In this video tutorial, viewers learn how to perform the best six pack abs exercise. In this video, viewers will be performing the plank and side plank exercises. Users should be straight and have hips pushed down. Pull the belly button up, squeeze the pelvic muscle high, point the chin down and squeeze in stomach. Hold this position for about 30 seconds. On the side plank go in a straight position, squeeze, pulse up and feel the oblique muscle. This video will benefit those viewers who want ...
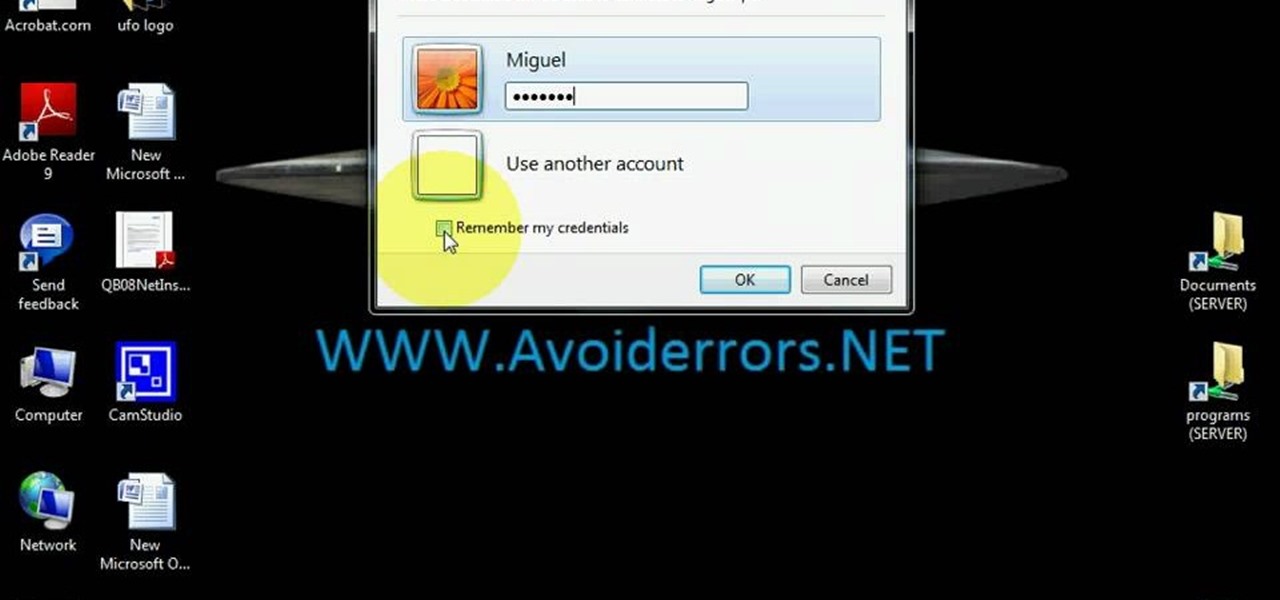
Learn how to use Windows Vista remote desktop on your computer in simple steps. First go to Control panel, select 'User accounts' and create a password for your account. Now right-click on My Computer, select 'Properties' and click on 'Remote settings'. Now select the user you created by searching and return back to the properties area. Go to 'Advanced system settings', click the Computer name tab and find your computer name. Now open the Remote desktop connection, enter your name and enter y...
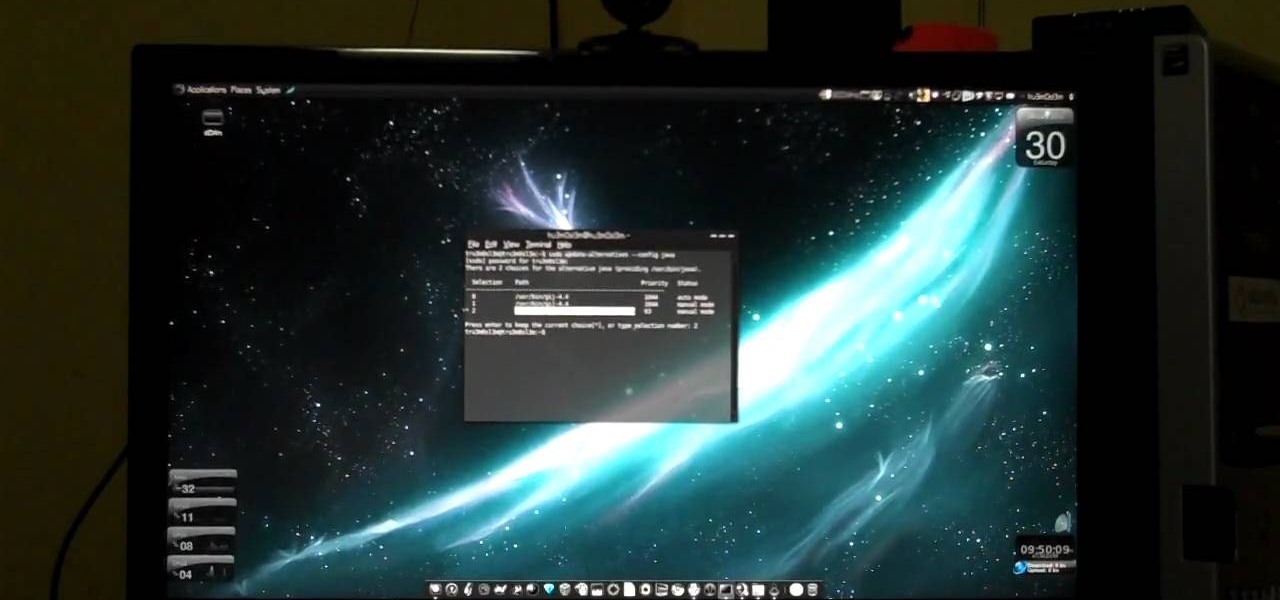
In this video, viewers learn how to install and setup JDownloader on Ubuntu Linux Downloader is open source download manager. It simplifies downloading files from One-Click-Hosters like Rapidshare.com or Megaupload.com - not only for users with a premium account but also for users who don't pay. It offers downloading in multiple parallel streams, captcha recognition, automatically file extraction and much more. Of course, JDownloader is absolutely free of charge. This video will benefit those...

In this video tutorial, viewers learn how to make a dirty martini and Bloody Mary. The dirty martini is a cocktail made with gin and vermouth. A Bloody Mary is a popular cocktail containing vodka, tomato juice, and usually other spices or flavorings. For a dirty martini, users will require these ingredients: 3 oz of gin or vodka, 2tsp of dry vermouth, 1 tsp of olive brine, 1 olive, and ice. To make a Bloody Mary, users will require these ingredients: 1 1/2 oz of vodka, 3 oz of tomato juice, d...
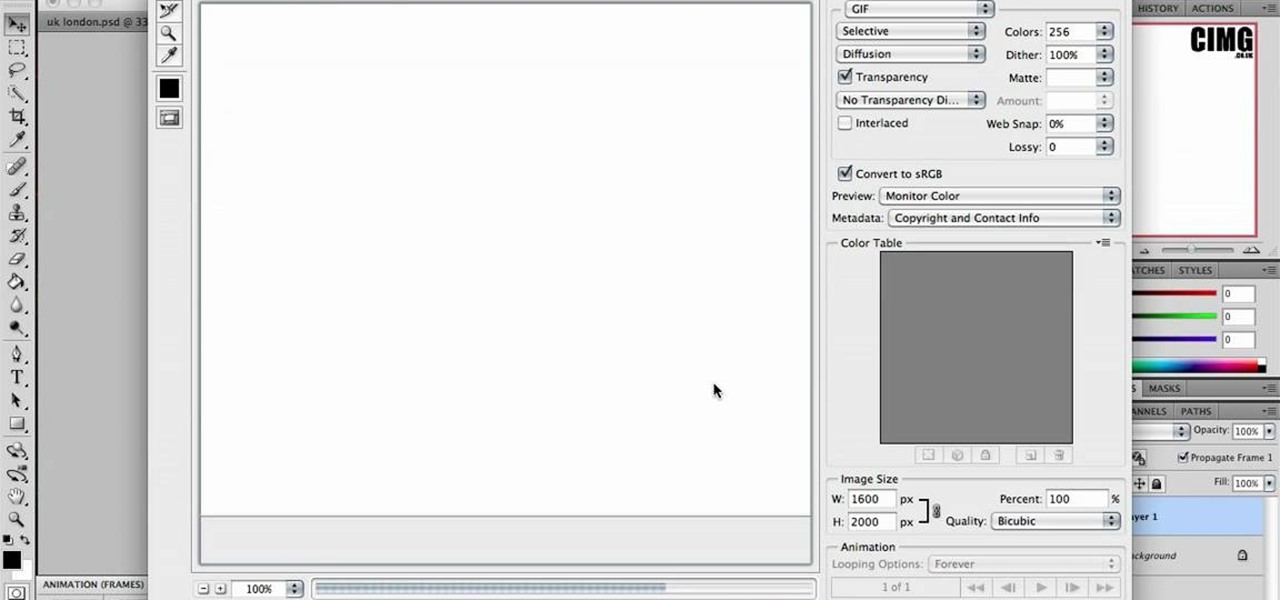
This video shows the process of making animations in the image program Photoshop. It shows users how to open up and navigate the animation dialogue box in Photoshop by adding frames with variations on the image to be animated, with attention to using as many frames as needed to ensure a "clean" looking animation (one that is not jumpy but rather has smooth transitions). In closing, the instructor shows its viewers which options to select on the animation settings (particularly noteworthy is t...
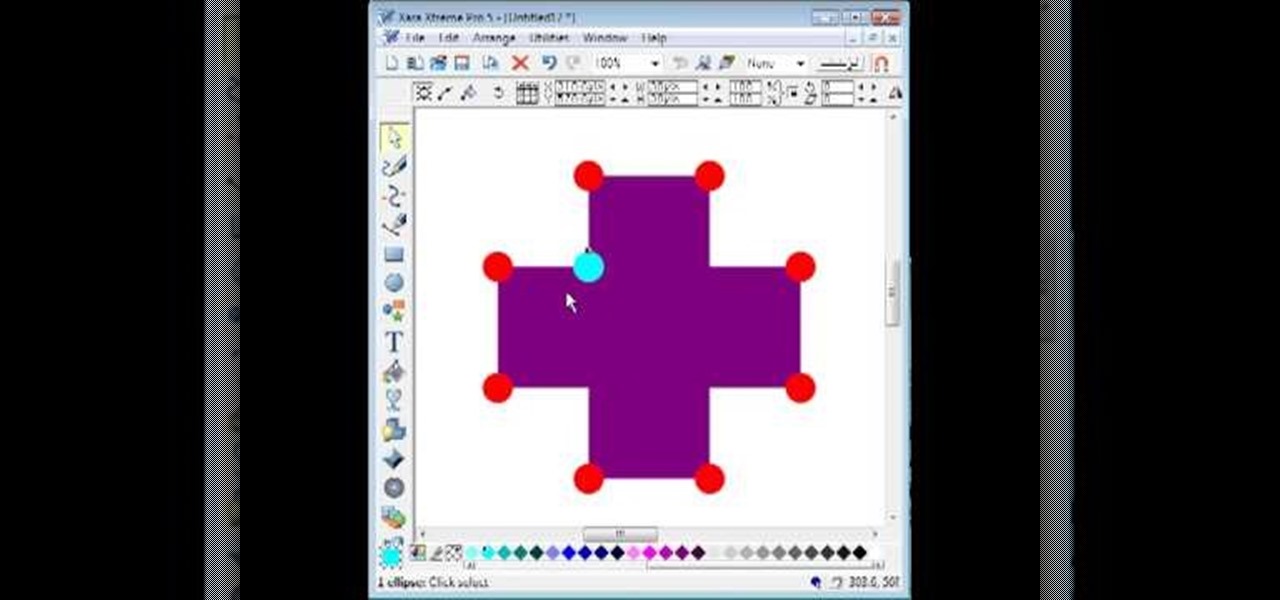
By utilizing the click and drag features of Xara Xtreme, users can take shapes and duplicate them for quick work (ctrl K). Further by identifying them by colors and other subsets, users can add or delete with just a button push, or (use the add shapes, subtract shapes options.) All this is done in the event for the sake of convenience; eliminating the tediousness of creating shapes one by one, and using them as plot points on a map to create projects within record times.

There's no better way to learn or simply brush up on a scripting or programming language than using it. In keeping with that philosophy, this video tutorial will walk you through putting together a full-featured, dynamic clock app that keeps track of both the tdate and time.

The ability to create professional and clean presentations can be a valuable asset to one’s career. With this video tutorial, learn how to use Adobe Presenter in order to augment Power Point presentations. Presenter offers users the ability to record narration under a set order of slides in a simple interface, and provides an interactive quiz option to further engage audience members. Alternatively, users may also convert a presentation into PDF format, for use as a physical or virtual document.

Are you interested in becoming a master Adobe Acrobat 9 user? Who better to teach you than this expert user from Adobe TV? This video tutorial narrates how to create basic fillable forms within Acrobat 9 using the Live Cycle Designer form wizard. An exact replication of what you can expect to see on your own screen makes the process incredible easy to follow. You can become a seasoned Acrobat 9 professional in no time with this series of fantastic videos.

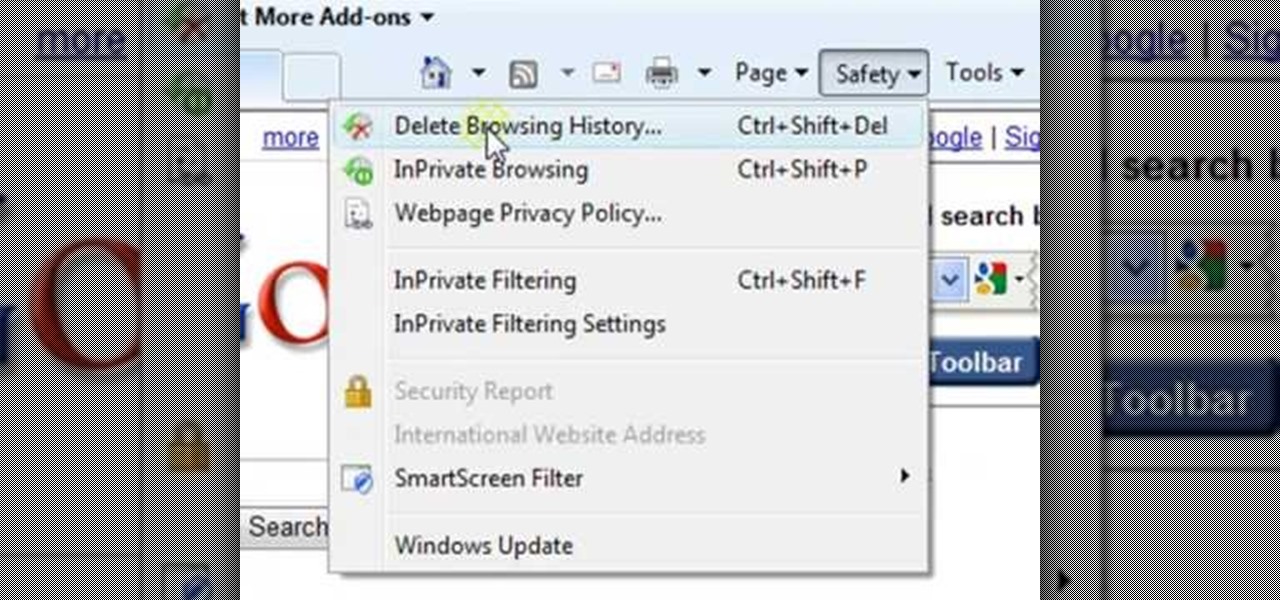
ClearTechInfo presents a how-to video on clearing Internet Explorer 8's browser history. Computer users are reminded that the only silly question is the question not asked. In the video, the viewer is shown that by clicking the button marked "Safety" in Internet Explorer 8 the "delete browser history" option is revealed. As long as each option is clicked, the history for the computer user is deleted. The browser history, cookies, cache, and passwords can all be deleted with the click of the b...

Software expert David Steinlage guides the viewer through the step-by-step process of installing VMware and Windows XP on a computer driven by Ubuntu Linux. The first step is to get a serial number, which can be obtained free by visiting the site www.vmware.com and filling out the registration form. The VMware installer application Automatix is then opened and upon clicking the desired options, the installation of VMware starts automatically. At the end of installation, the user is prompted t...

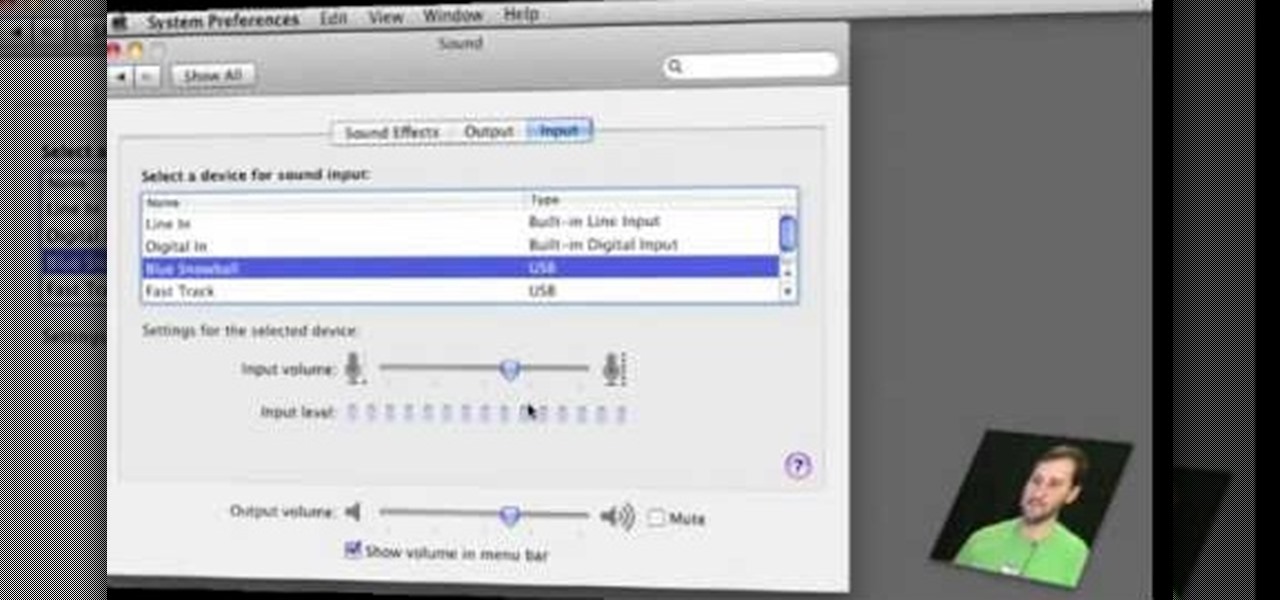
Gary Rosenzweig of MacMost is describing how we can use sound input and output controls on one's Mac computer. He mentions of the availability of multiple input and output devices like built-in mic; line-in etc and speakers , USB headset and provides a detailed information of using each of it; by selecting the one the user requires. He shows how the user can use popular communicating tool the Skype with the Mac laptop. One must go through this video to understand the selection of the output o...

This video will allow you to view your saved usernames and passwords in Firefox. This may be useful for users in case you forget what your user names or passwords are for different sites and would like an easy way to find them. Under the Firefox toolbar, go to "Tools" and then "Options" in order to get a popup which will allow you to view different aspects you can change in Firefox. Go to the security tab and then click on the button which says "Saved Passwords" in order to view all your save...

This video shows you how to recover and read someone else's text messages with a SIM card. It's called a SIM reader professional. It reads the information on the SIM card. You can either buy one or rent it. This device can give you information that has been deleted from the user's phone such as phone numbers, phone calls, contacts, text messages and MMS messages. Then you can block numbers and control who is calling your child.

To be the best at the Madden NFL video game, you have to be willing to get advice, but not just any old advice... professional advice. To beat everyone, you have to be ruthless and know all of the strategies and gameplay tricks. To master Madden 08, check out this quick, football game, video tip from Madden Nation (EA Sports and ESPN) with video game pro Haaruwn Brown (or Houseshoe).

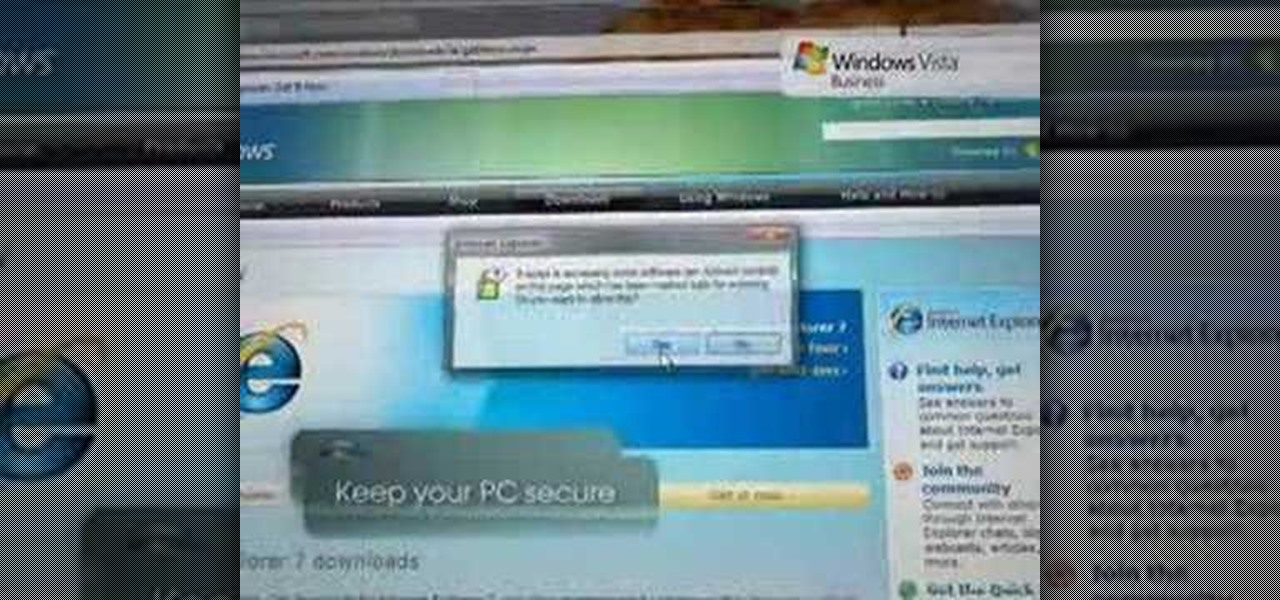
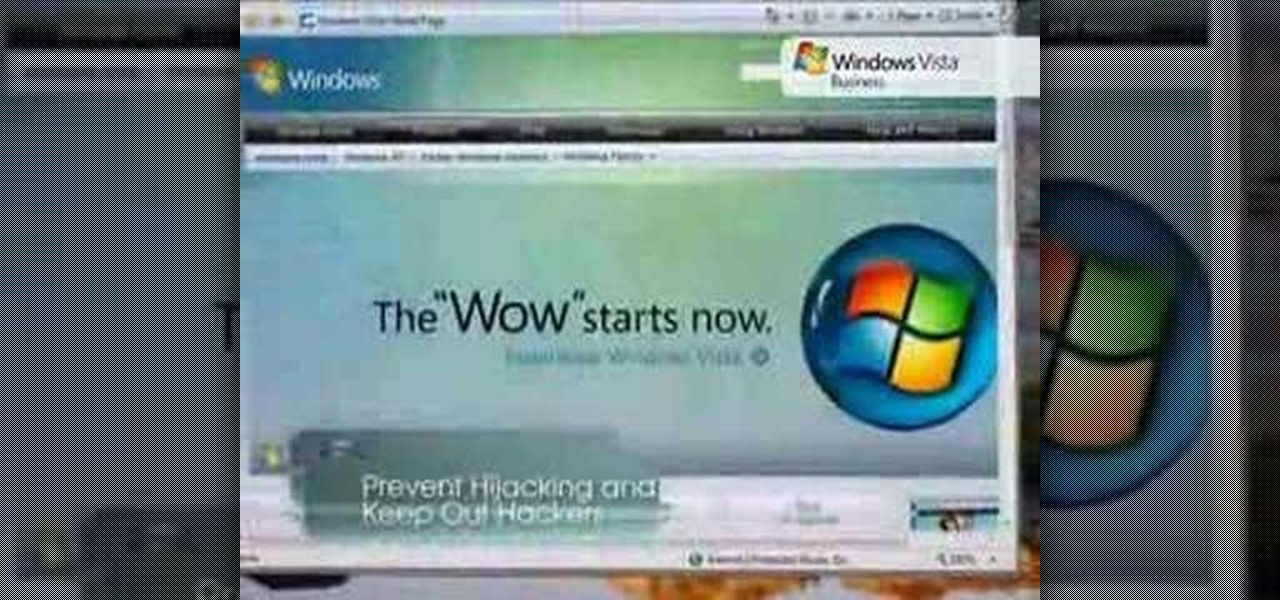
Web browsers such as Windows Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Microsoft Internet Explorer 7 has several new features that make using the web easier and safer than ev...

Web browsers such as Windows Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Microsoft Internet Explorer 7 has several new features that make using the web easier and safer than ev...

This is a maya 8.5 lesson but Jason really wanted to cover this crash course in animation for Zbrush users. This is everything you need to know for a pose to pose animation setup. This is geared towards illustrators to learn the basics, not full animators.

This tutorial is for users new to Zbrush or Zbrush 3.0 users wanting to understand all the differences and new features for brushes and masking in 3.1. The first video also covers the interface and new abbreviations on icons.

In this tutorial, we learn how to use torrent software like uTorrent. First, go to the website, Burn OSX, and download their software, then install it. After this, go to isohunt. When you get to this website, type in the name of the item you are searching for. When you find it, click on it and it will start to download through uTorrent. When finished, you will be able to open up what you downloaded and then use it how you wish. It will then start seeding, which means that it is being shared w...

If you would like to use Google AdSense on your website, in order to make money from your site, you will need to get a Google account. Click "sign in" on the Google home page: www.Google.com. Next, scroll down to the bottom of the page and click on "create an account now. Fill it out. It will send you an email to verify your account. You'll need to open your email to confirm.

Mike Callahan from Butterscotch describes how to manage the passwords on your iPhone by using the 1Password app. The application costs $5.99 for the Pro version. First, you enter an Unlock Code to give you access to the app. The icons across the bottom of the screen correspond to different features of the app. The Logins icon stores your login information. The Wallet icon stores information about your credit and bank cards. The Passwords icon holds all your passwords. The Add icon allows you ...

Tom of Videomaker teaches how to use the green screen to make a character appear in front of a set or to achieve the website spokesperson effect. Install a green screen in such a way that the fold at the corner of the wall and the ground is instead curved in order to create an even transition from the top to the bottom of the green screen. Build the base at the bottom part of the screen by weighing down the fabric at the corners and stretch it evenly. Light the green screen separately from th...

Want to forget about always pulling out your credit card to purchase something on your BlackBerry? There's a little application that can do it all for you? But how? Best Buy has answers. The Best Buy Mobile team explains how to use the BlackBerry Wallet application. This application can store personal information such as credit card information and shipping addresses on a secure website for easy access when shopping online.

This article is all about creating content. This is a very important concept to grasp because the content that you create for a website is going to be the basis for how you will advertise and promote that website. Content, meaning articles, videos, and even podcasts is now really the new advertising. Instead of traditional types of advertising and instead of the traditional separation between editorial content and advertising, that has gone the way of the dinosaur.

Here's a nasty little Null Byte. An open redirect vulnerability was found in both Facebook and Google that could allow hackers to steal user credentials via phishing. This also potentially allows redirects to malicious sites that exploit other vulnerabilities in your OS or browser. This could even get your computer flooded with spam, and these holes have been known about for over a month.

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

Sometimes an iDevice is best used for idle, pointless fun. Today's segment of Making Art on Your iOS Deviceis a mixed bag of time-wasting cool effects and random, but useful art-making tools. Below, 10 apps for creating anything from erratic hand-shaken digital effects to your very own DIY Andy Warhol prints.

Yesterday's installment of a Gamer's Guide to Video Game Software featured Unity 3D; today we'll be covering one of the oldest consumer game making engines, RPG Maker.

Internet culture loves many things, but there are two web crazes in particular that always grab my attention: the notoriously addictive facebook game, Farmville, and the insane art of cake decorating.

Here is a fun afternoon project that will add a little fare to your dogs wardrobe. Instead of buying your next dog collar, try making one out of an old belt. Some say dogs look like their owners and now they can dress like them too.

Watch this great cooking video on how to cook Indian shrimp biryana, which is a Goan rice dish. If you’re tired of the same old biryanis, try this Goan-inspired recipe for shrimp (prawn) biriani. With the creaminess of coconut milk and freshness of mint, it’s the perfect combination!

Ads aren't the only annoying part of navigating websites in Safari. Colorful banners, autoplaying videos, embedded objects, and other distracting elements can make it harder to read or watch what you want. Although ad blockers are one answer, they only get rid of advertisements, so you'll need something else to remove other irritating elements from your favorite websites.

There's nothing quite like getting lost in the TikTok void. While you'll likely never run into the same video twice, the same can't be said for popular sounds and fads. Some trends get so viral, it feels like you hear the same song or track every other TikTok. Just know this: you don't have to put up with any trend you're sick of.

The spatial computing world of Magic Leap is no longer limited to the rarefied tones of Sigur Rós and Sennheiser's Ambeo Augmented Audio app. Now, the entire music universe will be at your augmented reality fingertips.

All Kohl's wants for Christmas is Snapchat augmented reality. In conjunction with a holiday pop-up hosted in New York City from Nov. 7 through Nov. 10, Snapchat ran a sponsored portal lens available to targeted Snapchat users in the AR carousel. The experience gave users the ability to virtually transport themselves to the pop-up.

Facebook recently hit a snag in its quest to take augmented reality face effects to its millions of users.

The original iterations of the Terminator film franchise have served as the inspiration (via the heads-up display of the T-800) for future augmented reality dreams, so it is fitting that the current crop of AR gives the latest installment in the series a promotional boost.

Who's ready to let future Facebook augmented reality smartglasses read their brain? Well, ready or not, the tech giant is making progress in the area of brain control interfaces (BCI) by funding research.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.