
SPLOIT: How to Make a Proxy Server in Python
NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!


NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Microsoft dropped a couple of huge bombs at their Windows 10 event Wednesday afternoon. Free operating systems and holographic glasses? This must be a Sci-Fi novel or a Hollywood blockbuster, because it reeks of fiction.
One of the biggest improvements in Mac OS X Yosemite came to the Spotlight search feature, allowing users to not only search through their applications, but also their emails, text messages, iCloud, and the web.
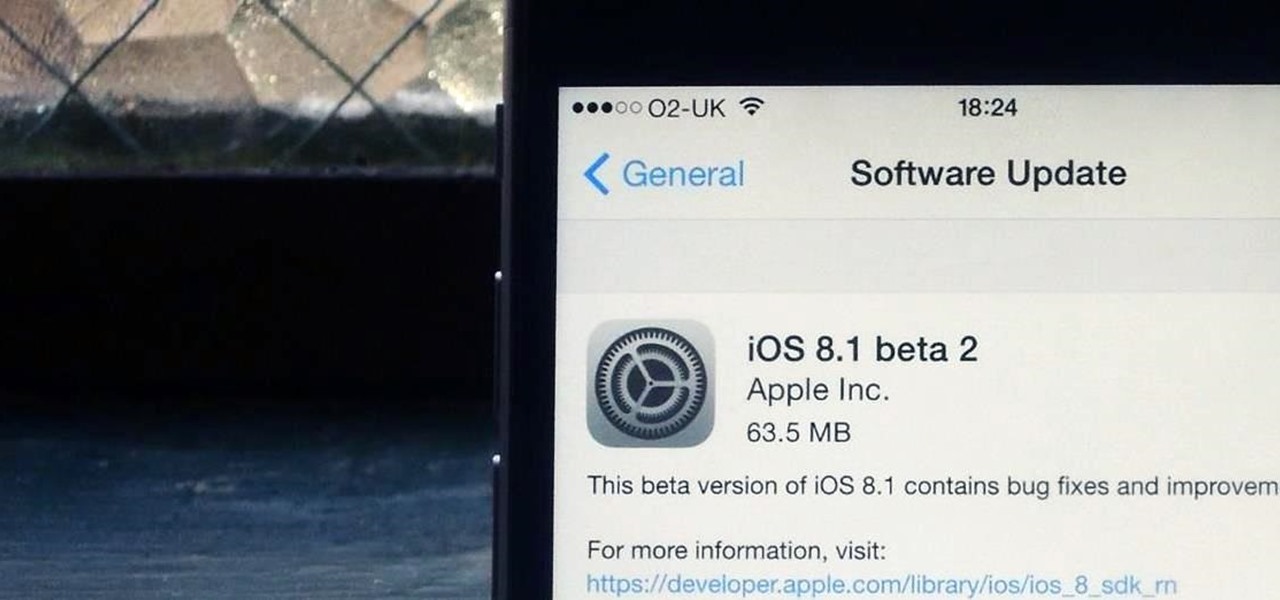
Shortly after Apple's iOS 8.0.1 update fiasco ruined many iPhone users' cellular reception (which was fixed with iOS 8.0.2), developers were treated to the first beta release of iOS 8.1, which will be the next big update for iPad, iPhone, and iPod touch.

It's been a long-rumored feature, but today, VoIP calling has finally started rolling out to users of Google's Hangouts service. Essentially integrating Google Voice into the popular messaging platform, Google has given Android (as well as iOS) users an easy way to make calls without eating up their plan's minutes.

Instagram is not only a great platform to easily share some of your favorite moments with friends and family, it's a useful service for peering outside of your physical location. While you share a picture of your dog in Los Angeles, you can almost instantly view and like a picture someone posted of their breakfast in Tokyo.

The Galaxy S5 is a flagship-level device with some pretty advanced features, like its 4K video recording capability, water-resistant casing, fingerprint sensor, and KitKat running out of the gate.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.
There has been much talk about how unsecure the cloud is because of PRISM’s newfound ability to demand all of your data without any resistance. This has spin doctors in the Cloud Storage industry losing their mind. They suddenly went from a central hub for 10GB of your files, to an easy window for Big Brother to track you through. Centralized cloud storage is no longer a safe way to keep your files, but we still need a way to access our files anywhere we go.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

There's nothing more inherently awesome than looking up into the stars and wondering WTF is really out there. Outer space is one of those rare items that a Google search cannot provide all of the answers for.
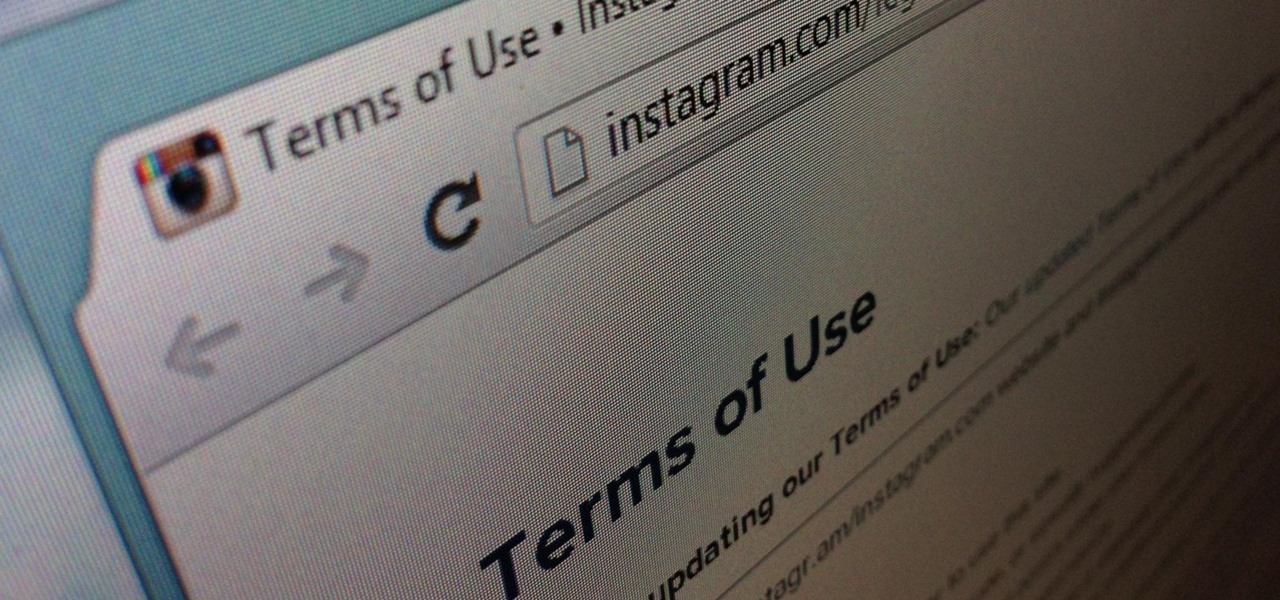
Instagram's controversial terms of service update this past month has spurred an onslaught of dismay and anger from users of the popular photo-sharing social network. The specific set of the new terms that set off this firestorm basically said that businesses could use your uploaded photos for advertisement, without you receiving any of the profit.

After everyone updated their shiny Apple devices to iOS 6 a few months ago, they were shocked to find that their beloved YouTube app was missing. As it turned out, Apple decided to kick YouTube off their list of pre-installed stock apps. The new YouTube app (found in the iTunes App Store) is definitely better than the native one from iOS 5, but it's lacking a direct upload to YouTube option. Sure, you could upload videos from your iPhone's Camera Roll, but the options are limited as to what y...
Feelings can get hurt on Twitter as fast as an update. Everything is fine and dandy because two people are mutually following each other, then out of nowhere, one person has unfollowed the other out for seemingly no reason. Twitter doesn't notify users when someone has unfollowed them, so there are millions of people out there who get used for their follow! Well, now you can find out who unfollows you on Twitter with these mobile apps.
Facebook has always been notoriously difficult to customize. Personally, I think this is an improvement over MySpace's totally open platform (some people should not use code), but users should still have the option to change a few things if they want. While you'll never be able to choose your own background image or add an obnoxious number of aWeSoMe quiz results to your profile, there are a few browser plugins that let you at least change the color scheme.

Most of the spam messages are commercial advertisements, phishing websites and get rich quickly messages that asks users to provide personal details and other confidential information.Spam filters in Gmail prevent its users from these spam messages and restrict them to enter in user’s Gmail inbox.Generally, it acts like a firewall between spam messages and Gmail Inbox.Gmail filters detect the sender’s email address and accordingly send the received messages in Inbox or Spam folder.

Lightning has struck, but not everyone is excited. Apple's new 8-pin Lightning connector for the iPhone 5 has replaced the aging 30-pin connector. Many users have concerns that their current third-party devices will no longer operate properly with the smaller all-digital design, not to mention the expensive price tag for each adapter. What Does This Mean for the User?

Mike Callahan from Butterscotch describes how to manage the passwords on your iPhone by using the 1Password app. The application costs $5.99 for the Pro version. First, you enter an Unlock Code to give you access to the app. The icons across the bottom of the screen correspond to different features of the app. The Logins icon stores your login information. The Wallet icon stores information about your credit and bank cards. The Passwords icon holds all your passwords. The Add icon allows you ...
Not everybody in this digital age has PowerPoint, whether on Windows or a Mac. But at least Mac users can find other ways to share their PowerPoint presentations with other Mac users via iPhoto. PowerPoint 2008 for Mac makes it easy to share your slideshows. The Microsoft Office for Mac team shows you just how to share PowerPoint slides as an iPhoto album in this how-to video.
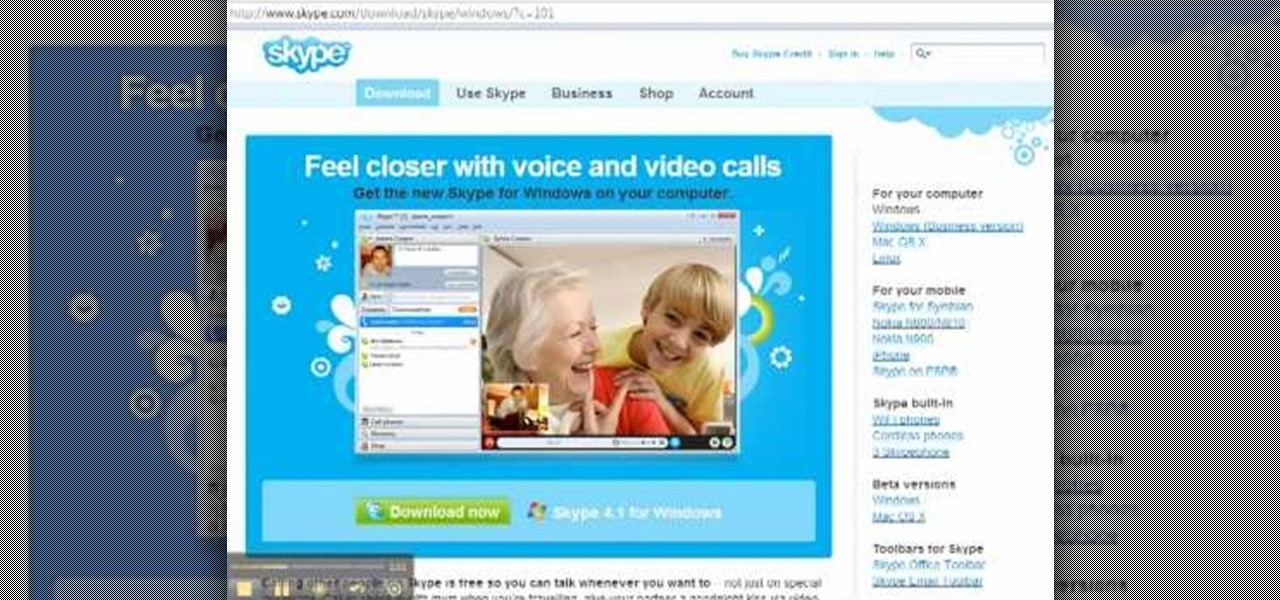
This video will show you how to use the program Skype for online video calls. Skype is a free program that can be used through your computer to make phone and video calls. Go to Skype and download either Mac or windows depending on your platform. It will ask you to fill out some user information, including a user name. Be sure to pick a good user name as you cannot change it later on. Some features include free Skype to Skype calls, instant messaging, free video calls, calling phones and mobi...

Even if you never took home ec, you can create simple projects by learning the basics of sewing machine use.

It was bound to happen with all those numbers floating around in your brain – you've forgotten your Windows password. Here's how to recover it.

Video: . Download: here
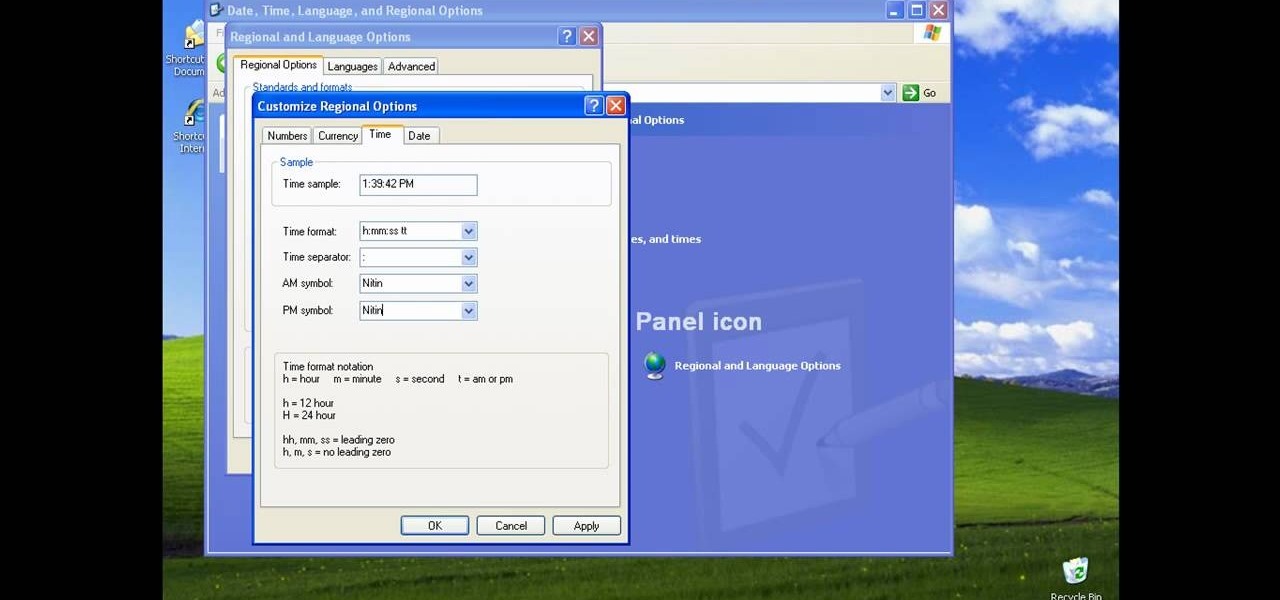
There could be multiple reasons why you would want to input a name in the Windows taskbar on your PC, like when dealing with a network of computers, to help identify workstations, or simply for a customized personal feel. With this tutorial, you'll see how easy it is to put your user name or computer name (or any other name) down in the taskbar, right besides the time in the bottom right.

In this video tutorial, viewers learn how to make funnel cakes. Users will need some cream puff dough. Place the dough into a disposable plastic bag and snip off one of the corners of the bag. This will allow the user to squeeze the dough out. Then heat some oil at medium heat for 3-4 minutes. Now pipe the dough into the boiling oil in a circular motion. The dough should sizzle in the oil. Cook the dough for 2-3 minutes on each side. Finish by draining the dough and add some powdered sugar. T...

In this video tutorial, viewers learn how to completely uninstall a program on a Mac computer. There are 2 ways to uninstall applications. The first way is to drag the application into the trash bin. With this method, users will also have to drag the related, numerous preference and supported files. The second ways is to download an application called App Zapper. With this program, users just need to simply drag the application into the App Zapper program to completely uninstall it. This vide...

In this video tutorial, viewers learn how to get their music heard. To get their music heard, users should create a mix tape of their best songs. They need to have connections with a music producer or have friends that have connections with a music producer. This will allow the friend to introduce you to the music producer. Users also need to put out their records on their own in public places such as clubs or parties to allow any nearby music producers to listen. This video will benefit thos...

In this video from Dr. Carlson, users are shown how to witness the effects of the relationship between temperature and matter firsthand, using light-sticks. For the experiment, users need 3 beakers (or vessels of the sort,) and 3 light-sticks of the same color, shape, and light. To test the range, each beaker must correspond to one of the following states: room temperature, ice-water, or boiling water. Deposit a stick in each of them and observe for two minutes. Thus, one will see how the ato...

In this video tutorial, viewers learn how to improve the control and shooting of iron golf clubs. Most people when they hit a golf ball go short of the green. Users are advised to use one more club (instead of 8, use 7). This will allows users to swing easier, allowing more control. When hitting with an iron, make sure it leaves a divot. It gives a better chance of contact and backspin. Find out where your swing hits the bottom. This video will benefit those viewers who enjoy playing golf and...

In this video from diethealth, viewers are shown how to perform a bridge with an exercise ball. The process begins with the user lying flat on their back, and having their legs positioned on the ball so that their knees are bent. Then, they must lift their hips so that their spine is in a neutral position, and then lowering it back to its previous position. Along with the lifting, they must inhale with the lifting and exhale with the descent, while tightening their gluts and shifting the weig...

The tutorial focuses on using Cheat Engine 5.5 to cheat (or hack) Epic Battle Fantasy 2, an online RPG game. The user will need to choose the "Epic Mode" under difficulty setting. The tutorial maker's mouse also shows where the user is clicking for the menu to come up. This tutorial is directly recorded from the tutorial maker's desktop, rather than using a video camera, therefore, the graphics are clear and just like what you would normally see on your desktop when you're playing. If you fol...
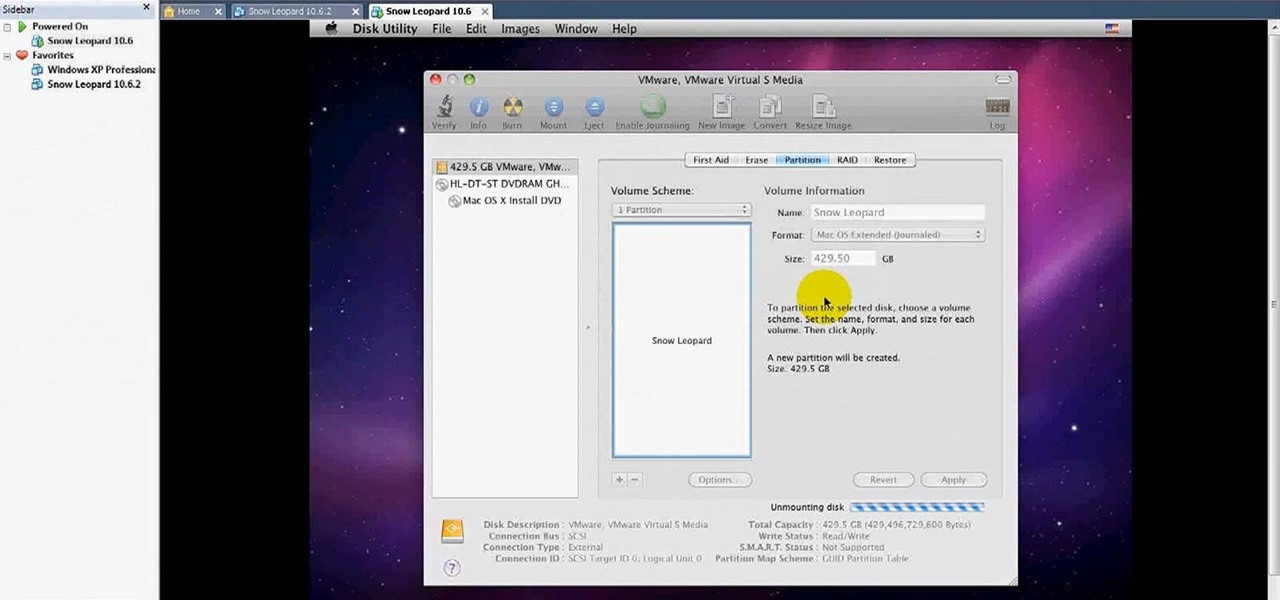
In this video tutorial, viewers learn how to install Mac OS X Snow Leopard in Windows PC using VMware Workstation as virtual machine. Begin by downloading the program from the link provided in the video description. ISO image is made especially for Windows PC users. Mac users can download the DMG file from there too. This video is a complete tutorial for installing Snow Leopard in Windows 7, XP, or Vista.
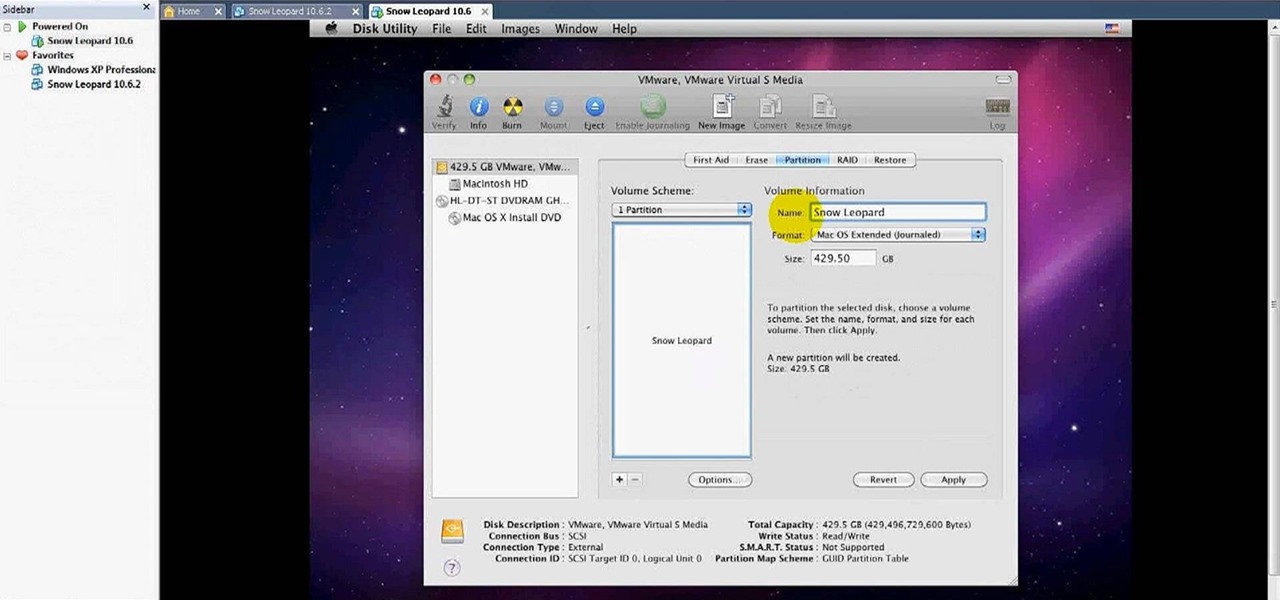
In this video tutorial, viewers learn how to install Mac OS X Snow Leopard in Windows PC using VMware Workstation as virtual machine. Begin by downloading the program from the link provided in the video description. ISO image is made especially for Windows PC users. Mac users can download the DMG file from there too. This is a full video guide on how to install Snow Leopard in Windows 7, XP, Vista using VMware Workstation and download all the software (VMware workstation, Mac OS X Snow Leopar...
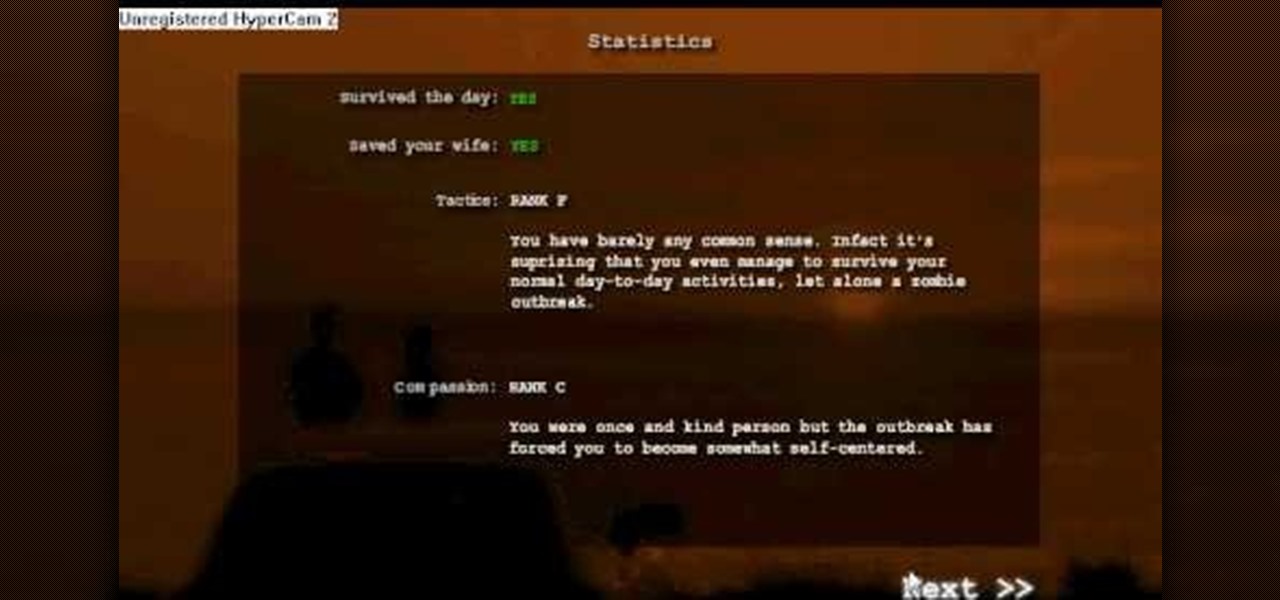
In this video tutorial, viewers learn how to cheat on the flash game Dead Frontier Outbreak. Dead Frontier Outbreak is a new promotional game released on multiple game sites by AdminPwn. It is a text-based zombie adventure game, complete with voice acting. It was created mainly to promote Dead Frontier among gamers who may not have heard of it. To perform this cheat, users simply right-click and select "forward until it reaches the end of the game." Users only need to do this three times. Thi...

Veteran video walkthrough provider Tasselfoot shows users how to beat all 30 levels of the browser based game Factory Balls 3, step-by-step. Gameplay revolves around dropping balls over tools in the correct order, in order to recreate the ball pictured on the box. The game features 30 levels, with later levels more challenging. The game is the third in the "Factory Balls" series, a creation from none other than Bart Bonte, of "The Bonte Room" fame; users who enjoy his brand of eccentric puzzl...
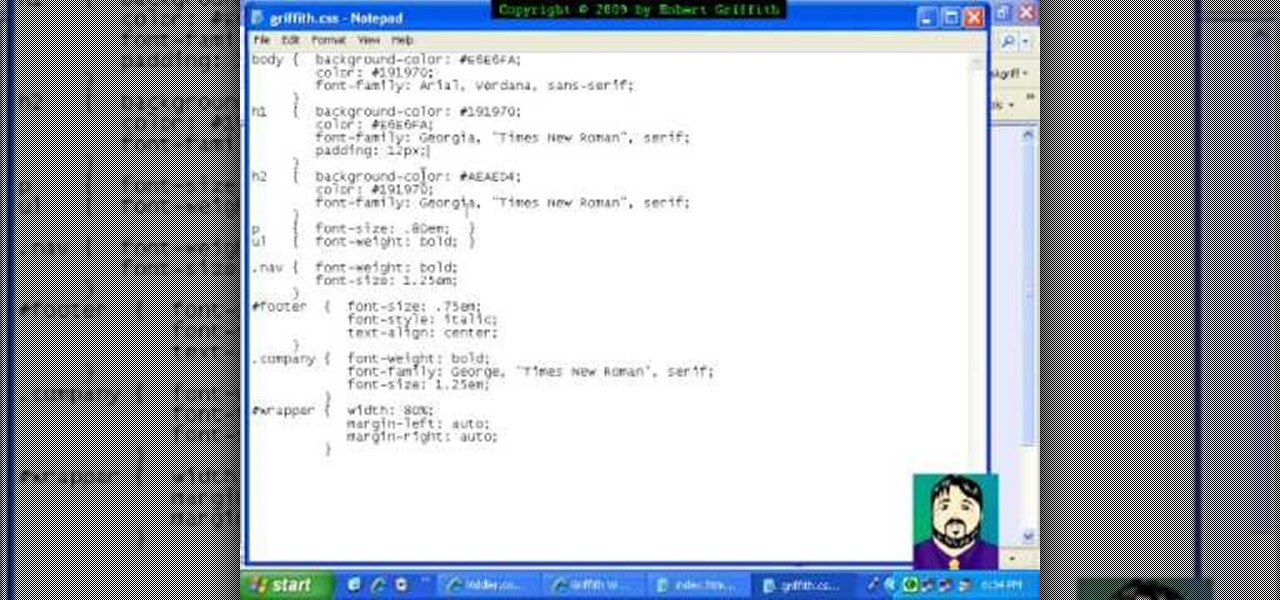
Have you seen extravagant graphics on web pages or in the GUI (Graphical User Interface) of a commercially published program? Do you wish you could create graphics comparable to published works? Now you can! This tutorial will take you step by step in creating visual elements in CSS. Cascading Style sheets are the present and future of web pages and this tutorial will make sure you are not left behind. The visual aspect of web pages are of utmost importance and the major determinant of a user...

On this YouTube video the user Vvistacomphelp shows you how to print screen and crop pictures. The first thing that the user shows is where the Print Screen button is located at on most keyboards so that you can press it on yours. The second thing is go to the start menu in Windows Vista and type in "paint" in the search box on the bottom left then open Paint under Programs. The third thing that is shown is how to make an image appear inside of the paint program so you can crop it. After foll...

This innovative handset makes user convenience its priority. Created with the aim of overcoming the limitations of existing mobile phones, every function is available through a flexible layout of navigation keys. Fixed keypads are a thing of the past with the LG KF600 Venus cell phone.

This tutorial goes over how to edit the text document that controls the hot key (shortcut key) commands. It doesn't go into the advanced commands or even begin to describe the various commands that you can invoke by changing the text document, but most of the users who will be editing this are ADVANCED USERS. NEVER. NEVER change the shortcut settings on a machine that is not yours and ALWAYS. ALWAYS make a backup copy of the document before you start to work on it.