Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

While the PlayStation 3 is an awesome gaming console and the iPhone is an awesome smartphone, Apple and Sony have made two devices (that could be perfect for each other) nearly incompatible. Truth be told, this is more Apple's fault than Sony's, but we'll get into that later.

Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft Security Bulletins.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

If you just got a new Android mobile phone, then chances are, the first thing you're going to want to set up is your email account, so you have instant access to your emails all the time, everywhere and anywhere. Setting up your specific email account or accounts is actually not hard. Best Buy has answers. The Best Buy Mobile team explains how simple it is to set up an email account on an Android cell phone.

This video tutorial shows how to open a port for torrent downloading on your computer. Click Start menu, type cmd command in Search area. In cmd window type ipconfig and press Enter. Remember or write down your IP adress. Type exit and press Enter to close cmd window.

In this video you will learn how to get past website blocks on your school network. Some school computers have command prompts blocked. If this is the case then you will want to open a notepad. In the notepad type command, then save as something school related, making sure the file name ends with .bat. Do not save it on the desktop, but rather in a folder deeper on the unit. Once you've saved it, make sure no one is looking, then open the file. It will bring up a blank black window. In the bl...

Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords.

Clinton Kelly, the lifestyle expert, shows the right way to ‘Set your Buffet Table’ for a buffet party, in this video. He suggests that all the serving dishes and utensils are laid on the buffet table, the night before the party. This will throw some light and give ideas as to how to place the dishes on the table. You could place the plates on one side of the table, the food at the center and the napkins to the other side. You should also decide the heights of the various serving platters, co...

1. The ingredients (servers 2 or 3)for this are: Rice - 1 1/2 US cup, Water - 1 2/3 US cup (400 ml), Kombu kelp (spice). For dressing, Vinegar - 1/5 US cup (43 ml), Sugar - 2 tablespoon, Salt - 1/2 tablespoon.

Know which Indian entrees are low-calorie and which are diet busters. Step 1: Forget the fried stuff

You can eat Italian and still stick to your diet. Just follow these guidelines. Step 1: Skip the garlic

Shed extra weight safely and effectively with these tips. You Will Need

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a motorcycle camera mount for under five bucks.

Watch this demonstration on Spotlight on SQL Server Enterprise by Quest Software. Spotlight on SQL Server Enterprise is a part of the Quest Management Suite for SQL Server as well as standalone offering. This demonstration shows the use of Spotlight on SQL Server Enterprise within the Management Suite

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.

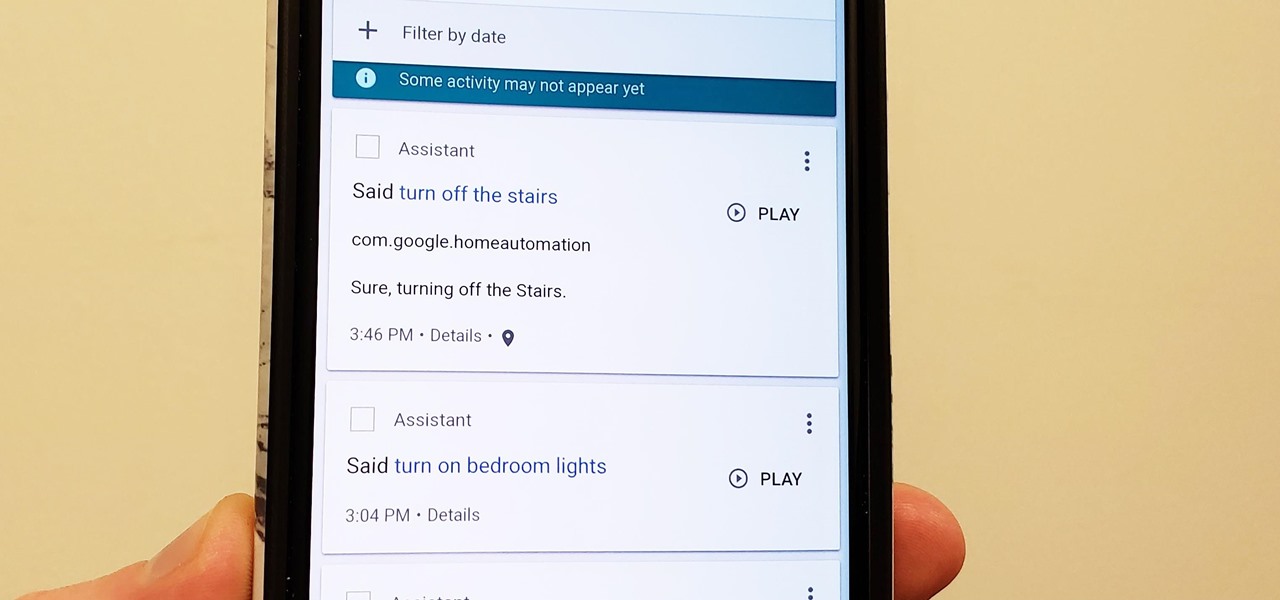
Privacy is a hot topic. In the wake of Facebook's data scandal, many want to safeguard their personal info. On the other hand, we all gain a certain amount of convenience by using services administered by huge companies like Google, Facebook, and Twitter. Google Assistant collects plenty of data, but you can easily check what is stored and delete items at will.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

It seems like there's a cyber security scare every day. Consumers are growing increasingly concerned about the safety of their accounts, and they have reason to be. Hackers will maliciously attack you anywhere — and we mean anywhere — they can to get your private information.

Not everyone digs Siri. Some of you probably can't live without the personal assistant on your iPhone, and some of you probably never even use it — and likely never will. If you fall into the latter category of iPhone users, you can simply disable the feature altogether, which will prevent accidentally triggering her or him anymore and will keep your iPhone nice and secure overall.

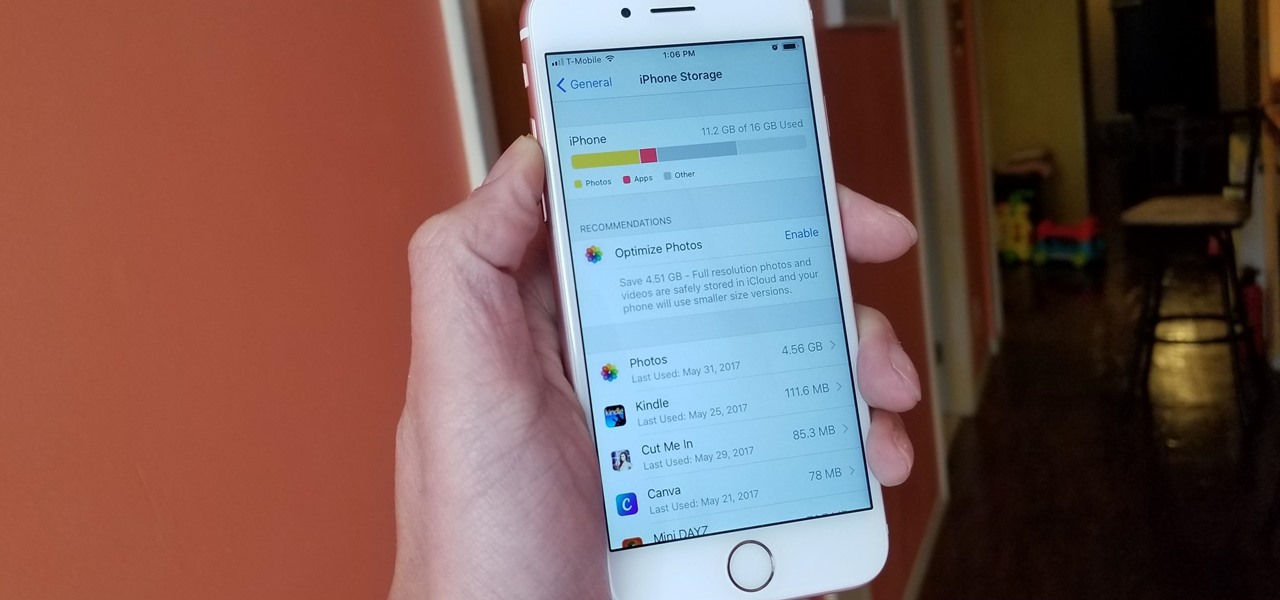
When Apple revamped the storage management system in iOS 11, it built in a feature that lets you free up space on your iPhone in a more efficient manner. The option allows you to remove an app while preserving its data and documents should you choose to reinstall it later — and it can even do so automatically for unused apps when you're running out of space.

With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years has sent shockwaves through the technology world.

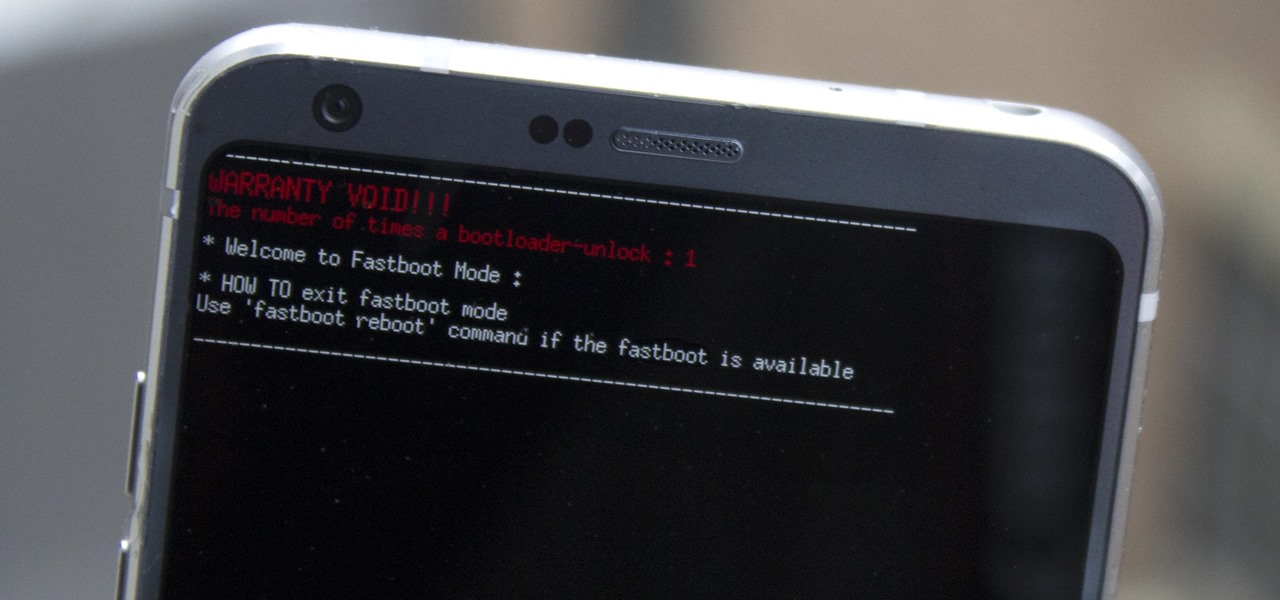
Preorders for the LG G6 have all been fulfilled, and the phone has been up for grabs at local cell phone providers for three weeks now. However, not every LG G6 was created and released equally. The T-Mobile variant of the LG G6 features an unlockable bootloader, while most other North American variants come with a tightly locked down bootloader, which effectively limits the full potential of your brand new fairly expensive phone.

Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS.

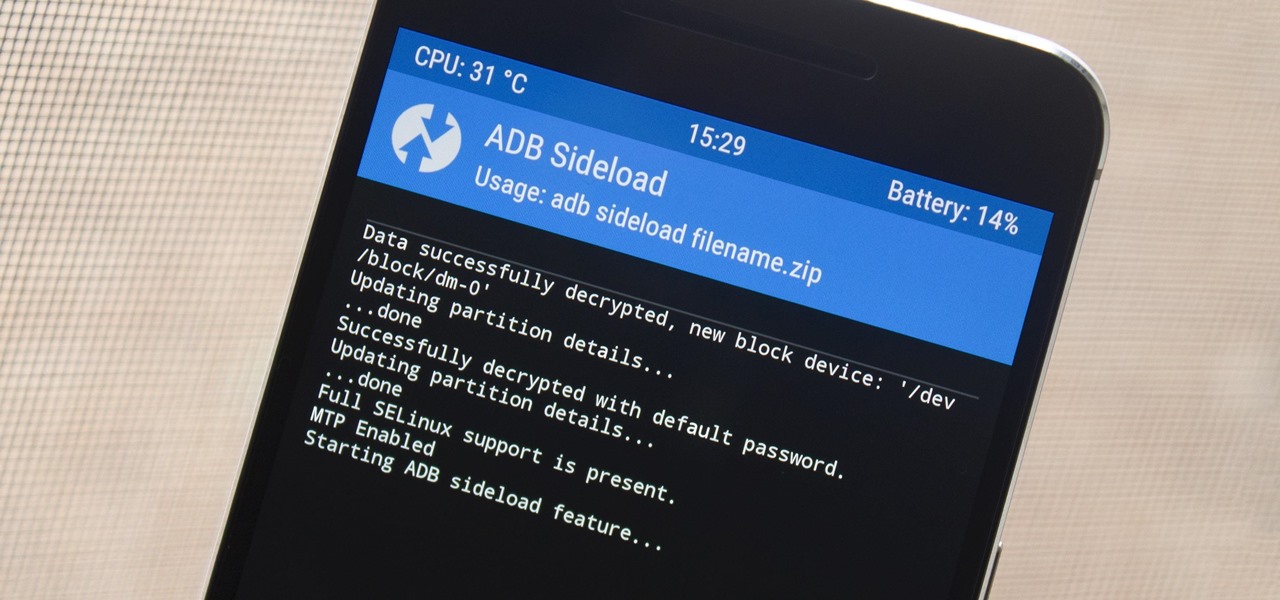
If you're one who likes to tinker with Android, TWRP is the first thing you should install. It replaces your phone's stock recovery mode interface and adds over a dozen advanced features to your device—most notably, the ability to flash ZIPs that can modify practically every aspect of your operating system. It's certainly one of the most powerful tools available for Android, and there's simply nothing capable of replacing it.

Cyanogen, Inc., the for-profit company that spun off from its CyanogenMod roots several years ago, has announced that they're shutting down all of their services. The company's impending demise shouldn't directly impact many Android users, but the announcement does have one major repercussion: The servers that used to host the popular CyanogenMod custom ROM have now been shut down.

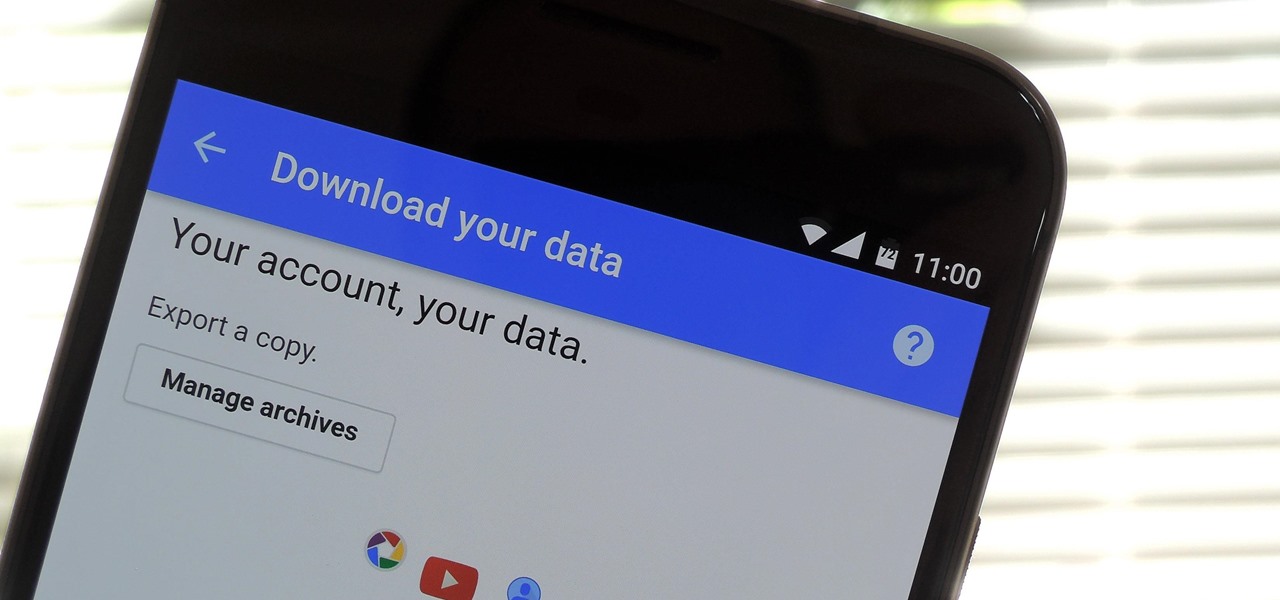
If you're an Android user, Google probably has almost your entire digital life stored on its servers. Family pictures are backed up on Google Photos, your e-book library resides with Google Play Books, videos are on YouTube, chat logs in Gmail and Hangouts, starred places and location history in Google Maps, and so much more.

Kryptowire, a company specializing in mobile security solutions, released a report on Tuesday, November 15 that exposed firmware in a number of Android devices that was collecting personally identifying information (PII) and uploading it to third-party servers without users' knowledge.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.