While Apple's reputation for privacy and security is nearly unmatched, it'll never be perfect when Hey Siri is always listening. Aside from iOS devices, Hey Siri always listens for questions and commands on the HomePod and HomePod mini smart speakers. If you rarely use Hey Siri on those speakers, it's worth disabling the feature for some extra privacy.

Apple has an excellent reputation for its privacy and security policies. That said, it isn't a perfect reputation. Take Siri, for example. The helpful iOS assistant isn't just communicating with you — Apple saves and listens to a history of your Siri interactions. If you don't want Apple storing your Siri history forever, there's something you can do about it.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the outstanding feat of "magic" presented, we nevertheless hold fast to our survival-based grip on the truth: we just saw simply "can't be real."

Apple shocked us all yesterday when it released iOS 13.1 developer beta 1. It was an unprecedented move since iOS 13.0 is still in beta testing and since Apple has never pushed out a "point" beta release before the stable base version. And now, you can get your hands on iOS 13.1 for iPhone if you're on the public beta.

Apple's upcoming update for the iPhone, iOS 13, is introducing over 200 new features. Many of those were never formally announced, instead silently released in new updates to the beta. After eight developer beta cycles, we were anxiously awaiting the release of developer beta 9. What we got instead, however, was the first iOS 13.1 developer beta.

Beta testing certainly has its perks. While you do need to deal with bugs, you're introduced to new features before the general community. And if we're talking iPhones, there are over 200 new features in iOS 13 beta. If you're already on board with iOS 13 public beta 6 for iPhone, you can get an upgrade on that firmware as Apple just released public beta 7 today.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

I noticed the neon yellow sign at the new location of Pho Bar in Chinatown right away. The sweeping cursive yellow letters spell out "Crazy Rich Broth"; the same phrase printed on the back of servers' shirts. It's the kind of minimalist but colorful design feature that is especially popular on Instagram at the moment — shots of patrons in front of a glowing sign.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2017 selection of hacker holiday gifts — just in time for Christmas.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

Smartphone manufacturers do their best to keep you tied down to their ecosystem, but the reality is that there's not much keeping you from switching. Transfer some files, install a few apps here and there, and all of a sudden, you're knee-deep in a new operating system.

Brand loyalty is one of the main factors behind our decision to choose a particular mobile device, but it doesn't have to be the entire equation. Educated consumers know that certain devices simply fit their budget and usage better than others, which means you can't always let a logo dictate what kind of phone or tablet you buy.
Welcome back Hackers\Newbies!

When I got my first smartphone, it didn't take long before my friends and I created a game that we liked to call "Paste-Send." You see, instead of having to use T9 to type out text messages, the touch-based interface made copying and pasting incredibly easy. So that meant we could copy a piece of text, then paste it into text messages in rapid succession to text bomb the annoyed recipient. It was all in good fun, of course, and it usually evoked a stream of swear words from the guy on the oth...

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

Notch loves Halloween. He must, because he keeps putting scarier and scarier things into Minecraft around Halloween time!

Like theme music, I always feel that I need more fog in my life. Fog can be useful for many reasons—warding off smaller siblings from your bedroom, keeping curious hands out of your cupboard, and tricking your friends into thinking there's something horribly wrong with their vehicle. So, today we'll be making a very simple fog machine for small scale applications.

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

As if teasing its own smartglasses weren't enough, augmented reality gaming developer Niantic gave gamers a glimpse of how 5G speeds can revolutionize how they play mobile games in the near future.

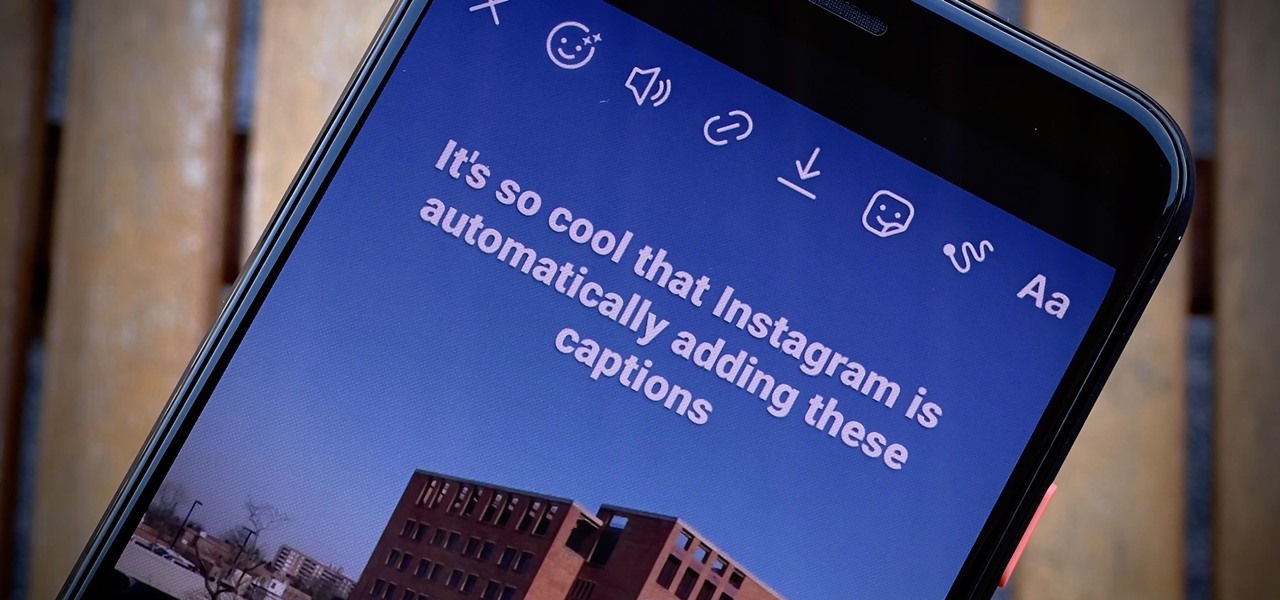
When creating video content for social media, such as a story on Instagram, it's common practice to add captions or subtitles to the post so that people can watch it wherever they are on silent. Doing this by hand is time-consuming and frustrating, but Instagram has a solution: a feature to add automatically-generated captions to any story you make from your iPhone or Android phone.

Your sensitive personal data should be strongly protected, and it's never more vulnerable than when you are online. The internet connection is a prime avenue of exposure, and email is one of the least secure forms of communication. Fortunately, there is an easy solution to both of those problems.

We all know that using a VPN not only has a ton of benefits but is essential in our digital age. But did you know that you can get access to your own industry-leading VPN for life with one one-time payment? Even better, we've found an amazing deal on one right now: for a limited time, a YoData VPN: Lifetime Subscription is on sale for just $17.99. That's 69% off the regular price of $59.

Amazon Web Services (AWS) is the premier on-demand cloud computing platform. Offering a wide range of APIs to companies, governments, and individuals on a pay-as-you-go basis, this Amazon subsidiary pulled in over $35 billion in revenue in 2019 alone.

Now that more people are working from home on unsecured networks and personal devices, hackers are having a field day accessing everything from private browsing histories to personal banking information. A virtual private network (VPN) is the first and most important line of defense when it comes to protecting all of your devices from digital intrusions, but not all VPNs are created equal.

Regardless of whether you're an aspiring or established coding pro, knowing just one or two programming languages and platforms is no longer sufficient if you want to be truly competitive in an increasingly popular and lucrative field. But before you spend an excessive amount of time mastering six new platforms, do yourself a favor and master Linux.

With millions of people working from home as a result of the coronavirus outbreak, hacking is on the rise. Nefarious black hats are taking advantage of the fact that workers have been forced to abandon their secure office networks in favor of home wireless connections. And white hats are spending even more time at home trying to be the next great ethical hacker.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.