
How To: Rooted Android = Your New PenTesting Tool
No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!


No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!

When you forget you charger,you can use this dynamo charger to charge the phone with your hand. I convert the dynamo LED flashlight into charger just adding bridge rectifier, capacitor and USB female plug.

Video: . this codes help

This video will show you how to tether your Samsung Messager 2, (the MetroPCS phone) to your PC to use as a modem for internet access. This will allow you to use your cell phone as your internet connection point, meaning you'll connect to the net for the cost of your cell phone's data plan. You will need your Samsung USB cable, a PC with Windows 2000 or higher, all current drivers for your phone and PC, and you will also need to head here to get the Samsung PC Studio program. This is part 1 o...

A video that describes how to install Google Chrome OS onto your PC without changing your current PC configuration. What this means that you can use Chrome OS without changing your current OS (Windows Linux etc) and without making any changes to your dis partition or BIOS. The first section of this video explains how to use a simple USB drive to boot into Google Chrome OS. The second section of this video explains how to install Google Chrome OS onto your computer and launch it using your hos...

Mike Agerbo explains the benefits from listening to one's music through AppleTV, however it seems that one cannot listen to any music or other audio files unless he/she is using iTunes media. Agerbo explains how you can use Apple TV with other types of media, using a program called ATV Flash. Agerbo believes ATV Flash to be an easy and inexpensive tool to upgrade one's Apple Television so it can use the USB port and download and use other media content. One can also create a Boxee account to ...

Do you need just a few more controls? Perhaps your wondering how hard it is to make your own controller? Then follow the steps in this 2 part series and build your first MIDI controller in about an hour for very little cash. Using only 8 electronics parts, a pre-made case and a DIY midi interface that is USB powered- you can build a controller and it wont require a degree in electrical engineering. For detailed, step-by-step instructions, on building your own DIY MIDI controller watch this vi...

You never know when your computer could eat up all of your work, but you can backup your important files on the music player you already own!
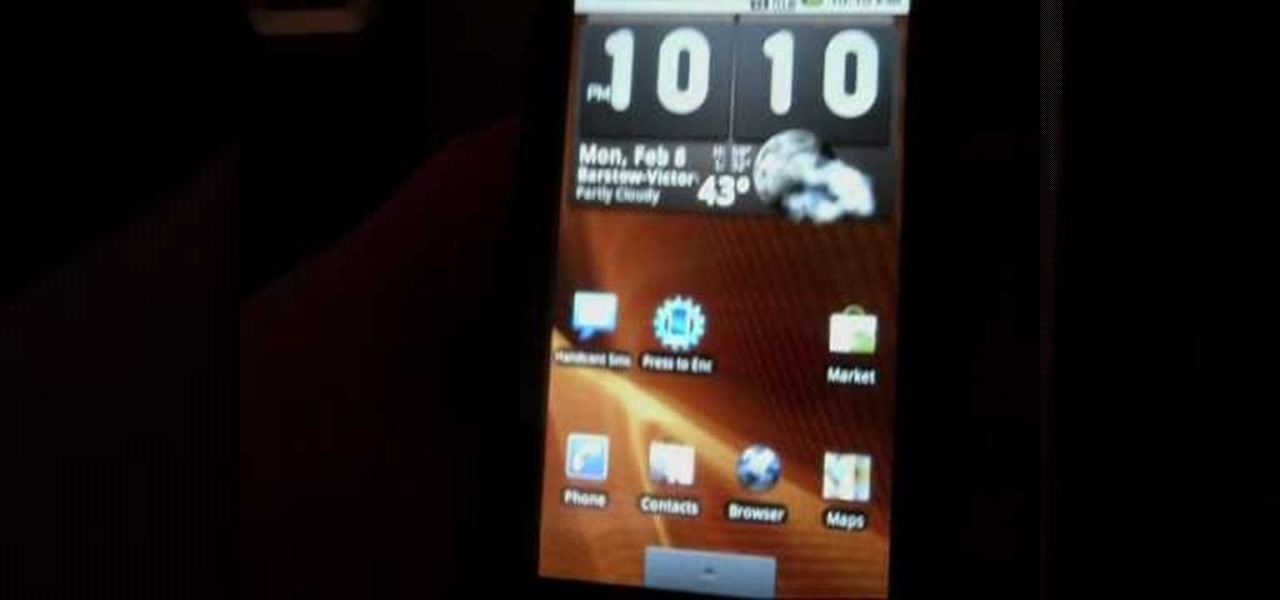
If you've rooted your Motorola Droid chances are that you are enjoying the results, but are concerned about the consequences if you phone updates or in any way become incapacitated since your phone manufacturer will not be pleased with what you've done to the phone. One way to ameliorate these fears is to back up your phone. This video will show you how to use Nandroid to make a backup of your rooted phone.

Losing your important data can be more painful than losing the hardware the data was stored on. Precious memories, files you don't often access but always want to have, there's so much you store on impermanent devices that you can't live without. Backing up your information to a secure, cloud-based location is the best way to stave off disaster here. Polar Backup Unlimited Cloud Backup Storage will give you an unlimited amount of cloud storage while making the process super easy.
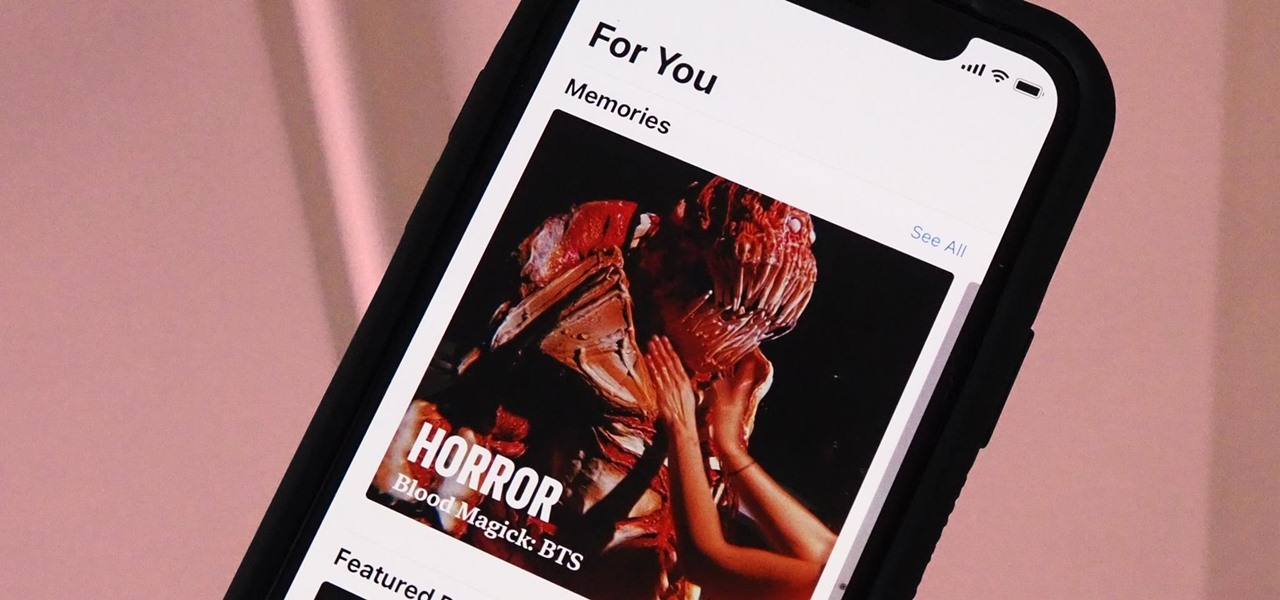
The Memories feature in Photos is meant to help you rediscover old or forgotten experiences by creating a short slideshow of photos and videos based on locations, dates, and events. It's a fun feature to relive exciting times, but it isn't always perfect because it's generated automatically. It might include incorrect content, but in iOS 14, you can now create your own Memory Movies.
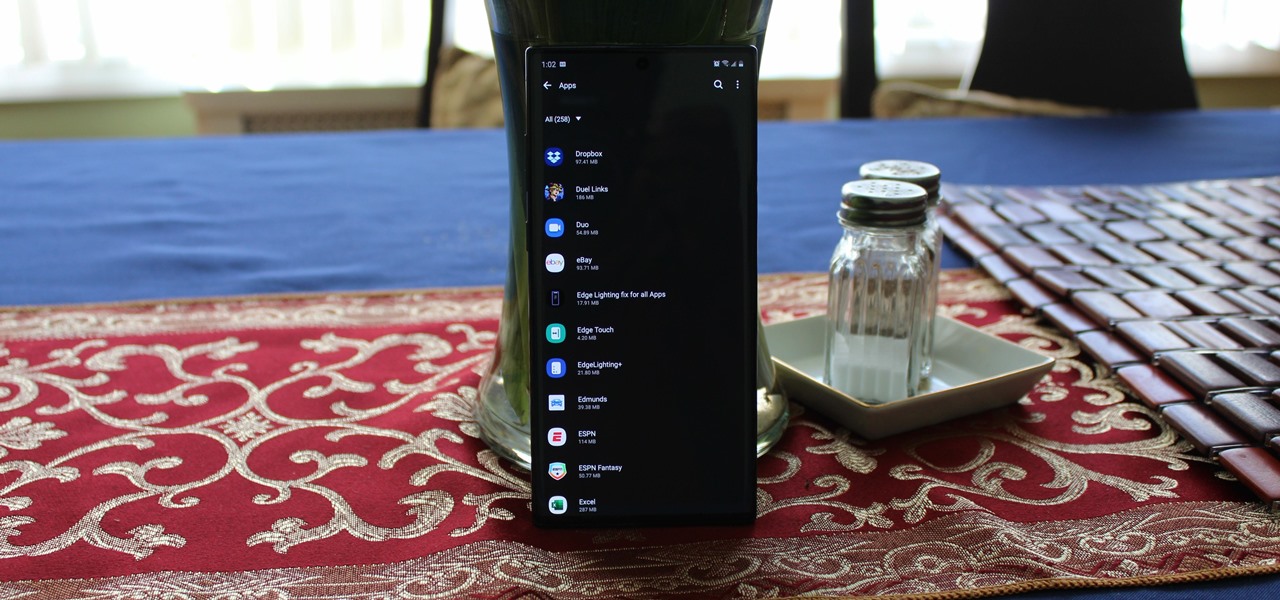
You may have noticed your Note 10 came with quite a bit of bloatware. Even the unlocked version of the phone comes with Facebook preinstalled, and if you bought it from a carrier, it's much worse. Luckily, there's a way to remove any apps you don't want, and you don't need root or a paid app to do it.

For years, Samsung has been behind the curve when it comes to fast charging. Up to the Galaxy S10, most of their phones used the very slow Adaptive Fast Charging system. Whether it was the Galaxy Note 7 fiasco or some other reason, Samsung has been reluctant to push the charging envelope. Until now.

The newly-announced Moto G7 Play offers some of the same upgrades as its sibling, the Moto G7, but at a much lower price. The upgrades are pretty significant when compared to last year's Moto G6 Play, taking this phone from the "only if you're on a strict budget" category into a great value option.

It wouldn't be iPhone season without a new controversy. Chargegate, Apple's latest PR nightmare, is the name being used for charging issues on some iPhone XS and XS Max devices. If you plug in your iPhone at night — or whenever — then wake up or come back later and see that your iPhone has even less battery power, you're affected. But there is a fix you can implement right now.

The S9 and S9+ are both fantastic phones. However, there's no getting around the fact that the S9+ has its advantages. In fact, it's an objectively better smartphone than its smaller counterpart — Samsung has given the S9+ features not found in the S9, meaning you'll be missing out if you choose the 5.8" Galaxy over the 6.2".

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2017 selection of hacker holiday gifts — just in time for Christmas.
Despite mounting scientific evidence that viruses can cause changes in learning and memory, the reasons have remained elusive.

The '90s were a great decade to be alive. Before the internet became a high-availability service, we were untethered from the bombardment of media present in today's culture. Children ran through the streets with levels of physical exertion beyond what's required to capture fictional creatures found in Pokémon GO. However, there were some video game consoles that kept kids indoors, such as the Game Boy, SNES, and more importantly—the first ever PlayStation.

What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey, as long as it's there, people can always go off to research themselves and eventually understand. So here is my contribution to the gradual and inevitable progression of Null Byte!

There's a good chance that your iOS device has become unresponsive at least once. It's usually at this point that you start thinking your device can no longer pass muster. You could upgrade to a newer model, but that's not always feasible, and often times, unnecessary.

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.

On mobile devices, the Notification Center received a huge facelift when iOS 8 was released, but it wasn't until Yosemite that its Mac OS X counterpart received the same amount of love—especially the much needed ability to add custom widgets, like a FaceTime dialer.

Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app.

If you've ever had issues charging your iPad, iPhone, or iPod touch, like most other Apple products, the culprit to blame is usually a frayed or damaged cable. It's a common design flaw due to the thinness of the cords and the weak sheath surrounding them — but that's not always the problem.

As you may have already heard, the worst bug in OpenSSL history went public yesterday, dubbed Heartbleed. While we can go deeper into the technical details of it later, the short version is that OpenSSL, the library used to encrypt much of the web running on Linux and Apache has been vulnerable for up to two years.

It seems nowadays the word "easy" has taken on an alternate meaning. When I see "easy," I expect a quick and painless process, but when it comes to flashing or installing a custom ROM, easy means anything but.
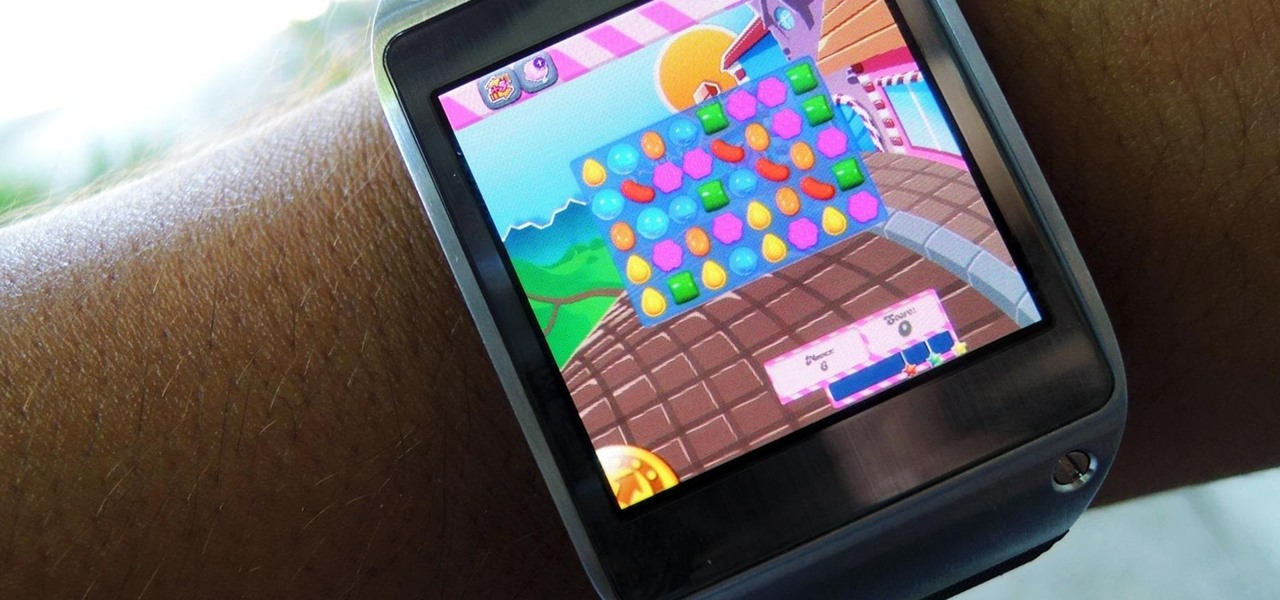
With the Samsung Galaxy Gear smartwatch only several weeks old, the extent as to what you can do with it is limited since there are only about 70 apps in the Gear Store right now, and a lot of those need the full app installed on your Samsung Galaxy Note 3 in order to function properly.

To really customize your Samsung Galaxy S3, you'll need to be rooted, because most of the coolest mods and hacks require root access. If you haven't rooted yet, you're just barely touching the surface of what your GS3 can do for you.
I remember how fast my Nexus 7 was the first time I turned it on. Boy, do I miss it. Now my tablet is pretty buggy and crashes happen frequently, and I'm sure that goes for many of your Nexus 7s as well. Even if you upgrade to the new Nexus 7 next week, it will eventually develop similar issues.
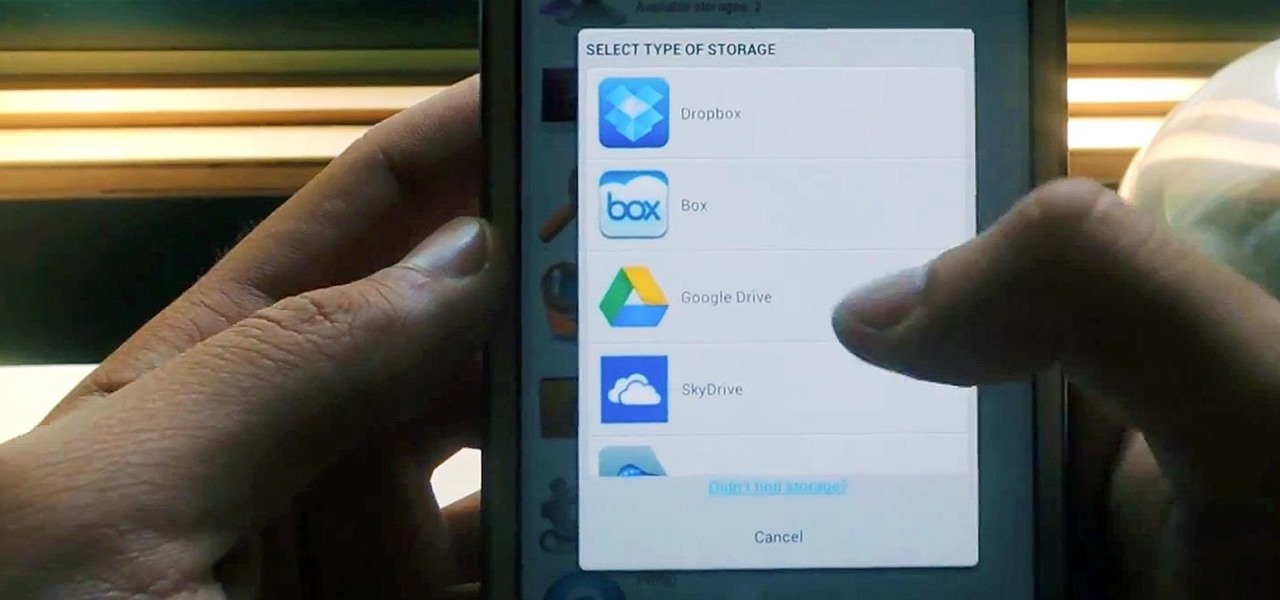
Cloud storage looks pretty good compared to the heavy restrictions that hard drives and other types of external memory carry. The cloud is not only limitless in what it can hold, but it can also easily be accessed from any device that has Internet—your smartphone, work computer, personal laptop, tablet, and more. While accessing a specific cloud storage system like Dropbox or Google Drive may be easy on your Samsung Galaxy Note 2, managing all of them individually can not only get confusing, ...
When the amount of memory on your computer sucks, you either have two options: Buy more RAM, or make use of the storage space you've got by compressing your files. One program that will become your new BFF should you choose to do the latter is WinRAR. WinRAR is a compression and packaging software that makes it way easier to store large files on your computer.

This tutorial shows you how to master the use of proprortions. Ignore most of the formulas given in professional books. Learn how to draw accurate and proportionate human faces directly from memory, and learn the most accurate proportions for the human face.

Start with a stack of plain brown paper lunch bags. Then, follow the steps outlined in this video to make a beautiful Christmas keepsake scrapbook album. A great gift for a loved one, or keep it yourself as a memory of the year.

The archenemies of cell phones— puddles, toilets, swimming pools— can cause serious damage to your gadgets. And if your mobile phone has taken the dive, don't panic— there's hope for recovery.

At its heart, Lewis Carroll's "Alice in Wonderland" is a book about growing up, about the sometimes crazy and nonsensical journey into the world of pretty crazy and nonsensical grown-ups. But at the same time it is a story that celebrates childhood and the wondorous imagination that one can only have at that point in time.

If your photo albums are older than you can remember and have yellowing, ripped pages and photos askew, then we can bet that your photos aren't in good condition. So save your prized memories and keep them looking great for future generations by organizing them neatly into a photo album.

Rings add a chic finishing touch to any outfit, but quality rings can be expensive and affording more than one or two is difficult for girls on a budget. If you're a big fan of wearing some bling on your fingers but don't feel like spending your entire paycheck on them, watch this video to learn how to make your own.
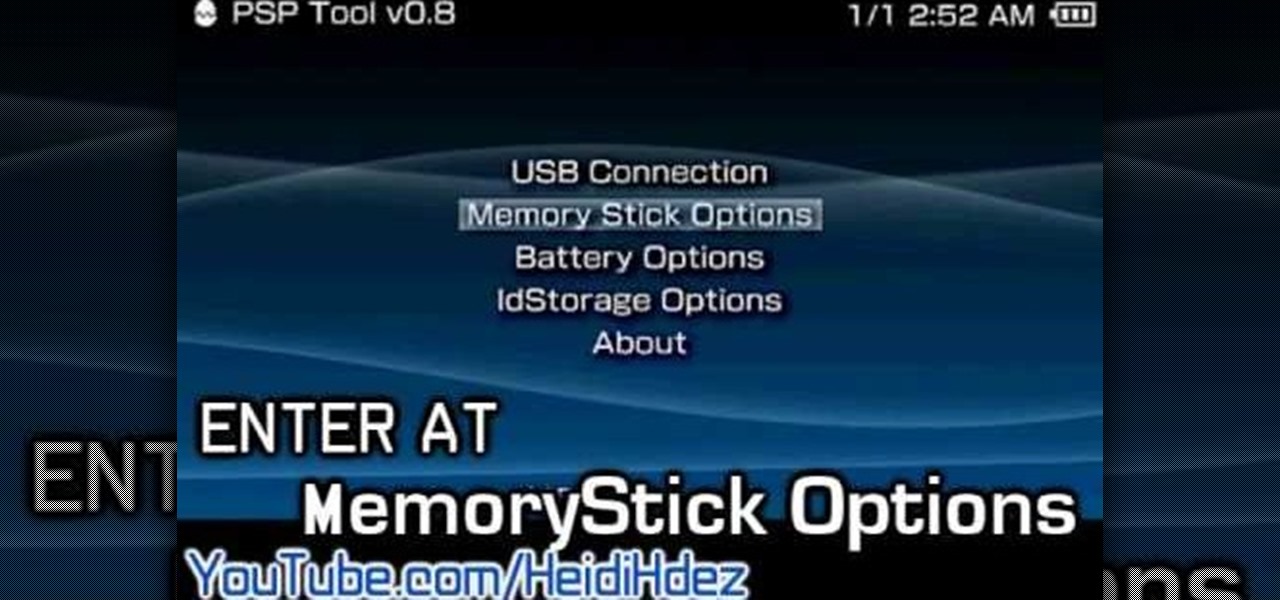
Hacking the PSP is a complicated process, and there has been some demand for a software tool that would make the process easier. This video has that solution. It explains how to use a program called PSPtool to create the magic memory stick and Pandora's battery much more easily than you could otherwise. Follow these instructions and play those homebrews!