
Hacking macOS: How to Create an Undetectable Payload
Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.


Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

Hello everyone! How's subnetting going? Did you practice a lot? I hope you did, but even if you didn't we will go through some more examples so you can be feeling confident after reading this article. It's all about that bad boy binary!

Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...

Welcome to my tutorial where Voidx and I will be expanding on my previous article to provide more clarity into the logic of the code.

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.
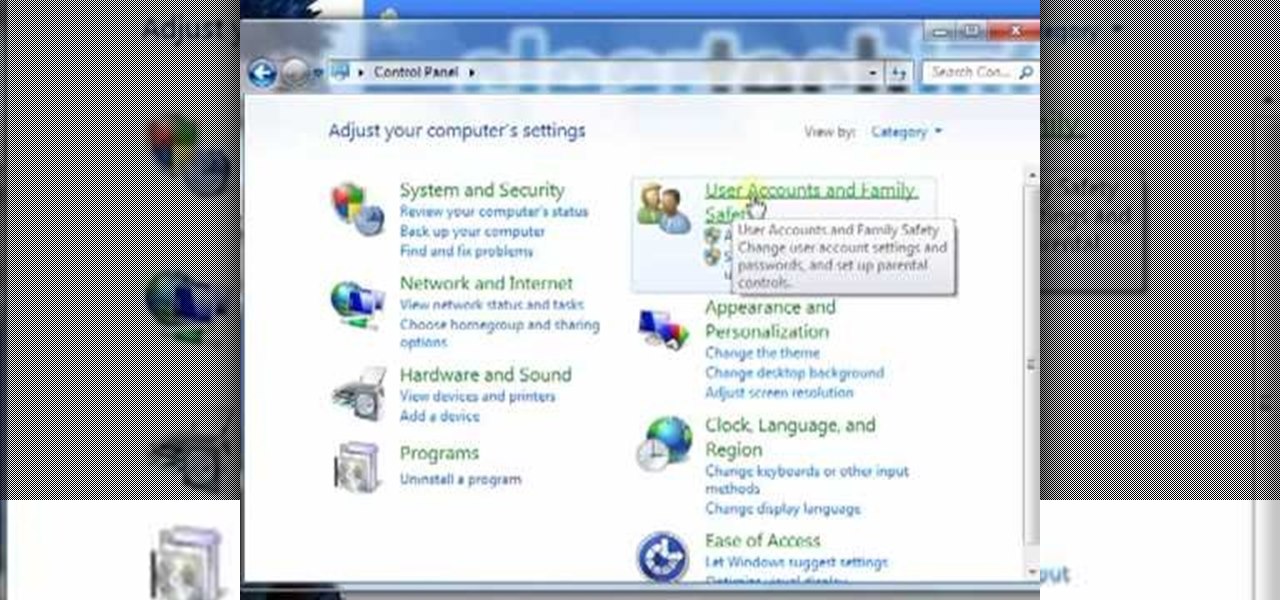
In this video tutorial, viewers learn how to create a new standard user and administrator account. Begin by clicking on the Start menu and select Control Panel. Then click on User Accounts and Family Safety and click on User Accounts. Now select the "Manage another account" option and click on "Create a new account". Users are able to name the account and select the account type (Standard or Administrator). Finish by clicking on Create Account. Users are then able to make changes to the accou...
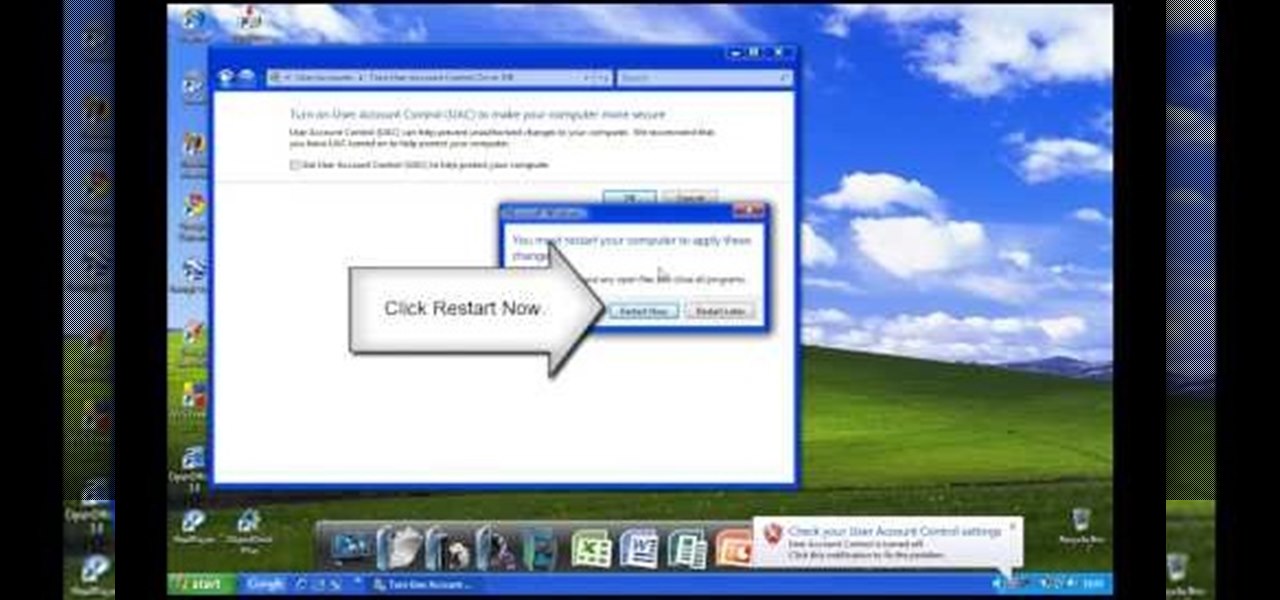
In Windows Vista start off by going into the control panel in the start menu. In here go into "user accounts and family safety". Inside go into "user accounts". A screen will appear where you can make changes to your user account. Here there should be an option to turn user account control on or off. Click on this will bring up another window where if you uncheck the solitary checkbox you will have succeeded in turning User Account Control off. After doing so click ok and then press restart n...
This video contains instructions about how to disable or enable the user accounts on Windows Vista. It is very simple; just go to control panel -> user accounts and safety -> user accounts. You can click the check box on or off to disable or enable the user accounts. This can also be done by using command line. Open run and type the following command:
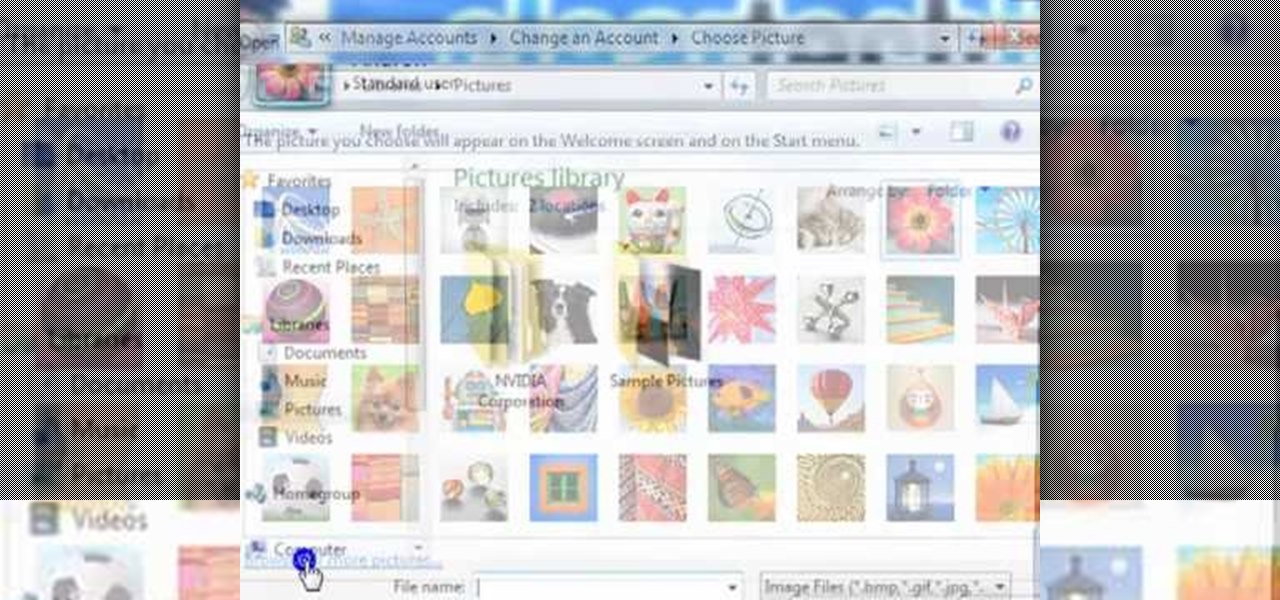
ClearTechInfo live up to their by offering clear and concise information on how to manage user account settings in the new OS from Microsoft, Windows 7. Begin by pressing the start button and going into the control panel. In here look for 'user accounts and family safety', open it. Now go into user accounts and then manage another account. If you are the administrator then you can change whichever setting you want for whichever account but if you're just a standard user you can only alter you...
In this video tutorial, Chris Pels will demonstrate how to create a custom user control in ASP.NET that can be used throughout a web site or across many web sites. Start out by learning the basics of creating a user control that will be used in multiple pages including validation, controlling formatting using style elements, and loading/saving data for the user interface elements. Throughout the video considerations for building user controls that can be easily maintained and used across mult...
In this video tutorial, Chris Pels will show how to determine what capabilities a user’s browser has when viewing pages in an ASP.NET web site. First, learn how to access an instance of the HttpBrowserCapabilities object from the ASP.NET Request object associated with the web page request. Next, see the different information available in the HttpBrowserCapabilities object such as the type of browser and whether the user’s browser supports JavaScript and Cookies. Then see an example of how to ...
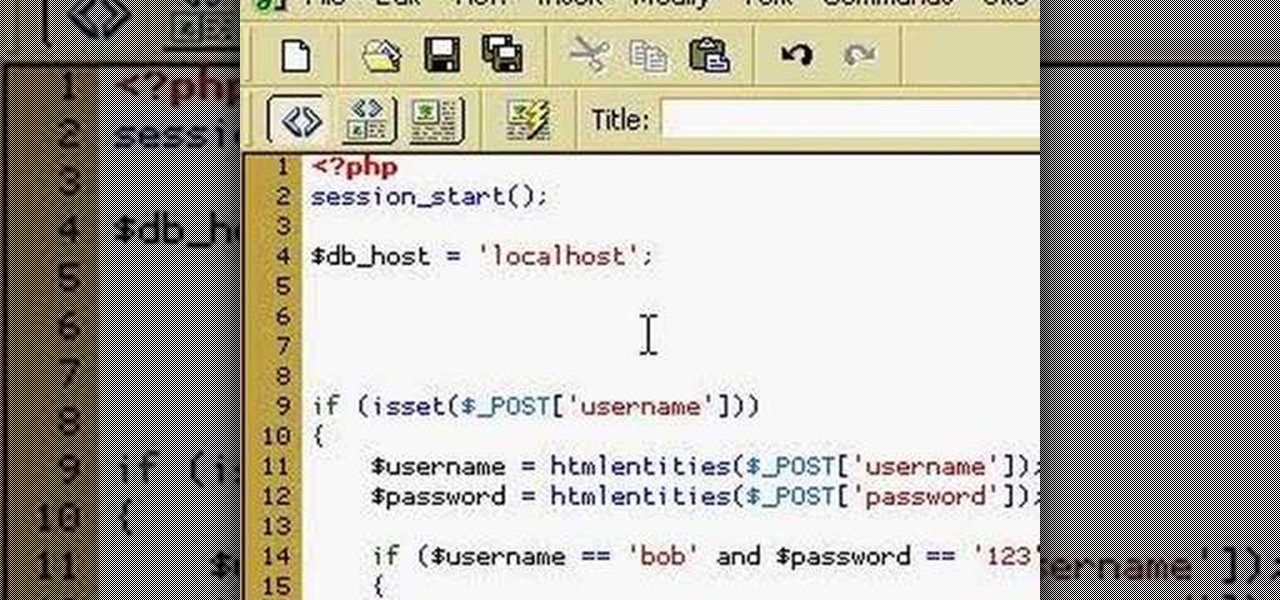
How to program a user registration using php, sql and phpmyadmin. Part 1 of 3 - How to Program a user registration with PHP.
How to manage user logins by creating a MySQL user login database with PHP. Part 1 of 3 - How to Create a MySQL user login database with PHP.

Users will need an exercise ball to perform this exercise. Begin by going on your knees and elbows on the ball. Users basically go into a plank position in the ball. Now users will need to go into a straight position from the shoulders to the knees. Now users will draw the alphabet using their elbows, while rolling the ball. To make the exercise more challenging, users may choose to lift one or both knees off the ground while doing the exercise. This video will benefit those viewers who want ...

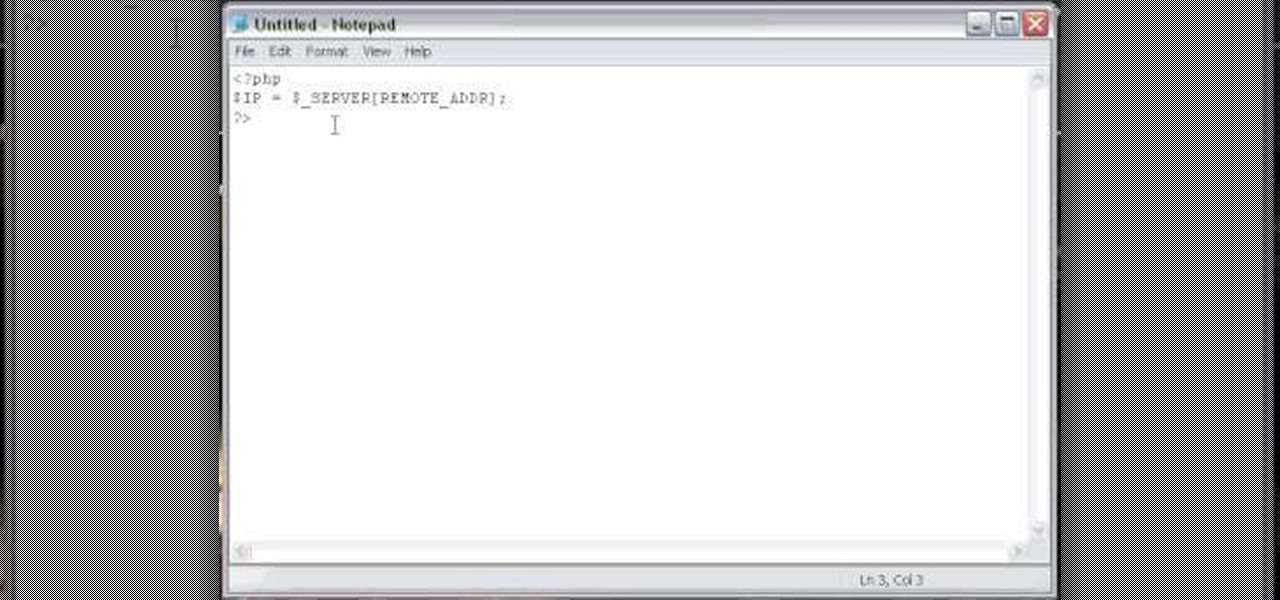
In this how-to video, you will learn how to find the IP address you are using on your computer without using any third party sites. First, go to the start menu and click run. If you are using Vista, go to search in order to the run the file. Next, you should type in cmd.exe into the prompt. A window should now open up. In this window, type in ipconfig /all. From there, your IP address should be listed. This simple video shows you a very easy way to find your IP address without having to use a...
Microsoft recommends a unique user ID and password for every user. In order to switch user ID or log off one need to click to the 'Start' menu as shown in the video. Press the move button at the shut down menu as shown. In the sub menu you can see the Change user and Log off. The window will typically shut down and restart on change of user ID or Log Off. In case you need to leave your PC unattended you can press 'Lock' from the same menu which will refrain anyone from changing your desktop s...

Follow along as we are shown how to set a password for a new user in Windows 7. -First, go to the Start menu.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.
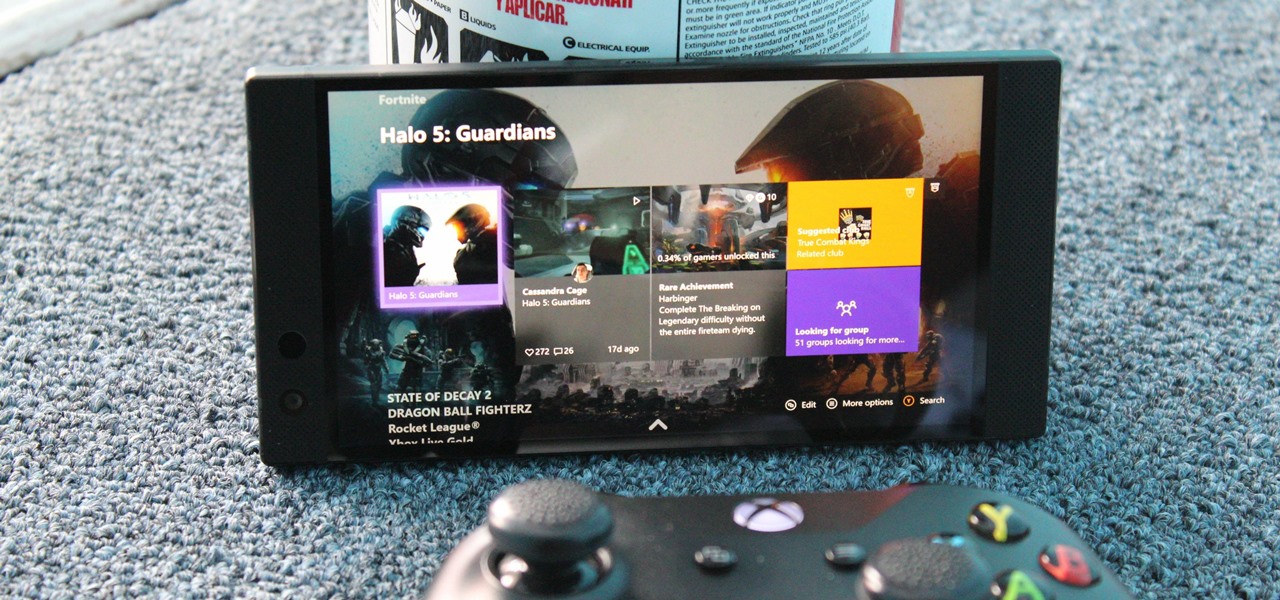
Game streaming has never been better. Not only can you watch your favorite Twitch streamer play, but with the new tools being added to YouTube, you can even play along with them. And now, with a solid internet connection, you can stream your Xbox One games to your phone to enjoy console games on the go.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

Following the surprise release of Magic Leap's SDK on Monday, March 19, Unity, Unreal Engine, and Mozilla followed up by announcing official partnerships with the company.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Last year, OnePlus released not one but two excellent flagship devices with the OnePlus 5 and 5T. While the 5T released sooner than expected, it brought some worthwhile upgrades, such as a near bezel-less display and a much-needed camera enhancement. Now, that the OnePlus 6 has arrived, it's time to see what OnePlus has in store for 2018.

With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone.
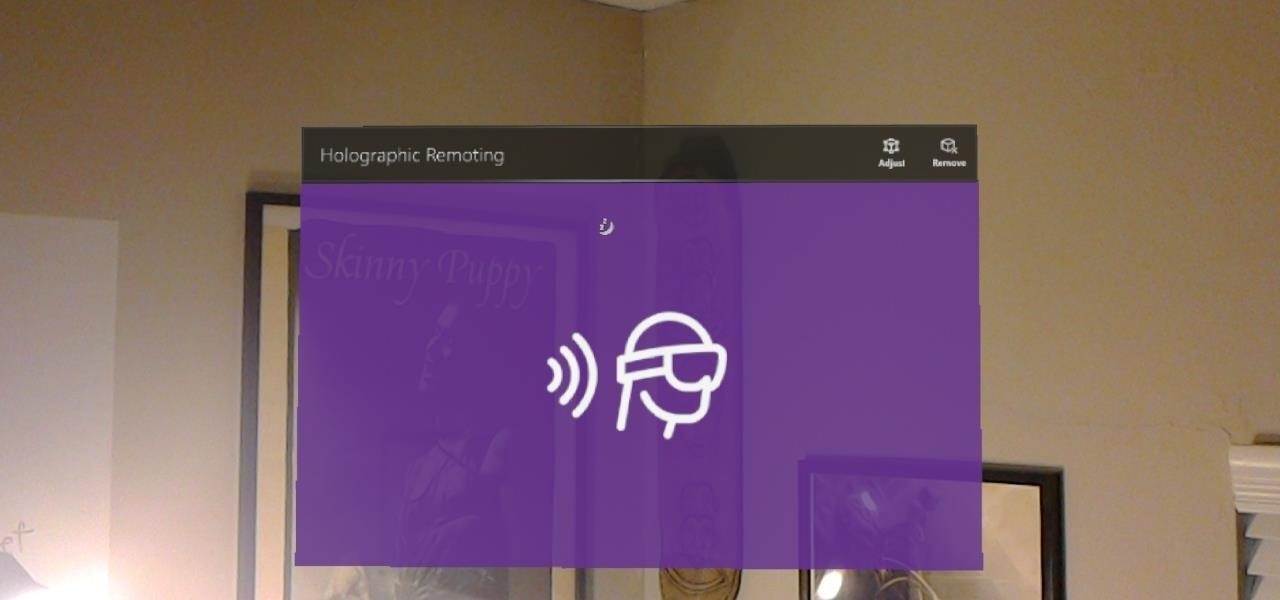
Way back, life on the range was tough and unforgiving for a HoloLens developer. Air-tap training was cutting edge and actions to move holograms not called "TapToPlace" were exotic and greeted with skepticism. The year was 2016, and developers had to deploy to their devices to test things as simple as gauging a cube's size in real space. Minutes to hours a week were lost to staring at Visual Studio's blue progress bar.

One of Android's biggest strengths is its ability to interact with other operating systems. When you plug your phone into your Windows PC, you instantly see all of the files it holds—and all it takes is a simple syncing app to do the same with Mac. To top that off, apps like Pushbullet and Join bridge the gap even further by allowing you to share links, files, and messages between all of your devices.

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

At last, what you all finally waited for! Hi! Fire Crackers,

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Apps that have no business accessing the internet can share your location, device ID, and other personal information with potentially malicious data snatchers. If you're connected to the internet on your Nexus 7 tablet, you're a potential target for cyber threats.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.