If you ever need to make calls and/or send texts to the U.S. or Canada from abroad, or even just receive them from those locations, there's an easy way to do so without breaking the bank. In fact, it's free, and all you need is a smartphone, computer, and some free tools.

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

I'm sure that many of us have heard of that nasty Shellshock vulnerability, but not very many people know how to exploit it. Try these few tricks on vulnerable websites!

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

Welcome back, my novice hackers! This is the third installment of my Python scripting series. If you haven't read the previous two articles, take some time now to go back and read Part 1 and Part 2 before you proceed here.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

Welcome back, my hacker noviates! In a recent post, I introduced you to Shodan, the world's most dangerous search engine. Shodan crawls the globe from IP to IP address, attempting to pull the banners of each web-enabled device and server it finds.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

Remote desktop in windows is set up with these easy to follow steps. First go to your start menu this is in the bottom left corner of your desktop. In the start menu locate your control panel. In the control panel open up your systems folder. Once this is open click the remote tab at the top right of this folder. In this tab you will have the option to check “allow user to connect remotely to this computer.” From here press ok to exit out of the systems folder.Again click the start menu, navi...

In this tutorial series Mike Lively shows how to convert Wordpress into the Adobe Flex 3 application Flexpress.

Update: this article is referring to the 1.9 pre-release beta version, which is now commonly referred to as 0.1.9, released in October of 2011.

The automatic software update setting on your iPhone is nice, but you may not always want to install new iOS versions blindly. New updates could contain bugs and vulnerabilities, and your favorite features may even disappear. With the auto-update option turned off, you can manually download and install updates, but there are also hidden options to be more specific about how you want to do it.

Whether you're looking to add a substantial coding foundation to your hacking skill set or want to get a job in programming and development, knowing one or two programming languages just isn't going to cut it.

Since its release back in 1988, Microsoft Office has been the top client and server software suite for businesses around the world. Office's domination is thanks to both Microsoft's extraordinary foresight and their continual updates and innovations to ensure that companies always get what they need.

As we settle into our new normal, this extra time provides a perfect opportunity to learn new skills. Speaking a foreign language is a great way to expand your cultural boundaries while also training your brain. Not only will you pass the time more effectively, but you'll also be doing something positive for your health.

There's nothing quite as exciting in the beta testing world as a new update. Battling overloaded servers to download the latest update as fast as possible, just to scour through the new OS looking for the biggest features to the smallest changes. It was only Thursday that Apple seeded iOS 13.2 developer beta 2, so count us surprised that we get to experience today's release of developer beta 3 so soon.

Dark mode is finally rolling out for Gmail on Android. But this is a Google product, so you already know it'll be a while before the server-side update hits most devices. Sideloading the newest APK doesn't work, neither does switching accounts. But if you're rooted, you can enable dark mode by modifying a simple XML.

The software updates from Canadian smartglasses startup North keep coming, each with a unique new twist.

Although Niantic is already an augmented reality startup unicorn thanks to the success of Pokémon GO, the company has reportedly captured yet another round of funding.

Apple wastes no time with betas. Right on the heels of the official release of iOS 12.1, Apple released the first beta for iOS 12.1.1 to developers on Wednesday, Oct. 31. The update comes just one day after iOS 12.1, which itself was in beta development for 43 days this year. The denotation for 12.1.1 indicates it's a minor update over 12.1, and there are only a few things in its release notes.

For years, Skype has been synonymous with video calling and messaging. However, as the industry moved toward encryption and privacy, Skype usage was discouraged by experts due to its murky encryption. To combat this, Skype has introduced true end-to-end encryption.

Incognito Mode is a privacy feature that was popularized by Google Chrome, and it recently made its way to GBoard. Now it's coming to the YouTube app to help make your video watching experience truly private.

Another AR cloud savior has emerged this week in Fantasmo, a startup that wants to turn anyone with a smartphone into a cartographer for spatial maps.

If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning ethical hacking on a budget runs the "Re4son" Kali kernel and includes a compatible wireless network adapter and a USB Rubber Ducky.

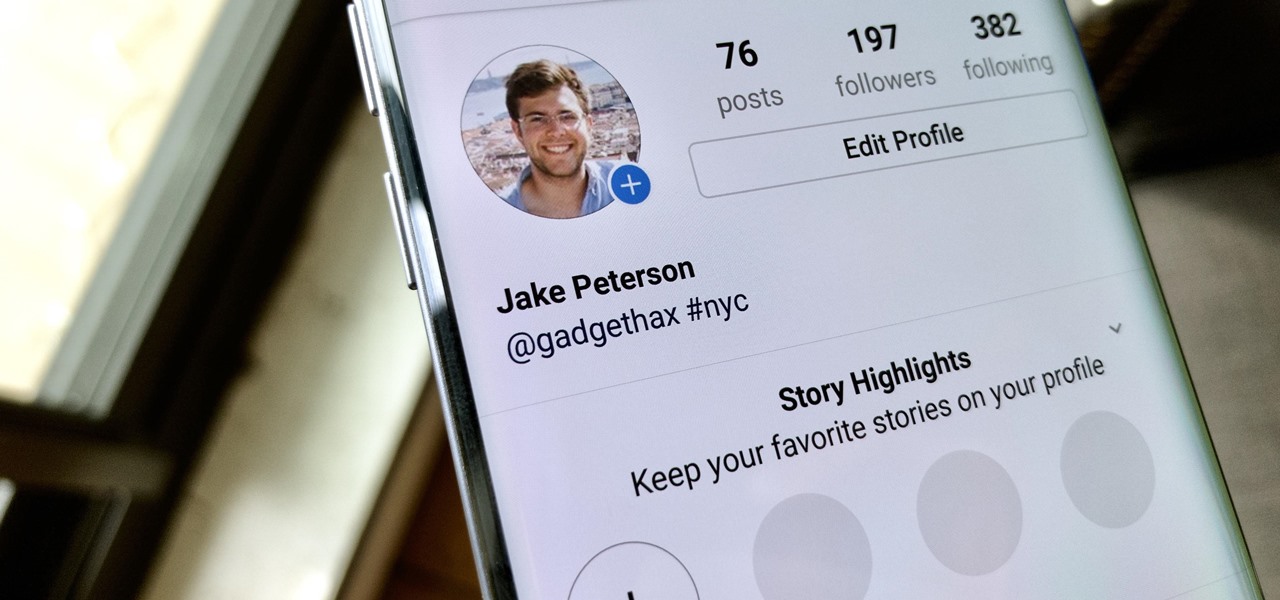
Your Instagram bio could always be used to link to other websites or profiles or just to show off your witty personality. Now, you also have the ability to use this section to tag other Instagram accounts as well as add tappable hashtags. Whether you want to link out to your best friend, company, or the latest trend in your city — if it has a profile name or tag, it can be in your bio.

Snap Inc.'s dedication to augmented reality has expanded the world lenses in Snapchat to our own Bitmojis. While it's great to see our characters interacting with real environments, we haven't seen them connect to other Bitmoji in AR space. That all changes with "3D Friendmojis," a lens from Snapchat that lets you stage scenes between your Bitmoji and a friend's.

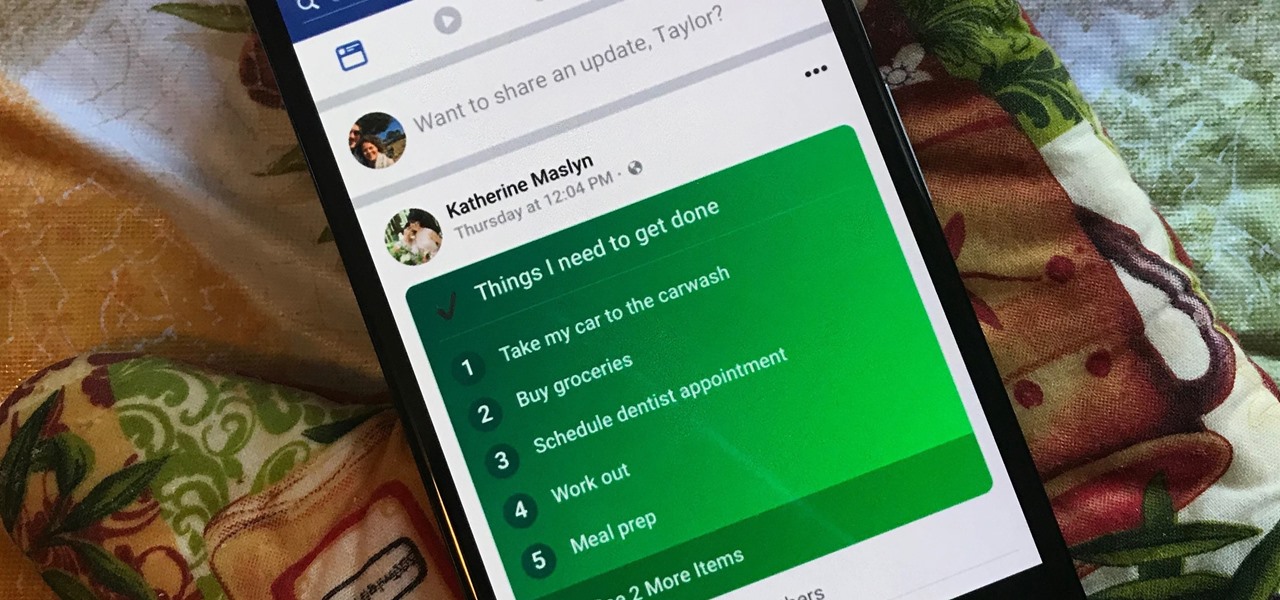
Facebook's status update box has received many new features over the years. You can go live, sell something, and even create a poll. But since all this was added, the status update box has been relatively stagnant. That's finally changing again with Facebook's newest addition: Lists.

Ports allow network and internet-connected devices to interact using specified channels. While servers with dedicated IP addresses can connect directly to the internet and make ports publicly available, a system behind a router on a local network may not be open to the rest of the web. To overcome the issue, port forwarding can be used to make these devices publicly accessible.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simple as downloading the Tor Browser.