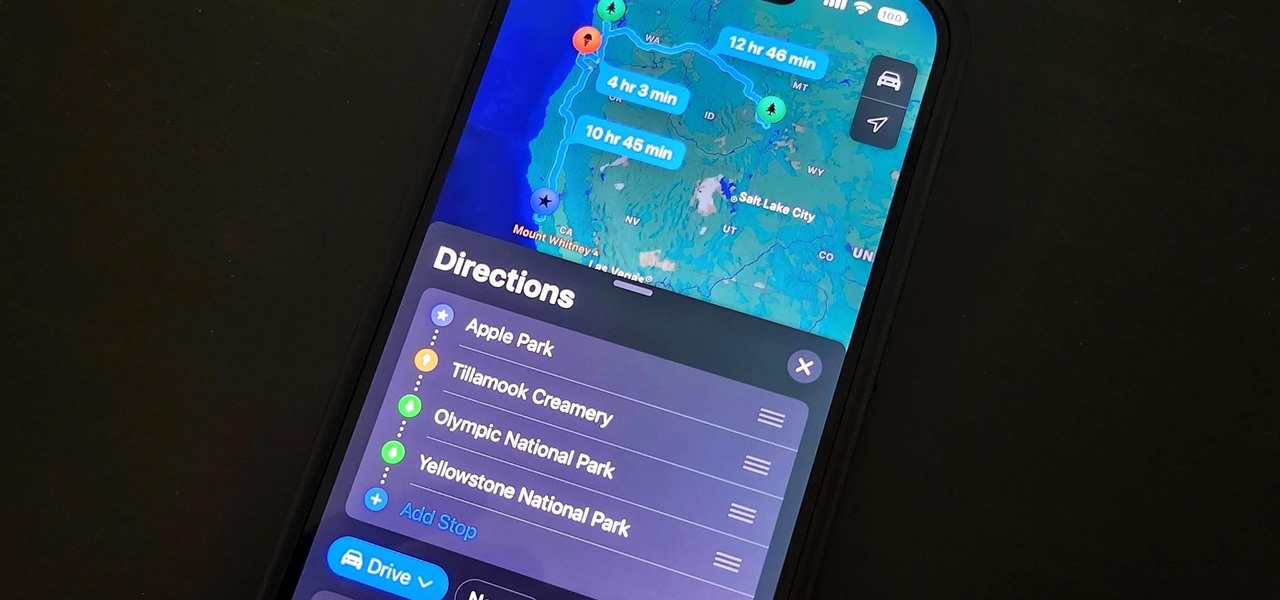
One thing Apple Maps always lacked was the ability to add stops along a route while planning a trip. Navigation would help you travel from the beginning location to the final destination, and the only places you could add between that were pit stops like banks and ATMs, coffee shops, convenience stores, eateries, fast food, gas stations, and parking lots. That all changes in Apple Maps' latest update.

When you need to drive somewhere unfamiliar, you probably use Apple Maps to get there if you're an iPhone user. But just getting there isn't enough sometimes. If you pull up to the location, and there's nowhere to park, it doesn't matter that you arrived on time since you'll be late trying to find somewhere to leave your car. That's where Apple's new Maps tool comes in handy.

While Apple's reputation for privacy and security is nearly unmatched, it'll never be perfect when Hey Siri is always listening. Aside from iOS devices, Hey Siri always listens for questions and commands on the HomePod and HomePod mini smart speakers. If you rarely use Hey Siri on those speakers, it's worth disabling the feature for some extra privacy.

Instead of using a single APK, YouTube Vanced recently started being distributed as a bundle that requires a third-party app to install. Some fans found this too difficult, so the Vanced developers decide to make the process easier.

When you don't have a steady cellular signal or immediate Wi-Fi access but need to communicate with others around you, you can set up an off-the-grid voice communications network using a Raspberry Pi and an Android app.

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you even more protection against online threats.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

Despite some of the biggest players in tech still lagging in terms of offering smartglasses options, there are nevertheless a number of smartglasses makers, including North and Vuzix, with consumer-grade smartglasses on the market right now.

UPDATE: The OnePlus 8 Pro has been released! Check it out on the official OnePlus website or read through the rumored specs we've left below for posterity.

You watched the live stream, pored over the specs, and are now super excited for the Google Pixel 4. But specs don't tell you everything. After using the Pixel 4 XL for over a week now, we've found several things you wouldn't know without getting your hands on the phone.