
News: Cover Girl Opts for Browser AR Try-on Tool Instead of Mobile App & the Results Are Tragic
The latest cosmetics brand to launch its own augmented reality try-on tool is Cover Girl, which introduced its browser-based experience this week.


The latest cosmetics brand to launch its own augmented reality try-on tool is Cover Girl, which introduced its browser-based experience this week.
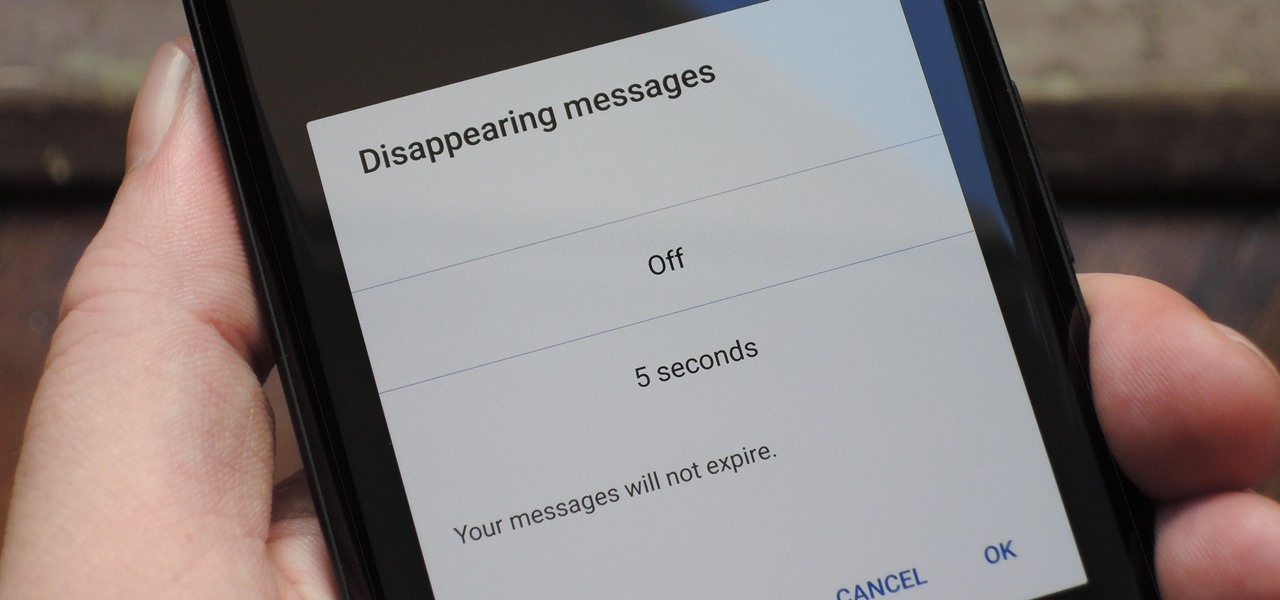
With Signal's class-leading end-to-end encryption, you can be sure your messages will remain secure as they travel to the recipient. However, once the message arrives, its privacy is completely dependent on the receiver, who could share it anywhere if they wanted. To patch this vulnerability, Signal added disappearing messaging.

OnePlus is on track to deliver Android 8.0 Oreo to its flagship users by Q1 2018. Open Beta 1 was released for the 5T in late December, and we just received Open Beta 2. But this update isn't just tweaks and bug fixes, OnePlus has included a few new features to enhance the Android experience.

It looks like there is a fatal flaw in the current macOS High Sierra 10.13.1, even straight from the login menu when you first start up the computer. This severe vulnerability lets hackers — or anyone with malicious intentions — do anything they want as root users as long as they have physical access to the computer.
Root, TWRP, Xposed, Magisk, custom ROMs — before you can have any of these, the first thing you should do is unlock your bootloader. Thankfully, the Pixel 2 and Pixel 2 XL are some of the most modder-friendly phones out there, so you only need to send a single fastboot command to unlock the bootloader.

Since the very first moment I saw the iPhone X track a human face and display the results in real-time on an Animoji character, I've been waiting for the first great hack of this new iPhone feature.

As if Amazon didn't already make it easier to buy things from home than in a store, the company has now given shoppers yet another reason to avoid the holiday rush with an ARKit update to its iPhone app.

If you're following the classic Halloween playbook closely, you've already got a costume or three picked out, you've binged-watched your favorite horror movies, and you've likely visited a haunted house. But it's 2017, so how about trying something new, like a haunted house that's not actually there?

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

While ARKit and ARCore are poised to bring AR experiences to millions of mobile devices, one company is poised to anchor those experiences anywhere in the world with just a set of geographic coordinates.

While Meta Company has agreed to a settlement in its lawsuit against a former employee and his company, they find the tables have now turned on them in the form of patent infringement allegations from another entity.

With the release of Apple's ARKit comes endless possibilities for education and learning. One of those possibilities is an AR rotating model of our solar system in your room, another is using AR to instantly know the nutritional value of food items.

A new dating app has arrived, and it'll finally land you a date with your celebrity crush ... kind of. The app — Dating AI — uses face search technology to help you search for potential love interests that resemble a celebrity you're attracted to.

There are a ton of new features in iOS 11, but some of the best ones, in my opinion, are in the Camera app. They're not huge features, but they're much appreciated to anyone who's ever taken a Live Photo or portrait, or even to those who've needed to scan a QR code quickly.

Toyota is testing blockchain and distributed ledger technology (BC/DL) for data sharing for driverless cars and other applications. This could eventually reassure buyers of its upcoming high-end cars by making sure their sensitive data is secure.

Put yourself in Google's shoes: You know that business is becoming increasingly mobile, but the mobile operating system you maintain is wide open by design, and it's garnered legions of loyal fans that love to explore and exploit every aspect of it. There's a clear conflict of interest developing.
Over the past week, we are seeing more companies capitalizing on services leveraging augmented reality. One company secured funding to expand their service, while two other companies grow its own services through acquisition.

Augmented and mixed reality developer Arvizio is working on a suite of software solutions for enterprises that will extend HoloLens capabilities as a full-fledged collaboration and conferencing tool. The company will demonstrate its Mixed Reality Studio suite to attendees at the Augmented World Expo, which begins later this month in Santa Clara, California.

Your friends are ditching Snapchat for Instagram. After the social network turned camera company announced it lost $13.30 per user in its first quarter as a publicly traded company, well, it doesn't look too good for the platform's future, y'all.

The Gorillaz have launched a new app in promotion for their new album Humanz that allows you to "[s]tep inside the hallowed halls of the Gorillaz house" through the power of augmented reality.

The "Discover" tab in the latest version of the Google Home app has a new tip that says multiple users are now supported. Google Home uses a built-in speaker and microphone combo to give users access to smart search, a personal assistant, and smart home controls. This addition has the potential to make the voice-activated speaker powered by the Google Assistant much more efficient for households with more than one user. However, it seems that Google wasn't quite ready to announce this new fea...
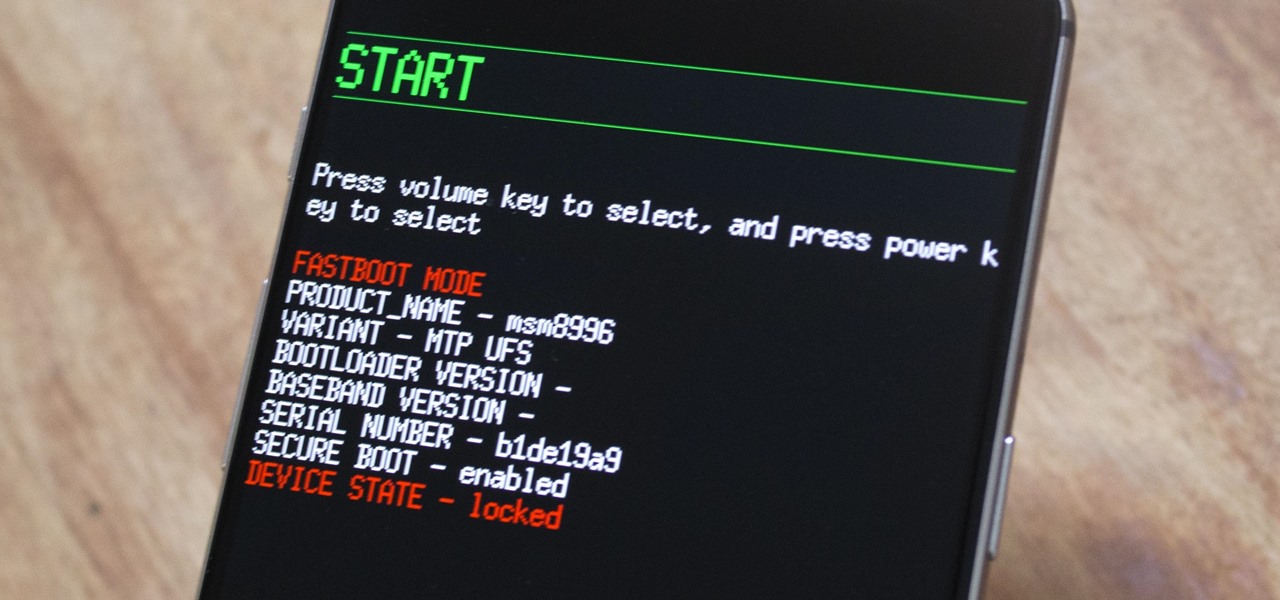
The OnePlus 3 and 3T are two of the most modder-friendly devices to be released in 2016. Not only that, but they're both extremely solid phones which happen to sport a very reasonable price tag. Among the things that make these devices such a joy for tinkerers is the fact that they have an unlockable bootloader, receive timely kernel source releases, and are actually quite easy to root.

Within the coming months, software startup Neurable plans to introduce the next paradigm in virtual and augmented reality: the brain–computer interface (BCI).

The modern age of techno-dating has made an interesting landscape for social interactions when there is some modicum of romance (or lust). For those of us born before the internet evolved into the prolific monster it has become, we first met our love interests face to face. Today, however, apps like Tinder have changed the introductory stage, for better or worse.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

Students from Carnegie Mellon University's Entertainment Technology Center have been working on an augmented reality system to help teach music in a project called Music Everywhere.

Intel, the company which is mostly known for creating computer processors, once again showed off their Project Alloy "merged reality" experience, this time during their CES 2017 press conference. Intel's Chief Executive Officer, Brian Krzanich, stated that they will be "productizing" this tech with their partners in the fourth quarter of 2017.
Starting in October, many Nexus 6P users have been experiencing a bug that causes their phone to completely shut down, even though there was 20% or more battery life remaining. At first, it was thought to be a direct result of the recent Android Nougat update, but a combination of factors indicate that this isn't necessarily the case—or, at least, it's not the only problem.
When a new version of iOS comes out, everybody gets caught up in the craze of finding features and playing around with new functionality. But this generally leads to a lack of coverage on the finer aspects of the update—things like bugs, minor tweaks, and pain points that users discover along the way.

Google's new cross-platform video chat app, Duo, is finally making its debut today, following a long waiting period that began in late May. The app was heavily teased during the keynote speech at Google I/O, but was not made available for download until now, so any early hype Google managed to whip up has died down quite a bit.

Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about.
This is a how to to change any user password on a windows 7 computer. If you forgot your password you can change any account password even if you are locked out of your account.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.

Many users across the web have reported issues with receiving notifications from the Gmail and Hangouts apps on Android. The problem is most prevalent with users running Marshmallow, and the gist is that notifications from these apps are extremely delayed or don't come through at all.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

Welcome back! In the last iteration of how to train your python, we covered loops, today we'll be covering something that I wish I had learned about much earlier in my scripting career, errors. We all run into them, and they can be frustrating, but there is also a silver lining to them. Today, we'll be discussing why some errors are unavoidable, and what we can do when we run into them. Also, this article will be more of a concept and less of writing actual code, but the information is equall...

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.
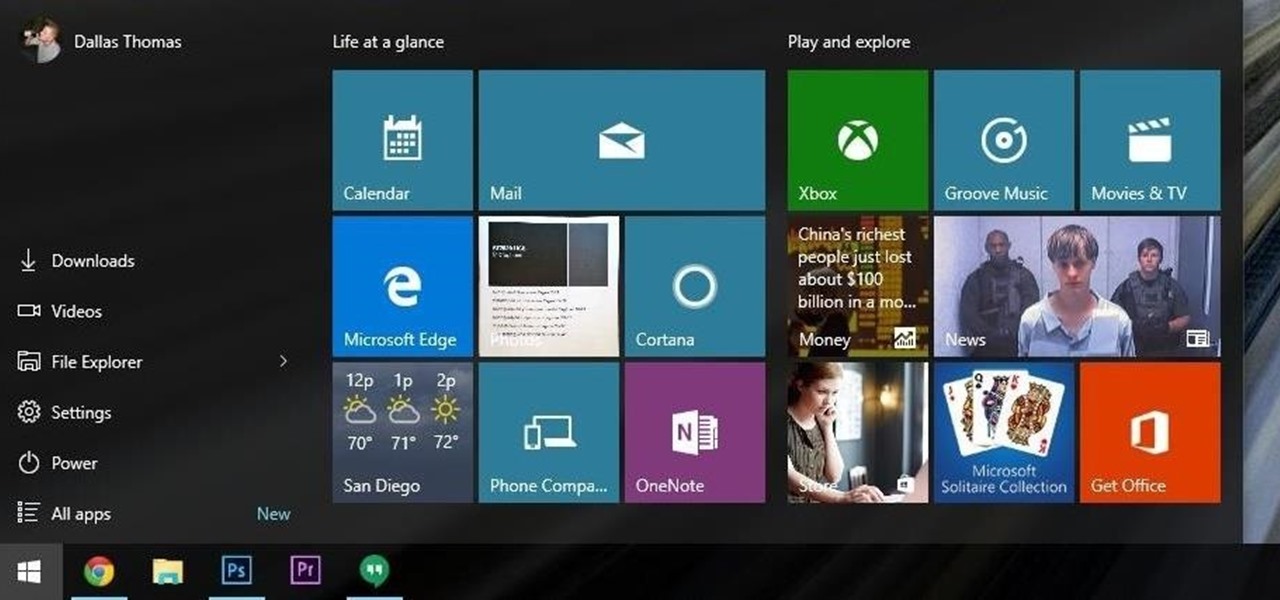
The desktop Start menu is finally back! After receiving a lot of negative user feedback, Microsoft ditched the touchscreen-first approach of Windows 8 and went with a more traditional setup for mouse-and-keyboard users in Windows 10.