So, you're scanning the internet for some cool articles to read during your lunch break and you come across something pretty interesting—"The 50 Most Incredible Things Every Person with a Brain Should Know." That sounds interesting, so you click, and boom, you are hit with the utterly obnoxious Page 1 of 50. Really?

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...
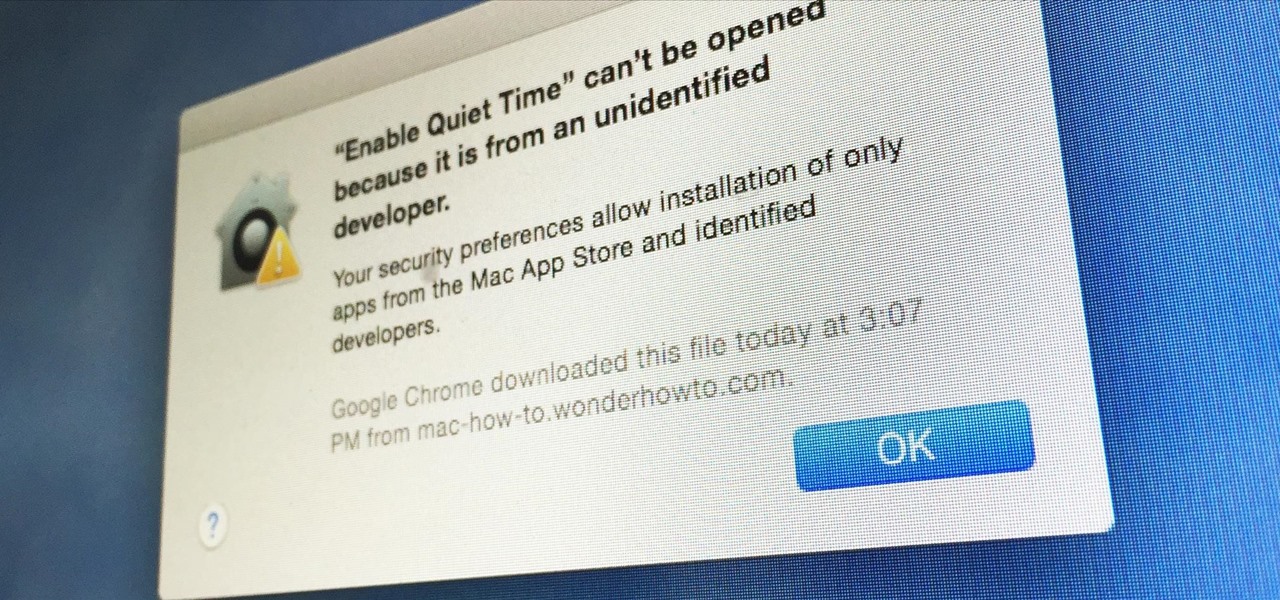
Apple has a built-in way to protect you from opening up potentially malicious apps on your computer in Mac OS X Lion, Mountain Lion, Mavericks, Yosemite, El Capitan, and macOS Sierra. This setting, named Gatekeeper, will never stop you from installing apps from the Mac App Store, but it could from anywhere else. If it's an app you're sure you want to install on your system, here's how to do it.

Ah, the age-old problem of sharing pictures with friends and family. Ten years ago, the best method available to us was passing around duplicate photos printed out at the local drug store. As easy as smartphones have made this act, you'd think we'd be satisfied by now.
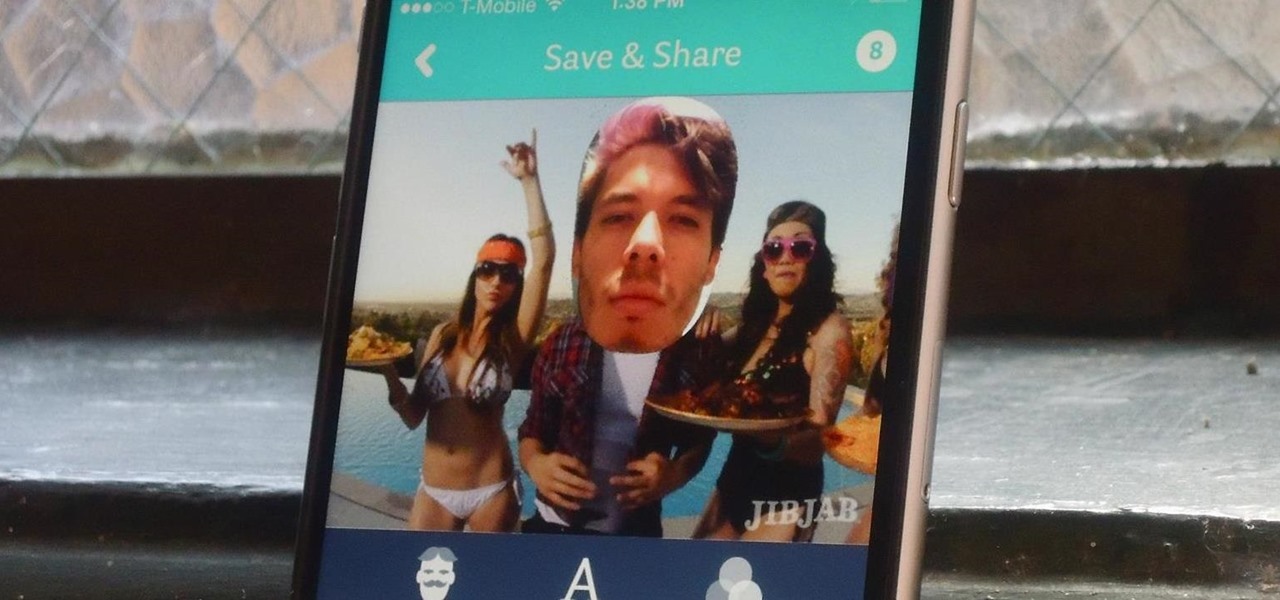
JibJab may not ring the bell, but you've probably seen one of their personalized videos. Using your own images, JibJab will place you first-hand into silly and usually musically-inspired videos that you can view online. Currently in beta, JibJib has made it's way to iOS in the form of personalized GIF creation. And if you're wondering, "why the hell would I want this", trust me, you'll love creating GIFs starring your and your friend's faces. Check out the guide below to get the app installed...

Minor mishaps occur all the time in the kitchen, whether you cut your finger while dicing an onion, scorched your hand in a grease fire, or burned the roof of your mouth because you were to eager to taste-test your killer pasta sauce.

Tired of playing old-school Game Boy Advance, Game Boy Color, Nintendo, and Nintendo DS games on your iPhone? We've got another retro video game system for you to add to your arsenal of emulators—Super Nintendo.

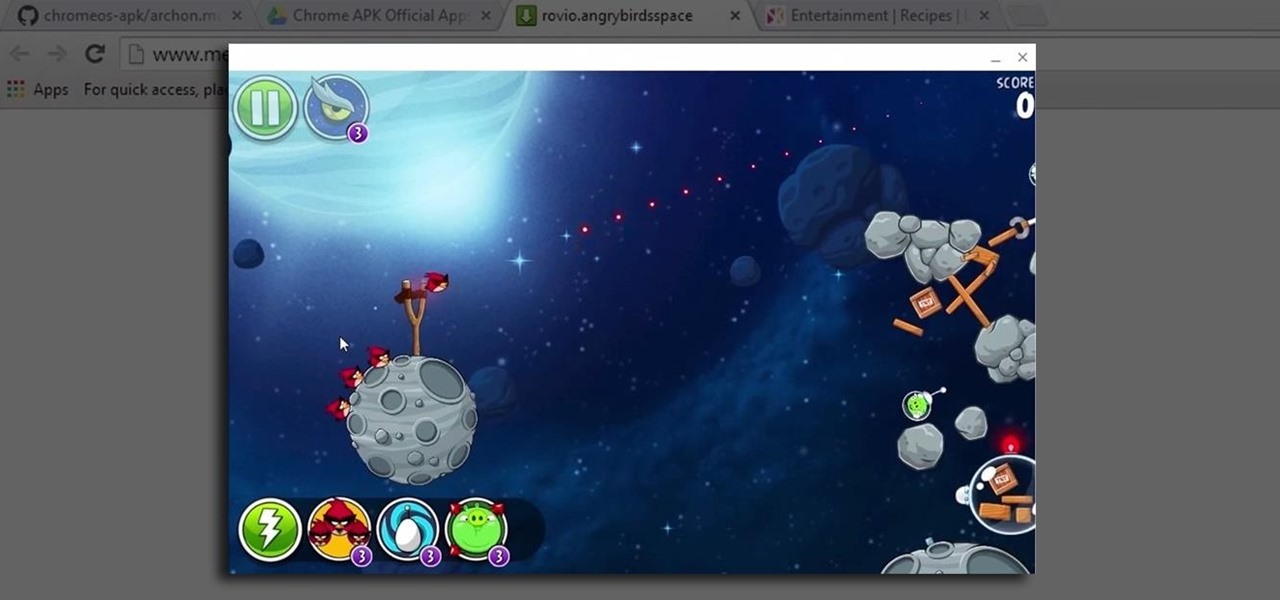
When Google announced that it would begin supporting Android apps on its own Chrome OS, it was great news for all the folks with Chromebooks. But, as that operating system only makes up about 0.2% of the PC and laptop market share, most of us were out of luck.

Keeping data private is vital in the days of smartphones and the free-floating information they carry. Justin wrote a guide on many of the deeply hidden and sometimes concerning privacy settings in iOS 7. Now we're back to cover some of the new (and old) privacy settings in iOS 8 that you need to address right now.

If you have a custom recovery installed on your Nexus 5, you're able to flash custom ROMs and lots of other cool Gadget Hacks. But when it comes time to receive and Over-the-Air (OTA) update directly from Google, having a custom recovery installed can be a fairly big hindrance—and for the upcoming Android L release, you're going to want to alleviate that.

When Android 4.4 was released, the massive changelog led to some awesome new features getting lost in the virtually endless list of new tweaks. One such change was the ability to set a default text messaging app, which streamlined the existing process of installing a third-party SMS client.

It's really amazing how much you can do with root access on an Android device. From various themes to porting exclusive funtionality from other devices, the power of Superuser privileges is truly awesome.

Pushbullet is one of those apps that helps separate Android from its competition. By pushing the boundaries of cross-platform data syncing and file sharing, the service truly demonstrates how flexible and robust the world's leading mobile operating system can be.

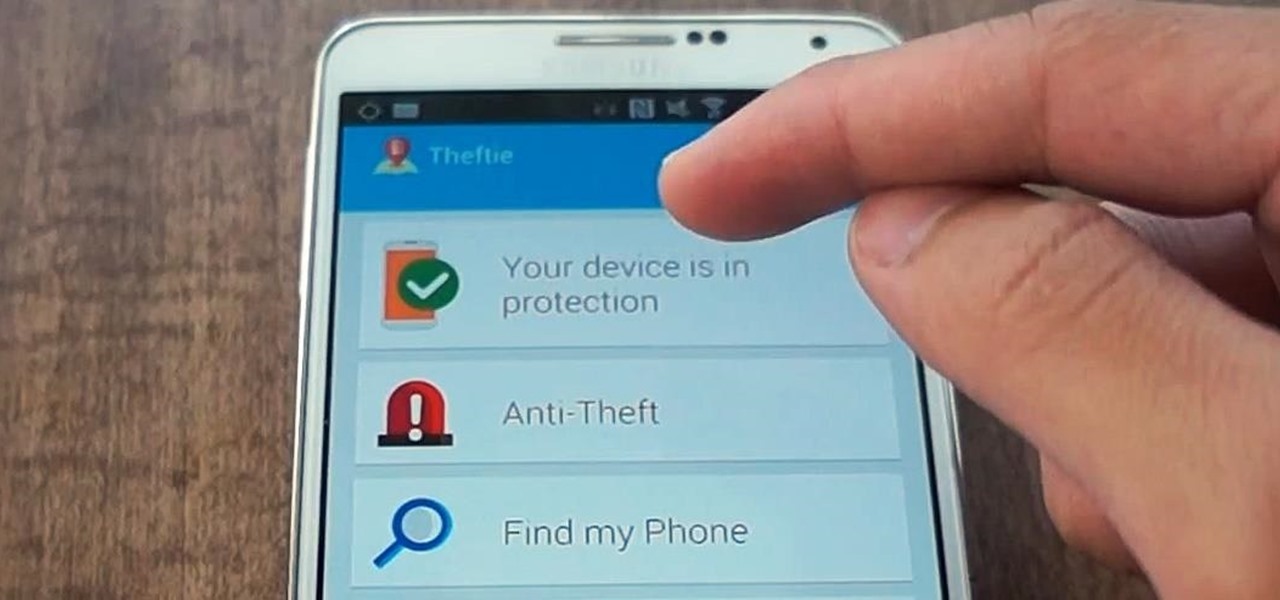
When you misplace your Android device, finding it with the Android Device Manager, or even better, Whistle Me, can help you find it no problem. But what about when your phone is not just hiding under the couch cushions? Your worst nightmare just came true. It's officially gone.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

This is the best how-to's website that I've ever seen, and I wanted to join it. It taught me a lot, but, because I'm here to learn too, please correct me if I'm wrong.

The biggest hurdle faced when text messaging (besides more convincing lies) is accurately communicating our emotion and tone. Anything we say can be interpreted in various subjective ways by the recipient, and that's why we have emoji—to illustrate what we actually want to say.

While Google would like you to believe that Flash is incompatible on Android KitKat, there is a functional workaround that will get it up and running on your Samsung Galaxy Note 3's gorgeous screen in no time.

Google's Calendar service is one of the best out there. Just because of Google's web presence, your Calendar is available to you on almost any platform, so you never miss an appointment.

When we look back on it, 2014 may be remembered as the Summer of Android Wear. With two new flagship smartwatches due out soon, Google's been readying its mobile OS for the wearables sector.

When Apple recently unveiled iOS 8, many of the newly-added features in their mobile OS seemed eerily familiar to Android users. This is probably because the vast majority of these new features have been available in Android for quite some time.

Apple's new iOS 8 has a ton of new features, and so does their revamped Safari app, only some of the features aren't quite as obvious as others. In this guide, I'll show you my 5 favorite Safari secrets in iOS 8 for your iPad, iPhone, or iPod touch.

The new iOS 8 was just unveiled, and it looks pretty awesome. Apple showed off some of the enhancements and new features we can expect to receive in the fall at WWDC, and while not the huge facelift we saw with iOS 7, it does showcase what Apple does best—refinement. Continuity

Facebook is a black hole. The constant stream of baby photos, #hashtags, BuzzFeed quiz results, and unintelligible status updates is mind-numbing. I know too much about too many people I hardly know.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

There is no shortage of games for your iPhone, and I'm sure you and your friends are probably sick to death of playing Candy Crush Saga by now. To spice things up, instead of waiting for cool new addicting games to come out, take control and make your own, then share them with your friends.

You've got to be sick of it by now. Those meaningless and unsatisfying articles, lists, and videos you were duped into clicking on because their headline made them impossible to resist.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

The all new HTC One M8 is the latest Android flagship making the rounds through major carriers hoping to beckon your purchase. Coming in at about $200 for most carriers with a contract, it makes a good case for itself with its advanced features and solid price point—but, there's another way to buy the One, and it's not from your carrier.

It's time to trip out with your tablet. If you're not looking to drain that precious battery life with a fancy-looking live wallpaper, then apply an optical illusion that appears to be moving on your Nexus 7 (or any other Android device) instead.

Samsung's exclusive music streaming service, Milk Music, has been making waves across the web thanks to its peculiar name and ad-free stations.

The Academy Awards, commonly referred to as The Oscars, are airing this weekend. If you're a movie buff or just want to watch the dimes walking on the red carpet, The Oscars is not to be missed.

You probably use your smartphone to mostly surf the web, play games, and communicate with others, but there's so much more it can do. Thanks to integrated features and third-party apps, you can seamlessly control things around your home, including your TV, tablet, Bluetooth speakers, and even lighting fixtures.

Texting can be difficult sometimes. When you're browsing the web or playing a game on your iPhone and need to respond to text message real quick, you have to exit your current app to do so. Not exactly efficient, especially if a quick "K" is all you need to say.

If you've been keeping up with anything Android these days, you've no doubt heard about a little dandy called Xposed Framework kicking around. Xposed, by XDA developer rovo89, is a framework for Android devices that lets you easily modify your stock or custom ROM.

Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.

One of the most frustrating things about full touchscreen phones, especially for those coming from one with a physical keyboard, is typing and editing text. Whether it's a quick text message, or Swyping out a full e-mail, it sucks realizing you've messed up a few words and have to go back and fix them.

NSA aside, Apple makes it difficult for users to extract and download text messages from their iPhones onto a computer. For whatever reason (legal, devious, neurotic, etc), we've all found a time where we'd like to save backups of certain meaningful, important, or perhaps incriminating conversations (including all MMS or iMessage pictures and videos). While there are a handful of third-party applications that can help with this process, the majority of them cost money and implement certain te...

It's sad to say, but the chances of a new system launching without any hitches or glitches is just not realistic. If you're one of the lucky few that has gotten their hands on the new PlayStation 4, or if you are waiting in line right now to get one, the first thing you're going to want to do before gaming is update your software to the newest version. This update isn't required, as most single-player games can be played without an Internet connection and without signing into the PlayStation ...

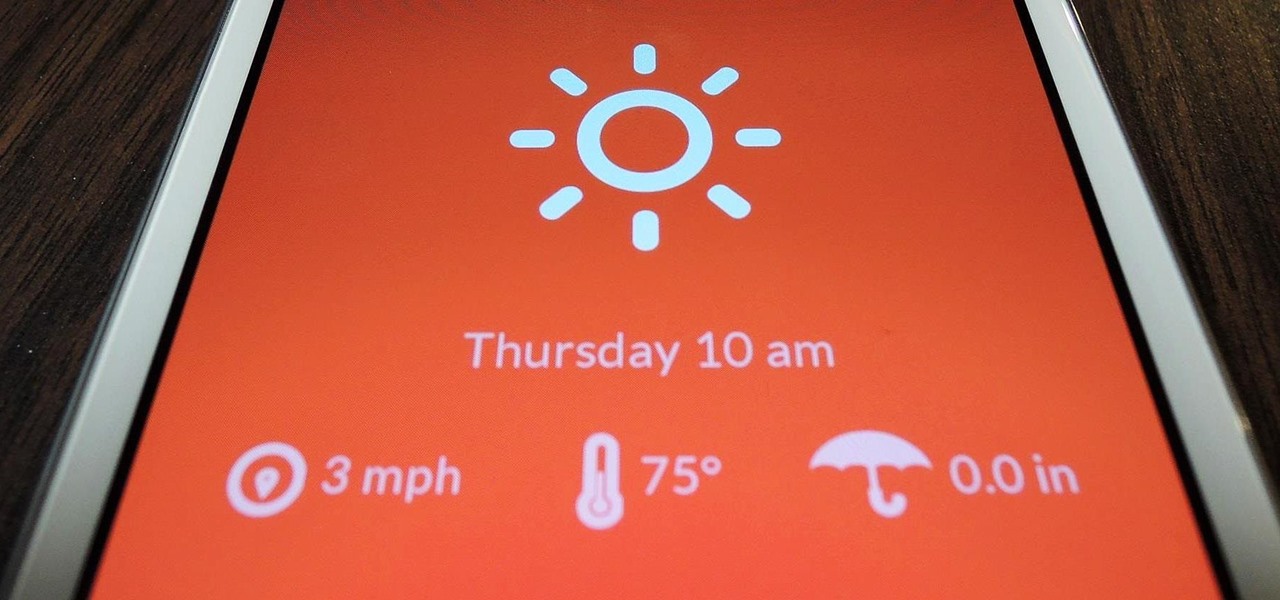
70 degrees, 8 mph winds, and sunny clear skies. That's the current forecast here in Los Angeles and I can't really complain. However, if you don't live in Southern California, checking the weather may be the difference between getting stuck in a snowstorm or remembering to bring an umbrella.