In February, the popular Facebook-owned WhatsApp Messenger service jumped on the "stories" bandwagon and replaced their in-app, text-based "About Me" status (you know, those lovely little messages where you can say "Sleeping" or "Not Sleeping" under the tiny nub of your profile picture). Taking its place was a clone of Snapchat's Stories feature, continuing the social media giant's recent trend of shamelessly copying Snapchat.

In recent weeks, thousands of Nexus 6P users have reported that their devices are shutting down with 30% or more battery life remaining. The phones won't start back up until they're plugged into a charger, so it's as if the battery completely dies even though there is plenty of juice left.

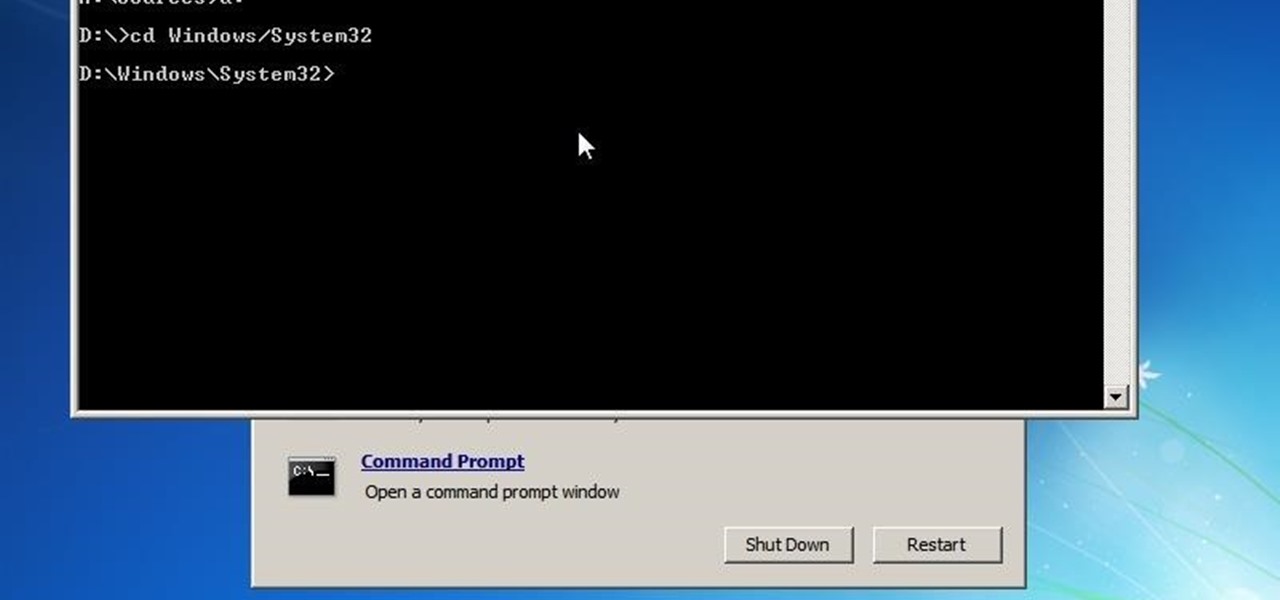
This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

HoloLens users will have a handful of ways to interact with the mixed-reality, holographic world. Gaze Input lets the user control a cursor in their field of vision. In other words, it's essentially a mouse that you control by looking around.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

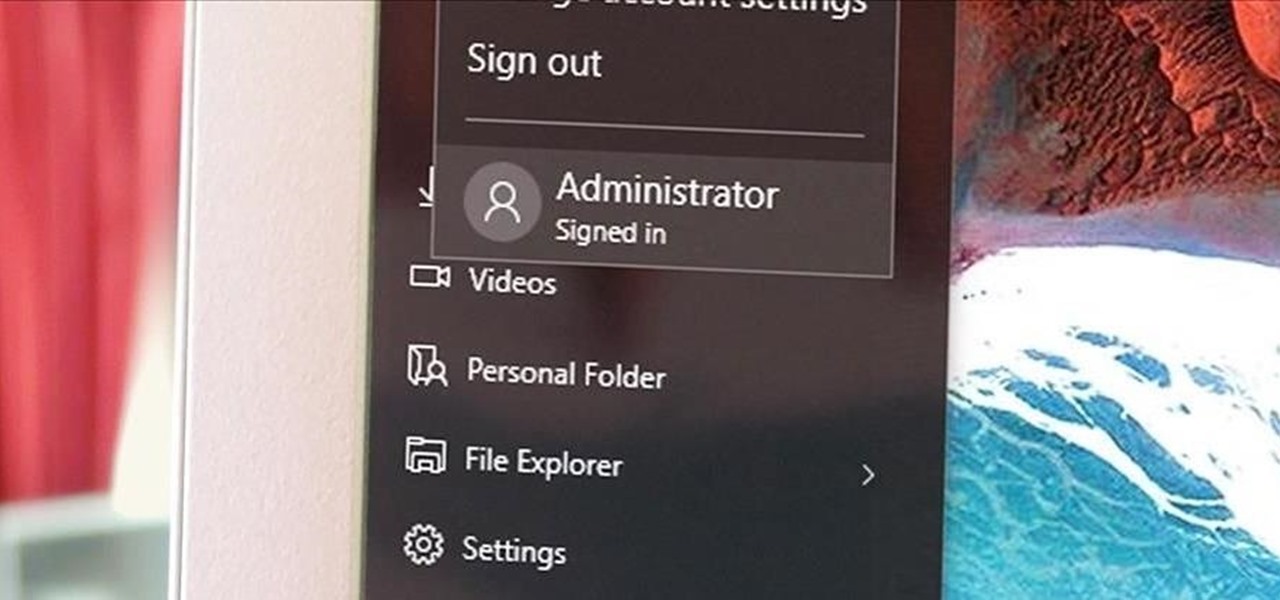
Windows has always had an "Administrator" account that allowed you to install programs and manage system files with elevated privileges. The difference between this account and a regular user account with administrator access was that you never got bothered by annoying User Account Control popups when you were logged in as Administrator.

Hello everyone! I'm glad to post my first tutorial and hope you will appreciate it.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

As with any software, Android apps can occasionally suffer from bugs. But finding the root cause of such issues can often be difficult, and reporting bugs is a cumbersome experience.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

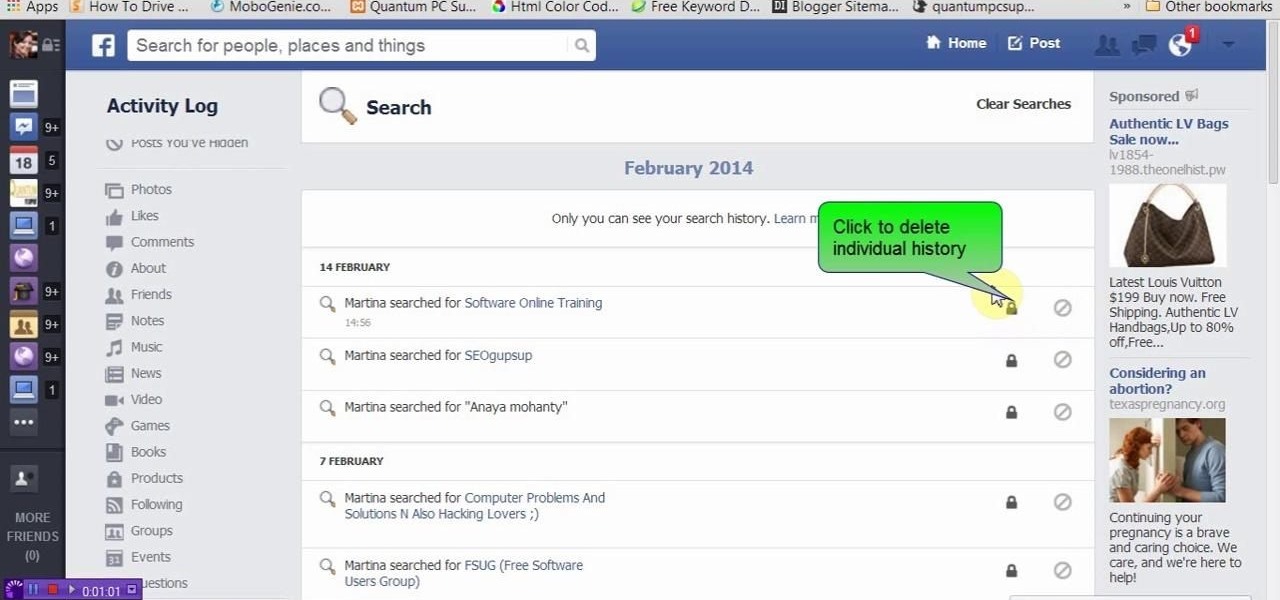
This video will show you how to delete or view Facebook search history. Facebook saves its user search history. User could view and delete this search history. Watch the video and follow all the steps to do it yourself.

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

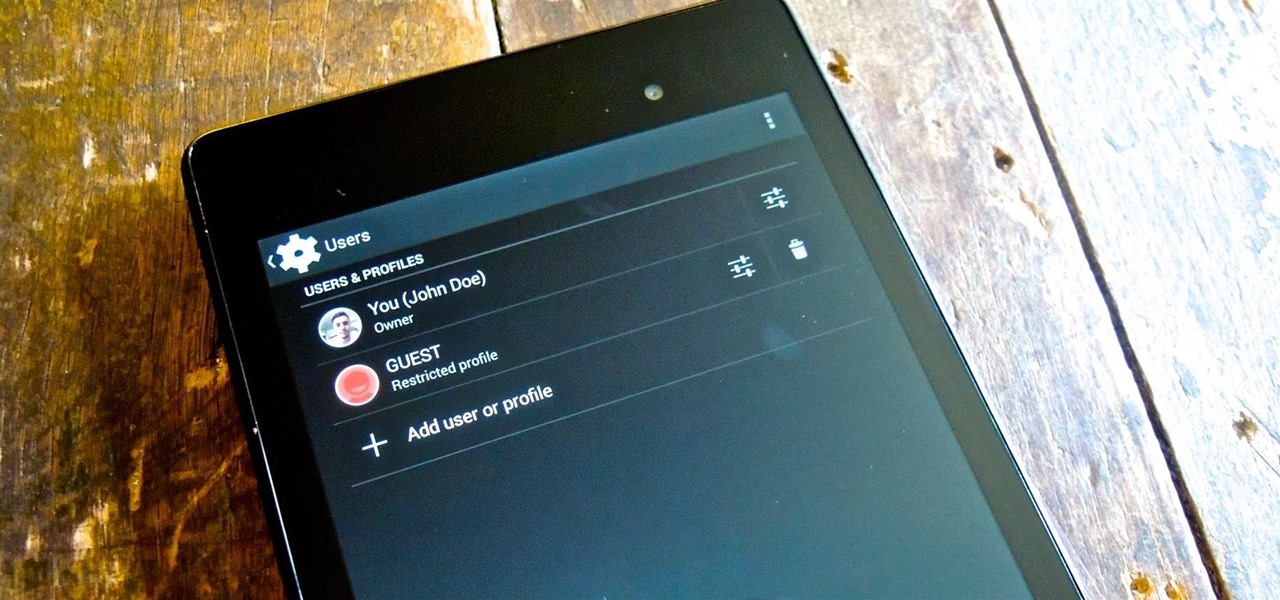
Whenever I hand my tablet over to someone, my heart always races for a second at the thought that they may stumble across my private pictures, texts, and videos. I trust them, and they may not be the snooping type, but it can be easy enough to come across private stuff by accidentally opening a gallery or messaging app.

Currently, all Nexus tablets running Jelly Bean or higher can enjoy multiple user accounts. With tablets often migrating between various people in the same household, there’s no reason for Dad’s finances to mingle with little Tammy’s candy crushing. Multiple users, each with separate profiles, just makes sense on an Android tablet.

Just days after news spread that Snapchat could be exploited by spammers, an anonymous group of hackers have released the private information of over 4 million users of the popular photo-sharing application.

This video will show you how to use top 10 tips and tricks for windows7 users. This video includes 10 useful windows 7 tricks for windows 7. Just follow the easy steps to implement yourself.

Welcome back, my tenderfoot hackers! This is the third installment of my series on basic Linux skills that every hacker should know. Although some hacking tools are available for Windows and Mac, every real hacker uses Linux—for good reason.

Video: . Optimize your Marketing with a Mobile Website

It's been a rough week for Instagram. First they came out with a new terms of service that suggested the right to let companies use people's photos for advertisements without the user's permission. Then everyone started freaking out and debating whether or not to leave the online photo-sharing and social networking service. Now, they've changed the controversial wording saying that the selling of user photos "is not true and it is our mistake that this language is confusing".

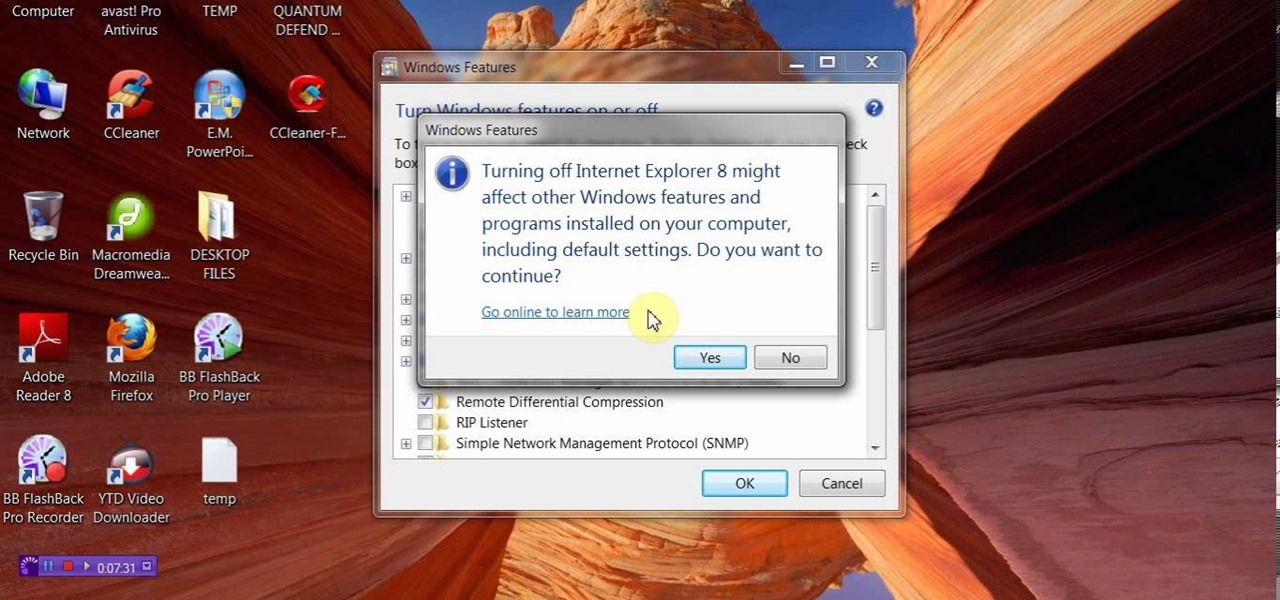
Microsoft's updated web browser, Internet Explorer 10, has only been out for a few days on Windows 8, and there is already a storm of controversy surrounding its launch.

Yesterday, we pointed out that hackers could remote-wipe certain Android-based Samsung smartphones like the Galaxy S III using a USSD exploit. All they have to do is hide a small code into any webpage or text—even barcodes—then once you click on it, the phone resets to factory settings in a matter of seconds. The video below shows just how easy it is.

If you use apps on your smartphone, chances are you have no idea what those apps are doing with your information. Just this year, there have been several scandals involving apps transmitting user data, like Path uploading users' entire address books onto its servers, HTC's Security Flaw, and Brewster exposing users' personal information (even Ashton Kutcher's). A new service called Mobilescope wants to make sure you always know where—and to whom—your data is going. Lots of apps copy your cont...

This is OSCAR, the Overly Simplified Collaboratively Actuated Robot. He's built from an old Roomba and an Android tablet, and he's about to make Google+ a lot more interesting. The robot is controllable by users in a Google+ Hangout, allowing the audience to interactively explore OSCAR's environment via his on-board camera.

Hello, today I will tell you about how you can create a page through wordpress. this is a performance for those who have scarcely been touched wordpress. This guide will put you through basis and create a user and a website among millions of people.

The user demonstrates how to draw Disney's Eeyore in this video. The first step is to draw a circle about the size of a 50 cent piece for his head and add construction lines to it, including one across the lower part of the circle to use as a reference. The user also suggests creating a mark below the "head" to mark where the end of Eeyore's jaw will be. Then, starting at the bottom cross line, he begins drawing the rounded area of his snout. Next, he draws a straight line from the other side...

Are you playing through Dark Souls and having flash backs to all those times you died in Demon Souls? IGN is here to help you with several tips and tricks on surviving. This guide shows you good spots to grind, what gift to pick for your character, and where to get the Sorcerer's Catalyst item that will allow you to cast magic in the game, even if you aren't a magic user.

Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does make backup files of everything, so eventually everyone will reclaim their email history. In fact, as of yesterday, Google has successfully restored all information from their backup tapes and has started returning everyon...

The spider boss known as Chaos Witch Quelaag can be a difficult boss to defeat. However, this IGN guide will help you out, especially if you are a magic user. Also, it helps to bring a friend or NPC to help you beat the Chaos Witch.

If you're a Google Chrome user, you can remove the annoying Facebook news ticker recently implemented on the site with this quick trick. So if you find the news ticker annoying, this how to guide on how to hide it will clean up your Facebook just the way you want.

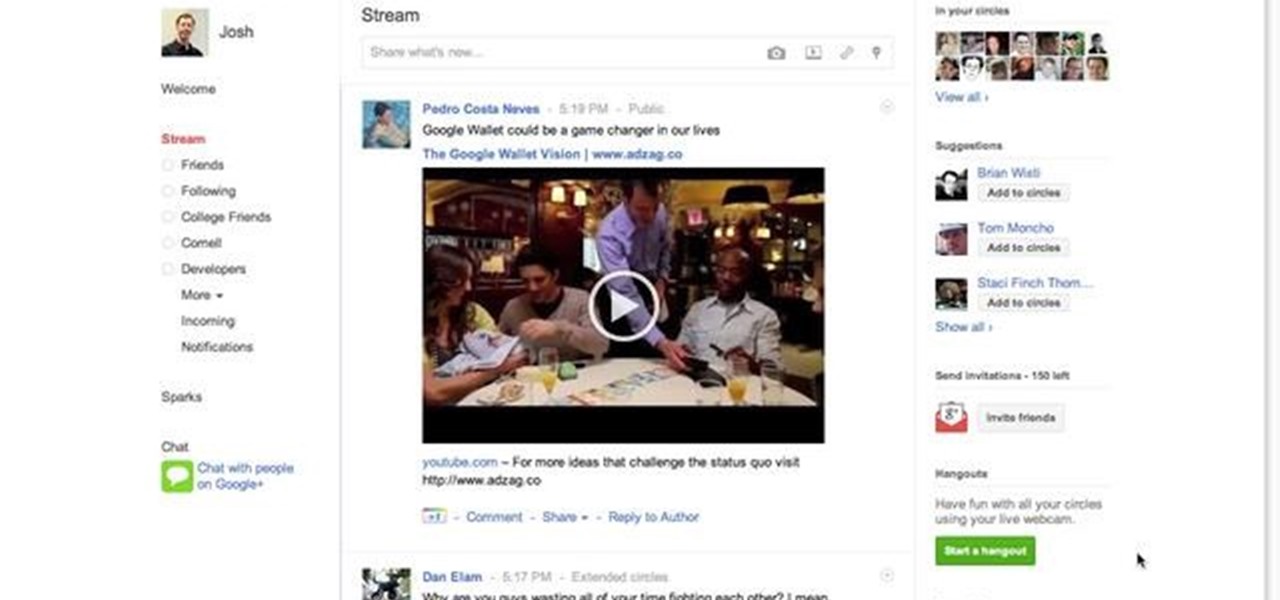
The Hangouts feature of Google+ allows you to interact with and talk to different Google+ users and circles via your webcam. Hangouts is a great way to have a video conference with several different individuals and is similar to the Group Call feature of Skype.

If you're new to Google+ and want to know how photos that are uploaded by Google+ users can be browsed or viewed, take a look at this tutorial. You can use the arrow keys to navigate the Google+ photo galleries, or simply click on the photos at the bottom of the lightbox.

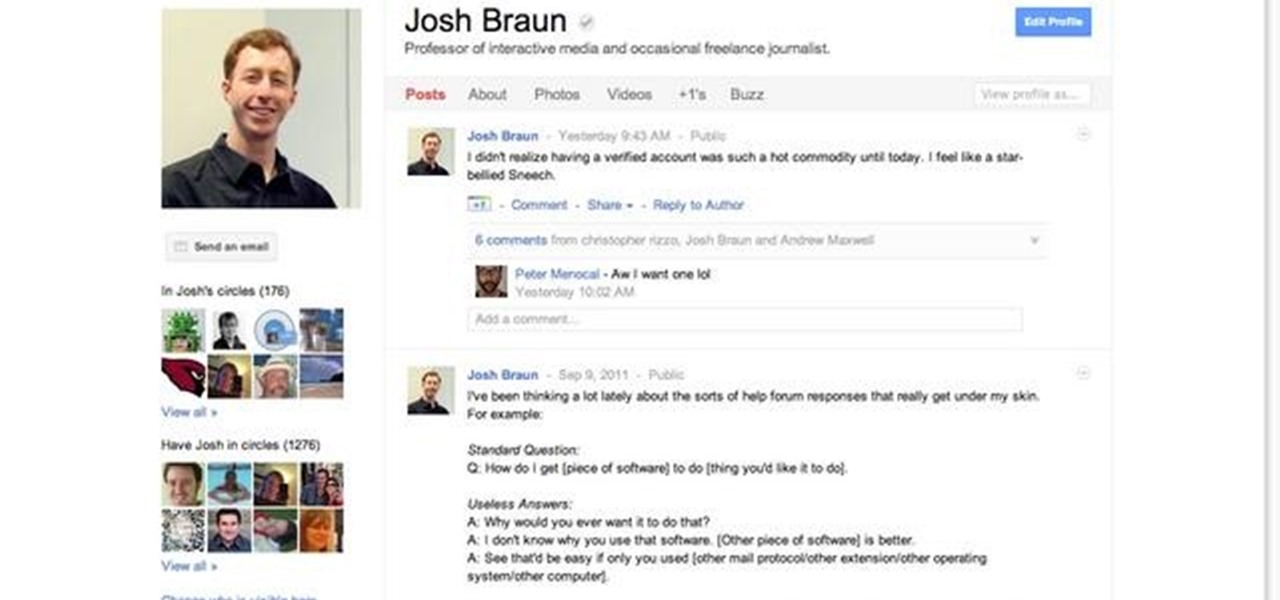
The profile pages on Google+ allow you to represent yourself in unique ways to other Google+ users. If you want to edit the information displayed on your Google+ profile, such as the title that appears under your name or who is visible in your circles.

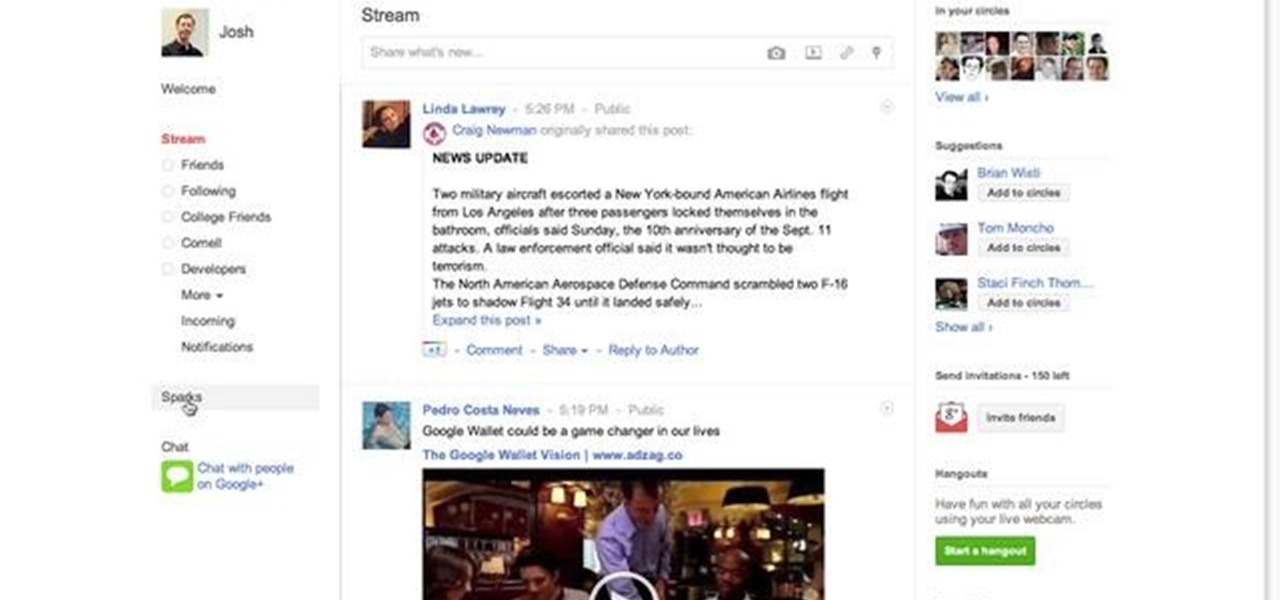
The Google+ Sparks feature is a kind of social search that allows you to find and read different articles and websites that have been selected by the people you follow and other Google+ users. It can help you find interesting posts and information on a specific topic.

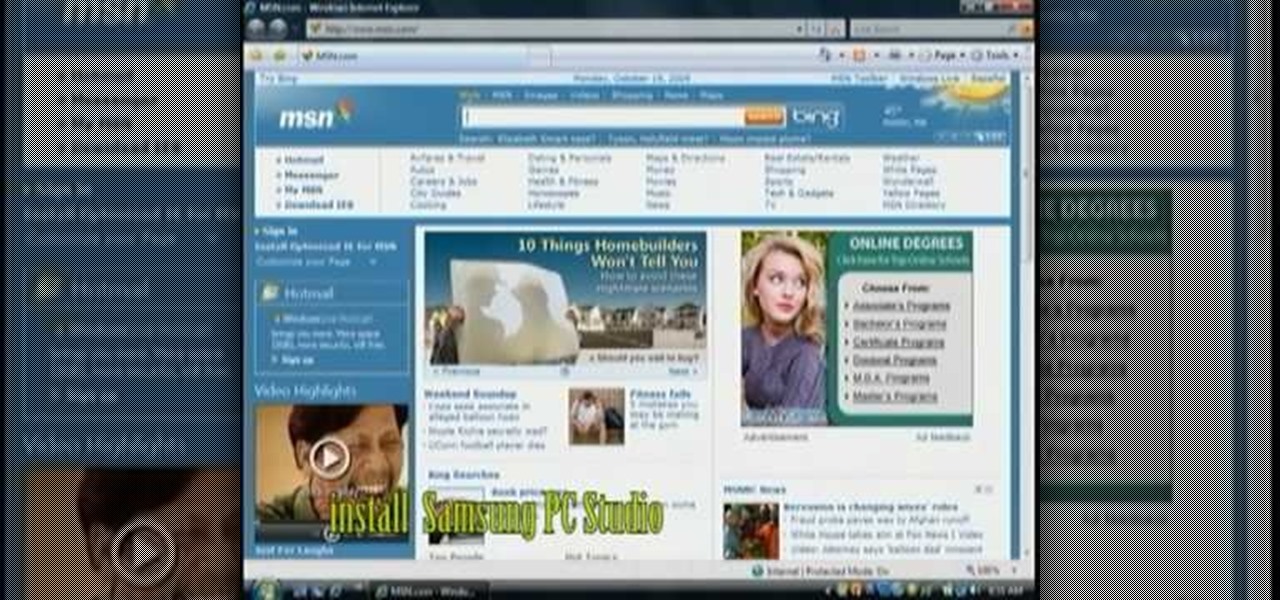
If you're a MetroPCS user and would like to tether your phone to your PCS to use it as a modem, this video will show you how it's done. First of all, hit the subtitles button to make sure you're getting the instructions in english. Next, you'l want to go here to get the Samsun PC Studio link tool which will let the connection be made. Enjoy!

The Newstweek might be the coolest new device of 2011 that no one is talking about. It's a pocket-sized device that allows you to access the data streaming through a wireless internet access point and change the news being read by fellow users at the hotspot, from any site, however you want. It allows you to do some amazingly inspiring and sinister things, like any really progressive technology, and this video will show you how to use it.

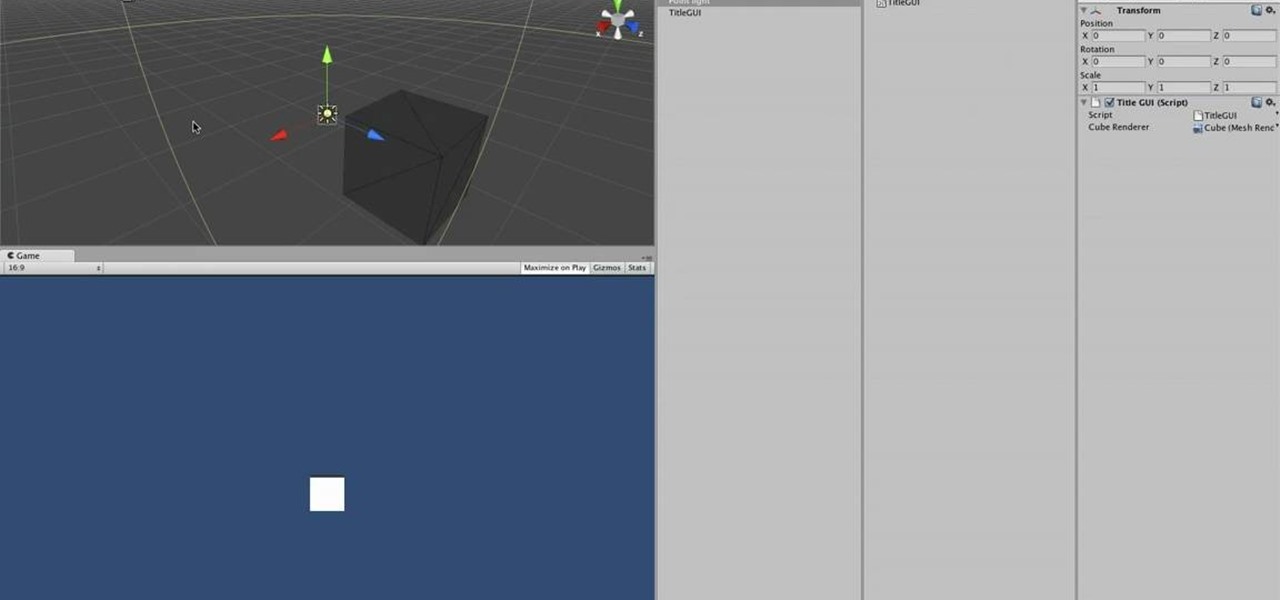
If you've already made a game using Unity3D and want to wrap it up with a nice GUI (or graphical user interface) (or menus) watch this video for a guide to making basic GUI elements using the built in ones in Unity3D.