No, you didn't miss a beta. Apple just released the second public beta for iOS 13.6 today, Tuesday, June 9, three hours after the release of 13.6 dev beta 2. This update might come as a surprise to you, considering your iPhone might currently be running iOS 13.5.5 public beta 1. Indeed, this update is that version's successor, just with a major name change.
PirateBox is a great way to communicate with others nearby when cellular and Wi-Fi networks aren't available. With it, you can anonymously share any kind of media or document and even talk to one another by voice — without being online. However, it needs a Raspberry Pi, which is more expensive than ESP32 boards, and if you only need a text-based chat, there's a much simpler option.

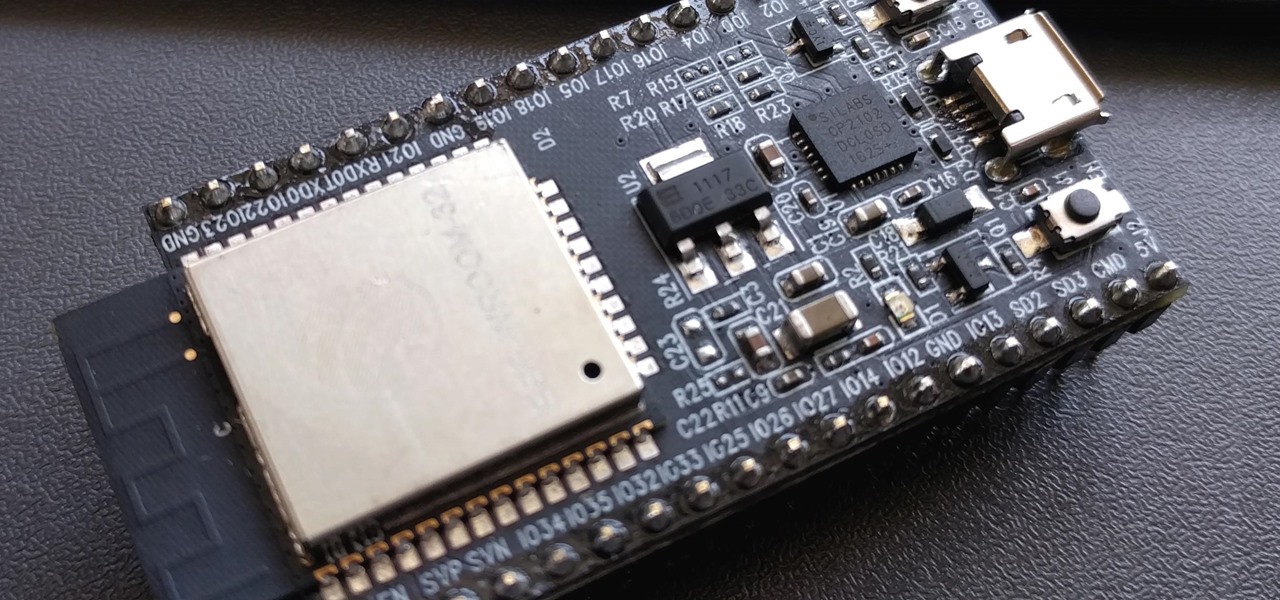
In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift to create fake networks known to be in other areas, we can manipulate where a device thinks it is with an ESP8266 microcontroller.

It's OK to want an extended break when you're working or learning from home. Maybe you want to play a video game, spend more time with your family, hang out with your dog, or FaceTime with friends. But how can you do that when you're supposed to be in a Zoom video conference or class? Thanks to one Zoom feature on your iPhone, it may be easier than you think.

On March 13, President Trump announced during a briefing in the Rose Garden that Google was building a COVID-19 screening website to help Americans understand if they might have the new coronavirus. If likely infected, the site would also include the location of a local drive-through testing site to visit. So how can you access the screening website?

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

After the lackluster update that was iOS 13.3.1, we beta testers were in need of some excitement. Thankfully, Apple delivered the goods with iOS 13.4 developer beta 1, introducing fun new features like fresh Memoji stickers and a new Mail toolbar. Of course, that update was for developers only, so we public testers are thrilled that Apple just released the first public beta today.

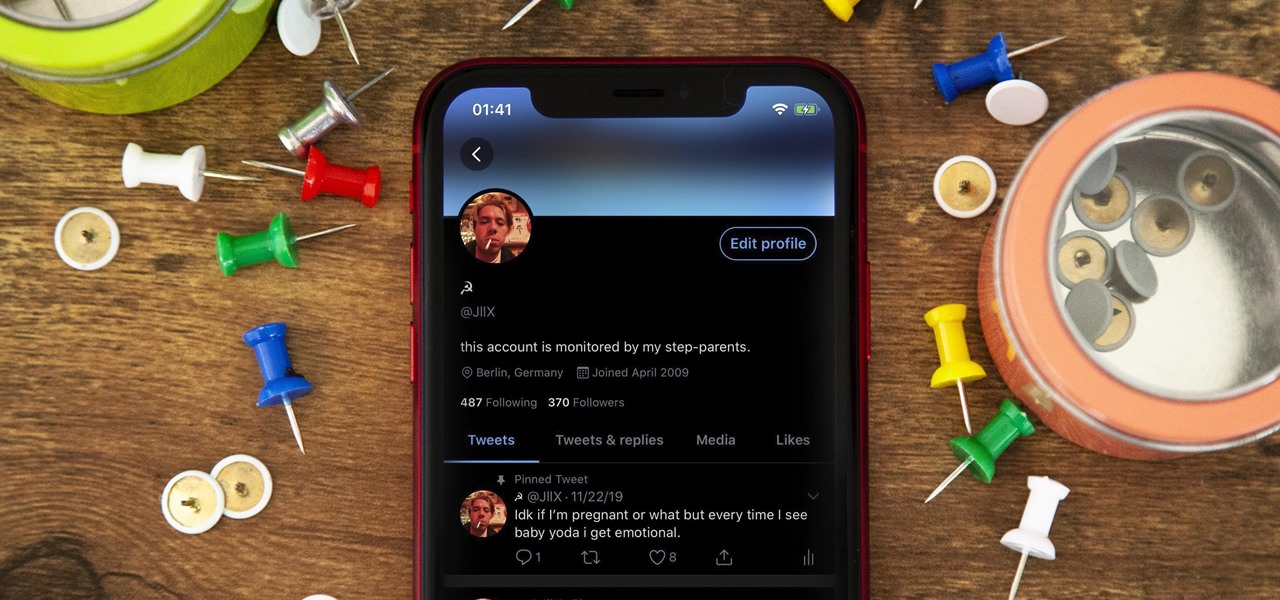
Pinning a tweet is a great way to get the point across because it's the first post people see when they visit your Twitter profile. When you pin a tweet, reply, or retweet, it sticks to the top of your profile, whether you create new tweets or not. It's the perfect spot to place one of your more popular tweets, a fantastic blog you wrote, or even just a joke that shows your personality.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

No one likes in-app advertisements, especially in mobile gaming, but they're necessary because they offer developers a way to make revenue without having to charge you to play. In some games, in-app purchases give you the chance to remove ads, but what can you do about apps that don't offer the option to kill ads?

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

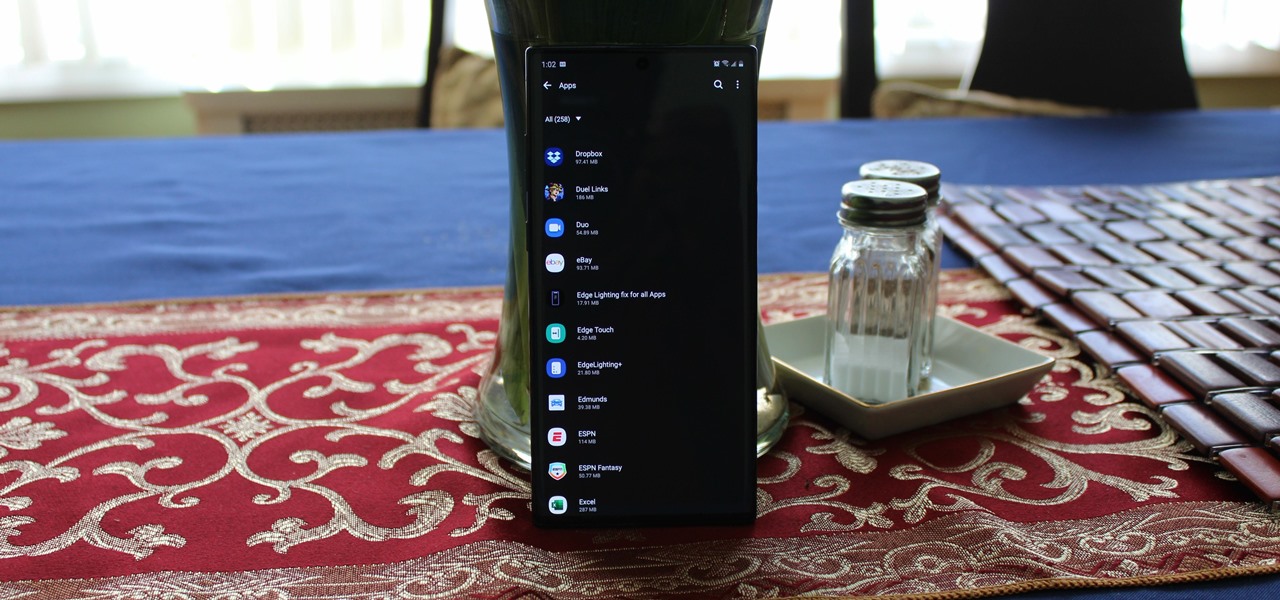
You may have noticed your Note 10 came with quite a bit of bloatware. Even the unlocked version of the phone comes with Facebook preinstalled, and if you bought it from a carrier, it's much worse. Luckily, there's a way to remove any apps you don't want, and you don't need root or a paid app to do it.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

One of the best ways to dig into a website and look for vulnerabilities is by using a proxy. By routing traffic through a proxy like Burp Suite, you can discover hidden flaws quickly, but sometimes it's a pain to turn it on and off manually. Luckily, there is a browser add-on called FoxyProxy that automates this process with a single click of a button.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

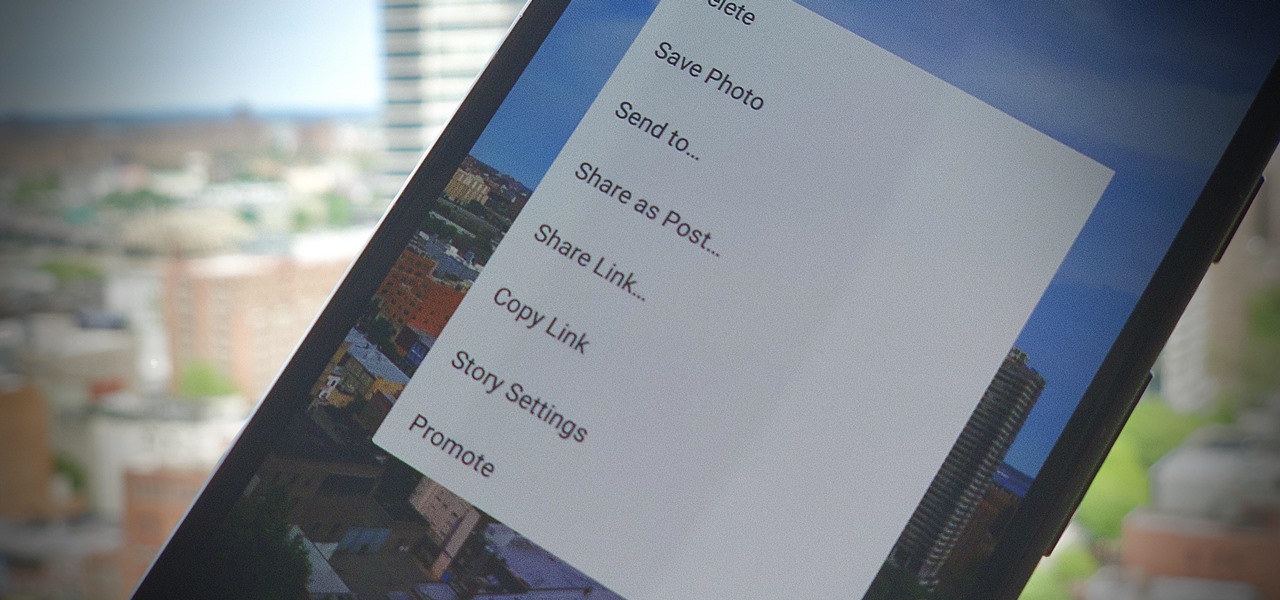
On Instagram, it's all about the sharing, but not all sharing is equal. Take stories, for example. Up until recently, stories couldn't be easily shared outside the Instagram bubble. Now, Instagram lets you share a convenient link to a part of your story or your entire story on any other platform — text, email, social app — pretty much anywhere.

In a world of seemingly endless streaming services, podcasts continue to offer free, unlimited entertainment for all. When you find a podcast that's just too good to keep to yourself, sharing it with family and friends is inevitable, but how you share may determine whether or not they listen to it or not. Links alone aren't enough. Audio and video clips are how you get them sucked in.

During the keynote at WWDC earlier this year, Apple introduced the latest iteration of its mobile operating system, iOS 12. Despite a thorough demo on stage, Apple glossed over new eye tracking features that use ARKit 2. Developers can now use the TrueDepth camera on the iPhone X, XS, XS Max, and XR to determine where your eyes are looking, opening up incredible new possibilities for new apps.

As great as passcode and biometric security features like Face ID are for preventing unwanted access, they aren't needed 100% of the time. When you're at home with a locked door between you and anyone you wouldn't trust with your phone, they really only serve to slow you down. Android has long had a solution for this, but a new Cydia tweak has now brought a similar solution to iPhones.

Google's next-gen cellular carrier, Google Fi, which replaces Project Fi, is making waves across the mobile industry. With super-cheap plans starting at only $20 and the ability to connect to millions of Wi-Fi hotspots across the globe, it's tempting many users to make the switch from AT&T, Sprint, T-Mobile, and Verizon Wireless.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

Let's say you want to download an Instagram video to your iPhone. What do you do? While Instagram doesn't offer an official solution, there are backchannel methods that exist to get the job done. However, if you want native support for downloading Instagram videos directly to your Photos app, you can start by updating your iPhone to iOS 12 and installing Shortcuts.

After months of beta testing, Siri Shortcuts has finally arrived on all iPhones that support iOS 12. Anyone familiar with Workflow will understand how useful it is to set custom Siri commands for your favorite apps. Of course, your favorite apps need to be compatible with Shortcuts in order to take advantage of the new feature.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

While some of our group chats should probably remain private and closed off, others will only get better with more people. Whether you're organizing an event and need a headcount or you want to share a funny YouTube video with a large crowd, you can add all the friends you wish to on Facebook Messenger by sending them a unique link.

The internet is chock-full of fun and interesting content, but there's only so much time in the day for consuming it. That's when saving webpages for later comes in handy. If you don't want your bookmarks and favorites folders to clutter up fast, consider using the "Reading List" feature built right in Safari on your iPhone.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

There are over 3 million apps in the Google Play Store, all optimized for the small screen in your hands. While that number sounds staggering, there are still many online tools and websites that require you to use a mobile browser since app development is expensive. However, that's where Progressive Web Apps (PWAs) come into play, a cost-effective way to turn websites into mobile apps.

The iPhone X, iPhone 8, and iPhone 8 Plus may be some of the fastest phones of 2o17. However, the equally new iOS 11 isn't quite as impressive. That being said, Apple is continuing updates to the developer beta for iOS 11.1, as it releases the 5th version of the beta today.

What makes YouTube such a special platform is that anyone and everyone can upload their own content. Big players upload their videos to the same site that the little guy does.

Greetings fellow hackers. This tutorial is about creating "safe" passwords. This is different from strong passwords. Safe passwords is just creating a password that is not used by someone else or colleague, my definition. But how do you prevent something like this from happening? Of course you won't ask your friend if s|he is using the password you are about to create. Before I show you some of my tele-psychic powers like Professor Xavier, you might want to read this for advice on creating "s...

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

After you have registered to this site,sign in then to start missions. Basic Missions