Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

If you'd like to have access to all your files at home without the hassle of spending money on expensive file hosting services or installing foreign software on your computer that could potentially harm it? Well Google has the answer for you, taking over the world one more computer at a time! In this video you will learn how to use your Gmail account and a Gmail Drive shell Extension to gain access to your files from any computer regardless of location!
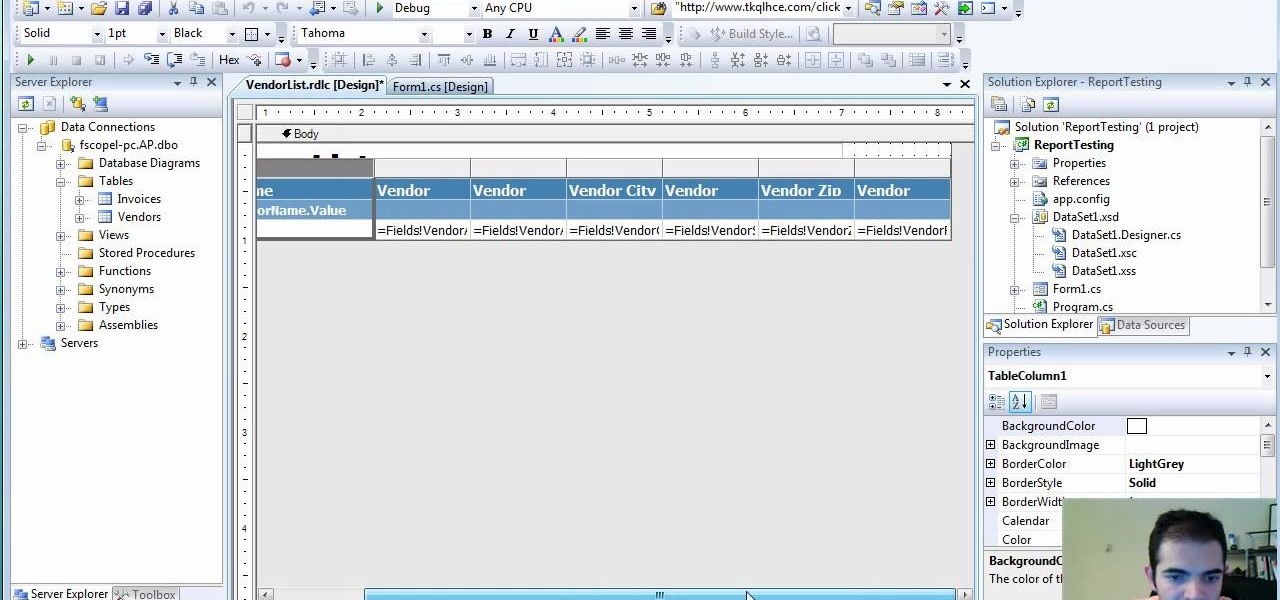
If you're not sure about creating reports in Visual Studio, this two-part video will cover the entire process. This assumes that you already know a few things in Microsoft Visual Studio and the C# programming language. So, if you're not a beginner and still need help to create reports from data in the SQL Server, this is how you do it. Also, learn a quick and easy way to pass parameters to reports in C#.

Welcome to a tennis lesson from FuzzyYellowBalls, the the best place to learn how to play tennis online. Our free video tennis lessons teach you how to play the game in a new way that combines technical analysis, visual learning, and step-by-step progressions.

How to Watch Hulu on your Xbox 360. The problem is HULU doesn't look good on some old PCs. Fix this by running it on your TV or projector. This uses the program PlayOn to run Hulu through your XBOX 360. This will tie it into your Media Center. This will make YouTube, Hulu and Netflix on your XBOX video game console. Go to Video Library and access you PlayOn server.

In this tutorial Mike Lively of Northern Kentucky University shows you how to get started with Wireshark. Wireshark is a network protocol analyzer for Unix and Windows. It is used for network troubleshooting, analysis, software and communications protocol development.

In this video tutorial, Chris Pels shows how to create a custom profile provider to store and retrieve data associated with a user profile in SQL Server tables separate from the standard ASP.NET membership provider’s aspnet_Profile table. The principles covered in this video will apply to creating profile providers for other databases like Access and Oracle. After learning how to create the custom profile provider we learn how to install the provider in a web site and see a demonstration of l...

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

After receiving many requests for the feature, Signal introduced read receipts last year to its mobile apps. However, some users don't like the idea other people knowing when they've read messages. Luckily, Signal lets you disable this feature and reclaim a little privacy.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

For years, PuTTy has reigned supreme as the way to establish a Secure Shell (SSH) connection. However, those days are numbered with the addition of the OpenSSH server and client in the Windows 10 Fall Creators Update, which brings Windows up to par with macOS and Linux's ability to use SSH natively.

Internet Relay Chat, or IRC, is one of the most popular chat protocols on the internet. The technology can be connected to the Tor network to create an anonymous and secure chatroom — without the use of public IP addresses.

If you maintain a digital library of your favorite movies, Plex is the perfect solution for bridging the gap between your computer and your mobile device. All you have to do is install the server program on your Mac or PC and point it to the folder where you store your movies, then you can use the Plex app for Android or iOS to watch the movies on your phone or tablet.

Supercell's highly anticipated Brawl Stars has soft launched in Canada, with gamers worldwide salivating at the prospect of a full debut around the corner. Unbeknownst to many, this game can be played on your iPhone right now, regardless of where you live.

Despite a round of updates to Pokémon GO that patched and eliminated location spoofing, the game still has a difficult time dealing with the most hardcore cheaters. Like weeds on a grassy lawn, third-party bot makers still remain the biggest thorn in Niantic's side and continue to thrive despite the developer's best efforts to root them out. While the latest updates have blocked users from running modded versions of the game, like Pokemon GO++, that feature built-in joysticks to move your pla...

Reddit user Mr. Squishy recreated the entire Game Boy Pokémon Red Version game in Vanilla Minecraft, i.e., a Minecraft server without gameplay modifications. Instead of using mods, he used 357,000 commands blocks—blocks that execute commands in the popular sandbox game. How long did it take him? Almost two years.

The Stagefright exploit, which allowed for malicious code to be embedded in files on your device, is now very real in the form of Metaphor. Developed by software research company NorthBit, Metaphor is their implementation of exploits to the Stagefright library, and when executed, can access and control data on your device.

Alright, this will be my first tutorial in C. Note that this guide is written for Linux.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

Hello fellow Null-Byters! This is my first post so please be respectful and constructed criticism is much appreciated. I am no professional, however I believe that it is important to understand technologies before you go poking at them and trying to break them, I therefore decided to make this series. In this "tutorial" we are going to setup a web server with php and mysql. I will be doing this with a raspberry pi because a pi is quite versatile.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

Thanks to the internet and its increasingly lack of privacy, secrets don't even seem safe in our own homes anymore. So how do you hide your secrets, stash your cash, or keep your valuable jewelry out of sight where no one can find it? Well, the answer might be right above you... if you're standing under the threshold of a door, that is.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

A recently discovered bug in iOS 8's Mail app by Jan Soucek can allow the maliciously-minded to quite easily phish your iCloud password without you ever thinking something has gone awry. Using a bug that allows remote HTML content to be loaded in place of the original email content, unsuspecting victims would be prompted for iCloud credentials in a popup that resembles the native one found on iOS.

If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achievable. Plus, we've got 50 promo codes to give away for a free year of service!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Ah, the art of the April Fool's Day prank. It has to walk a fine line: not enough prankish flair and the joke falls flat. If it's too mean, then you've just bummed everybody out.

It's really amazing how much you can do with root access on an Android device. From various themes to porting exclusive funtionality from other devices, the power of Superuser privileges is truly awesome.

When browsing the web, you may not be quite as anonymous as you think, especially if you are using public WiFi. The easiest way to stay as anonymous and safe as you are going to get, is to use a VPN (there are a number of great free ones). In this tutorial, we will show you how to set up a VPN on Android, and how this protects you.

Have you ever been called a "noob" or "eZ" after some person kills you? have you ever said "you hack" or "you suck" after getting your butt kicked by another player? this wont ever have to happen again. It is actually possible to be very good at PvP in Minecraft, and you can also be good at it. Now, it is your turn to win in every battle you fight in Minecraft PvP.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

For a photo- and video-sharing app based around privacy, Snapchat sure has a lot of security holes floating around. At one time, you were able to take screenshots of Snapchats in iOS 7 without the sender knowing, which is something that you can still do on rooted Android devices.

In Minecraft, many people enjoy "Faction" aka "Raiding" multiplayer servers for their unique gameplay and survival aspect. Plus, it's always fun when you find a chest full of somebody else's free stuff.

Creating a class in Black Ops 2 is kind of like an art form. Every player has an insane amount of options for creating a character for all sorts of situations. Combining perks, with secondary weapons, and attachments allows for a wide range of killing options. But in order to unlock a lot of these perks and attachments, you need to gain XP. Gaining XP and collecting tokens is the lifeblood of the online gaming experience.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

If you have an iPhone or an iPod Touch then you probably think that the only places you can listen to your MP3 files are on your laptop, your i-gadget of choice, and your car. But in reality anything that you can groove to on your iPhone or iPod Touch can be listened to - and transferred to - your PlayStation 3.