In February, the popular Facebook-owned WhatsApp Messenger service jumped on the "stories" bandwagon and replaced their in-app, text-based "About Me" status (you know, those lovely little messages where you can say "Sleeping" or "Not Sleeping" under the tiny nub of your profile picture). Taking its place was a clone of Snapchat's Stories feature, continuing the social media giant's recent trend of shamelessly copying Snapchat.

In recent weeks, thousands of Nexus 6P users have reported that their devices are shutting down with 30% or more battery life remaining. The phones won't start back up until they're plugged into a charger, so it's as if the battery completely dies even though there is plenty of juice left.

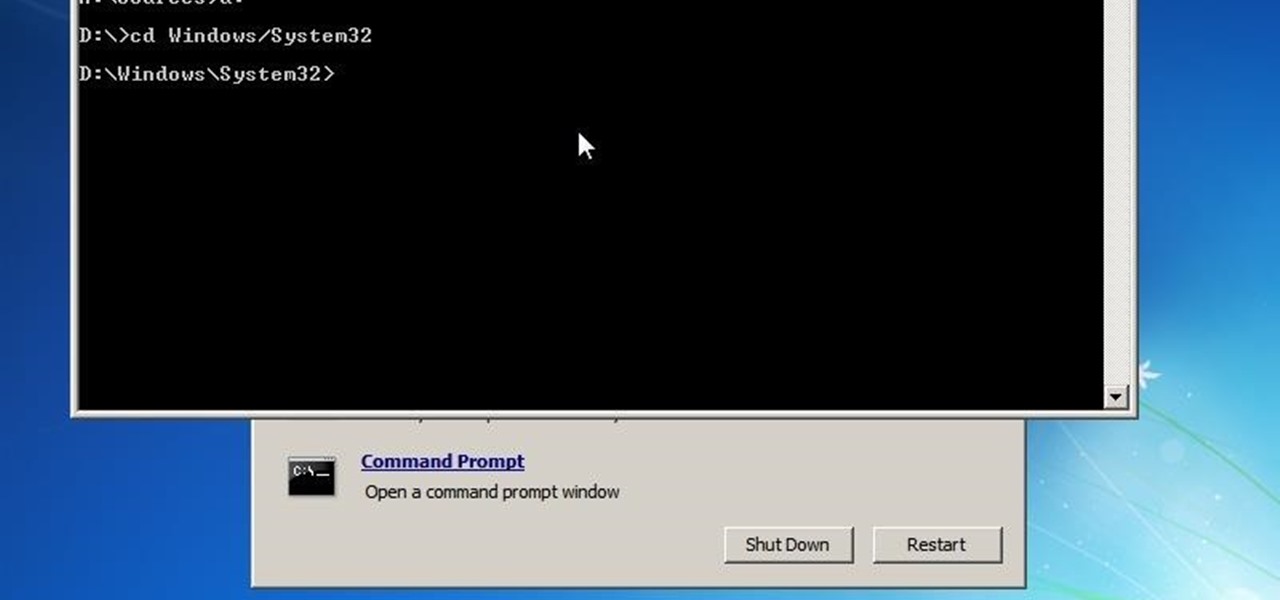
This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

Windows has always had an "Administrator" account that allowed you to install programs and manage system files with elevated privileges. The difference between this account and a regular user account with administrator access was that you never got bothered by annoying User Account Control popups when you were logged in as Administrator.

Hello everyone! I'm glad to post my first tutorial and hope you will appreciate it.

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

As with any software, Android apps can occasionally suffer from bugs. But finding the root cause of such issues can often be difficult, and reporting bugs is a cumbersome experience.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

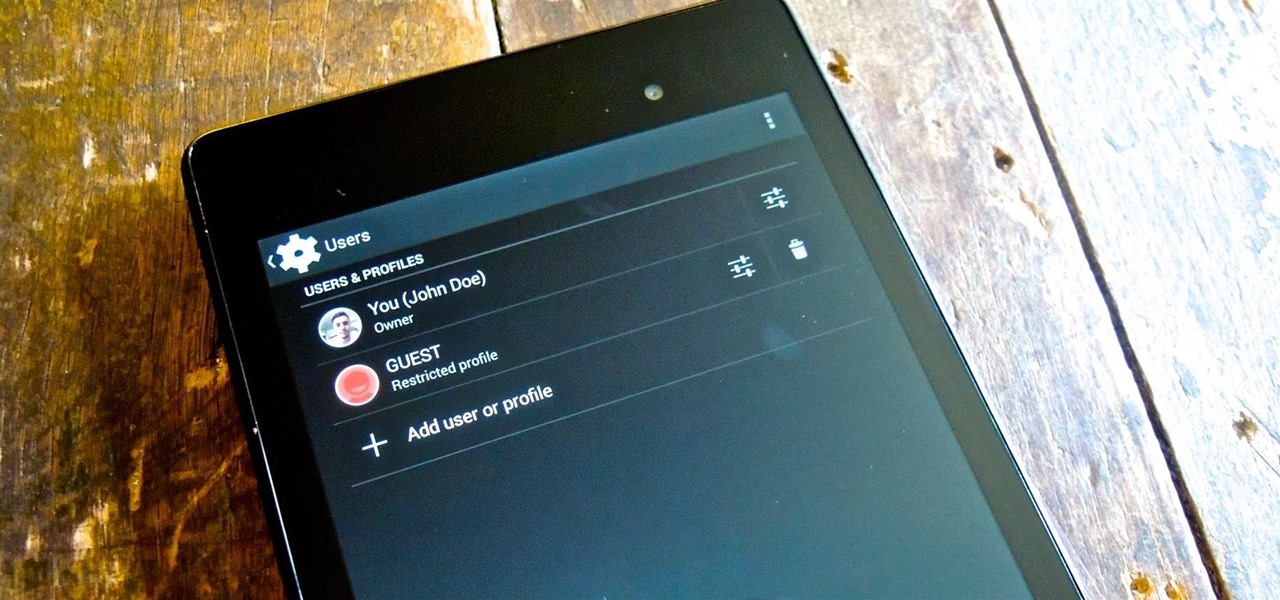
Whenever I hand my tablet over to someone, my heart always races for a second at the thought that they may stumble across my private pictures, texts, and videos. I trust them, and they may not be the snooping type, but it can be easy enough to come across private stuff by accidentally opening a gallery or messaging app.

Currently, all Nexus tablets running Jelly Bean or higher can enjoy multiple user accounts. With tablets often migrating between various people in the same household, there’s no reason for Dad’s finances to mingle with little Tammy’s candy crushing. Multiple users, each with separate profiles, just makes sense on an Android tablet.

Just days after news spread that Snapchat could be exploited by spammers, an anonymous group of hackers have released the private information of over 4 million users of the popular photo-sharing application.

Video: . Optimize your Marketing with a Mobile Website

It's been a rough week for Instagram. First they came out with a new terms of service that suggested the right to let companies use people's photos for advertisements without the user's permission. Then everyone started freaking out and debating whether or not to leave the online photo-sharing and social networking service. Now, they've changed the controversial wording saying that the selling of user photos "is not true and it is our mistake that this language is confusing".

Microsoft's updated web browser, Internet Explorer 10, has only been out for a few days on Windows 8, and there is already a storm of controversy surrounding its launch.

Yesterday, we pointed out that hackers could remote-wipe certain Android-based Samsung smartphones like the Galaxy S III using a USSD exploit. All they have to do is hide a small code into any webpage or text—even barcodes—then once you click on it, the phone resets to factory settings in a matter of seconds. The video below shows just how easy it is.

If you use apps on your smartphone, chances are you have no idea what those apps are doing with your information. Just this year, there have been several scandals involving apps transmitting user data, like Path uploading users' entire address books onto its servers, HTC's Security Flaw, and Brewster exposing users' personal information (even Ashton Kutcher's). A new service called Mobilescope wants to make sure you always know where—and to whom—your data is going. Lots of apps copy your cont...

Hello, today I will tell you about how you can create a page through wordpress. this is a performance for those who have scarcely been touched wordpress. This guide will put you through basis and create a user and a website among millions of people.

The user demonstrates how to draw Disney's Eeyore in this video. The first step is to draw a circle about the size of a 50 cent piece for his head and add construction lines to it, including one across the lower part of the circle to use as a reference. The user also suggests creating a mark below the "head" to mark where the end of Eeyore's jaw will be. Then, starting at the bottom cross line, he begins drawing the rounded area of his snout. Next, he draws a straight line from the other side...

Need to divert a little rain water fall from falling off of your roof? Let home improvement expert Danny Lipford show you how to install a rain diverter on your home's eave.

Are you playing through Dark Souls and having flash backs to all those times you died in Demon Souls? IGN is here to help you with several tips and tricks on surviving. This guide shows you good spots to grind, what gift to pick for your character, and where to get the Sorcerer's Catalyst item that will allow you to cast magic in the game, even if you aren't a magic user.

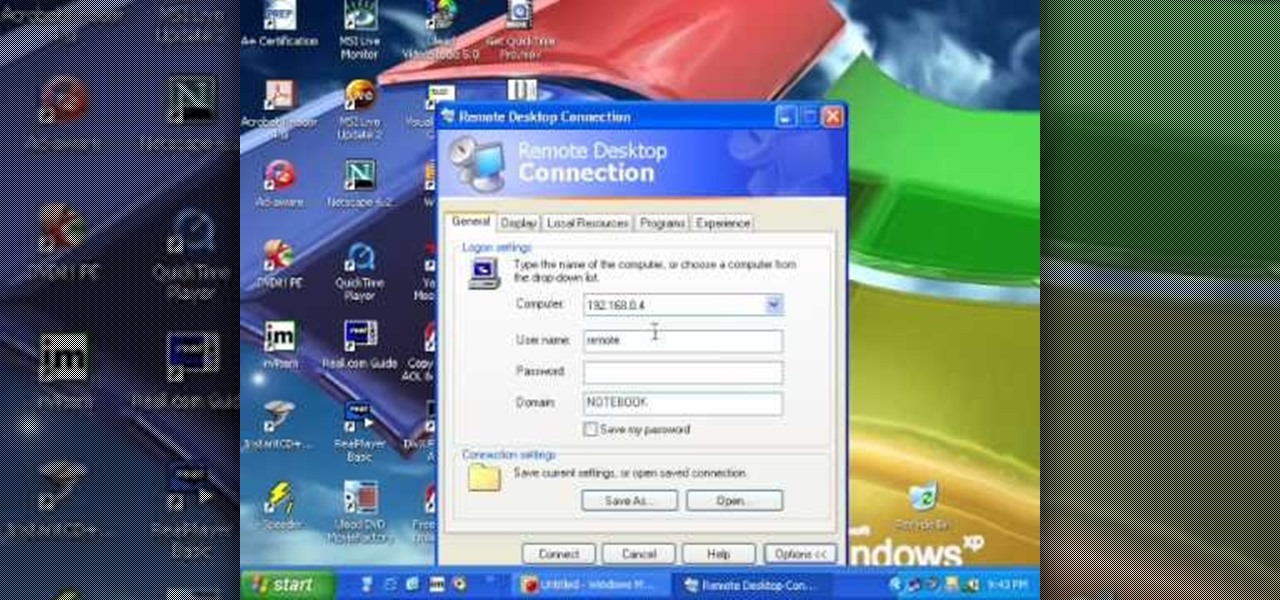
This video from Michael presents how to establish a Remote Desktop connection in Windows XP Professional.This type of connection allows you to access your computer via Internet from any place and manage files, local resources, or perform any other remote activity.To establish Remote Desktop connection click Start button, right click My Computer, from the opened menu select Properties. System Properties window will open. Choose Remote tab. Check Remote Desktop - Allow users to remotely connect...

Use this path: C:\Users\USER\Documents\My Games\Terraria\Worlds to find your Terraria world. This will allow your to export and share Terraria worlds with your friends. Follow the instructions in this video and you'll be able to play Terraria as a member or the online community.

In this clip, you'll learn how to create a new user on a desktop or laptop computer running the MS Windows Vista operating system. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.

A scrollbar adds a little bit of user interactivity to your website, letting visitors navigate and helping you optimize page space as well. This tutorial shows you how to utilize the scrollbar component when you're building a website in Adobe Flash CS3.

In this clip, you'll learn how to use the iPad Papers application to annotate any PDF file. Whether you're the proud owner of an Apple iPad or perhaps just considering picking one up, you're sure to benefit from this free video tutorial. For more information, including a detailed overview, watch this iPad user's guide.

In this video tutorial, viewers learn how to disable ads with the Ad Block Plus add-on in Mozilla Firefox. Begin by going to the Firefox add-on site and search for "ad block". Then click on "Add to Firefox" to install it. Once installed, users will be able to block out any advertisements. Users are able to add a filter subscription. To block an image, right-click on the image and select "Ad Block Image". Users are able to customize their ad block filters to only allow certain advertisements. ...

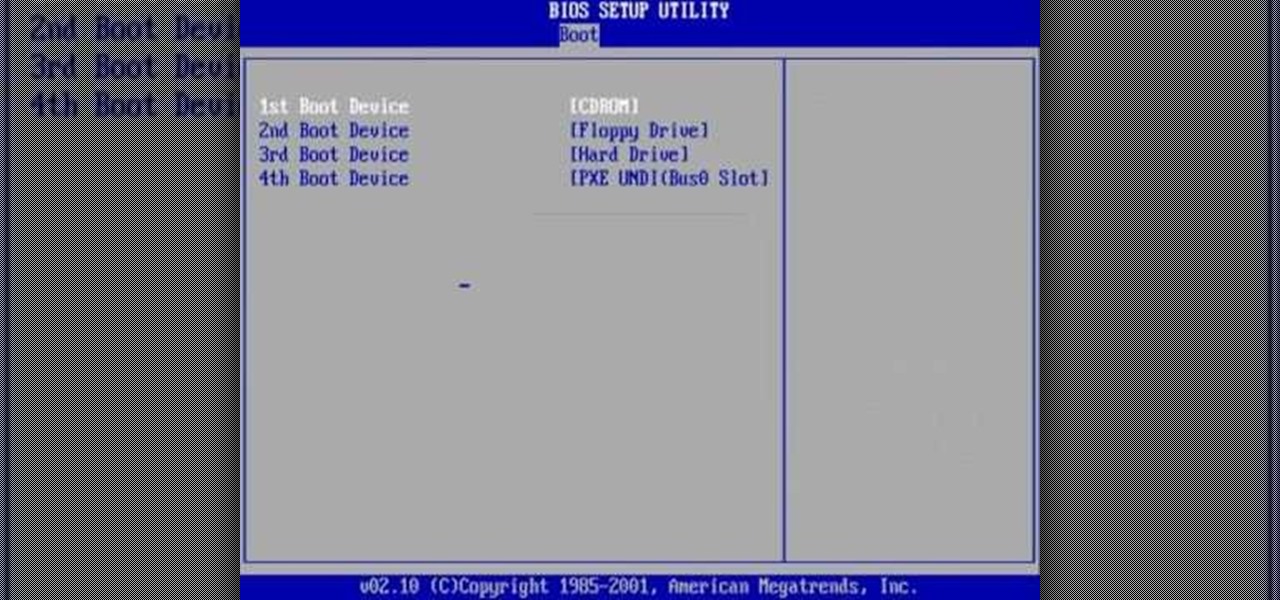
The video shows users how to change the boot sequence in a computer with an older AMI (American Megatrends, Inc.) BIOS to boot from the CD/DVD drive. This is required, for instance, if you need to reinstall an operating system, or fix a corrupted windows installation by running Windows Setup from the installation CD. Users should first enter the BIOS setup by pressing the delete key when prompted shortly after powering the computer on. Once the Bios Setup screen has loaded, users may navigate...

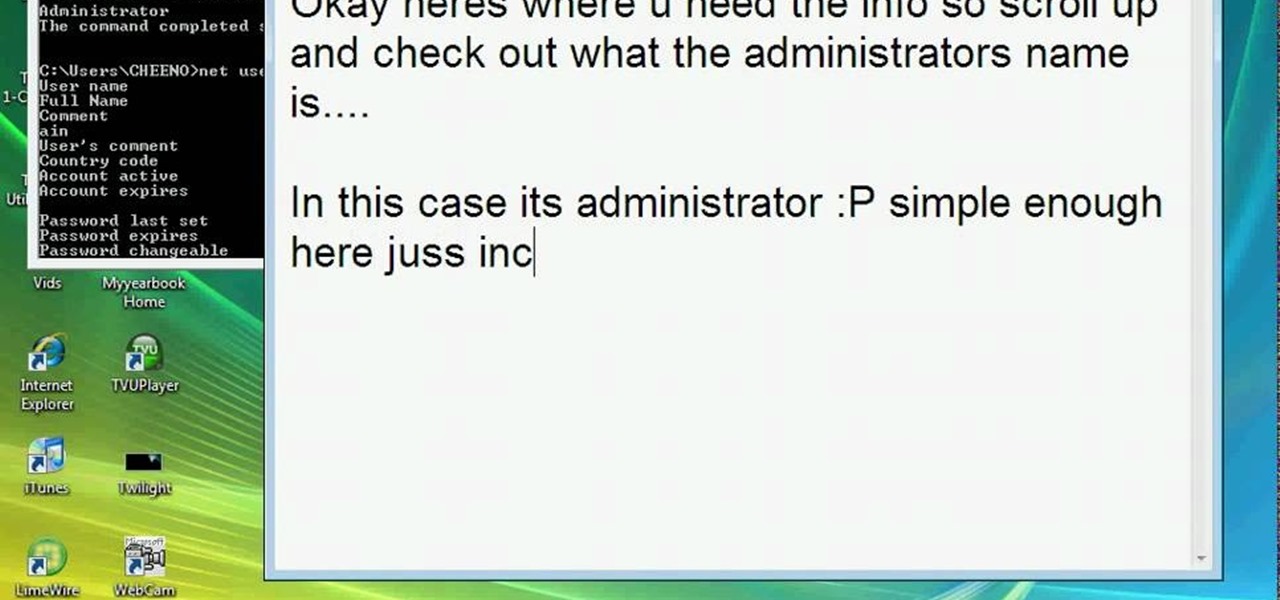
This video teaches how to change/hack administrators Account/Password. Click START and find CMD. Type "net user" without the "". Now type "net user administrator" without the "". Scroll up the screen and find the administrator's name. Now go back down and type "net user administrator *" without the "". Now it will ask you for a new Password. Type a new Password which you won't forget. Now another command prompt will pop up. Just type in exit to come out of the CMD. Don't get caught and do it ...

Many seasoned users of Microsoft Excel, who have been using spreadsheets for years, still scroll through their spreadsheets, laboriously, with the horizontal and vertical scrollbars. In this software tutorial, you'll learn how to navigate around in Excel both quickly and efficiently. For more, take a look!

MySQL is a multithreaded, multi-user SQL database management system which has over 10 million installations. It runs as a server providing multi-user access to databases. It is by far the most popular and common database used in web applications throughout the world, and almost all hosting companies provide it free of charge to their users. MySQL AB makes MySQL Server available as free software under the GNU General Public License (GPL). For this tutorial we are going to download and install ...

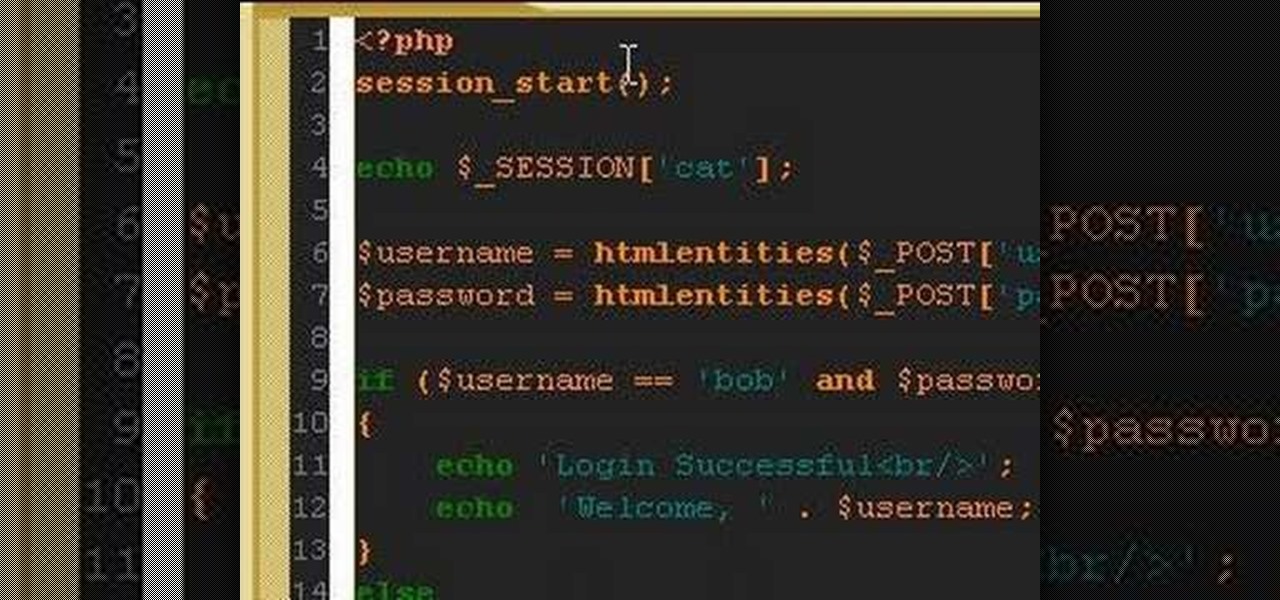
A PHP programming tutorial on creating login sessions to keep users logged in.

iMovie allows the average computer user the ability to quickly make movies out of your digital video footage or home movies. This is not the most professional way to color correct your footage, but it should be sufficient for the average Mac user. Follow along and see how to adjust color using iMovie.

Important emails can slip through the cracks in any email client, especially sent emails you were expecting responses to but never received — and ultimately forgot about. Apple has an easy solution for this problem, helping you get answers in Mail for all your pending questions.

There has been drag-and-drop functionality for iPhone since at least iOS 11, but iOS 15 adds a new ability that makes essential emails even easier to find when you need them.

A temporary email can go a long way. Using your actual email to sign up for a mailing list to receive 10% off a purchase doesn't make sense if you don't use the website much. It means you'll have to deal with spam emails from then on, which is why an anonymous email is perfect not to have to deal with all that trouble. And that's where the TempMail shortcut for your iPhone comes in handy.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.