Every industry has its own jargon, acronyms, initializations, and terminology that serve as shorthand to make communication more efficient among veteran members of that particular space. But while handy for insiders, those same terms can often create a learning curve for novices entering a particular field. The same holds true for the augmented reality (also known as "AR") business.
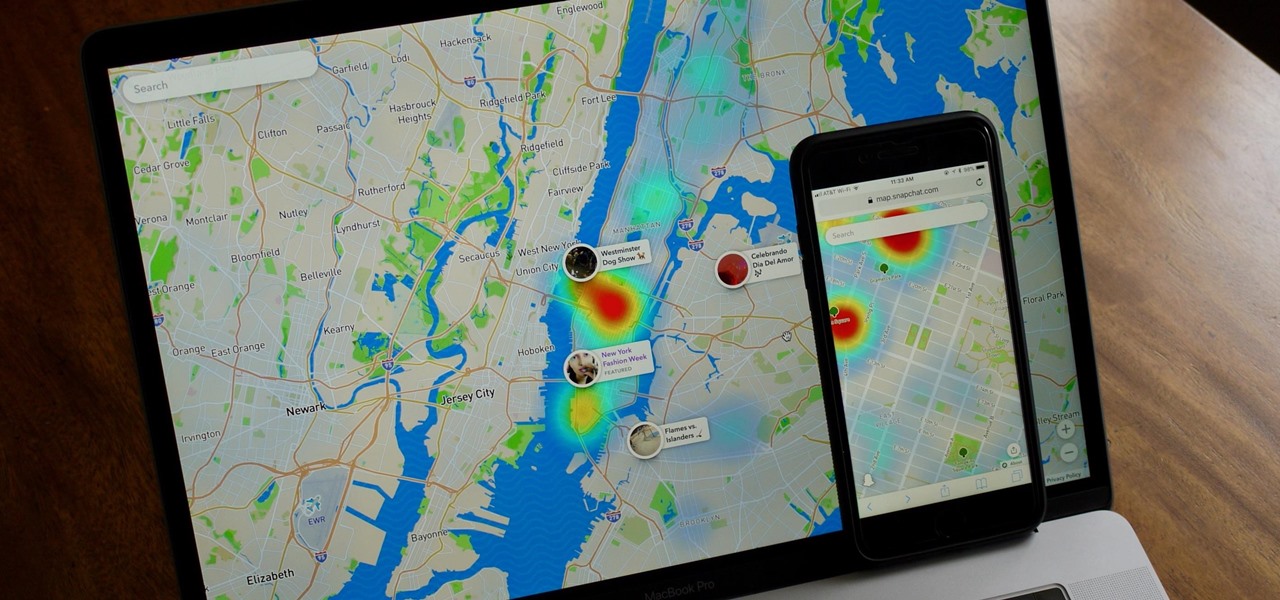
When first released, Snap Map made a lot of users uneasy. Beaming their location to the world at all times isn't necessarily the definition of privacy, but Snapchat's map is nonetheless intriguing, offering users a view into the lives of people across the globe. Now, you don't even need to have an account to access Snap Map — you can view it right from your web browser.

Unsurprisingly, Google wants to be the caretaker for augmented reality on the web, and its latest move in this endeavor is a 3D model viewer prototype called Article that's designed to work across all web browsers.
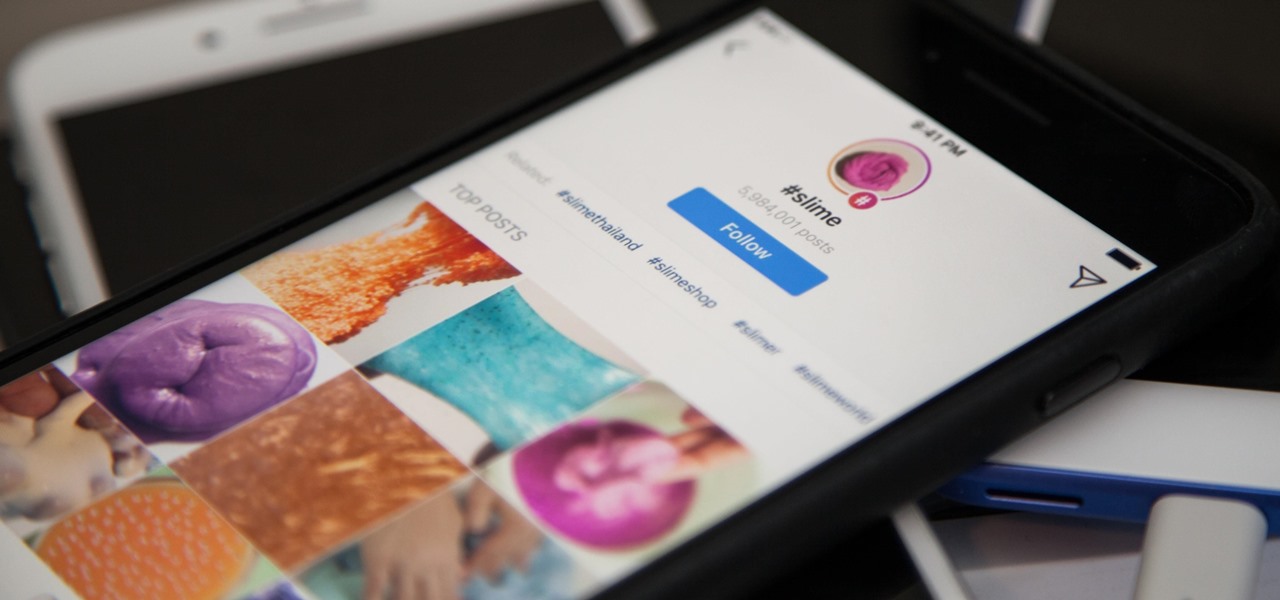
Hashtags are the backbone of Instagram. They connect photos from users all around the world and give visibility to users who don't have many followers. Now, Instagram has added more functionality to this indispensable tool, and this new feature lets you follow hashtags in your main feed right alongside all the pics and videos you see already from people or companies you follow.
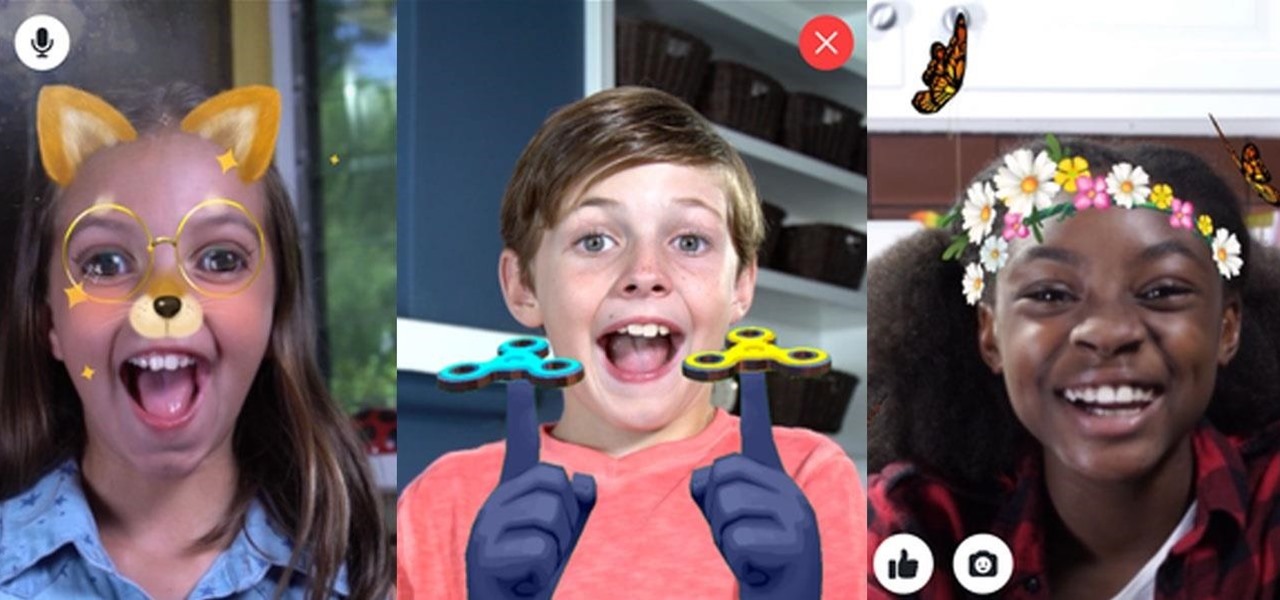
Next to millennials, one of the groups most coveted by brand marketers is "Generation Z," the consumers of tomorrow who were born between 1996 and 2010. On Monday, Facebook established a beachhead with that demographic in the realm of augmented reality by launching Facebook Messenger Kids.

With the advent of ARKit, apps that can place virtual furniture in a real room have become nearly a universal practice for furniture retailers, with Pottery Barn being the latest to join the fray.

Have you recently tried to type the words "it" or "is" on your iPhone only to have the Apple keyboard attempt to autocorrect them to "I.T." or "I.S.?" If so, you're not alone.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

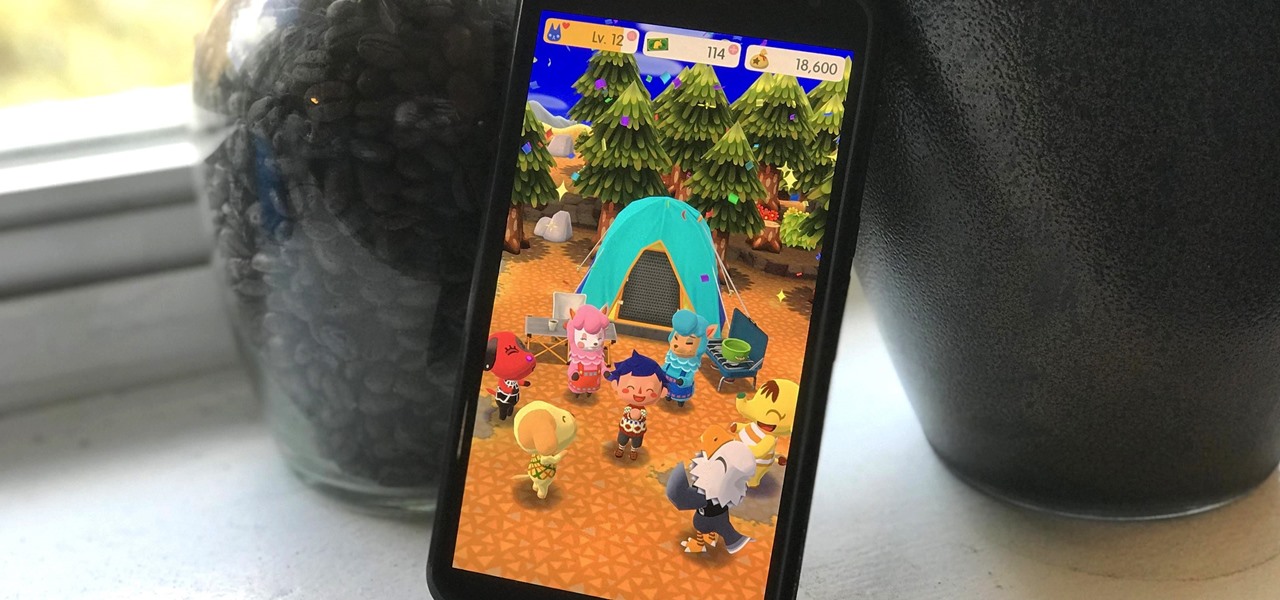
For a friendly mobile game, Animal Crossing: Pocket Camp has an overwhelming number of items and collectibles — from fruit to fish to friends. Even though it can be difficult to keep up, this guide will be a great stepping stone to creating the campsite of your dreams without spending a dime.

At the Augmented World Expo Europe press conference in Munich today, RE'FLEKT will unveil the addition of remote video calling to their RE'FLEKT One enterprise augmented reality platform, in addition to ARKit and ARCore apps that demonstrate the platform's capabilities.

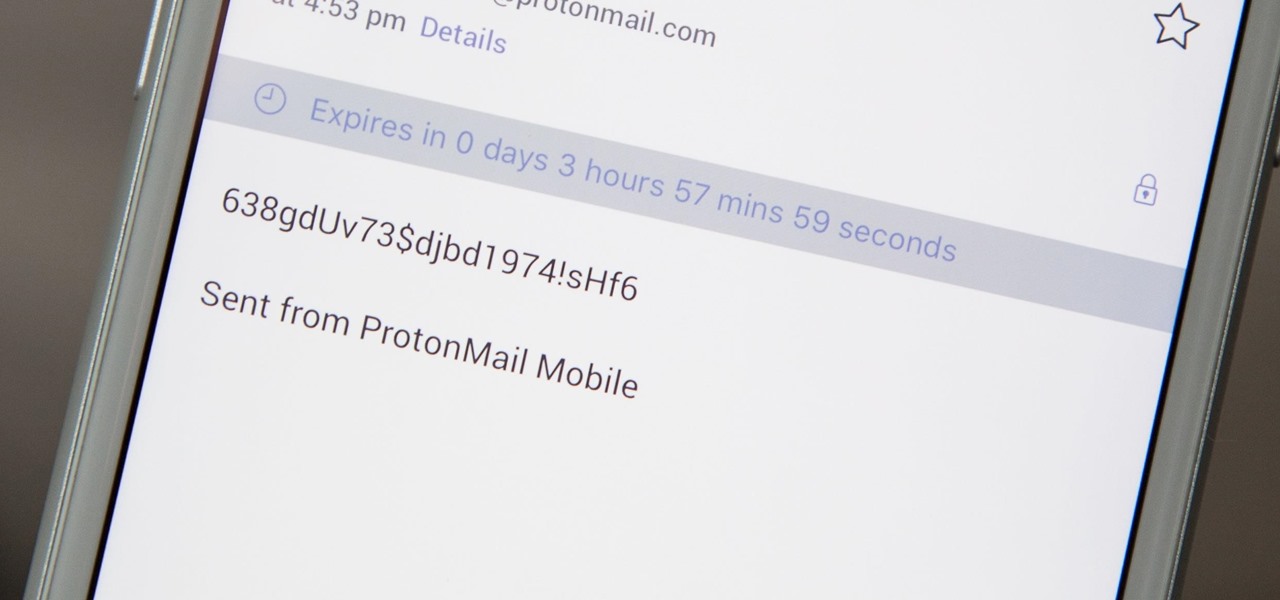
When you're sending sensitive information via email, it's best to do so with end-to-end encryption. Even better, set the email to destroy itself after a set amount of time for a little piece of mind.

At IFA in Berlin today, Sony introduced the latest models of the Xperia line, with new features in tow that should appeal to creators of augmented and virtual reality content.

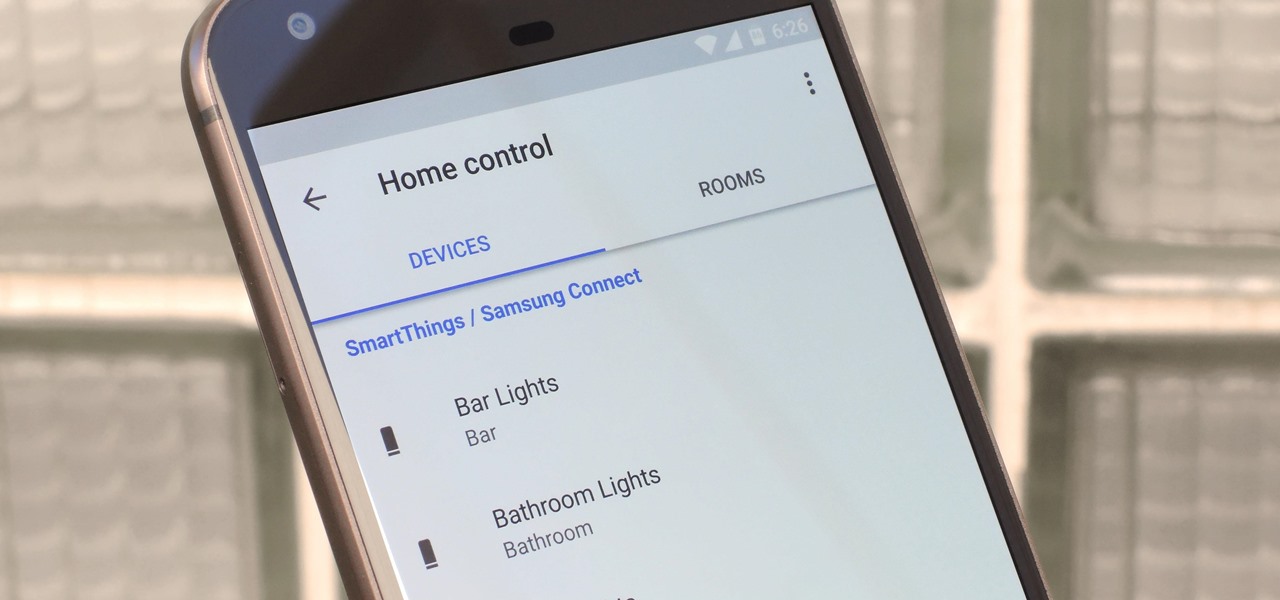
The world around us keeps getting smarter. Not only do we have advanced AI services like the Google Assistant, but now we've got the Internet of Things connecting physical objects to the digital world. It's amazing when you think about it, but the real sci-fi stuff starts to happen when these two technologies intersect.

Though the Microsoft HoloLens' release to the consumer market is still a distant thought at the moment, Ubisoft is preparing for the future with the unveiling of AR video game prototypes.

Aspiring engineers, your challenge, should you choose to accept it, has been issued by Jaguar Land Rover.

While you may not notice them at first, iOS 11 included some pretty significant improvements to the Photos app on your iPhone. These upgrades will help you make your Live Photos livelier, surprise you with photos you totally forgot about, keep your photos and videos organized, and more.

According to a source at TechCrunch, a new version of Snap's 'Spectacles' could include augmented reality.

Meta CEO and founder — and Next Reality 50 member —Meron Gribetz unveiled a new operating environment for augmented reality called Meta Workspace for the audience at the Augmented World Expo (AWE) in Santa Clara, California, today.

Tim Cook claimed 85% of new iPhone buyers are switchers from Android back in 2015. Now, after financial analysts noted a drop in the company's stock prices, Apple has unleashed a series of ad campaigns directly targeting the users it needs to win over. That's you, Android lovers.

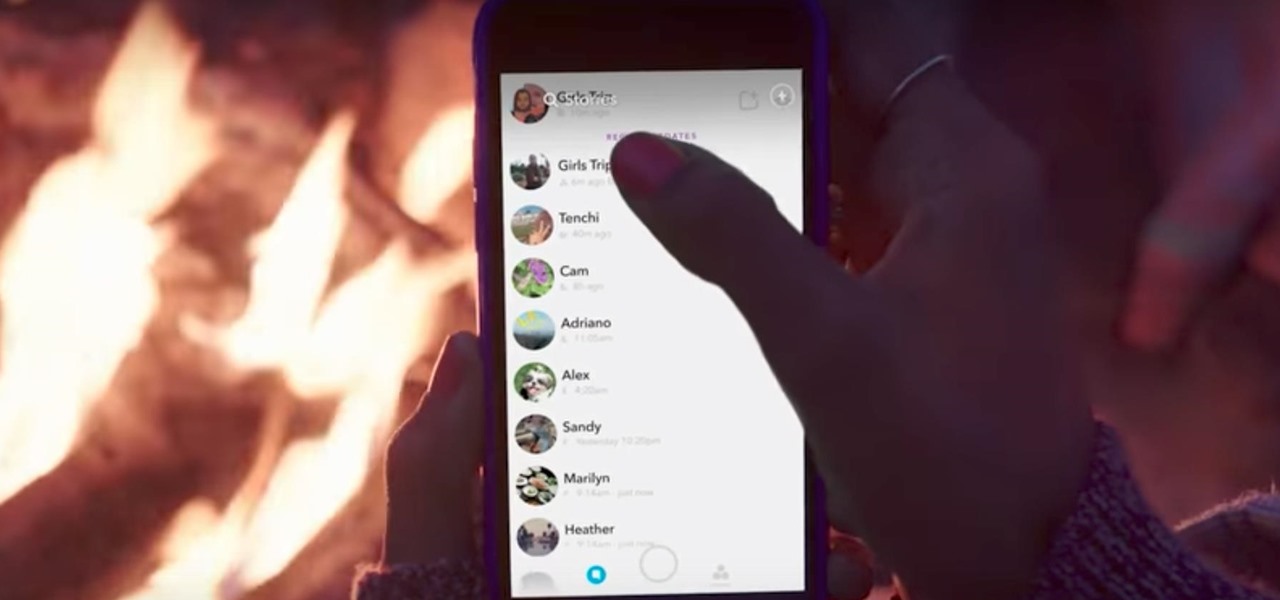
Snapchat hit back at its arch-rival Facebook this week with a number of new Group features, including custom stories. Facebook and Instagram both rolled out clone Story options this year, but Snapchat is obviously trying to up the ante in this arena.

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.

Malware attacks on mobile phones are reaching an all-time high and it looks like companies like Samsung are doing all that they can to prevent any unwanted hackers from accessing its sensitive user data.

Amazon's first venture into the wireless phone market was a crash and burn moment — and that's us being kind. Their FirePhone went down in flames almost instantly, no pun intended.

Facebook really wants us to use Messenger. For the most part, they've succeeded; theirs is one of the most popular messaging apps right now. And with yesterday's announcement of new features, Facebook is only going to make their flagship chat application better.

The popular beauty app company Meitu is incorporating augmented reality (AR) video and image filters and effects in its selfie-editing app BeautyPlus for iOS and Android.

There are already a few ways to use your home computer on the go, but none of them feel very natural when you're out and about, and are clunky options at best. Samsung wants to change that with Monitorless, their upcoming augmented reality smartglasses, which offer remote desktop viewing capabilities as well as the ability to switch between augmented and virtual reality modes using electrochromic glass.

Creamer, milk (whole or skim), sugar, or even butter—you've probably added at least one of these to your coffee to improve its taste at some point. If you're looking for something different, though, try a new twist with a dash of cinnamon. This sweet, sharp spice can do so much more than improve coffee's taste, and I've got 10 examples for you to consider.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

Historically, battery life has not been a strong suit for machines running Windows. Poor decisions by hardware manufacturers combined with the resource-hogging behavior of Windows are to blame. However, Microsoft is trying to resolve this issue, once again, with the release of Windows 10.

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

Microsoft dropped a couple of huge bombs at their Windows 10 event Wednesday afternoon. Free operating systems and holographic glasses? This must be a Sci-Fi novel or a Hollywood blockbuster, because it reeks of fiction.

Aside from its many high-end features, the camera on the LG G3 is up there with other heavy hitters like the Galaxy S5 and HTC One.

so i have just signed up to this, and i dont know much about this website but i wanted to show my recent upload

Just what are probiotics and why are they so good for you? Probiotics are "viable microorganisms" that can confer lots and lots of health benefits if they reach your intestine while they're alive. You may have heard them described as "friendly bacteria."

Custom Timelines (CTs) allow you to control exactly which Tweets appear in a column on Tweetdeck. So if a particular event catches your eye as newsworthy you can tailor your CT to show what you consider to be the most relevant Tweets. These CTs can then be customized, shared and embedded on your website. This is a great way of increasing interaction on Twitter and sharing current, interesting and breaking news stories from any niche or subject

Instagram is not only a great platform to easily share some of your favorite moments with friends and family, it's a useful service for peering outside of your physical location. While you share a picture of your dog in Los Angeles, you can almost instantly view and like a picture someone posted of their breakfast in Tokyo.

Bottled water is a rip-off. Not only is it pretty much the same stuff that comes out of your tap for free, but plastic bottles are rarely recycled and thus account for a huge amount of the waste that's overflowing our landfills. Next Up: Water Bottles You Can Eat

How to Henna Your Hair Tutorial Pt.2 Please Dont forget to Watch Pt. 1

Video: . How to Henna Your Hair Tutorial #1

Very interesting interview with the editors of the New York Times Lens Blog, a website which is totally dedicated to photojournalism and videojournalism.