On Friday, the release date for her new album, Queen, Nicki Minaj is already grabbing headlines for the track "Barbie Dreams," where she disses Drake and a host of other rappers.

Now that the cat's out of the bag, Magic Leap has published videos of a pair of apps that will be available to Magic Leap One early adopters.

The latest preview build for Microsoft HoloLens is packed with new sharing features, including support for the Miracast protocol.

Data breaches are all too common now, and the latest one you need to know about involves Timehop, a mobile app that makes it easy to reminisce over old photos. The breach, which took place on July 4, was revealed on Sunday, July 8. At the time, Timehop disclosed that 21 million users had been affected by the breach, but it now appears that all users were impacted in some way.

Usually, the camera adds 10 pounds, but with a new augmented reality effect in Like's mobile app, the camera can actually make you look slimmer.

Augmented reality avatars that mimic facial expressions are no longer the exclusive province of Animojis on the iPhone X or AR Emojis from Samsung. Camera app Snow has added its own alternative to Apple and Samsung's features, which it also calls AR Emoji, for iOS and Android.

When you've had enough of someone's annoying baby videos or cat photos on Instagram, you would have to either unfollow them or even block them outright. Now, you don't have to cut ties with them completely — you can just mute them instead, a feature that Instagram's parent company, Facebook, has allowed on its platform for some time.

As if its users weren't already having enough fun with dancing hot dogs and face effects, Snapchat is upping the ante with a new kind of shared augmented reality content.

Snapchat is making it easier for developers and creators to build augmented reality effects in Lens Studio with a slew of new features, including seven face templates.

As part of its ARCore push this week, Google has promoted Just a Line from one-time AR experiment to a full-fledged app.

Location services provider Mapbox is giving developers a means for building location-based AR apps and multi-user experiences with its new Mapbox AR toolkit.

Multitasking on a smartphone has never been better, but it still has some ways to go to compete with a desktop experience. Samsung hopes to change that with a new multitasking view on the Galaxy S9, which allows the user to open notifications in a new, smaller window on top of the app they are currently using.

From its official launch back in September, iOS 11 has been equal parts revered as it has been criticized. Even with all the great, new features we've come to expect from a major iOS update, plenty of bugs and glitches have forced users to overlook the positives. Perhaps that is why, four months later, 25% of iPhone owners are still running iOS 10.3 or earlier.

As awesome as the 2017 Galaxy lineup may be, few can forget the monstrous disaster that was the Note 7's exploding battery. Needless to say, the last thing Samsung wanted was another news story about a problem with the Note 8's battery. Unfortunately, that's exactly where we find ourselves today.

On Wednesday, Snap, Inc. unveiled a revamp of its Snapchat app that draws a hard line between content from your friends and content from professional media organizations.

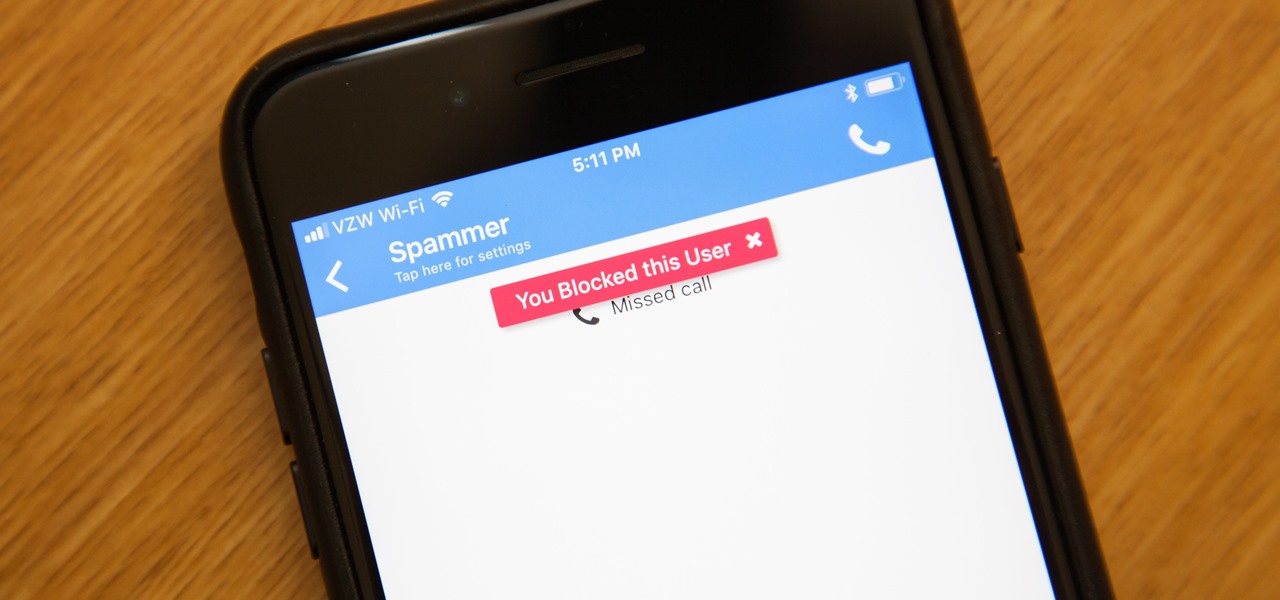
While it's a more secure platform for messages and calls, Signal's job isn't to prevent unknown users from contacting you, so you run into the same issues you would with a regular phone number. People you know that you don't want to talk to may try to strike up a conversation and you'll still get spam messages. Luckily, it's easy to block these suckers.

You know the drill. It's time to d-d-d-duel! This time you're a part of the Shadow Games in a way you've never been before, thanks to Micorsoft's HoloLens.

Developers are really having a field day with Apple's ARKit, announced last month. Since it's release to developers, videos have been appearing all over the Internet of the different ways that developers are getting creative with the ARKit using iPhones and iPads.

Today, Facebook Messenger is rolling out Discover, a feature that helps you chat with companies and locate nearby businesses of interest to you. First discussed in April at Facebook's developer conference F8, Discover is finally available for public use.

If you're like me and you typically find yourself scrolling through Twitter before bed, you will be psyched about this new update for Android.

Yes, you read that headline correctly. Spotify now has 140 million monthly active users, which is up from the 126 million users on the streaming service last year. (If you're wondering, Mexico's population is currently 127 million.)

A new feature of Google's Gboard for Android lets users doodle an emoji in order to find it. The change was part of a few updates introduced earlier today.

To celebrate its tenth anniversary, PornHub has just exposed all of our porn habits. All. Of. Them. Before you panic, no individual information has been released. Instead, PornHub has exposed the adult video trends and preferences of a variety of demographics.

Everyone feels a little safer with Android's security updates, which are welcome and often necessary protective measures. But what happens when the update that's supposed to safeguard your phone actually ends up wreaking havoc with its security system?

Theorem Solutions, a company that helps engineering and manufacturing companies reduce their costs, has taken the next step with their mixed reality technology. The company has now added their own app, called Visualization Experience, to the Windows Store for the Microsoft HoloLens

Google, the company that rules the internet, is now testing a method to leverage its machine learning with its ubiquitous presence on mobile devices. The new model they're employing is called Federated Learning, and it hopes to apply artificial intelligence to Google's services on Android without compromising user privacy.

It appears a privacy lawsuit that began five years ago is about to come to an end, and you might get some money out of it.

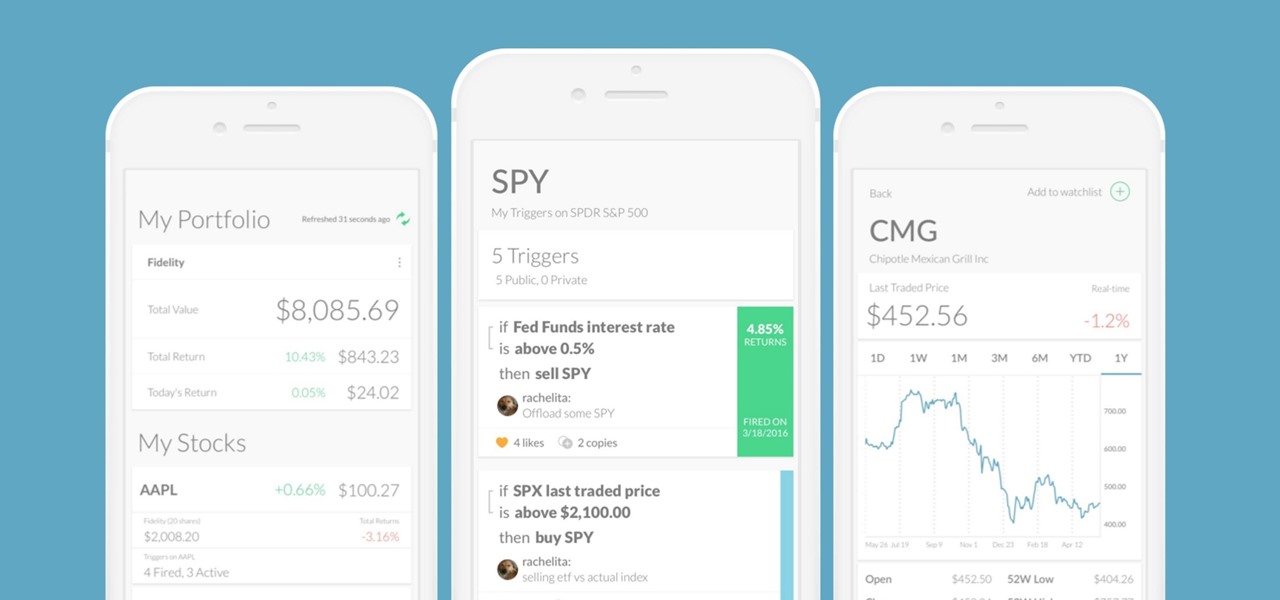
Every time Donald Trump tweets about a stock you own, Trigger Finance, or just Trigger—the app founded on the "if this, then that" rule to track and invest in the stock market—alerts you with a notification for real-time analysis of financial data.

In February, the popular Facebook-owned WhatsApp Messenger service jumped on the "stories" bandwagon and replaced their in-app, text-based "About Me" status (you know, those lovely little messages where you can say "Sleeping" or "Not Sleeping" under the tiny nub of your profile picture). Taking its place was a clone of Snapchat's Stories feature, continuing the social media giant's recent trend of shamelessly copying Snapchat.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Windows has always had an "Administrator" account that allowed you to install programs and manage system files with elevated privileges. The difference between this account and a regular user account with administrator access was that you never got bothered by annoying User Account Control popups when you were logged in as Administrator.

Hello everyone! I'm glad to post my first tutorial and hope you will appreciate it.

As with any software, Android apps can occasionally suffer from bugs. But finding the root cause of such issues can often be difficult, and reporting bugs is a cumbersome experience.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

A recent update to Google Chrome replaced the colored avatar menu in the top-left (Windows) or top-right (Mac) corner of the browser that let you easily switch from profile to profile with a plain gray button that simply names what profile you're in.

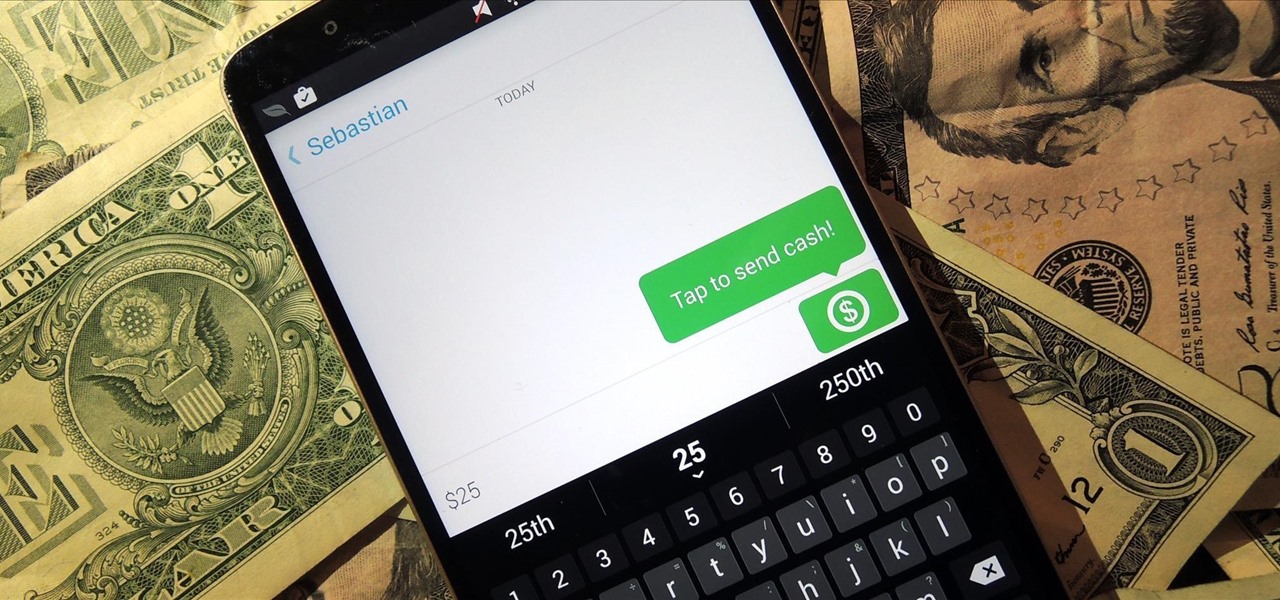
Snapchat is definitely not known for its stellar privacy or security features, but that hasn't stopped them from gaining millions of users. Now, those millions of users can do more than just share pictures and videos—they can share money.

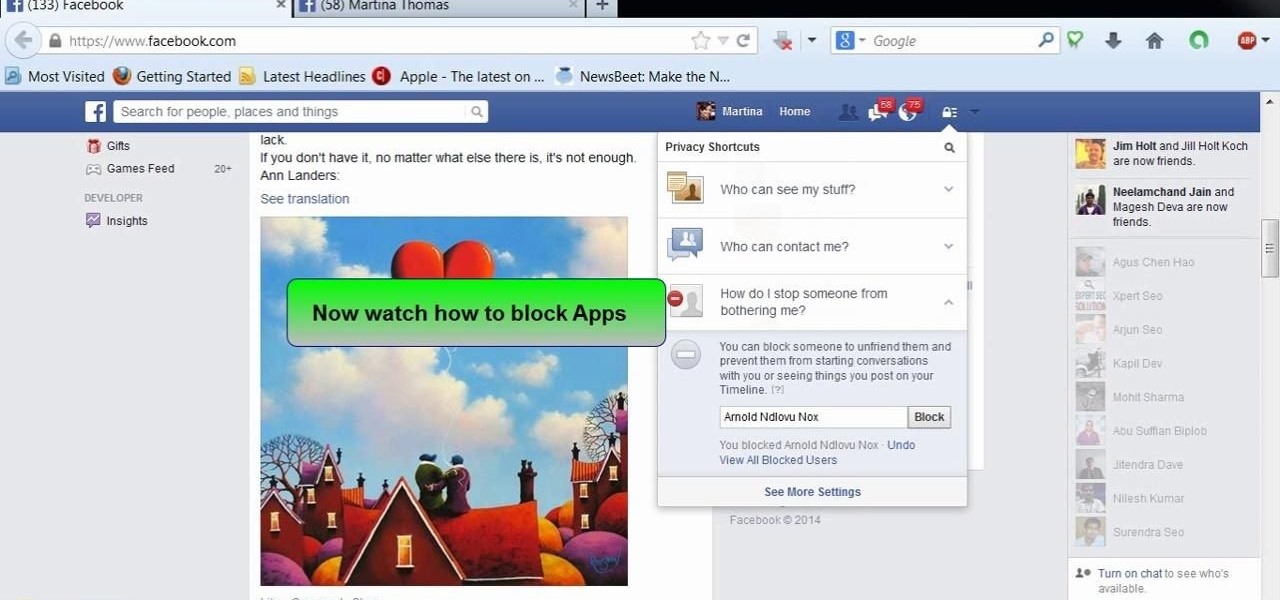
This video will show you how to block users and app invites on Facebook. You can also block apps from sending you notifications. If you accidentally blocked any user or app you intended you could unblock them easily. So please watch the video and employ the technique in your Facebook account.

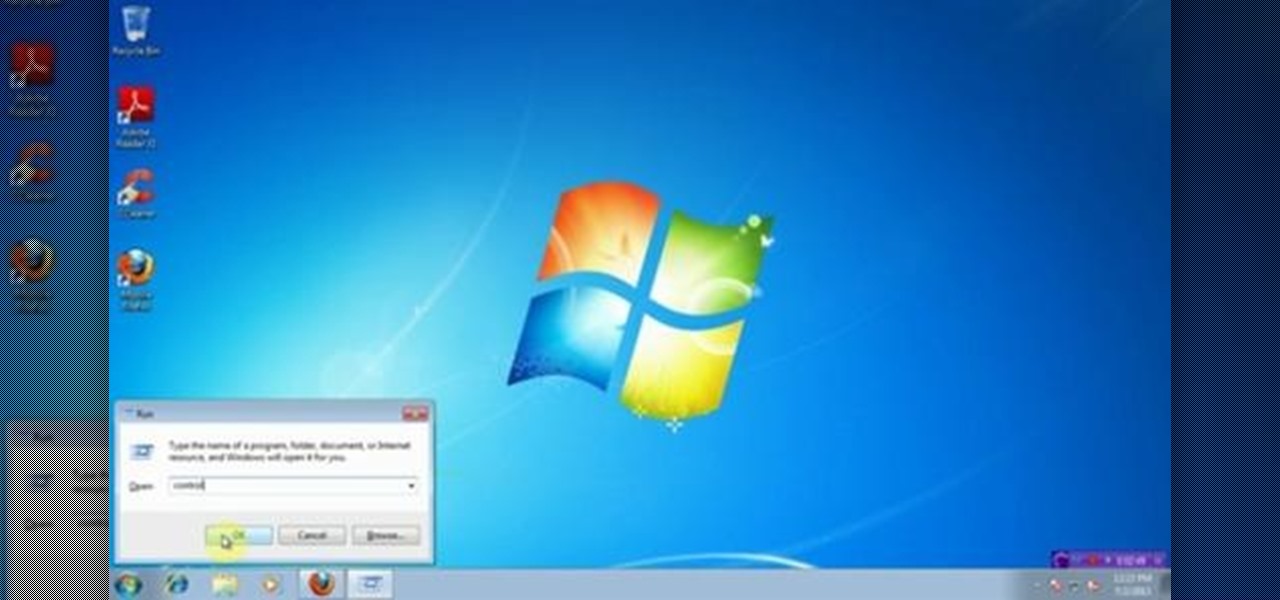
This video will help you how to disable user account in windows 7. This is very easy to employ. Watch the video and follow all the steps to disable user account in your PC.

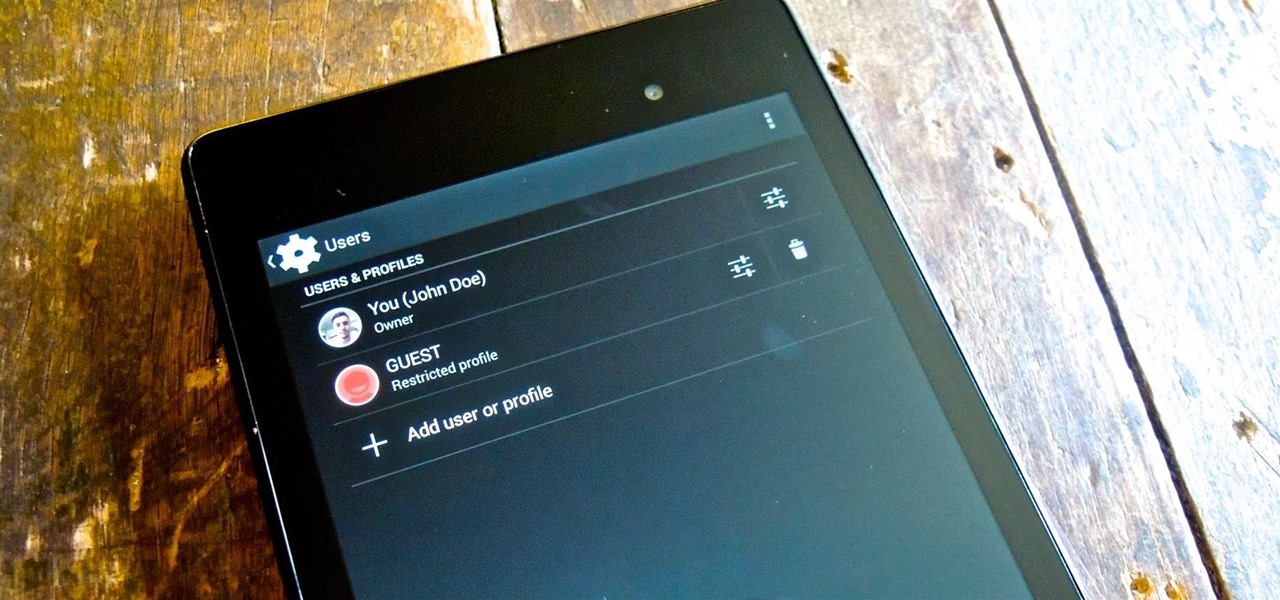
Whenever I hand my tablet over to someone, my heart always races for a second at the thought that they may stumble across my private pictures, texts, and videos. I trust them, and they may not be the snooping type, but it can be easy enough to come across private stuff by accidentally opening a gallery or messaging app.

Just days after news spread that Snapchat could be exploited by spammers, an anonymous group of hackers have released the private information of over 4 million users of the popular photo-sharing application.