Google is one of the most powerful forces on the Internet, and their technology can be the key to helping you find success in whatever your online endeavor might be, from web design to filmmaking. This video is a part of their Google Webmaster Series, offering help to webmasters the world over on how to best utilize Google in their work. This video will show you how to ensure that your Wordpress blog is safe from the hacker attacks that are so common for Wordpress users.

Create links and change elements with AS3 in Flash CS3 Use buttons to change the appearance of a button, navigate to a different place in a time line and link to a website. Use action script 3.0. Publish settings. Need to apply actions. Create an event listener. Attach to a button that you want it to listen for something to happen. When it hears a mouse click, it will execute the function. Give the buttons instance names R_btn, G_btn, and B_btn.
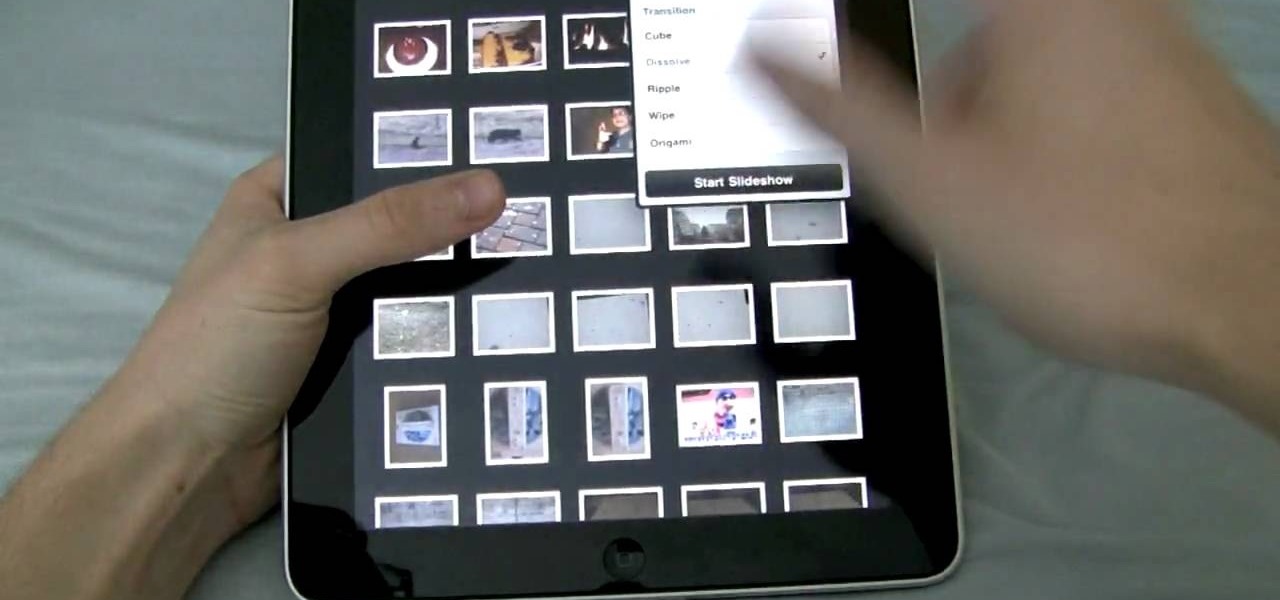
The iPad is the reigning king of the tablet PC's (although it isn't one, strictly speaking) and allows users to do things that they never thought possible with a computer. One of it's coolest and most applicable Apps is the Photo app, which allow you to view high-fidelity photos in a fun and portable way. This video will show you how this App works and how to use it to impress your friends with your awesome photos.

In order to access blocked videos and websites, you will need to set up a proxy service in the U.S., if you are trying to use Hulu. Go to a list site.

Photoshop allows users to create all sorts of cool text effects, some of the most popular of which involve creating firey or icey text for titles. This video focuses on the latter, teaching you how to combine several effects in Photoshop to create really cool letters that look like blocks of ice. Give you titles some flair! But don't get flares anywhere near them...
In this clip, learn how to use the Swype Key while texting with Swype on your cell phone. The Swype key is where all of your options are like dictionaries, tips and tricks, help menus and everything else you may need.

Ever wish there were a way to upload a video to YouTube without making it available to anyone with an Internet connection? While you might know about the option to make your uploaded clips private, limiting their viewing to 25 users of your choosing, you might not know about the newly introduced "Unlisted" status, which allows your videos to be viewed by only those people who know the video's direct URL. For more information, watch this free video guide from Tekzilla.

If you're a user of Google Chrome, you likely appreciate the browser for its speed. But were you aware the browser can be made faster still? This tutorial from Tekzilla demonstrates how to use smart shorcuts to speed up your web surfing. For specifics, and to get started using smart shortcuts yourself, watch this helpful how-to.

This video will discuss how to implement color changes in Photoshop editing. This step by step approach will tutor the novice Photoshop user how to utilize the various tools and applications to achieve, colorization in photos, swap select and hue, colors and backgrounds of photos, describes layering using saturation and blend techniques. This video tutorial will describe and demonstrate the correct settings and tool usage for easy application of each editing and color manipulation.

Household Hacker brings you fun hack how to projects in a variety of areas: electronic hacks, computer hacks, pranks, etc. Search Household Hacker on WonderHowTo for more videos by this creator. In this video, learn how to make YouTube paper.

Let us help you install your JVC Everio software and hook up your JVC HD Everio video camera to your computer. Just select your operating system.

In this video I show you how to get a Flash plugin to allow you to play videos in safari. Your iPhone/iPod Touch does not have to be jailbroken to do this. If you are having problems not getting the email make sure you look in your bulk or spam folder of your email. Just click the activation link in the email refresh the safari page and everything should work.

A steadicam can mean the difference between a professional and steady wide shot of Victorian era London or a wobbly, user-generated content-esque portrayal of some old lamps and streets. Having control over how your camera moves is so vital to good film production.

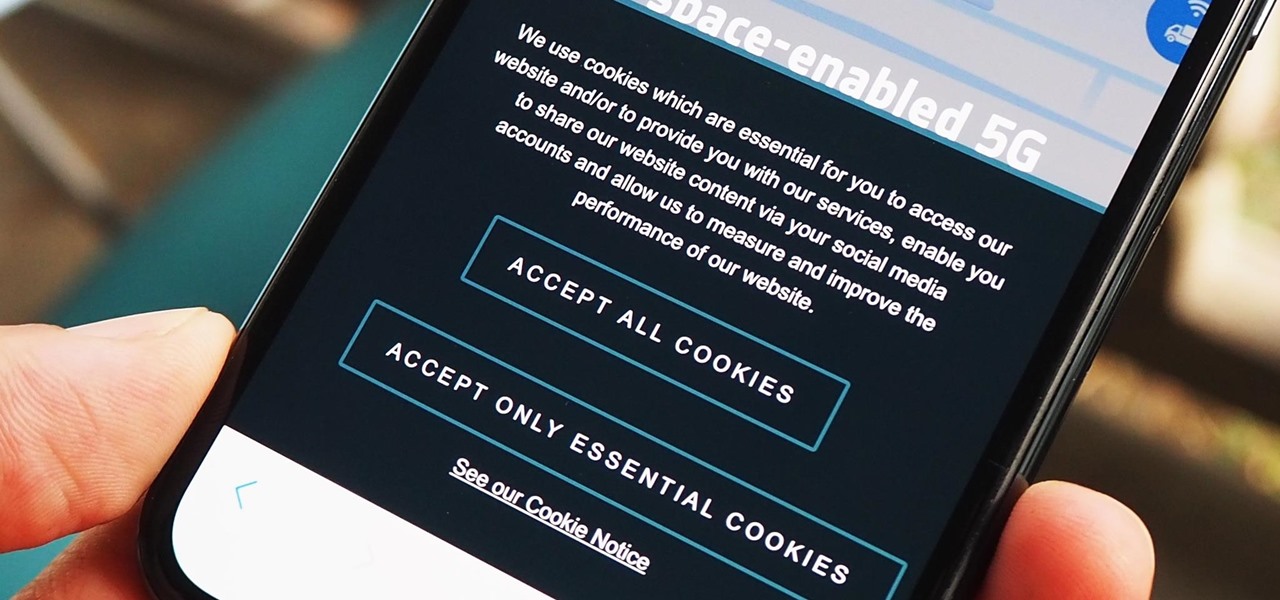
As a means to combat annoying and intrusive advertisements in Safari, Apple added native support for content blockers on the iPhone. Instead of being bombarded by notifications, banners, and pop-ups, content blockers prevent them from opening, which can also be said about those annoying cookie consent notices that many websites now have.

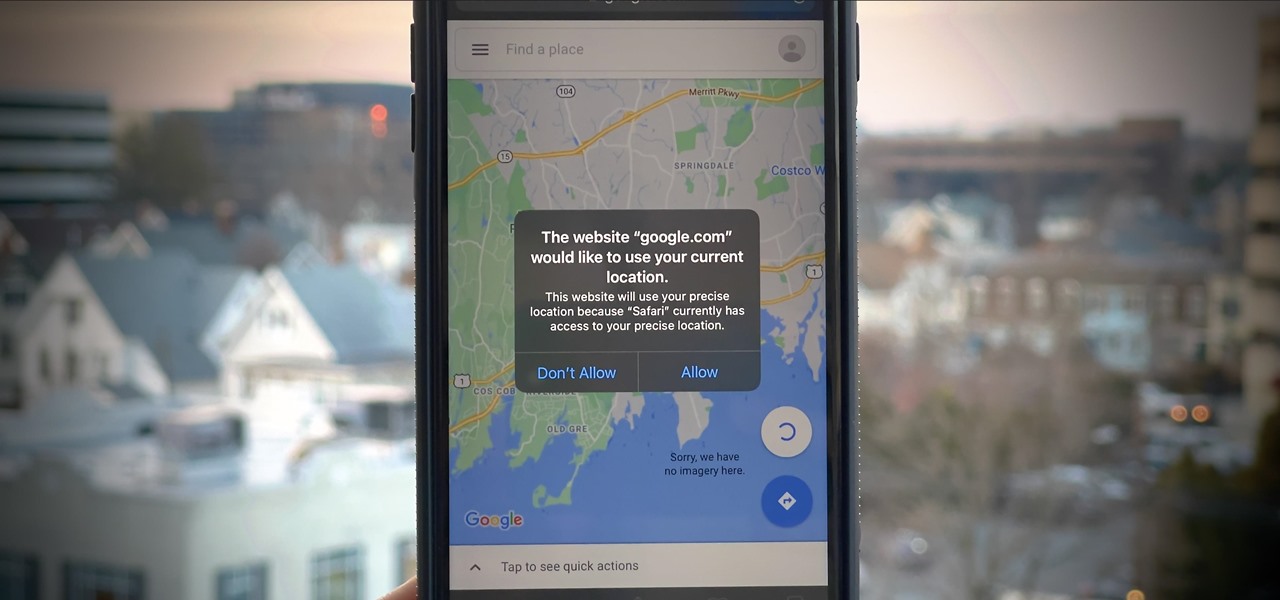
If you surf the web on your iPhone, you no doubt run into this problem all the time: a website wants your location. It can happen when performing a location-based task, such as using a store locator, or whenever a web app just wants to deliver better ads or local recommendations. If you're tired of allowing or denying permission each time, there's an easy way to stop the annoying security pop-ups.

With many office workers in the US being asked to work from home if their job allows, Magic Leap's customary updates for the Lumin OS and Lumin SDK brings some help to keep distributed workforces connected.

Lego has shipped several apps and products that add an augmented reality dimension to their playsets. But it has taken a reality TV show from Fox to allow brick fans to build with virtual bricks in augmented reality.

Did Google CEO Sundar Pichai kill Google Glass for non-enterprise users? That's the obvious first question following news that non-enterprise Glass users will no longer have access to Google's core apps after February 2020.

As far as HBO is concerned, it's not augmented reality — it's Snapchat. The premium cable network is leaning hard on Snapchat's AR magic tricks to promote yet another series, this time for the adaptation of Philip Pullman's His Dark Materials series of novels.

With Android 10 hitting the streets (at least for those mobile devices that get quick updates) and the public release of iOS 13 dropping on Sept. 19, Google is releasing an update on Thursday to ARCore that adds some fantastic new benefits to its cross-platform capabilities.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

Just weeks after revealing plans to port one of its most vital augmented reality products from HoloLens to the smartphone world, Microsoft has finally opened the mobile software floodgates to the public.

After showing off a prototype of the Grordbattle multiplayer first-person shooter at the Game Developer Conference, Magic Leap has added a new Shared World feature in version 0.95.0 of the Lumin OS update released this week.

Now that the NCAA Basketball Tournament is underway, 7-Eleven has decided to launch an augmented reality experience to remind basketball fans where they can quench their thirst throughout March Madness.

Every now and then, Hollywood has a moment where two (or more) movies arrive at around the same time, most recently with the release of dueling Fyre Festival documentaries.

Mobile augmented reality company Snapchat now has a special option for romantic message exchanging this Valentine's Day, a day which, incidentally, happens to be the first one in 116 years where Sweethearts, the original heart-shaped candy, will be unavailable for purchase.

With Magic Leap One approaching six months since launch, Magic Leap is fully focused on building a content ecosystem and developer community.

The newly-announced Moto G7 Play offers some of the same upgrades as its sibling, the Moto G7, but at a much lower price. The upgrades are pretty significant when compared to last year's Moto G6 Play, taking this phone from the "only if you're on a strict budget" category into a great value option.

The emerging narrative as CES begins is that consumer-grade smartglasses require a heavy compromise in functionality in order to arrive at a form factor and price point that appeal to mainstream customers.

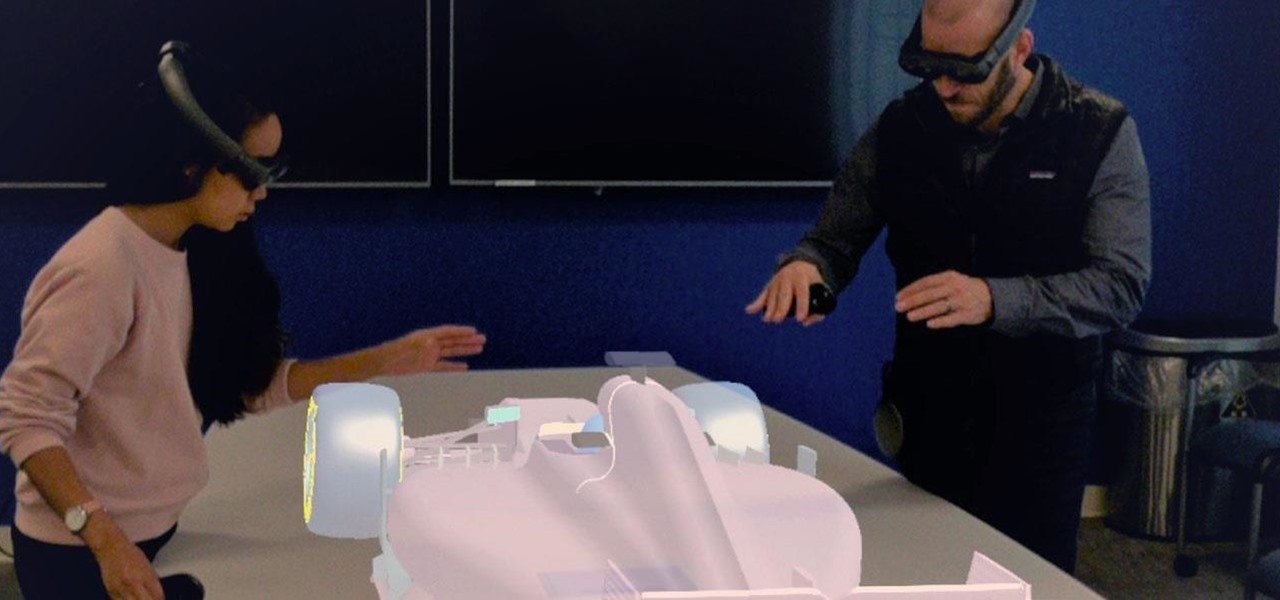
Publicly, things have been pretty quiet over at Meta, the augmented reality headset and software startup based in Silicon Valley. But that doesn't mean that the company doesn't have a few strong opinions about the state of AR in 2018.

Departing from the long string of entertainment-focused partnerships released in recent weeks and months, a new, enterprise-focused Magic Leap app has finally emerged in the form of Onshape.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

Less than four months after Snapchat introduced its Snappables platform, Facebook has met the challenge with its own AR gaming feature that surpasses the originator.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

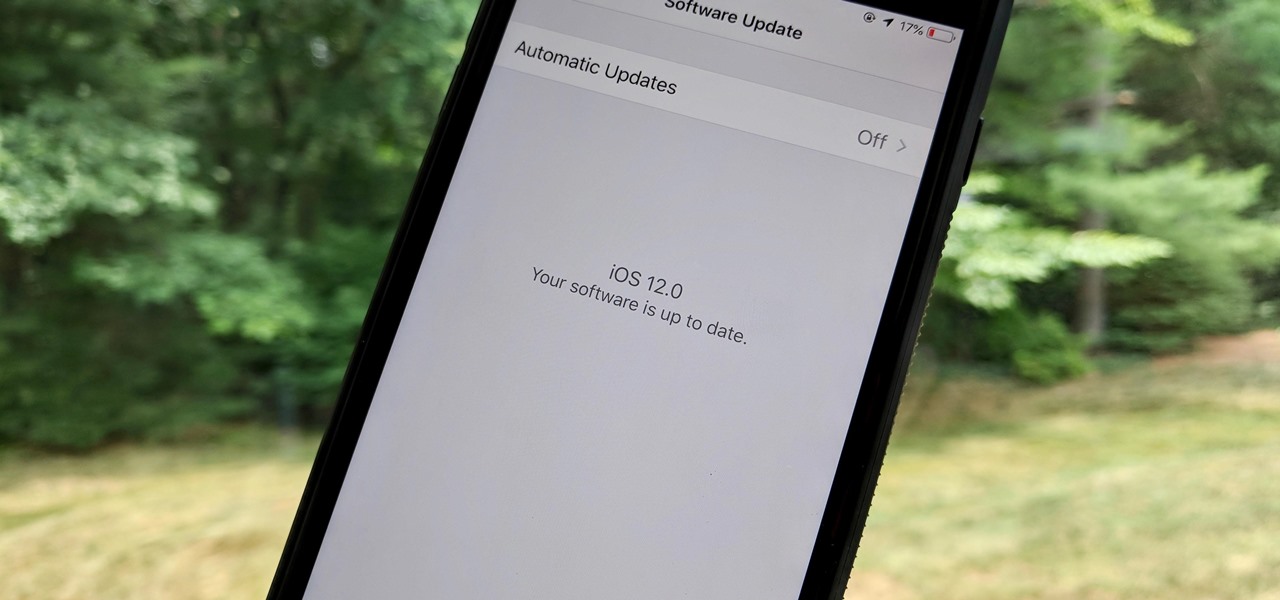
As the official release of iOS 12 nears closer each day, Apple continues to update its betas. The company released the fourth beta of the upcoming software to developers Tuesday, July 17, exactly two weeks after the release of the third developer beta which came out just a few days before the second public beta.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

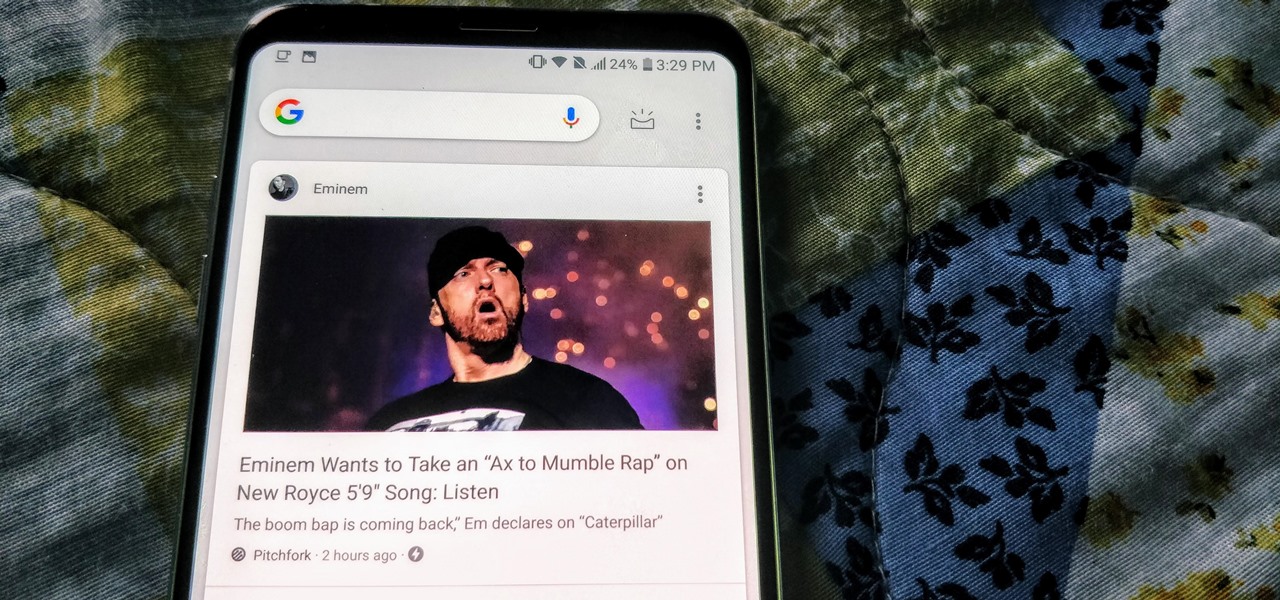
One of the better additions in the stock Android launcher is the Google Now page. Residing to the left of the home screen, this page presents a host of information based on the user's interests, which Google bases on analyzed data. Recently, the Google Now page design received a makeover which Nova Launcher users can now enjoy.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.