I rarely receive spam mail, but every now and then I’ll get an email from Cat Fancy Magazine. I’ve never read an issue of Cat Fancy Magazine or been to their website. Actually, I’m allergic to cats. So how did they manage to get my information?
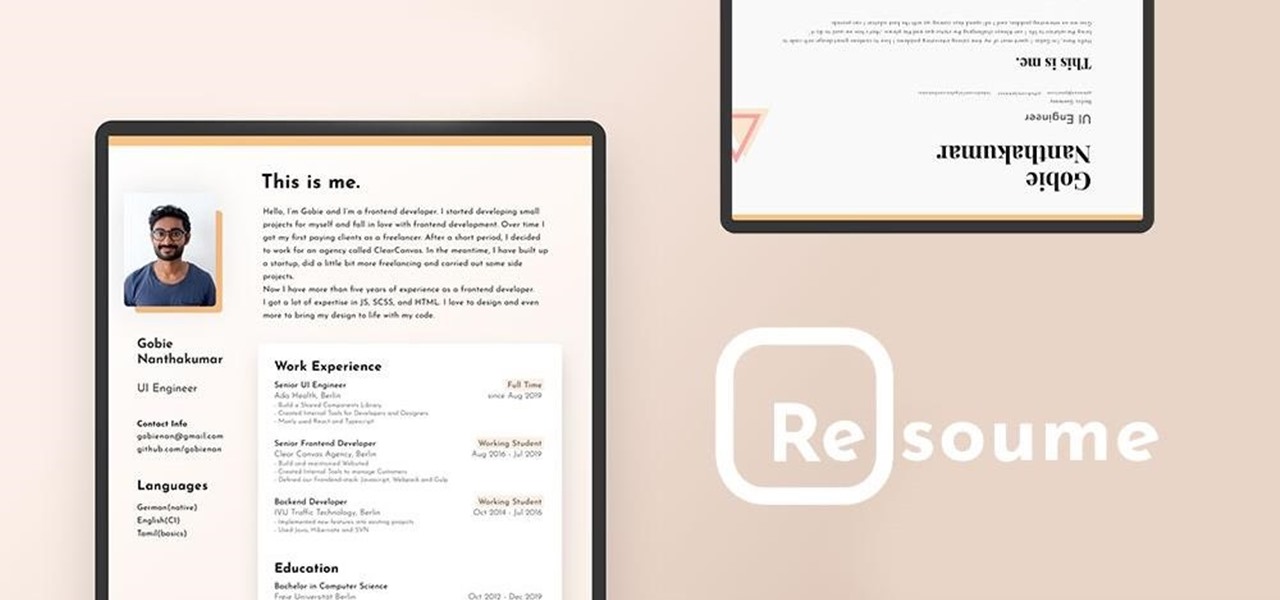
While the job market is slowly rebounding, competition remains fierce. Don't get caught behind when a new opportunity presents itself. Preparation is key to landing your new big job.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Apple Pay has been available to use in stores, as well as in select apps and websites, ever since its first appearance in iOS 8.1. Now, with iOS 12, there are currently 13 different iPhone models that support Apple Pay functionality without the use of an Apple Watch, and the list of partnered stores that accept Apple Pay has only grown. Here's our always-up-to-date list to keep you in the know.

There are a lot of manipulative people out there, but you don't have to let all of them push you around. It's time for the tables to turn.

Unwanted advertising is everywhere. Annoying pop-up ads, overly loud late night commercials, spam...it never ends. And before spam, there was junk mail. Junk mail is even worse because unlike TV commercials and internet ads, it's physical. You can't just delete or ignore it—and it's an awful waste of paper. So what can you do about it?

As government officials scramble to contain the new coronavirus outbreak with bans on large gatherings, travel restrictions, and school closures, the rest of us have to worry about how we're going to safely purchase water, toilet paper, groceries, and other household goods during the global COVID-19 pandemic.
Welcome back Hackers\Newbies!

Recycling your garbage is noble and, in many places, mandatory. But it also can be very confusing. This guide will clear up the rules.

The gig economy is thriving, and if you aren't already making money with your phone, you could be missing out on easy residual income. Some people just want extra cash, and some even manage to completely ditch the 9–5, enabling them to work at their own pace and set their own hours.

Give an 18-month-old a shoe, check back 10 minutes later, and it's a very big maybe he will have it on his foot. But give him your smartphone, and in a mere five minutes, he can take 100 pictures of the carpet, send weird messages, and delete essential apps. Imagine what your child could do if they were able to harness this technical aptitude and put it to good use — and they can, with learning apps.

Contrary to popular belief, augmented reality apps have been available for a while now. I remember using the Layar app (still available for iOS and Android) to explore nearby businesses and landmarks with varying success via an early-generation Android handset.

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

Next to spam calls, few things are more annoying than being inundated with spam, scam, and smishing texts. Your iPhone's Messages app should be a place for your friends and family to stay in touch, not a minefield of phishing attacks, malicious links, and viruses. Luckily, there are quite a few methods to block and report your way to a more spam-free iPhone.

Apple's latest big software update includes an entirely new Apple app, a controversial change in the TV app, better Siri control, an improved Shortcuts app, interesting Safari upgrades, Apple Music Sing, and more. Keep reading to see what iOS 16.2 has to offer your iPhone.

With all the time most of us spend on our phones each day, wouldn't it be great if we could get rewarded for our addiction? Well, we can, thanks to various iPhone apps out there that can help us make a quick buck, earn cash back, donate freebies to charity, get complimentary cryptocurrency or stock, and receive other types of rewards.

In a recent survey of more than 5000 UK jobseekers by TotalJobs.com, it was found that 60% spend less than two hours working on each application following a job search, all inclusive of the time it takes to write a CV and covering letter, and to prepare for an interview.

In this video, we learn tips on writing an email cover letter. First, when using "miss", write "ms". Also, make sure you use the correct grammar and the correct punctuation. Remember that this isn't an email to your friends, it's a professional email. Also, remember to use the last name, not the first name. You want to start off with an introductory sentence stating who you are and where you got that person's contact information from. Give why you want to work there, what department, and why ...

THC-Hydra is a remote dictionary attack tool from The Hacker?s Choice group. It?s a well made tool that supports a lot of protocols and options. The following protocols are supported: TELNET, FTP, HTTP, HTTPS, HTTP-PROXY, SMB, SMBNT, MS-SQL, MYSQL, REXEC, RSH, RLOGIN, CVS, SNMP, SMTP-AUTH, SOCKS5, VNC, POP3, IMAP, NNTP, PCNFS, ICQ, SAP/R3, LDAP2, LDAP3, Postgres, Teamspeak, Cisco auth, Cisco enable, LDAP2, Cisco AAA. Audit remote password using THC-Hydra.

Writers room is great for the new young writer who is just looking for some good feedback and guidance. Go to the BBC writers room. They can read your scripts and pieces for you to help you out and give you good feedback. Take a look.

White criminal Conrad Zdzierak has committed the ultimate crime of racial stereotyping, plus multiple counts of aggravated robbery after robbing four banks and a CVS pharmacy. The robberies took place on April 9th of this year, but Zdzierak wasn't caught until now, thanks to an incredibly realistic, $650 silicon mask named “The Player”.

Tower defense games have taught us little. We already knew that defending castles from baddies was fun and that legions of weenies are the key to success in most real-time strategy situations. What other insights have they to offer?

This is one of my previous posts that was initially rejected by WHT. So I'll post it here:

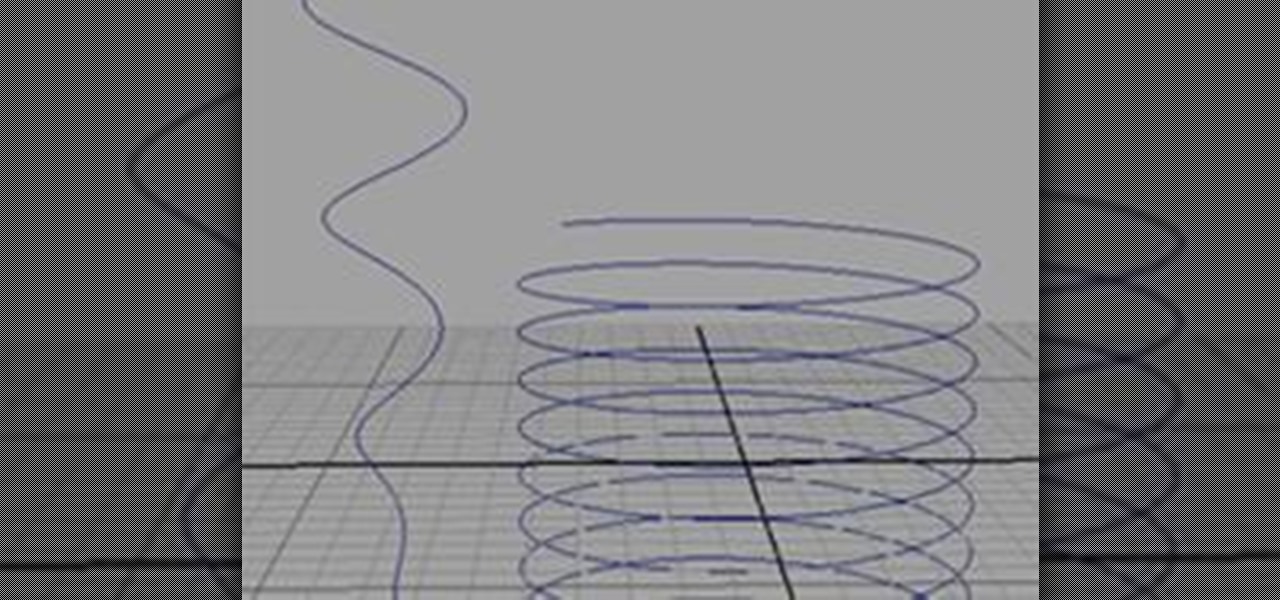
There are several ways you can go about creating your NURBS helix curve in Maya; I will demonstrate the two easiest ones.

Watch enough Glee and Buffy's Once More, With Feeling and it will never fail to instill the urge to do something stupid in public. And hey, what better way to do this than to drag others down with you? Welcome to the world of flash mobs, and in just a few simple steps you too could be arrested!

Backing up your files is a requirement in today's world of tech. In an instant, your storage device can fail. This is an unacceptable situation that should never happen to anyone. Storage is cheap, and backups are easier than ever to perform. Most of the time, this can be completely automated, so you can just set it and forget it. Today, Null Byte will be covering how we can automatically, and efficiently back up our data across all OS platforms, while giving a few alternatives to the built-i...

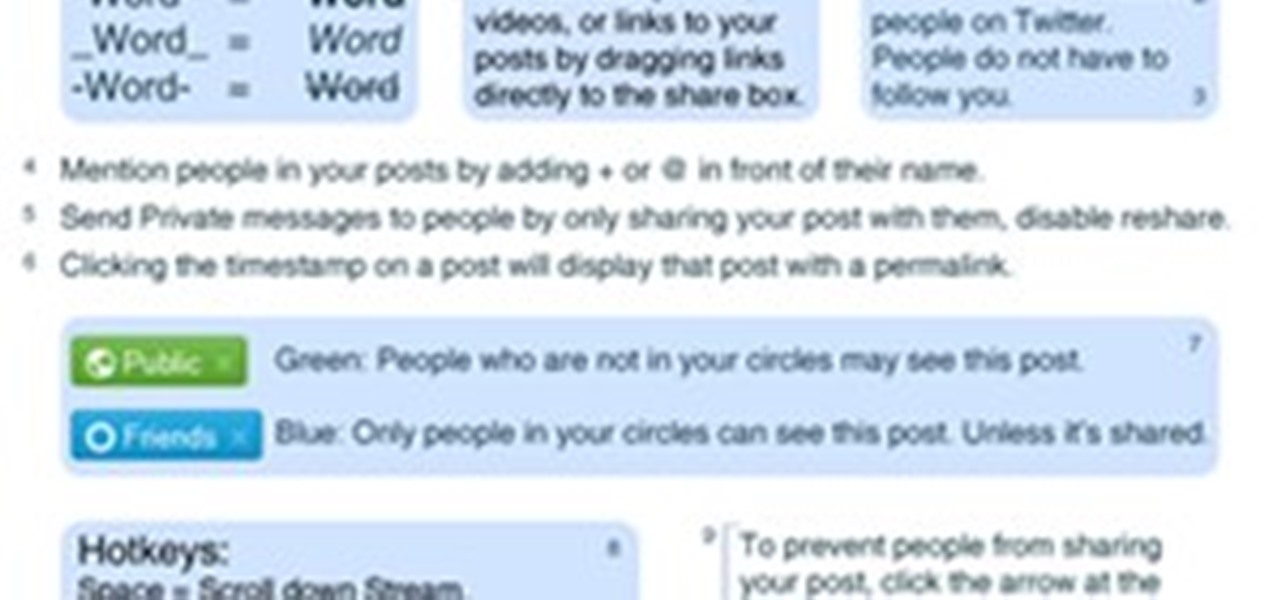
With the Google+ team members being generous and free-flowing with advice on some of the more advanced features of Google+, we'll be publishing a weekly summary of the latest pro tips. Chances are, if you've been following the Google+ team members, you've seen some of these already but you don't have them all in one handy place.

Motion trails in Autodesk Maya can be very handy at times when animating your scene. Keying a bone/joint or other object every so many frames can take up quite a bit of time and can sometimes be a big hassle, too. I have found many times when I could have really used one. I also don't like to search the Internet with a question and not find an answer (at least, without paying for it). So in this how-to article, I will demonstrate going about creating a simple (or complex) motion trail to make...

The last few months of WikiLeaks controversy has surely peaked your interest, but when viewing the WikiLeaks site, finding what you want is quite a hard task.