News: Kaspersky Offs Two Ransomware Strains
According to security firm Kaspersky Lab, CoinVault and Bitcryptor ransomware are officially dead.

According to security firm Kaspersky Lab, CoinVault and Bitcryptor ransomware are officially dead.

Recently the newly famous ProtonMail service was under attack by DDoS attack. This attack was believed to be the hacking group Armada Collective.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.
Well Welcome Back My Fellow Hackers. What is Slowhttptest? You may be asking. Slowhttptest is a Application Layer Denial of Service attack aka an attack on HTTP. You can read more about it here and also download it if you don't have Kali Linux. slowhttptest - Application Layer DoS attack simulator - Google Project Hosting.

Amazon is currently offering over $80 in free Android apps in the Amazon Appstore, but only for Friday and Saturday, so make sure to grab them quick before they all go back to normal price. Highlights include the Fleksy Keyboard (normally $3.99), Oxford Dictionary of English with Audio (normally $24.99), and EasyTether (normally $9.99).

Google's Chromecast streaming device is a marvel of functionality and form. Even with powerful features such as screen mirroring and collaborative party playlists, it's the device's idle screen that first catches the eyes of most folks.

Greetings, my friend. Welcome to Null Byte. I am Dr. Crashdump. Linux will be talked about a lot in Null Byte. It's used in most tutorials on this site, actually. You should learn how to use Linux as soon as possible, but where do you start? No worries. Let's figure that out.
For $100 each year (unless you used Faisal's workaround to save yourself twenty bucks), Amazon Prime membership gives you access to all the best that Amazon has to offer. From free 2-day shipping to Prime Instant Video, there's a lot to like about the service.

The new operating system for your Mac is here, and it looks fantastic—OS X Yosemite. At Apple's WWDC presentation, we were shown the new iOS-like aesthetics, as well as other awesome enhancements to the operating system. Improved Aesthetics

Even if your business is mostly online and computer related you will need paper, which in other hand will need classifier to be sorted out and easily accessed. The paperless office is as much of a myth as the paperless toilet, so accept it, if you are serious about business, you need paper. Important contracts between customers signed on papers, leaflets, reminders, advert previews, drafts for preview at the table. The paper is always used even in today highly computerized epoch.

It may be cheesy, but whipping out an origami flower while you're at the dinner table can really make someone's day, whether it's made out of a napkin, dollar bill, or burger wrapper. It's great for showing your waitress how much you appreciate the service, or for breaking the ice with your Valentine's Day date.
It seems that Facebook doesn't take rejection lightly. After being denied for a $3 billion buyout of Snapchat, Facebook-owned Instagram has updated their popular photo-sharing service with Instagram Direct—a new feature that allows users to send private photos/videos.

Spam emails are emails that are sent to you without your permission. They can quickly fill up your email account if you don't do anything about it. Each email server deals with spam in a different way. Gmail is good at separating the spam for you so that you can get rid of it more quickly. It is easy to delete the spam and if you want to take it a little farther, you can get some of the spam to stop coming all together.

Checking notifications from all of your social media accounts is half the fun of the Internet, but can become quite tedious—hopping from site to site can take up hours of your time, especially when you're running away from something (in my case, it was always homework/studying).

There are several ways to send pictures to others on your smartphone—picture message, email, Bluetooth, and even by bumping phones together. Now there's an even more unique way to transfer pictures from one Apple device to another—with sound. Chirp for iPad, iPhone, and iPod touch

A hidden feature residing in Mac OS X Mountain Lion is the ability to view and also reply to your friend's tweets through the Contacts application, previously known as Address Book. The only way to do this, though, is to provide your Twitter account login data to the Contacts app. To integrate your Twitter, just go to System Preferences, then click on Mail, Contacts & Calendars and choose Twitter. Put in your Twitter login information and then click on Update Contacts. Twitter will use your e...

If you have an iPhone or iPad, but use a Google account for most of your communication, syncing your contacts just got a lot easier. Google recently announced that they added CardDAV support, an open protocol that lets you seamlessly integrate Google Contacts into other services. Google states that "Syncing via CardDAV is only available over SSL for Apple devices on iOS version 5.0 and above." So, if you're running an older iOS version, you'll have to use Google Sync instead.

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...

As deeply as smartphones are integrated into our daily lives, it's no surprise that people are finding ways to use them to stay healthy. From detecting cancer and radiation to diagnosing STDs, phones have come a long way, baby.

A minigame we built with redstone! Video: .
If you've never done it before, making a podcast can be tricky, with multiple programs to use and multiple file types to deal with. But, this video series helps you through the complete process of creating a podcast, everything including recording, editing, images, exporting, converting, uploading, and finally… sharing. Watch this whole series to learn how to make podcasts using GarageBand, iWeb, iTunes, and Fugu.

In order to set up your email in Outlook Express IMAP, you will need open Outlook. In accounts, enter your user name in the box above: "for example John Smith". Switch the incoming mail server to IMAP. Fill in your server and outgoing mail SMTP.
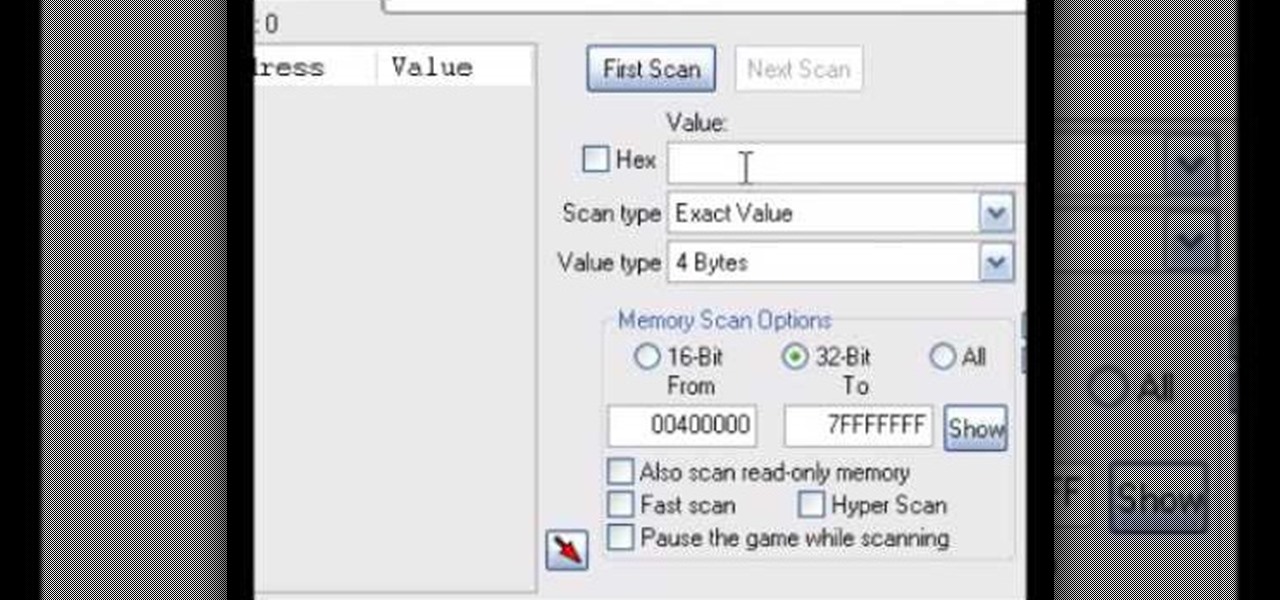
This tutorial shows you how you can use the free hacking program Cheat Engine to change both your speed and the stats for your weapons when playing World of Warcraft. The cheat works best when used on the live servers.

If you're new to DreamCoder for PostgreSQL, one of the first things you may want to know how to accomplish is to connect to a remote PostgreSQL database. Happily, this tutorial will walk you, step by step, through the process. To learn how to establish a connection between a given PostgreSQL database and the DreamCoder for PostgreSQL, take a look!
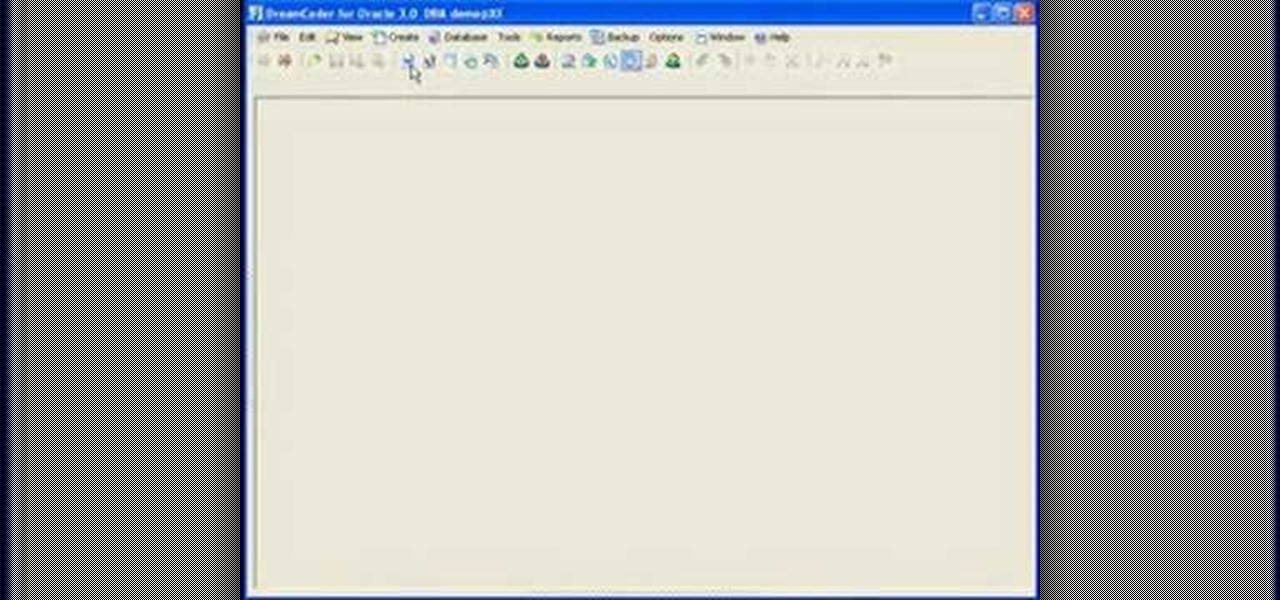
If you're new to DreamCoder for Oracle, one of the very first features you should acquaint yourself with is the export data process, which will permit you to backup your Oracle databases with ease. For step by step instructions, consult this how-to.

This video tutorial will walk you, step by step, through the process of importing data directly from an Excel document to a MySQL database server using the smart copy feature available in the DreamCoder for MySQL. For more information, press play!

How to summon Illidan in World of Warcraft. This only works on a private server.
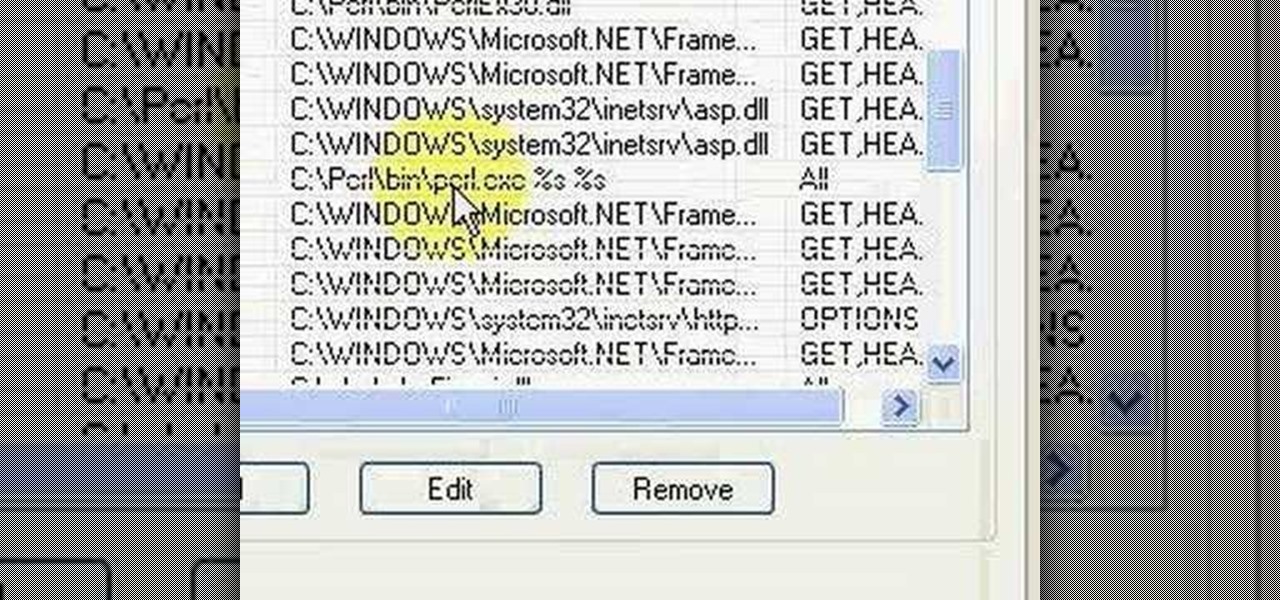
Brief 9-minute video demonstrates running "Hello World" Perl script on IIS and Apache Web Servers.

Welcome to Minecraft World! Check out our tutorials, post to the Inspiration board, and come play on our free server! HELLO, FELLOW MINECRAFTERS. Pmaguire here, bringing you my favorite idea for a competition so far! I hope that you will come to love it as much as I do! Well, starting off, as the title states, this week's Redstone Competition will be PvP Arenas! Except, not just ones where you physically fight. You have to have traps, things that make it hard to fight, and various ideas using...

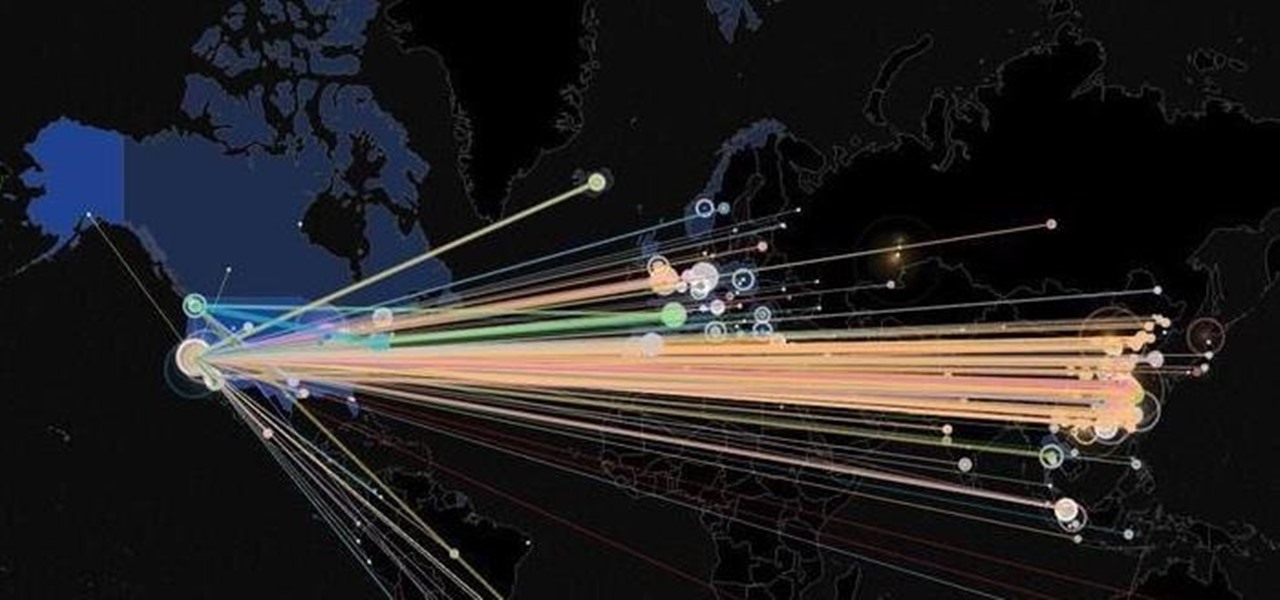
In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.
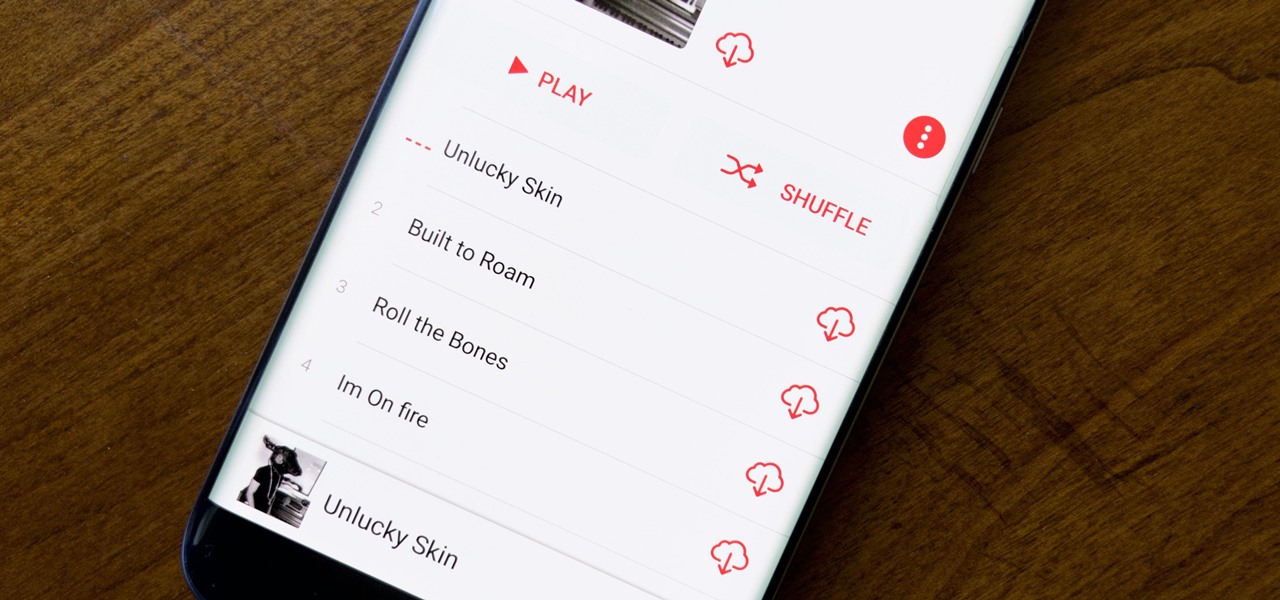
For most carriers, "unlimited" data plans aren't really unlimited, and they still cost more than data limited plans. So while subscribing to music streaming services and storing your own music library in the cloud may be more convenient, it may eat your data up like candy. To keep that from happening, try downloading tracks from Apple Music for offline playback.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Augmented and mixed reality developer Arvizio is working on a suite of software solutions for enterprises that will extend HoloLens capabilities as a full-fledged collaboration and conferencing tool. The company will demonstrate its Mixed Reality Studio suite to attendees at the Augmented World Expo, which begins later this month in Santa Clara, California.