It's nice to have the family together for Thanksgiving dinner, but having so many people together can make it tricky to figure out what you can do after dinner. Here are a few good ideas you can use for family friendly activities.

Like a scene from Charlie and the Chocolate Factory, this high-tech cookie offers 7 different flavors. The University of Tokyo's Tajuki Narumi and team presented the Wonka inspired augmented reality flavor-changing cookie at this year's SIGGRAPH computer graphics and animation conference in Los Angeles.
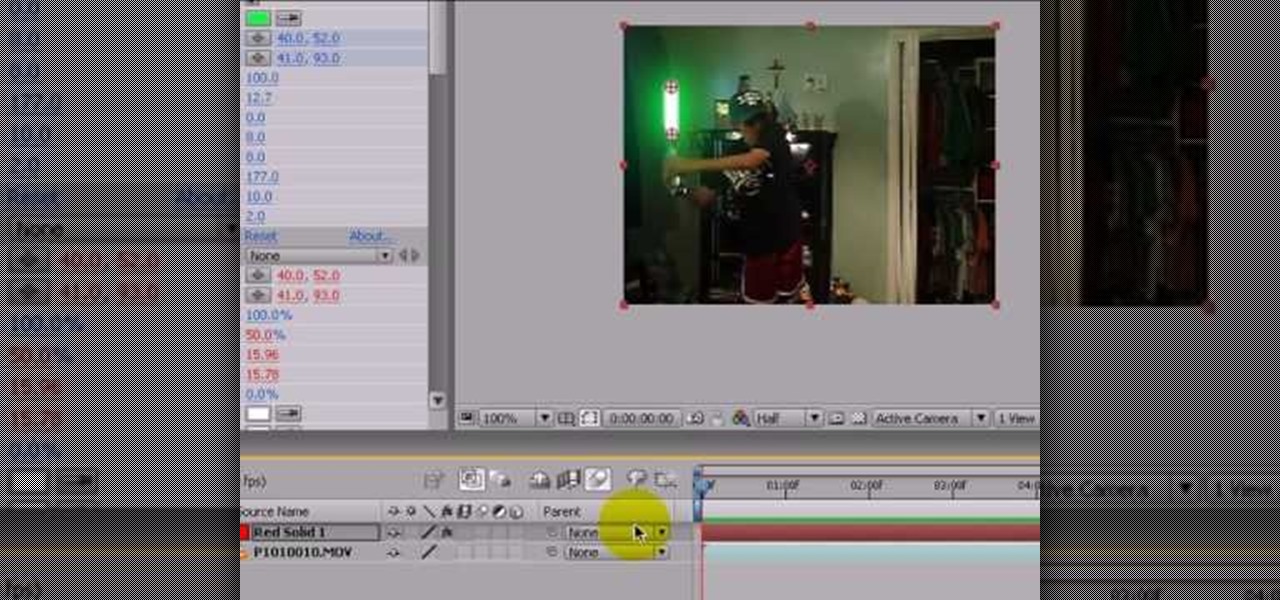
Did you ever want to know how to create Star Wars style lightsaber effects for your own home videos? Youtube user Comphelper225 has a way make this little bit of movie magic come to life using Adobe After Effects. Once you have a video of yourself or a friend swinging a base for your sword, the next step is to download Andrew Kramer's lightsaber presets from the Video Copilot website. Once it's installed, open up your video in After Effects to begin. Within the program, click Layer, New, and ...

Are you on a low-salt diet and need some healthy recipes that are friendly on your taste buds and wallet? This superb video serves up an easy and delicious recipe that will please everyone, whether or not the doctor has advised them to cut down on the sodium. The tutorial, one in a fantastic and free video series, offers excellent tips on how to properly cook your rice, as well as how to dress it up without damaging your health.

The menstrual cup is a great alternative to tampons and pads. This feminine hygiene product is reusable, eco-friendly and much cheaper than disposable tampons and pads. This tutorial teaches you how to insert and remove the menstrual cup. Watch this how to video and maybe you will decide to use the menstrual cup.

There are so many furniture polish sprays out there that sometimes its difficult to choose one. This how to video demonstrates how to polish wood using only olive oil and lemon. Its a safer, greener and eco-friendly manner of polishing and cleaning your furniture.

Watch this video to learn how to make a cranberry and popcorn garland. It's a beautiful decoration made of natural ingredients, and after the holidays it can be placed outside for the birds to enjoy!

Ever wish you could cuddle up to a cute little baby porcupine without getting hurt? Well, now you can!

There are few things more annoying than back button hijacking. You tap a link on a website and decide you want to go back to the previous page, only to remain on the same page again as if you didn't hit the back button. After years of frustration, Google has finally given us a solution.

Advances in technology continue to make our lives easier and more convenient. If you want to send fax, for instance, you no longer need to own a fax machine. You can easily and quickly send fax directly from your computer in one of several methods, including via an Internet fax service provider or using Windows built-in Fax and Scan tools. Read on how to use an Internet fax service, one of the faster faxing methods, to send fax messages from your PC.

Over the next few months, I'll be focusing on building a fully functional, long range UAV. This series will consist of several in-depth articles on my progress and the steps involved, so you can follow along and build your own unmanned aerial vehicle!

This article relates to changing the settings in Adobe Flash so that you can improve your overall computer security and privacy. Changing these settings might have a negative performance impact on your computer - but it is worth while.

Cheers to another completed Community Byte project! Things went well regarding timeliness and being friendly to the other coders and students. If you've got ideas for our next mission, or an idea for a tutorial, submit them to me. Friday, our mission was to take out HackThisSite, basic mission 5. This mission focused on JavaScript, again. This time there is a little bit more security in place.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

You may not know him by name, but Eric Leebow is the man we can all thank for inventing social networking. At least, that's what he thinks.

The whole world is connected to the Internet, which means bank for advertising companies who track your every move online. Most of the content you see on the web is free, and that's because of advertisements. If there were no ads, none of us would be addicted to the Internet because none of us would be able to afford it.
On Thursday, March 9, there was a news story on the evening news about Khan Academy (NBC News). The story began when Sal Khan started tutoring his cousin in 2004. Since he was in Boston and she was in a different city, he decided to make and post videos on YouTube so anyone could watch the videos. Later he added videos for her brothers and for people that contacted him with requests for other videos. During this time Sal had a job that he later replaced with another job. Today Sal has 2010 vi...

Alas, today we continue on the journey to a more environmentally conscious way of being with part 2 of How to make your beauty routine more eco-friendly. Check out part 1 here.

Hey everyone! Welcome to Cheaters Prosper, the best place on WonderHowTo to share your tips, tricks, cheats, walkthroughs and more for the games that you love! I'll be updating this as often as I can.

SEO is the name of the game. If you want your business or brand to succeed, ranking on the front page of Google is a boon. Getting to the front page of search engines takes work, but it's not impossible when you master SEO best practices.

Let's face it: standing out in the digital world is challenging. Graphics platforms are either cumbersome to learn or produce generic stock art. A better solution is needed.

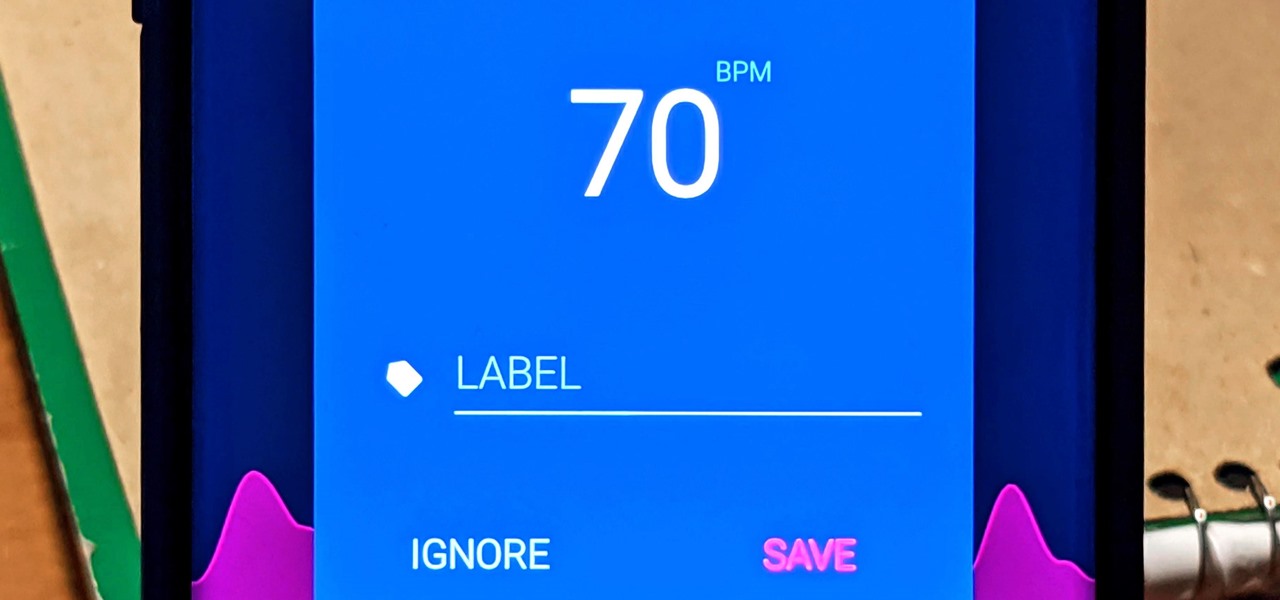
With the rise of smartwatches and wearables, you'd almost expect to need one to get a heart rate reading. While these devices can be helpful, not everyone has or wants to wear a gadget all the time to track their BPM. Luckily, when you combine Google Fit with a popular third-party heart rate measuring app, it will make things easy for you.

While "Baby Yoda" from The Mandalorian threatens to overshadow it, Star Wars: The Rise of Skywalker arrives in theaters next week, which means it's time for Disney and Lucasfilm to ramp up its promotional strategy.

When Facebook launched its first hardware products last year, the Portal and Portal+ smart displays, the company mostly touted its video-calling features as it faced off against Amazon and its Echo Show.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

Magic Leap is making it easier for developers to share their spatial computing experiments with other Magic Leap One users.

Unless you've been hiding under a (moon) rock for the past month, you already know that Saturday, July 20 is the 50th anniversary of NASA's Apollo 11 lunar landing.

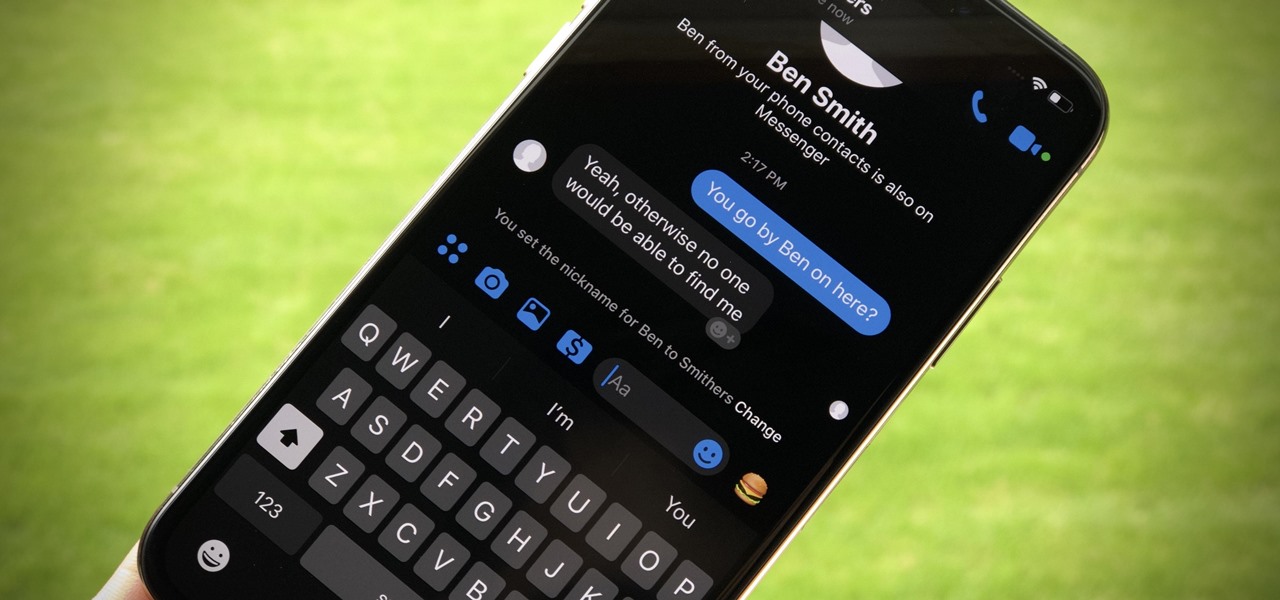
For the most part, people use real names on Facebook. That's all fine and well for keeping tabs on those you know, but it can make friendly Messenger chats feel oddly formal. Skirt around this stiffness by giving your friends nicknames in Messenger for Android and iOS, so your conversations reflect the way you and your friends communicate in real life.

After winning the 2015 FIFA Women's World Cup, the USA Women's National Soccer Team is ready to defend its title in the 2019 tournament.

The long-awaited augmented reality game based on the Harry Potter franchise from Pokémon GO masterminds Niantic is closer to release, as the developer has begun public beta testing of the app.

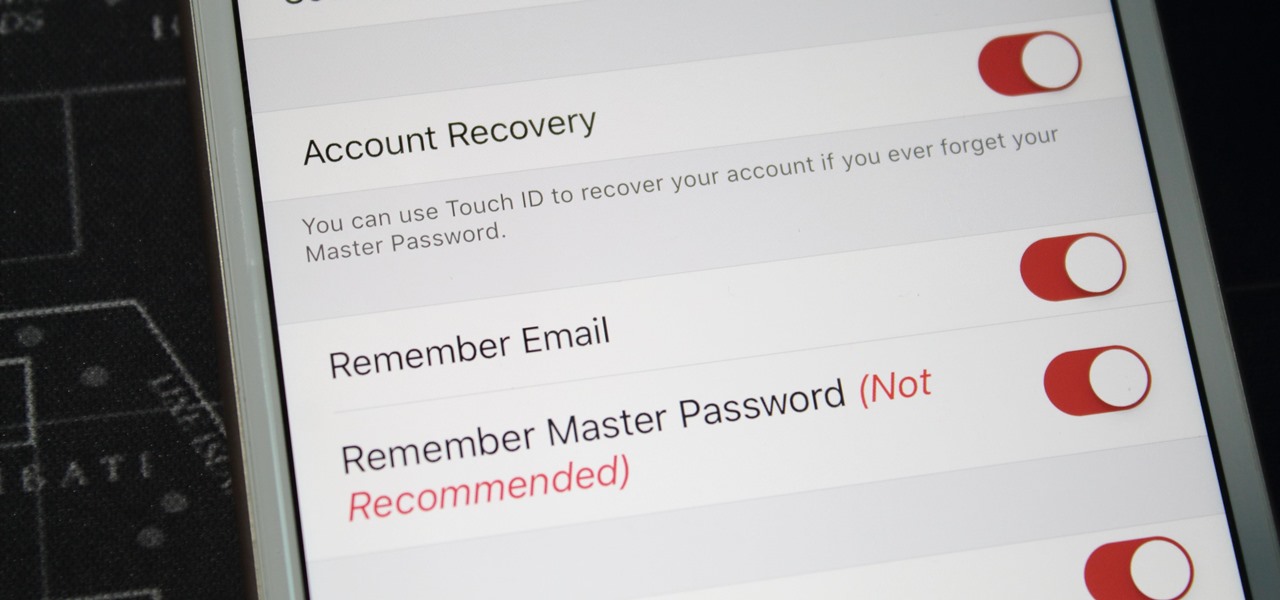
With any password manager, the only password you need to remember is the master password that locks the vault from both hackers and the company. This makes the master password very important. But what happens if you forget this password? Well, LastPass has you covered.

Instagram wants to bridge the gap between advertising and shopping for a more central buying experience. The app has long been a platform for advertisements, with both companies and creators using it as an outlet to link to products, so it's only natural for Instagram to allow users to buy content featured in posts without ever leaving the app.

Current-generation mobile augmented reality apps offer users numerous opportunities to punch up photos and videos with 3D content, but there's surprisingly few options for users to express themselves using virtual characters.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

After years of waiting, Microsoft has finally updated its industry-leading augmented reality device, the HoloLens.

It may sound like deja vu, but neural interface startup CTRL-labs has closed a $28 million funding round led by GV, Google's funding arm, for technology that reads user's nerve signals to interpret hand gestures.

Snapchat made augmented reality selfie effects famous, with Facebook copying the feature across its mobile apps. Of course, others have followed, but their face tracking apps often pale in comparison to the original.

The recent pitfalls and media fallout hitting Facebook hasn't stopped the social media giant from looking to the future.