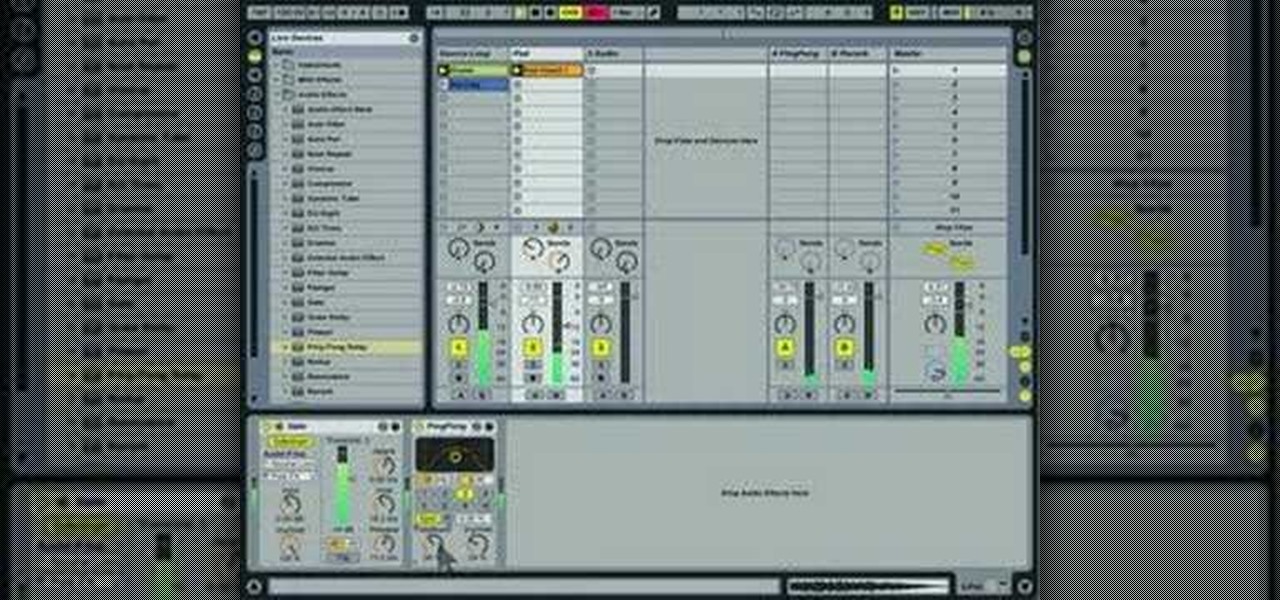
A helpful video for all budding musicians as it clearly explains the Gate sidechain feature in the Ableton Live. The maker of this video simply explains how the feature works and how to use it, clarifying what can sometimes be a daunting program to use. A great tutorial from a very good series produced by Huston Singletary to help newer users. The tunes created through the video are also a great inspiration as it is demonstrated how easy it is to create nice sounding music using these techniq...
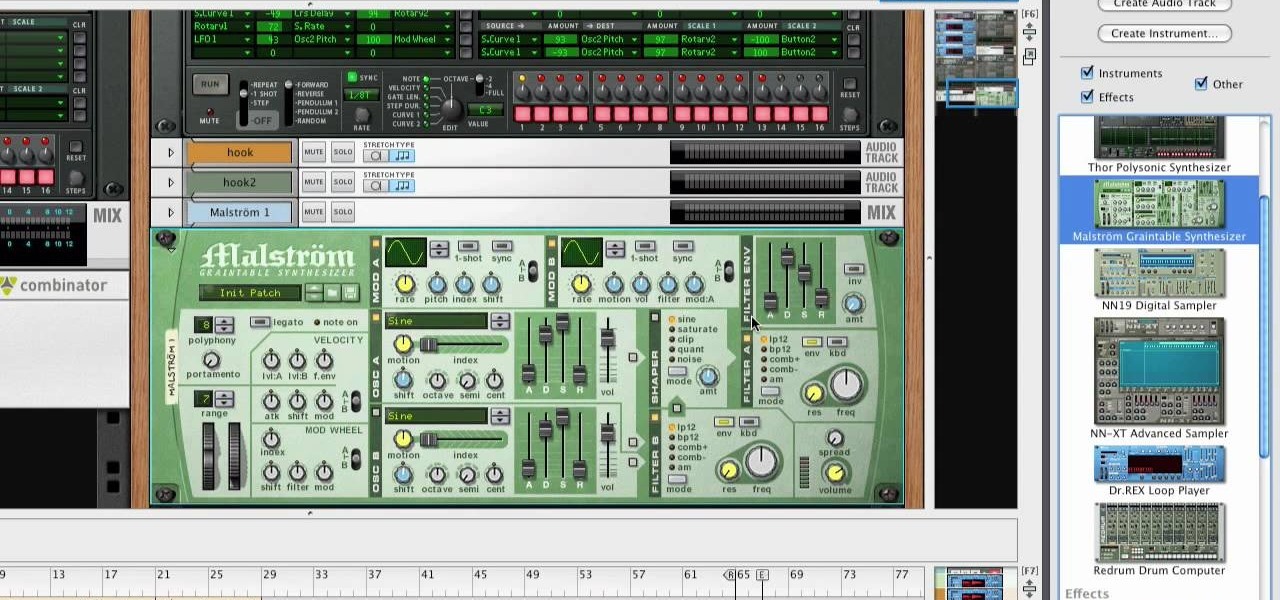
The video describes how Audio Editing Software, Record, and Reason can be used together on the same computer. Once all the three are installed on the same computer, they can be merged to form one large audio editing program on the same account. After installation of both of these, ensure that the program Record recognizes the installation of program Reason. By merging these two audio editing programs, the users will be able to access the features of both programs as if it is one large editing...
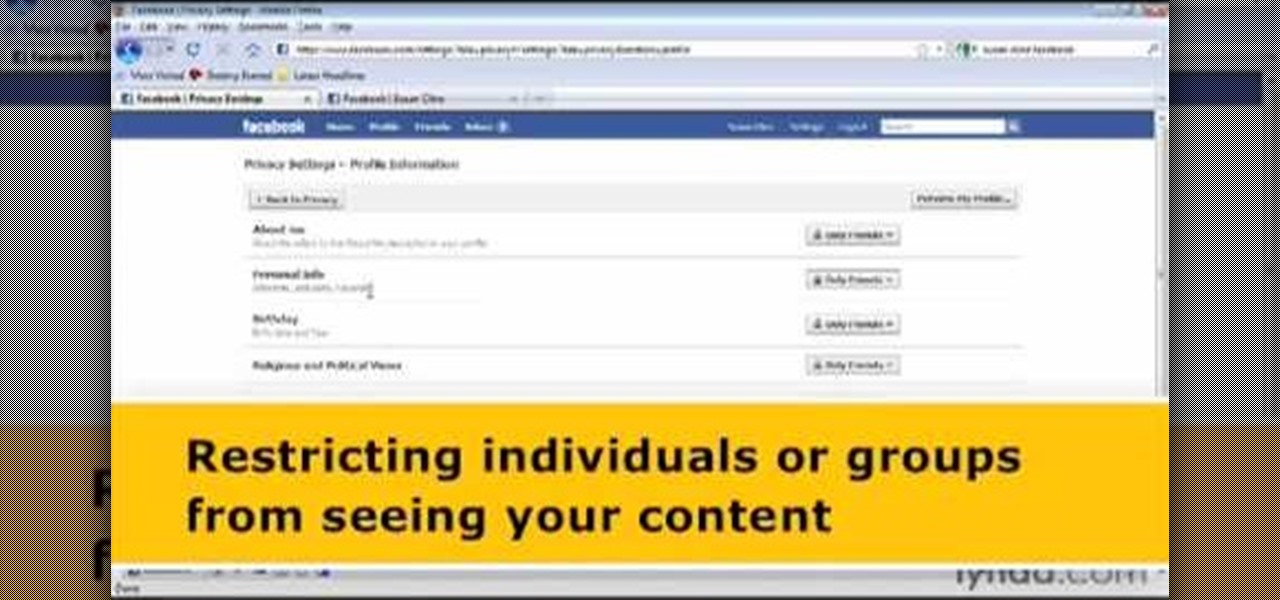
Facebook is one of the most popular social networking sites out there, so make sure you are being safe! Susan Kline shows you in her Facebook Essential Training series how to Restrict certain aspects of your profile. Login to Facebook and view your Privacy Settings. From there you can pick your About Me, Personal information, Wall Post, Photos and more and restrict showing it to people. You can pick everyone, certain friend lists, Networks, and even individualize it down to one person.

Elementtatootech explains the various tools of the industry and their uses to novice tattoo artists and interested viewers. In this tutorial, Elementtatootech focuses on the old school tattoo tool known as grommets or nipples. Utilizing a single close up shot, the instructor quickly educates viewers on the purpose of the grommet in addition to the most common users of the device. The instructor additionally shows viewers how to set up and assemble using this tool and a simple trick utilizing ...
Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.
Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

Learn all there is to learn about yarn from Naztazia... watch this video tutorial to learn how to crochet spiral scrubbies with a pattern.

Click the more info tab to see the instruction on how to get a bear on Mybrute.com. This is a tutorial on how to get a Bear on Mybrute.com, An Online RPG Game, It's a very popular game that a lot of people plays everyday, You don't need to do much action with your hands just sit back and enjoy the show. Getting a bear is hard, because it's a extremely hard pet to get on mybrute.com, some sample pets are Dog,Wolf/Panther,Bear. If you can't read what I typed or did on to get a bear here's a lis...

"Shamanism: Other Worlds" explores the ancient spiritual Amazonian enlightenment drug Ayahuasca. This documentary investigates Ayahuasca and its use largely as a religious sacrament. Those whose usage of ayahuasca is performed in non-traditional contexts often align themselves with the philosophies and cosmologies associated with ayahuasca shamanism, as practiced among indigenous peoples like the Urarina of Peruvian Amazonia. The religion Santo Daime uses it. While non-native users know of th...

Most people don't use their cameras to make movies (really bad quality and a sort of user-generated content feel are probably the culprits) but cameras with a record function are great for those impromptu memory-making moments when your dog tries to do a handstand or your grandma unloads the biggest belch ever.

Get moving! Learn how to walk, run and jump your way through LittleBigPlanet. LittleBigPlanet exclusively for the PLAYSTATION 3. It lets you PLAY alone, or with friends, in a world of infinite possibilities. Run, jump, grab and swing your way thru imaginative levels and mini-games. If you're feeling creative, you can CREATE your own levels, enemies, obstacles and even storyline. Once done, SHARE them with our online community of thousands of User Generated Levels from around the world for

Stick it to them! Learn how to resize, rotate, and stamp your sticker collection in LittleBigPlanet.

Get some clothes on! Dress up or Dress down, learn how to express your own SackFashion for Little Big Planet on PS3.

Hacker Defender is one of the most widely deployed rootkits in the world. It is a user-mode rootkit that modifies several Windows and Native API functions, which allows it to hide information (files, processes, etc.) from other applications. In addition, Hacker Defender implements a backdoor and port redirector that operates through TCP ports opened by existing services. This means it is not possible to find the hidden backdoor through traditional means, like launching a remote port scan agai...

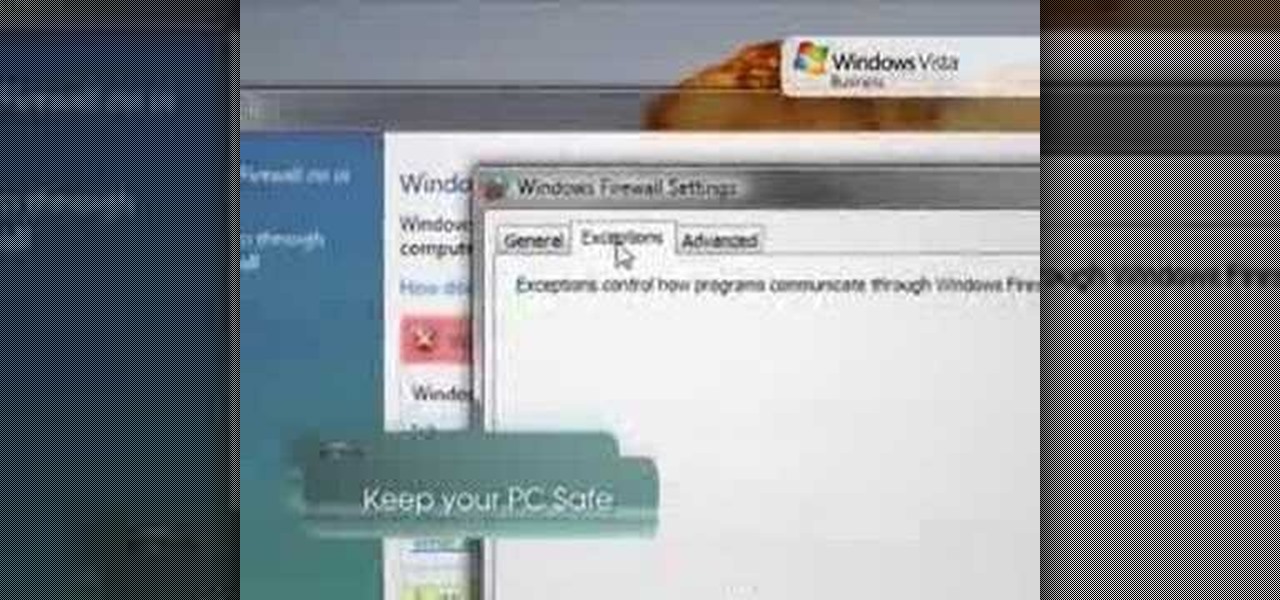
In order to keep your PC safe from annoying or potentially dangerous threats on the Internet, a properly-configured firewall is a crucial item in helping prevent your system from becoming compromised. The Windows Firewall in Windows Vista™ is the first line of defense in helping to keep your computer safe. By preventing your computer from being infected by malware, Windows Firewall is designed to be easy to use and is automatically enabled to protect your computer as soon as Windows starts. T...

Because of its portability, the acoustic guitar can be wonderful songwriting device. However, having a pocket symphony in your head–or pocket, as it were–does you little good if your hands aren't on board. Fortunately, YouTube user Sawlon is here to help you train your head and hands with his series of free video guitar lessons. In this installment, you'll learn how to a number of strum patterns devised for songs with three chords per measure. Remember, the more you practice and the more theo...

Boris Title Toolkit gives Adobe After Effects users advanced titling capabilities for maximum quality, speed, and creativity. Using Title Toolkit, graphic artists can import ASCII or RTF files for fast, easy credit rolls, take advantage of rich text style options such as bevel borders, gradient fills, simulated extrusion, and embossing, and save or apply custom or preset text styles, gradients, and colors, all of which can be applied on a per character basis.

If you’ve recently updated your Apple iPhone to firmware 2.1 and lost your jailbroken status, you’ve most likely heard that the Dev Team has released QuickPwn 2.1 for Windows users! Some of you have already jailbroken your iPhone 3G on 2.1 firmware when QuickPwn and Pwnage Tool for Mac was released.

Because of its portability, the acoustic guitar can be wonderful songwriting device. However, having a pocket symphony in your head–or pocket, as it were–does you little good if your hands aren't on board. Fortunately, YouTube user Sawlon is here to help you train your head and hands with his series of free video guitar lessons. In this installment, you'll learn how to incorporate slap rhythm on acoustic guitar. Remember, the more you practice and the more theory you know, the better you'll s...

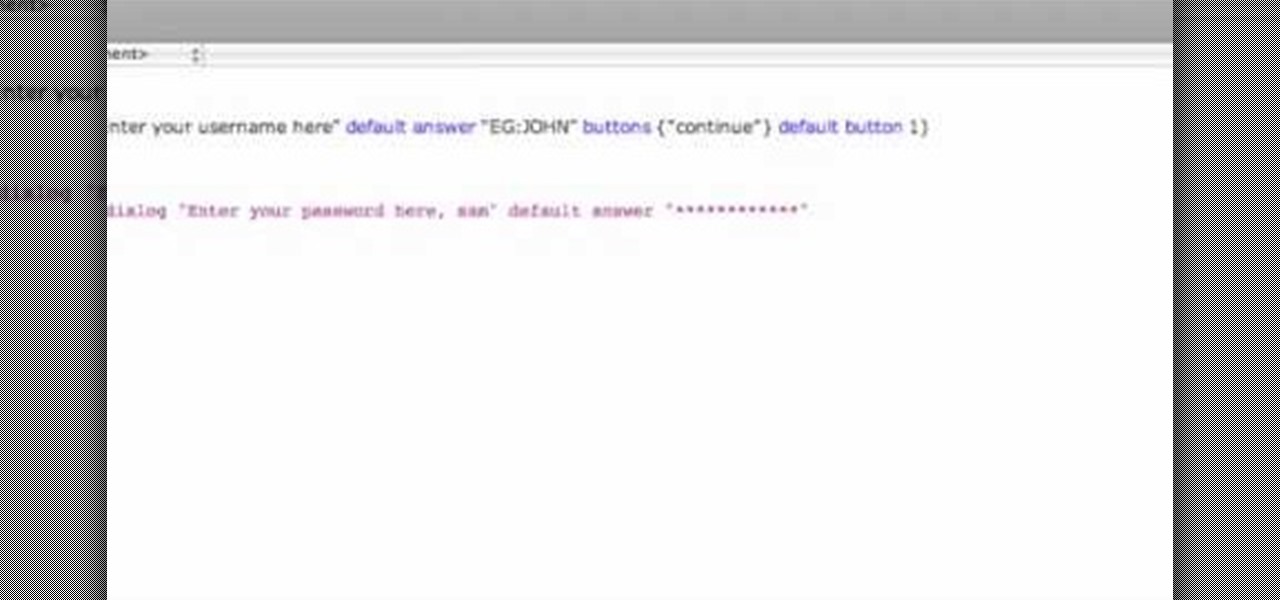
This video shows how to program a password and user protected application in AppleScript.

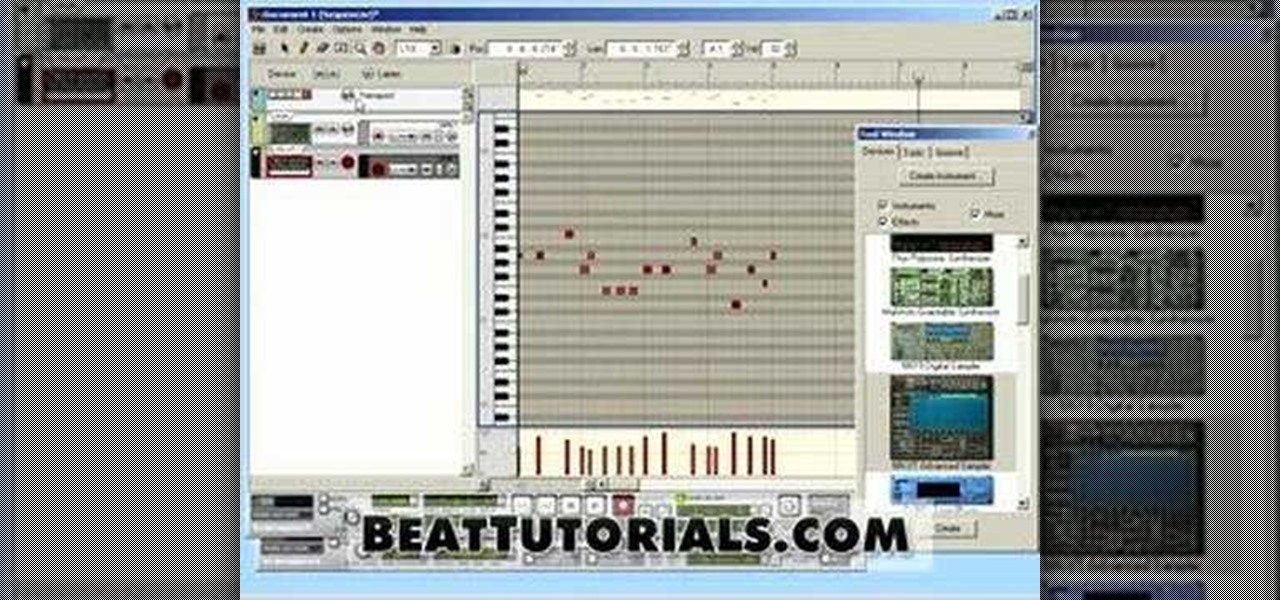
Here's a free tutorial from Beat Tutorials showing you how to create a hip hop style beat in Reason. This is a great tutorial for anyone who has never touched a keyboard to advance users who want a few tips.

Apple's exclusive chat services, iMessage and FaceTime, force many of us to stay locked into iOS, iPadOS, and macOS to communicate with other Apple users, so chatting with Android-using friends means SMS texts, third-party messaging apps, and third-party video chat services. However, Apple is breaking boundaries with iOS 15 so that we can FaceTime with Android, Linux, and Windows users.

There's an easy way to take your PC to the next level — without any need for a hardware upgrade. The secret is in software that unlocks uses and productivity hacks you never knew you needed. Even better, right now, The Power User PC Software Bundle is on sale for just $59.99. That's 90% off the regular price of $614.

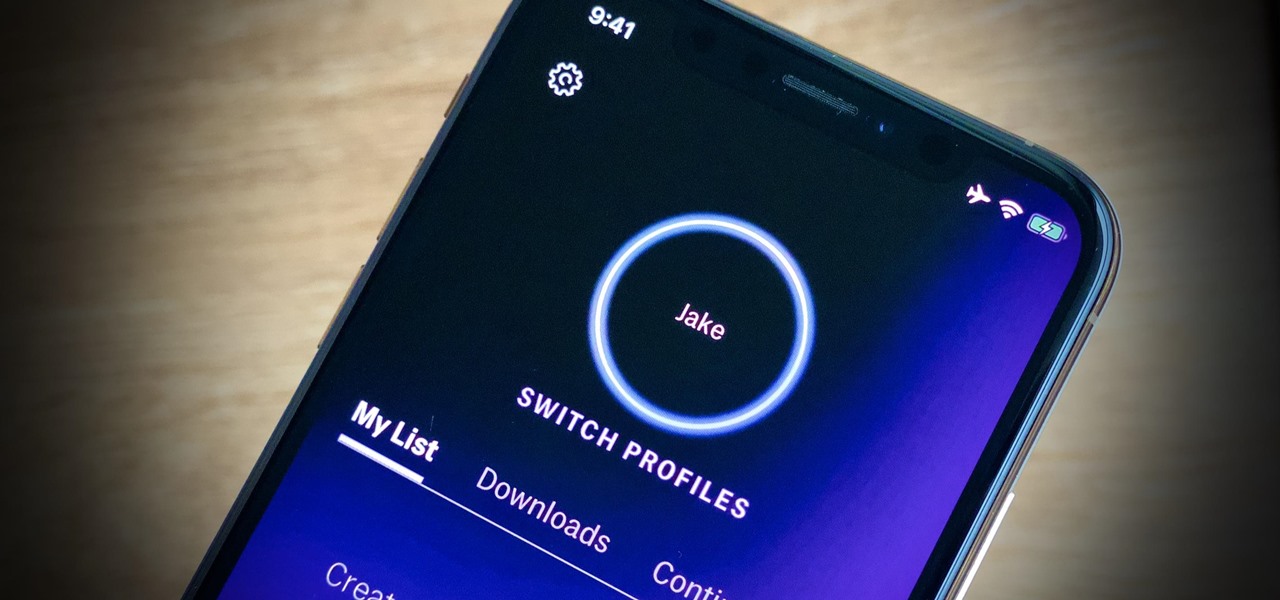
Many streaming services offer user profiles for different people in your household, some of which also include profile images. In most cases, you can set a custom profile image to better differentiate and personalize your account from the others, and HBO Max lets you do the same, albeit, with limited options.

Few things are more important than search engine optimization when it comes to increasing a brand's visibility online. Regardless of whether you're launching a new business from scratch or working as a marketing professional at a major corporation, you need to ensure that you're drawing the most people to your website and affiliate links by utilizing the latest and most powerful SEO tools and methods.

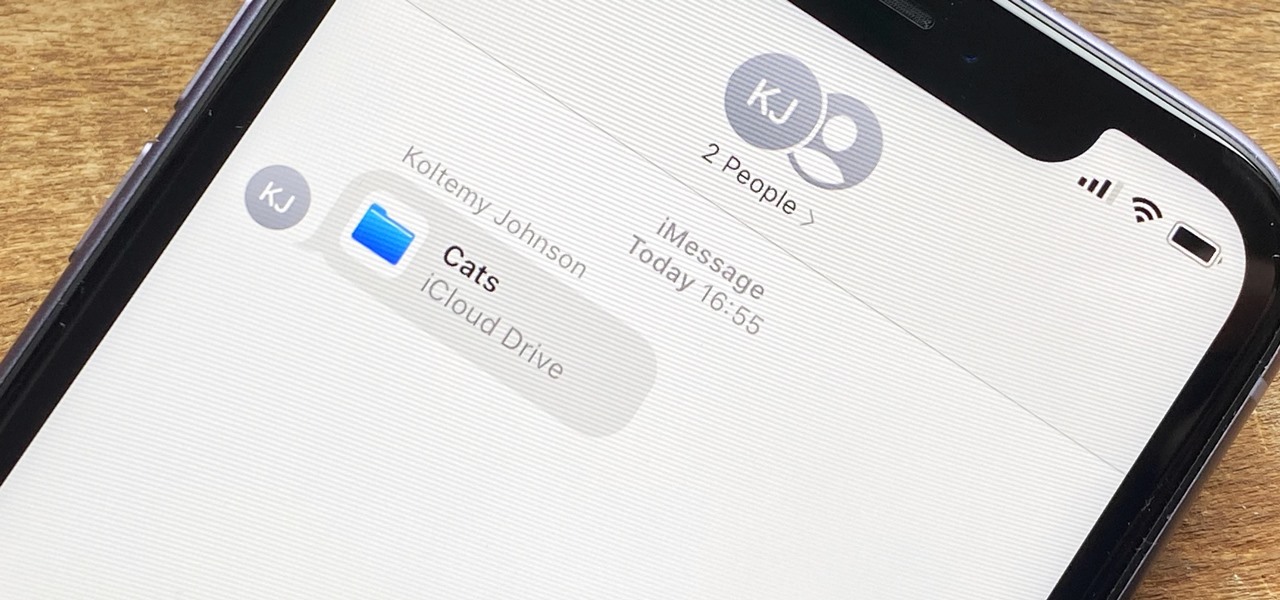
In the iOS 13.4 update, Apple added folder-sharing capabilities in the Files app. That means you can share multiple documents at the same time instead of doing it one by one. But that's not all — you can share folders with numerous contacts and even enforce access and permission settings.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

Just as predicted (but perhaps with less fanfare than usual), Apple has made the move of adding a depth sensor to the rear camera of its latest edition of the iPad Pro.

Apple's first AR wearable might not arrive until 2022, but we may have an early preview of what it will be like to wear a pair of its smartglasses via iOS 14.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

As fun as Twitter is, it can also quickly turn scary. Anonymous, aggressive, and troll accounts can attack you for your tweets and stalk your every move. While you could make your profile private and block users, there are lesser-known privacy and security features that you can switch to improve your safety online.

When watching stories in your Instagram feed, there's a high probability that you'll come across an AR filter that you'll want to try out for yourself. A quick browse and search in the Effect Gallery will bring up nothing in most cases. But all of that unproductive work isn't necessary because there's a faster and simpler way to get the AR effect in Instagram Stories, and it works all of the time.

When you think about your Apple Watch, what comes to mind? Fitness tracking? Replying to texts? There are a lot of things Apple Watch is good for, but social media doesn't appear to be one of them based on the App Store. If that's your perception, however, it's time for a reality check because you can start browsing Twitter and Reddit on your Apple Watch right now.

The cosmetics brands are among the earliest adopters of augmented reality, using virtual try-on tools to preview shades of makeup before buying.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

Apple's ARKit has built a considerable lead in terms of features over Google's ARCore, but Google's latest update to ARCore adds a capability that makes the platform a bit more competitive with ARKit.

After drawing attention from nostalgic Gen Xers for its Motorola Razr reboot with a foldable screen, Lenovo has a new augmented reality smartglasses concept that the company hopes will also turn some heads.

After leaning on augmented reality for its outdoor advertising, HBO has called on augmented reality again via Snapchat to promote its Watchmen series.

The Halloween season is the perfect time for telling scary stories, but augmented reality is here to bring the tradition of frightening children to the modern age.

Android 10 lets you personalize your device by adding a profile picture to your lock screen. Not only will it add your picture or avatar to your lock screen, but it will also add it to the Quick Settings menu. It's a nice touch of customization that makes your device feel like your own.