4DViews, the volumetric capture company that films actors and performers in augmented and virtual reality for things like movies, TV series, and applications, has just released the app 4DViews: Raise Virtual to Reality, to demonstrate its technology for smartphones.

Don't ignore the update sitting in your Settings app; you'd be leaving your iPhone's security vulnerable.

All you paying Spotify users are about to get another exclusive privilege besides getting out of all those annoying "Ever wonder what it would be like to have Spotify premium?" ads. The Sweden-based company is looking to lower the royalty fees they have to pay to major record labels for their music, by compromising on their policy that all their music be free to paying and nonpaying users. Spotify would for a limited time restrict access on major album releases to their paying subscribers.

There are already a few ways to use your home computer on the go, but none of them feel very natural when you're out and about, and are clunky options at best. Samsung wants to change that with Monitorless, their upcoming augmented reality smartglasses, which offer remote desktop viewing capabilities as well as the ability to switch between augmented and virtual reality modes using electrochromic glass.

In recent weeks, thousands of Nexus 6P users have reported that their devices are shutting down with 30% or more battery life remaining. The phones won't start back up until they're plugged into a charger, so it's as if the battery completely dies even though there is plenty of juice left.

It seems like a new, dangerous Android exploit is uncovered every month or two. The latest headliners are NightMonkey and Chronos from the list of CIA hacks reported by Wikileaks, which have been billed as gaping security holes in the world's biggest mobile operating system.

We can't be in two places at once, but with virtual touch interfaces we can theoretically use a machine to act as our second body in a remote location. Over at MIT, Daniel Leithinger and Sean Follmer, with the advisement of Hiroshi Ishii, created an interface that makes this possible.

HoloLens users will have a handful of ways to interact with the mixed-reality, holographic world. Gaze Input lets the user control a cursor in their field of vision. In other words, it's essentially a mouse that you control by looking around.

Welcome hackers. Hackacademic.RTB1 is vulnerable machine for training our skills.This machine can be download from free from here. There is many tutorial how to hack these machine but i did always be my self.

Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

I'm sure that many of us have heard of that nasty Shellshock vulnerability, but not very many people know how to exploit it. Try these few tricks on vulnerable websites!

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

Microsoft dropped a couple of huge bombs at their Windows 10 event Wednesday afternoon. Free operating systems and holographic glasses? This must be a Sci-Fi novel or a Hollywood blockbuster, because it reeks of fiction.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

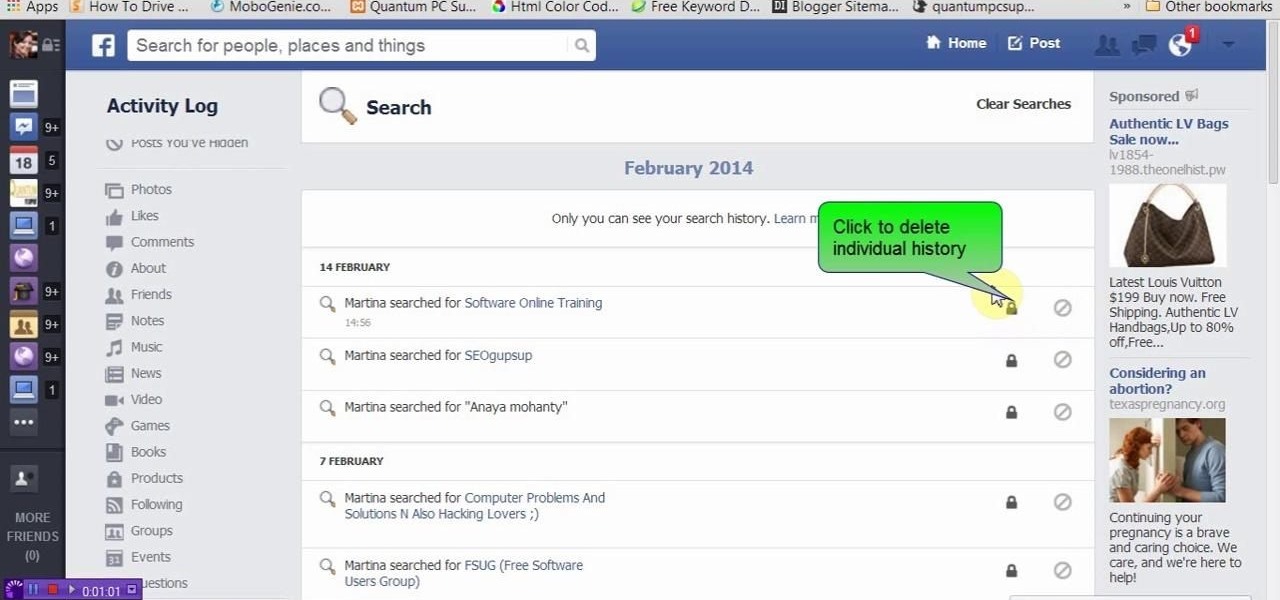
This video will show you how to delete or view Facebook search history. Facebook saves its user search history. User could view and delete this search history. Watch the video and follow all the steps to do it yourself.

Instagram is not only a great platform to easily share some of your favorite moments with friends and family, it's a useful service for peering outside of your physical location. While you share a picture of your dog in Los Angeles, you can almost instantly view and like a picture someone posted of their breakfast in Tokyo.

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

Currently, all Nexus tablets running Jelly Bean or higher can enjoy multiple user accounts. With tablets often migrating between various people in the same household, there’s no reason for Dad’s finances to mingle with little Tammy’s candy crushing. Multiple users, each with separate profiles, just makes sense on an Android tablet.

This video will show you how to use top 10 tips and tricks for windows7 users. This video includes 10 useful windows 7 tricks for windows 7. Just follow the easy steps to implement yourself.

Video: . Optimize your Marketing with a Mobile Website

TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in the Windows Store for free or purchase.

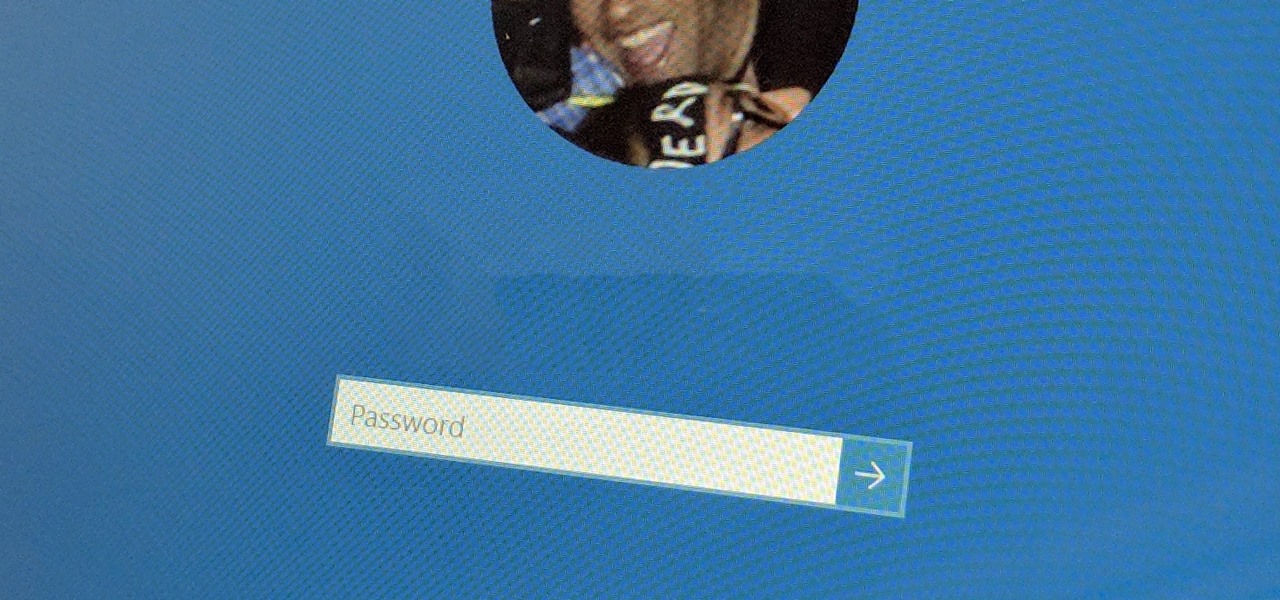
It's good to password-protect your PC to make sure that your personal files, folders, and important documents are safe and can't be modified without your permission. Though, entering the password all of the time before using your computer might frustrate you.

There is nothing more irritating than having a nice jam session interrupted by an ad selling B vitamins, and that's exactly what Spotify does to you if you don't pay up.

The newest update of the Firefox web browser was released yesterday, and whether you were upgraded automatically or manually, Mozilla is advising that you downgrade to Firefox 15.0.1 as soon as possible. Firefox 16 is Mozilla's latest release, and is apparently extremely susceptible to malicious sites hacking their users complete browsing history.

Lightning has struck, but not everyone is excited. Apple's new 8-pin Lightning connector for the iPhone 5 has replaced the aging 30-pin connector. Many users have concerns that their current third-party devices will no longer operate properly with the smaller all-digital design, not to mention the expensive price tag for each adapter. What Does This Mean for the User?

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...

This is OSCAR, the Overly Simplified Collaboratively Actuated Robot. He's built from an old Roomba and an Android tablet, and he's about to make Google+ a lot more interesting. The robot is controllable by users in a Google+ Hangout, allowing the audience to interactively explore OSCAR's environment via his on-board camera.

Hello, today I will tell you about how you can create a page through wordpress. this is a performance for those who have scarcely been touched wordpress. This guide will put you through basis and create a user and a website among millions of people.

In this video tutorial, viewers learn how to use the noise removal tool in Camtasia Studio. Begin by uploading the audio track into the time line. Then select and highlight the region that contains the noise. Now click on Edit and select Audio Enhancements. Under Background noise removal, users are able to select to automatically or manually remove the noise. Once selected, simply click on the Remove Noise button. Users also have the option to adjust the sensitivity. This video will benefit t...

In this video tutorial, viewers learn how to use volume envelopes in Sony Vegas Movie Studio. Begin by importing the audio track into the time line. Then right-click on the audio control panel, go to Insert/Remove Envelope and select Volume. This will place a purple line through the audio track. Users are able to control the volume by moving the line up or down to increase or decrease the volume. Users are also able to select certain points by creating starting and ending points in the audio ...

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...

In this video tutorial, viewers learn how to do a 21's workout for biceps. Users will need to use a barbell for this exercise. Users will be doing 21 repetitions of barbell curls. The first 7 reps is just the bottom part of the movement. Then the second 7 reps are the top part of the movement. The last 7 reps are the full movement of a bicep burl. This video also provides a demonstration for viewers to easily follow along. This video will benefit those viewers who are interested in health and...

In this video tutorial, viewers learn how to use the Nokia N97 phone. The power button is located on the top of the phone to turn on/off the device. The menu key will open a list of applications for use. The call key will allow the users to make a phone call. The end key will bring the user to a previous screen or end a call. There is a headphone jack at the top of the device. One the side there is a Micro connector, and lock key. This video will benefit those viewers who are just using the N...

In this C4D user's guide, learn how to ctrl-drag axes to bypass the object axis tool; how to change a group axis with several selected items; how to set a light to negative values to make darker areas; and how to undo camera (view) moves by choosing "shift-command-Z." Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more i...

In this video tutorial, viewers learn how to align and group objects, and use gridlines. Begin by clicking the Insert tab and select a shape from Shapes. To align the object, go to the Format tab and select the Align menu. From there, users are able to align the selected object in any direction. In the Align menu, users are also able to add gridlines by selecting View Gridlines. To configure the grid-line options, click on gridlines Settings. This video will benefit those viewers who use Micr...

In this video tutorial, viewers learn how to do the "Out of Beverly Hills" glitch on the video game, Tony Hawk's American Wasteland. Users will need to have the low gravity option turned on. There are several ways to do this glitch. Begin by going on top of a roof with a ramp. Then launch off the ramp and then jump off that roof to end up out of the map. Users are also able to super jump and ride an invisible board in this glitch. This video will benefit those viewers who enjoy playing this v...

In this video tutorial, viewers learn how to create tables in Microsoft Word 2007. Begin by clicking on the Insert tab and select Table. Then users are able to create a table by dragging the mouse across the squares to determine he amount of columns and rows. Make the final selection by simply clicking. Another option is to click on Tables and select Insert Table. Then users are able to input the number of columns or rows. This video will benefit those viewers who use Microsoft Office 2007, a...