Learn how to create a world in microcosm with this C4D user's guide. While the end result is not particularly pretty the tutorial does show you how do deal with lighting the Hair Render through another layer, creating a cloud layer and the texture for a bubble.
In this video tutorial, viewers learn how to get tabs in Finder. This can only be done on the Mac OS X computers. Users will need to download the Total Finder application from the site provided in the video. Once downloaded and installed, this program will allow users to manage multiple Finder windows in a series of tabs in a single window. In the Finder Preferences, users are able to configure the sidebar, label color, file name and trash options. This video will benefit those viewers who us...

Learn how to model a full 3D tire (or tyre) with this Blender user's guide. Whether you're new to the Blender Foundation's popular 3D modeling program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed instructions, take a look!
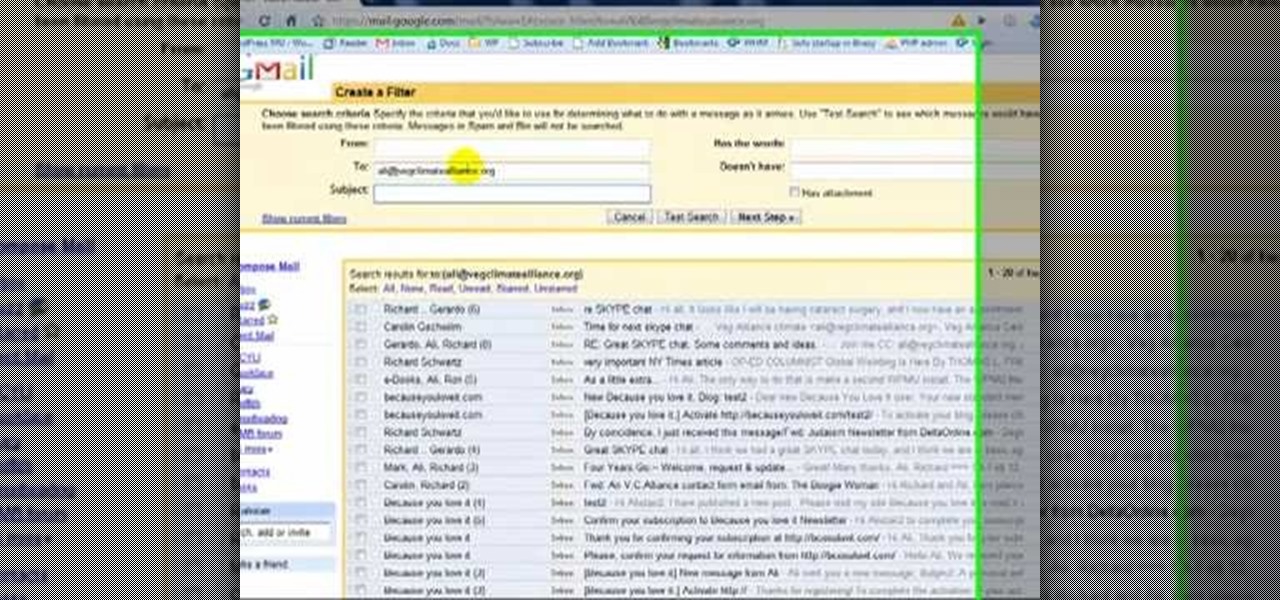
See how to set up multiple inboxes within Gmail and use filters and labels to have mail sent to different addresses automatically sorted (and mail sorted using other criteria too, like subject, or containing certain words). It's easy! So easy, in fact, that this Gmail user's guide can present a complete overview of the process in just over four minutes time. For details, and to get started using Gmail's useful filtering feature yourself, take a look.

In this video tutorial, viewers learn how to surf the web with mouse gestures. Users will need to use the Firefox Mozilla browser. Begin by going to the Firefox Mozilla add-on site and search for "fire gestures". Click on Add to Firefox to install the add-on. Once installed, users are able to use their mouse for certain signs or gestures such as: go back, forward, reload or open new tabs/windows. Users are able to customize the mouse settings in the add-on options. This video will benefit tho...
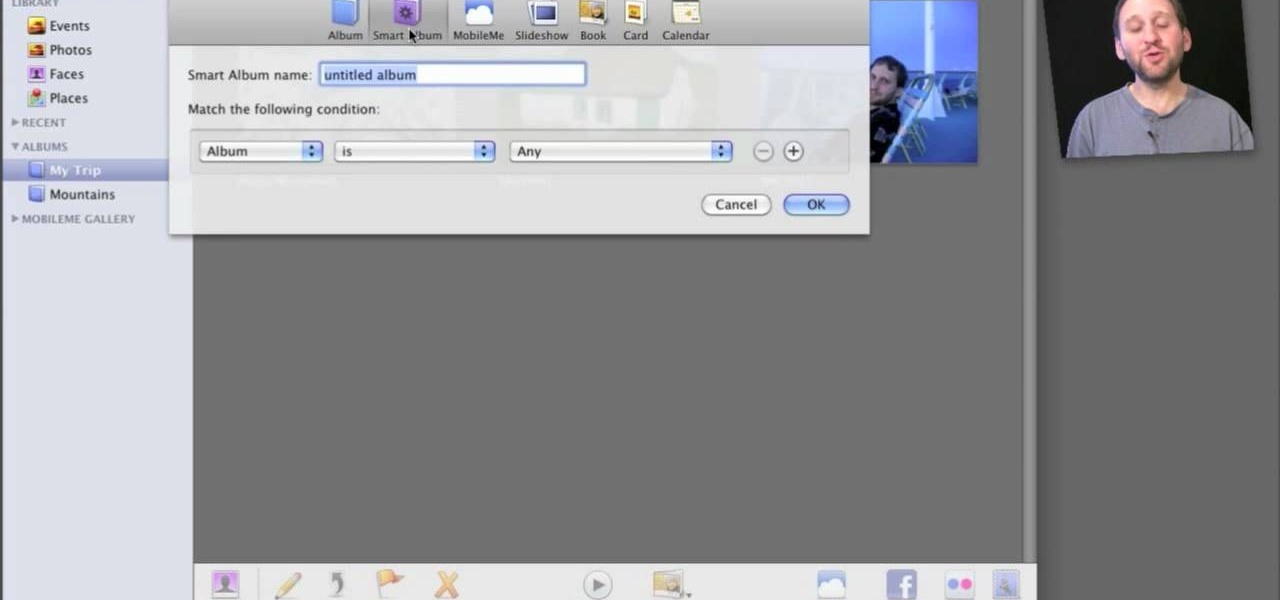
Organizing your photos in iPhoto 09 is a breeze provided you know how to take advantage of the program's various features (like, for example, keyword tagging). This free video software tutorial from the folks at MacMost will get you off and running. For specifics, and to get started organizing your own photographs, watch this iPhoto user's guide.

Looking for an easy way to cut down on the spam you receive at your main Gmail account? With plus (+) sign filtering, it's easy! So easy, in fact, that this free home computing how-to can present a complete (and somewhat talky) overview of the process in just over a minute's time. For specifics, and to regain control over your email account, watch this PC user's guide.

Looking for a guide on how to synchronize Microsoft Office Outlook with your Google Calendar account? It's easy! So easy, in fact, that this free home computing how-to can present a complete (and somewhat talky) overview of the process in just over a minute's time. For specifics, and to start combining your Outlook and Google calendars, watch this PC user's guide.

Need some help figuring out how to burn a Microsoft Windows 7 system repair CD? It's easy! So easy, in fact, that this free home computing how-to can present a complete (and somewhat talky) overview of the process in just over a minute's time. For specifics, and to start making your own Windows 7 restore discs, watch this PC user's guide.

Decided you want to leapfrog Vista and upgrade from Microsoft Windows XP directly to Windows 7? It's easy! So easy, in fact, that this free home computing how-to can present a complete (and somewhat talky) overview of the process in about six minutes' time. For specifics, and to start installing Win 7 on your own computer, watch this PC user's guide.

Need a little help figuring out how to capture screenshots in Microsoft Windows 7? It's easy! So easy, in fact, that this free home computing how-to can present a complete (and somewhat talky) overview of the process in just over a minute's time. For specifics, and to get started taking your own screengrabs in Win 7, watch this PC user's guide.

Want a swooshier Microsoft Windows 7? Try the jump list trick! It's easy! So easy, in fact, that this free home computing how-to can present a complete (and somewhat talky) overview of the process in just under a minute's time. For specifics, and to get started improving your own Windows Vista Sidebar, watch this PC user's guide.

Need a little help figuring out how to customize your Microsoft Windows 7 Start Menu? It's easy! So easy, in fact, that this free home computing how-to can present a complete (and somewhat talky) overview of the process in just a minute's time. For specifics, and to get started personalizing your own Win 7 Start Menu, watch this PC user's guide.

Did you know that you can use a USB flash drive to speed up a sluggish Windows XP computer? It's easy! So easy, in fact, that this free home computing how-to can present a complete (and somewhat talky) overview of the process in just over a minute's time. For specifics, and to get started speeding up your own Windows Vista computer, watch this PC user's guide.

Misplace your Microsoft Windows Vista Recycle Bin? Looking for instructions on how to replace it? It's easy! So easy, in fact, that this free home computing how-to can present a complete (and somewhat talky) overview of the process in just under a minute's time. For specifics, and to recover your own Vista Recycle Bin, watch this PC user's guide.

Want to speed up a Microsoft Windows Vista PC? Have a USB drive? This PC user's guide from CNET TV demonstrates how to take advantage of Windows Vista's Readyboost feature to convert your flash drive into extra virtual ram for your computer. For specifics, and to get started speeding up your own sluggish Vista PC, watch this handy how-to.

In this video tutorial. viewers learn how to change the size of text and icons in a Windows 7 computer. Begin by clicking on the Start menu and open Control Panel. In the Control Panel window, click on Appearance and Personalization. Then click on Display. Now users are able to select the size of text and icons to Smaller - 100%(default), Medium - 125% and Larger - 150%. If users select one of the larger sizes, some of the items will not fit on the screen. Once users have select the setting, ...

In this video tutorial, viewers learn how to do math with an ice cube tray. Users will need a ice cube tray and counting coins. Users can also substitute the coins for any kind of small counting item that will fit into the tray. There are several ways for the child to do math with the tray such as the teacher directed activity where the teacher gives out an amount of a number and the child would have to count that much using the tray. Users can also use flash cards to solve numbers and simple...

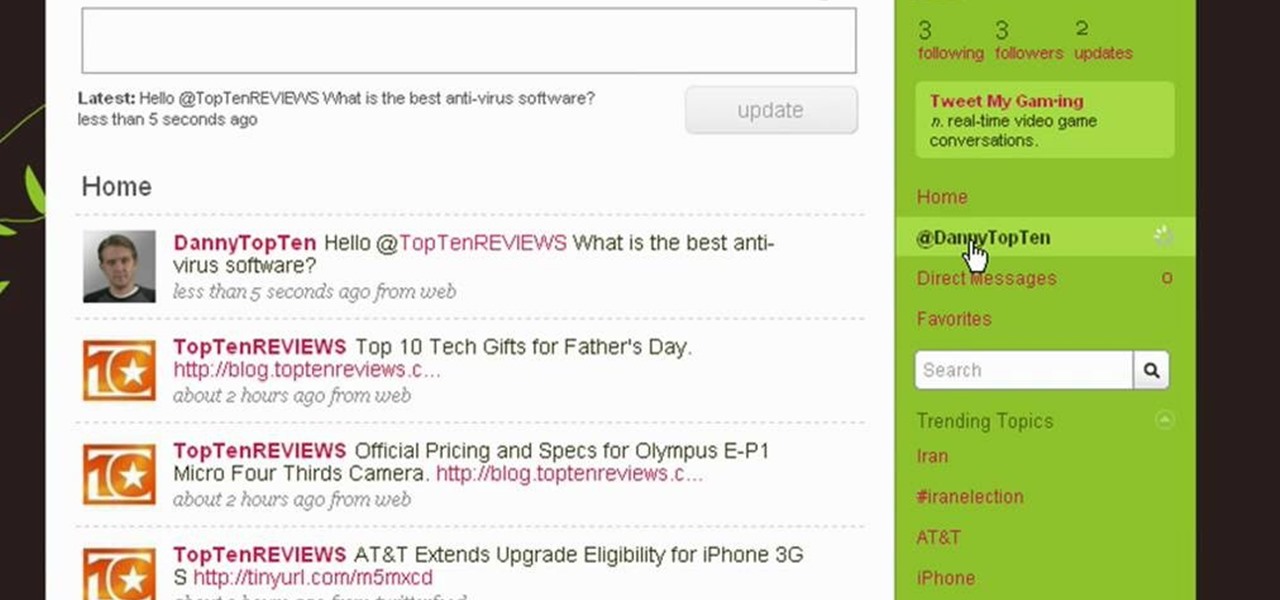
Twitter is a powerful social networking website which can be used to update you friends on what you are doing. To send different messages through twitter you will need a twitter account. Twitter account can be registered for free. Log in to your twitter account and go to your home page. There is a text box provided at the top with the text 'What are you doing?'. Enter the message you want in the text box provided. Click update and this message will be shown to all the people that are followin...

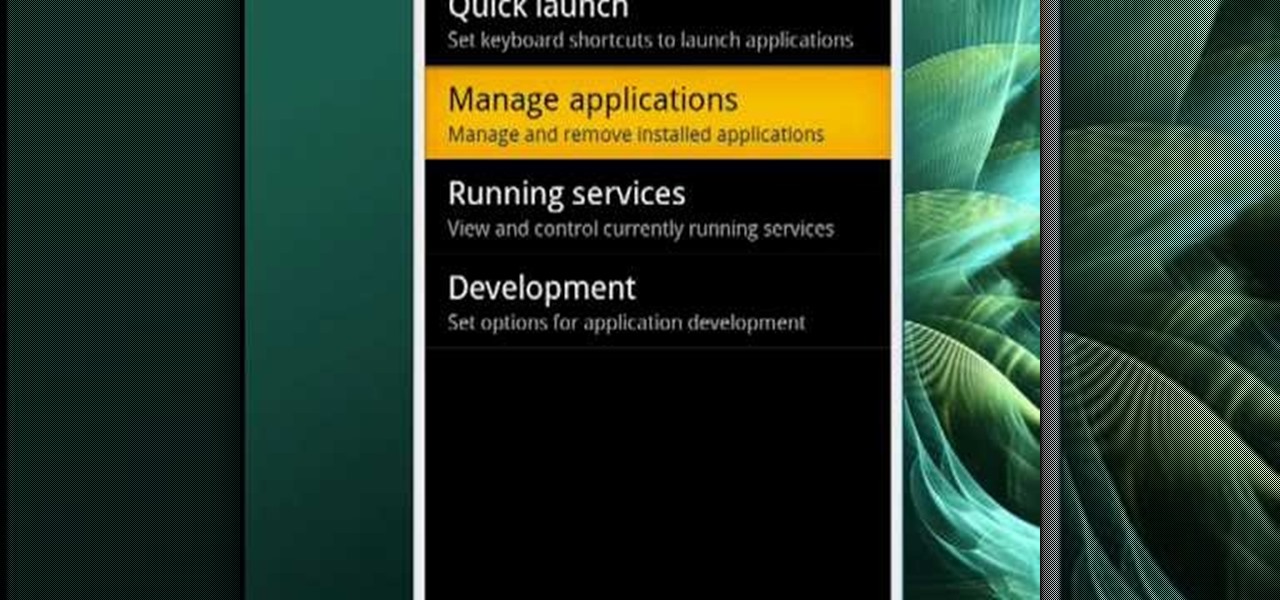
In this video tutorial, viewers learn how to uninstall the program on an Android phone. Begin by clicking on Settings and select Applications. Click on Manage applications. Now users will be revealed a list of all the applications that are installed on the phone. Simply scroll through the applications and select the unwanted application(s). Users will now see the information about the application, click on Uninstall. Now click OK and click OK again when the application is finished uninstallin...

In this video tutorial, viewers learn how to perform hanging knee ups. This exercise targets the abdominal muscles. Users will need to use a smith rack for this exercise. Begin by hanging on the top of the smith rack. Users should have a bar behind the rack that will support the back area. While hanging, users will point the chin down and bring the knees up. Then raise the chin up and bring knees down. Continue performing this movement in a series of sets and repetitions. This video will bene...

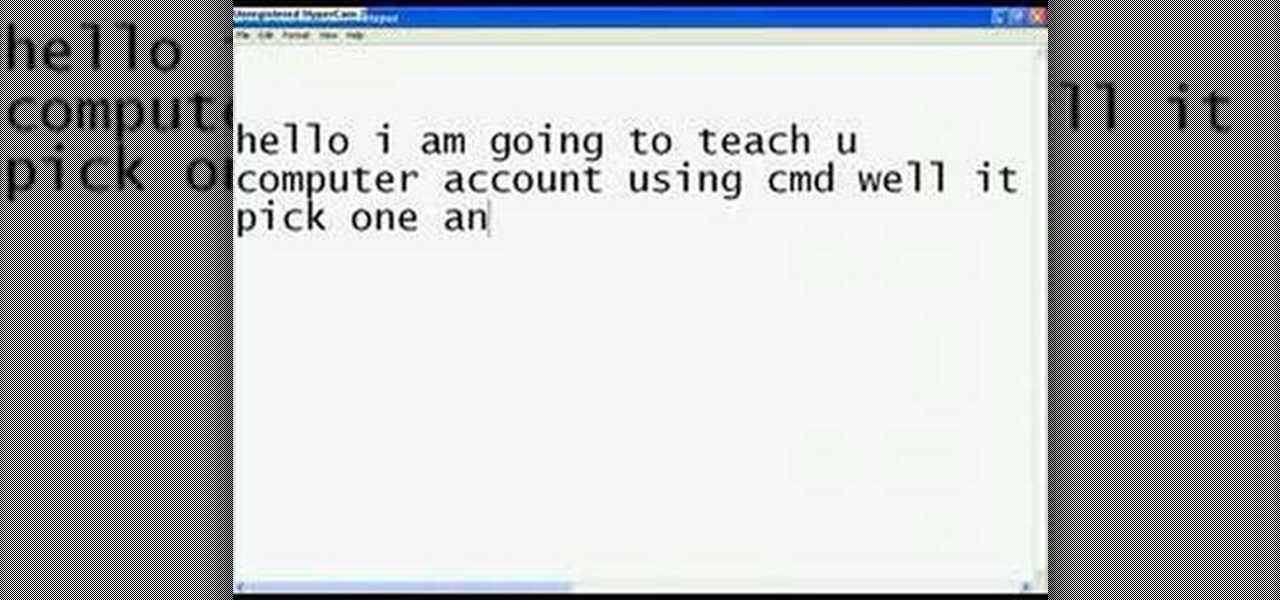
This video teaches you how to change your computer's account password using the DOS command prompt. The first step is to get to the command prompt, you can do this simply by clicking run in the start menu and typing "cmd." You next type "net user" which will show you all of the user accounts on the computer. Choose the one you would like to change the password for and type "net user (account name)." It will then ask you for a new password, you may type anything you like here keeping in mind t...

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

The developer who gained notoriety for his What Disney Are You? augmented reality filter on Instagram is striking again while the iron is hot.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

When it comes to augmented reality apps, visually immersive experiences are plentiful, but audio experiences are somewhat underrepresented. A new app for iPhones and iPads seeks to shift the AR paradigm toward the latter.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

For social media platforms like Facebook, augmented reality represents a whole new art form with which users can express themselves online. Now, Facebook is giving those users a new brush.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

BlackBerry's focus on secure software and their new partnership with manufacturer TCL are two of the biggest factors in their recent resurgence. Last year, the company announced two new devices — the KEYone and the BlackBerry Motion. The KEYone has been available for a while, but after months of waiting, BlackBerry announced the Motion will hit US shores in a few days.

Snapchat has broken new ground in its augmented reality advertising efforts, as BMW has opted to show off its new X2 model in AR with the Augmented Trial Lens.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Apple has sprung a massive AR following since the announcement of their ARKit, with users waiting to see what exactly the tech giant will do next.

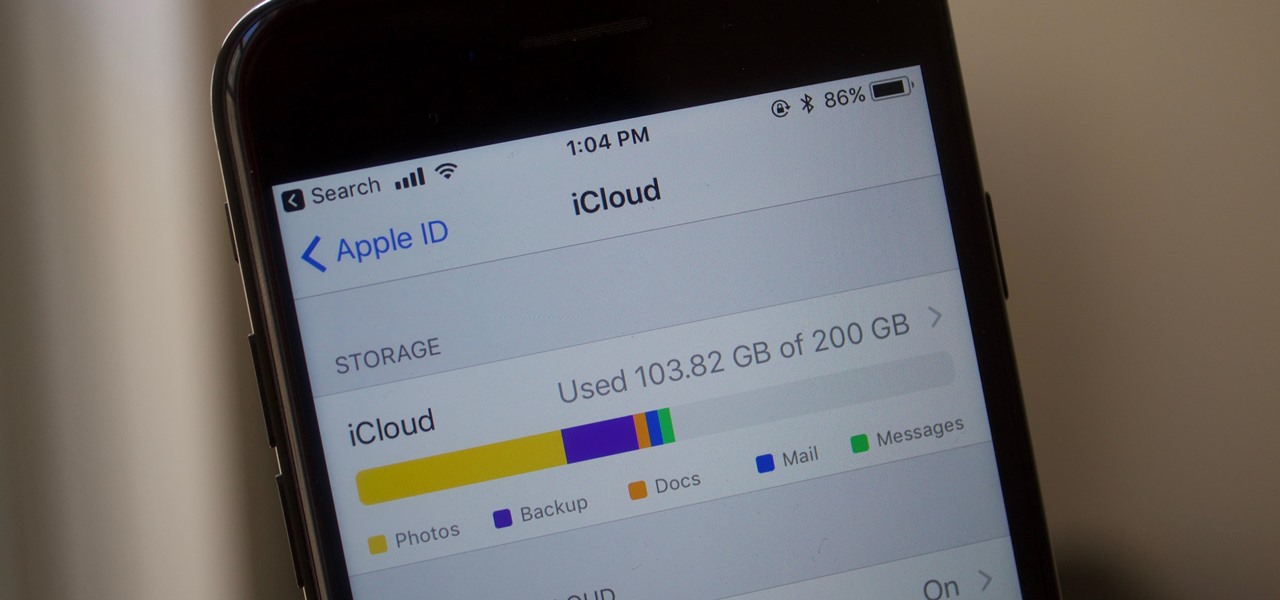
iCloud can occasionally be the worst part of being an Apple user. It's useful for backing up your information, however, sometimes the problems that stem from Apple's cloud service are so tremendously frustrating they almost seem intentional. Well, buckle in, because it's possible there may be a widespread login issue.

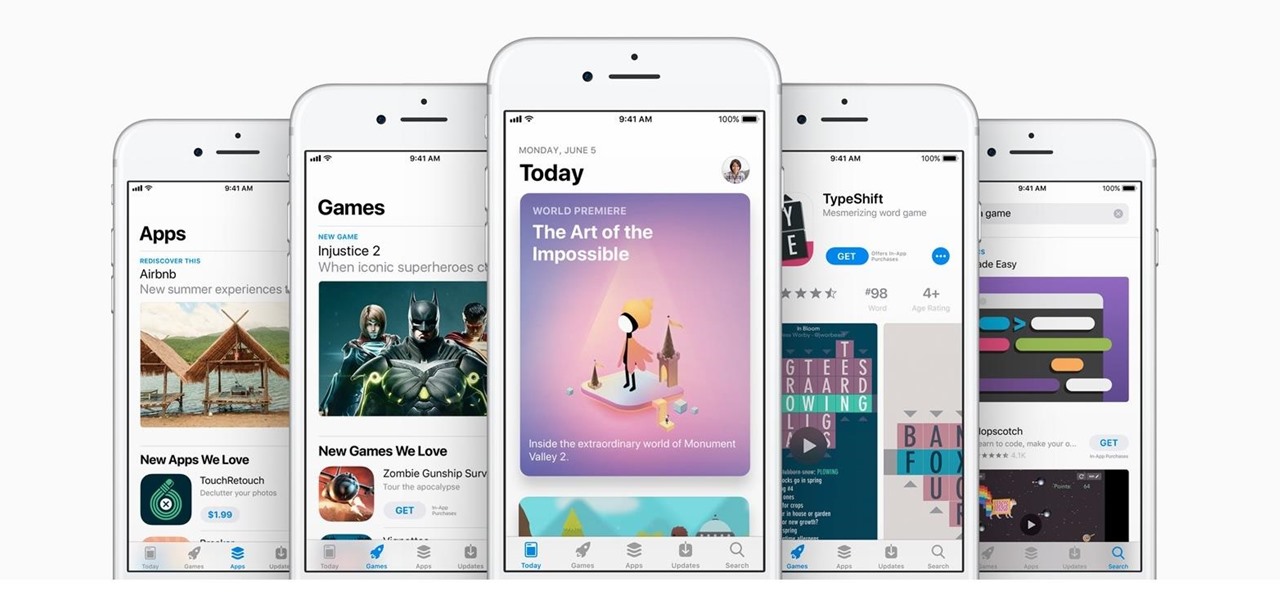
In the changes to the App Store Review Guidelines for iOS 11, Apple has announced that developers must use the App Store rating API. The API was introduced in the iOS 10.3 beta period as something that would eventually become mandatory. Now, Apple has followed through on that promise.