Tinder, marketed as a free 'dating' app, is no stranger to paid features. The company has long allowed users to step up their game by spending money on their 'Tinder Plus' service. Tinder would like more of your money, it seems, as it rolls out a new paid service with a highly-desirable premium feature — the ability to see who has swiped right on your profile, without having to match.

When you're taking a video in the Camera app on your iPhone, there's a little white shutter button in the corner that lets you take a still image while you're filming. Apple brought that same concept over to the FaceTime app in iOS 11, iOS 12, and higher, so you can take Live Photos of your friends during video chats.

You seriously won't even recognize Twitter after this. Twitter has launched a major redesign, their first in years and it seems the app is finally starting to listen to what users are looking for — starting to being the keywords.
With the hype surrounding the iPhone 8, Apple's announcement that it's developing driverless software, and the new iOS 11 beta out, it seems like the tech giant is constantly in the news. Today, Apple's continuing this streak with updates for its iWork app suite on iOS and macOS.

New updates to the journaling app Day One include more security for journal writers' data. For example, users can now enable end-to-end encryption. The encryption does not happen automatically; however, users must go to Settings — within Journals — then select each journal they want encrypted.

After 6 years of development, the big banks seem to be ready to combat Venmo on the money sending frontier, but now it might be too late.

Love him or hate him, we all know President Trump has a strong presence on Twitter. Whether it's 3 pm or 3 am, the president is probably tweeting. His frequent Twitter habits are often discussed by the media, and they've especially caught the attention of lawyers at Columbia University ... but not in a good way.

Getting support for your mental health is now as easy as opening up Facebook Messenger. By just opening up the Messenger app, you can connect to Woebot, a new chatbot developed at Stanford trained in administering cognitive behavioral therapy (CBT).

Another entrant — Aryzon — has joined the competition to be crowned as the "Cardboard of AR." The Netherlands-based startup launched their Kickstarter campaign Monday (May 29) and the campaign has already surpassed its funding goal. The company expects to ship units to backers in September.

Sometimes it's impossible to concentrate — let alone direct your personal assistant Siri — when someone is blasting music on their phone or talking to thin air. I mean I'm loud, but not that loud.

Ben & Jerry's addicts rejoice: Microsoft just won a patent for AR glasses that could help to combat overeating. Physical restraint is still needed to keep me away from that ice-creamy goodness, but a little virtual voice saying 'DON'T DO IT' could definitely help when the cravings come.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications' clothing," infects Android users.

While there are many good reasons to update to Apple's newest mobile software, a bug has made it to where you may want to double-check your iCloud settings after doing so.

4DViews, the volumetric capture company that films actors and performers in augmented and virtual reality for things like movies, TV series, and applications, has just released the app 4DViews: Raise Virtual to Reality, to demonstrate its technology for smartphones.

Don't ignore the update sitting in your Settings app; you'd be leaving your iPhone's security vulnerable.

All you paying Spotify users are about to get another exclusive privilege besides getting out of all those annoying "Ever wonder what it would be like to have Spotify premium?" ads. The Sweden-based company is looking to lower the royalty fees they have to pay to major record labels for their music, by compromising on their policy that all their music be free to paying and nonpaying users. Spotify would for a limited time restrict access on major album releases to their paying subscribers.

In recent weeks, thousands of Nexus 6P users have reported that their devices are shutting down with 30% or more battery life remaining. The phones won't start back up until they're plugged into a charger, so it's as if the battery completely dies even though there is plenty of juice left.

It seems like a new, dangerous Android exploit is uncovered every month or two. The latest headliners are NightMonkey and Chronos from the list of CIA hacks reported by Wikileaks, which have been billed as gaping security holes in the world's biggest mobile operating system.

We can't be in two places at once, but with virtual touch interfaces we can theoretically use a machine to act as our second body in a remote location. Over at MIT, Daniel Leithinger and Sean Follmer, with the advisement of Hiroshi Ishii, created an interface that makes this possible.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

HoloLens users will have a handful of ways to interact with the mixed-reality, holographic world. Gaze Input lets the user control a cursor in their field of vision. In other words, it's essentially a mouse that you control by looking around.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Welcome hackers. Hackacademic.RTB1 is vulnerable machine for training our skills.This machine can be download from free from here. There is many tutorial how to hack these machine but i did always be my self.

Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

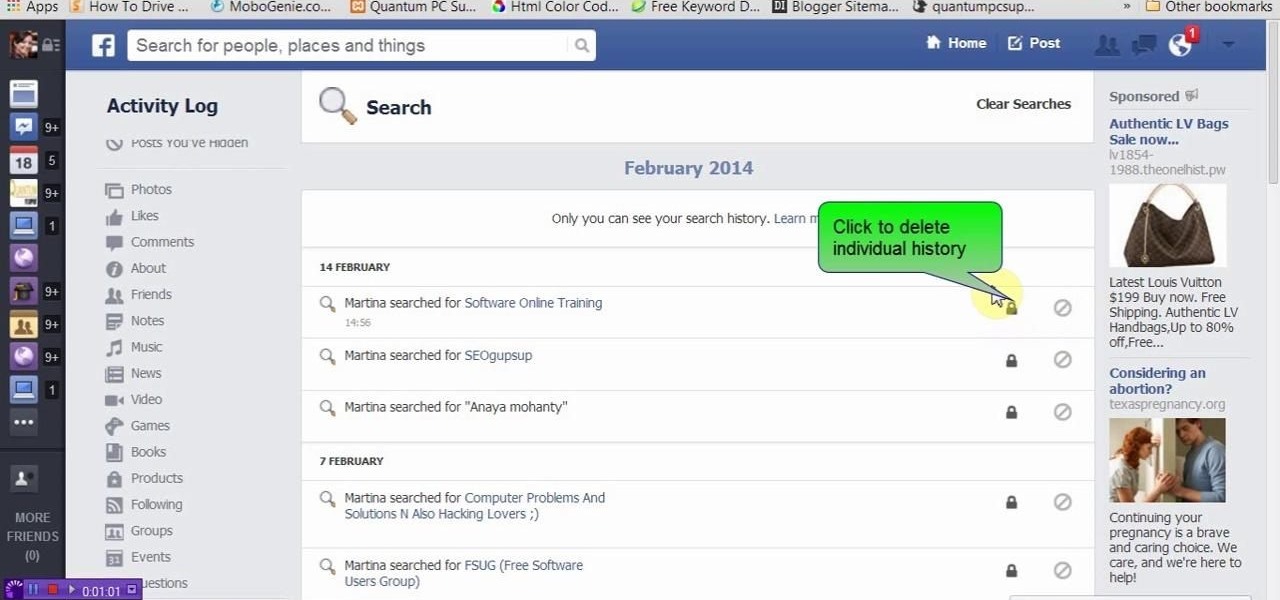
This video will show you how to delete or view Facebook search history. Facebook saves its user search history. User could view and delete this search history. Watch the video and follow all the steps to do it yourself.

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

Currently, all Nexus tablets running Jelly Bean or higher can enjoy multiple user accounts. With tablets often migrating between various people in the same household, there’s no reason for Dad’s finances to mingle with little Tammy’s candy crushing. Multiple users, each with separate profiles, just makes sense on an Android tablet.

This video will show you how to use top 10 tips and tricks for windows7 users. This video includes 10 useful windows 7 tricks for windows 7. Just follow the easy steps to implement yourself.

Video: . Optimize your Marketing with a Mobile Website

TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in the Windows Store for free or purchase.

It's good to password-protect your PC to make sure that your personal files, folders, and important documents are safe and can't be modified without your permission. Though, entering the password all of the time before using your computer might frustrate you.

There is nothing more irritating than having a nice jam session interrupted by an ad selling B vitamins, and that's exactly what Spotify does to you if you don't pay up.

The newest update of the Firefox web browser was released yesterday, and whether you were upgraded automatically or manually, Mozilla is advising that you downgrade to Firefox 15.0.1 as soon as possible. Firefox 16 is Mozilla's latest release, and is apparently extremely susceptible to malicious sites hacking their users complete browsing history.

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...