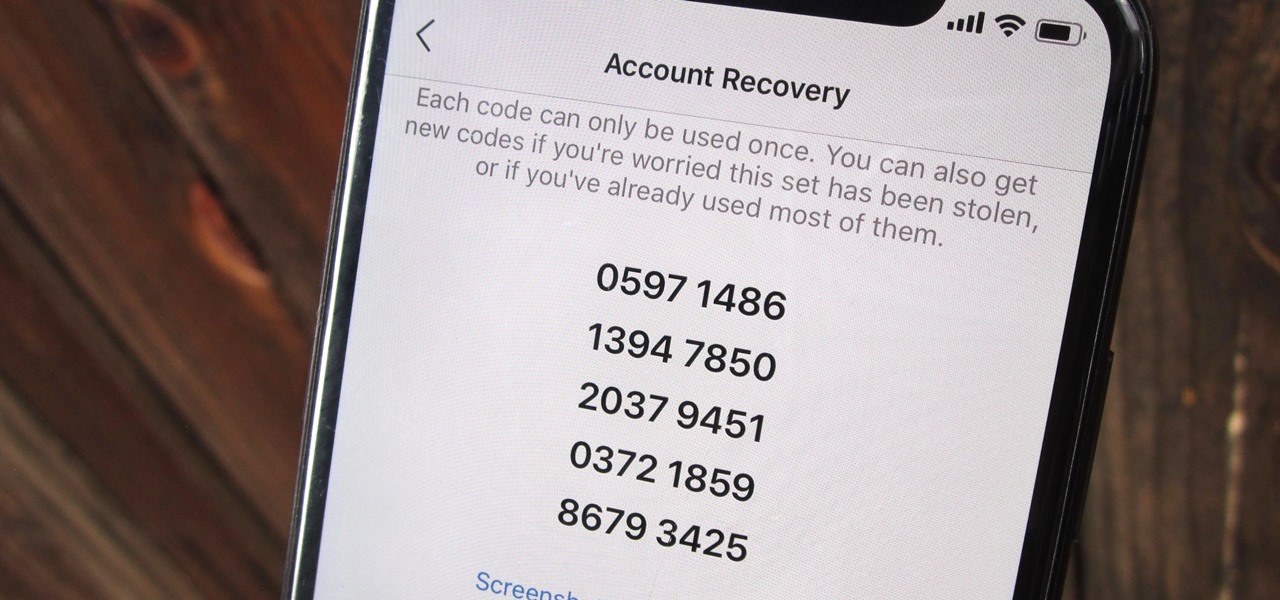
Apple seeded public testers the second beta for iOS 13.3 eight days ago. That update mainly added stability patches to iOS as a whole, as did the public releases of iOS 13.2.2 and iOS 13.2.3. Now, following the release of iOS 13.3 developer beta 3 earlier today, Apple seeded the same beta to public testers.
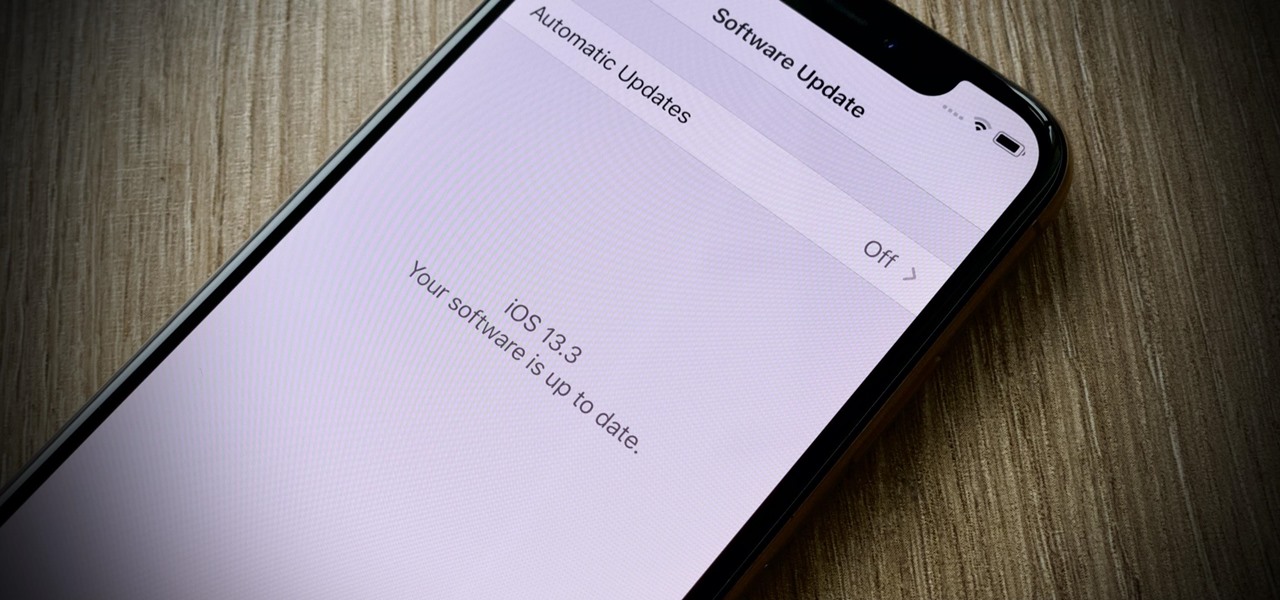
Just two days ago, on Nov. 18, Apple released iOS 13.2.3 to the general public, which included stability updates for bugs affecting iOS 13.2 and earlier. Today's update isn't for the general public, however. Instead, Apple just pushed out iOS 13.3 developer beta 3 for software testers.

Apple is often unpredictable when it comes to beta releases, especially with public betas. Developers receive their updates first, then public testers have to wait and see if Apple will do the same for us. Sometimes, the iPhone OEM makes us wait until the following day, but not with iOS 13.3 public beta 2. This update is now available to download and install.
We're finally back in the swing of things. For the first 26 days after the release of iOS 13.2, which introduced 22 new features and changes to the iOS 13 era, there wasn't a new beta. Then, Apple released iOS 13.3 developer beta 1, and now we seem to be back on schedule, as Apple just released 13.3 beta 2 to developers.

Is the augmented reality magic fading down in Plantation, Florida? That's the first question some may be asking following a casual revelation over the weekend that Magic Leap, the maker of the Magic Leap One, has assigned much of its patent portfolio over to JP Morgan Chase as collateral.

One of the best ways to dig into a website and look for vulnerabilities is by using a proxy. By routing traffic through a proxy like Burp Suite, you can discover hidden flaws quickly, but sometimes it's a pain to turn it on and off manually. Luckily, there is a browser add-on called FoxyProxy that automates this process with a single click of a button.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

Two-factor authentication (also known as 2FA) adds a necessary additional layer of security to your username and password in many important apps. On Instagram, 2FA requires you to confirm it's you attempting to log in, with a special code sent to you via text message. Enter the code and you're in ... but what happens when you need to log in and don't have access to your phone?

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

You just brought a brand new Pixel 3 from the Google Store, and you insert your SIM card only to find the phone won't recognize it at all. No matter what you do, the SIM card won't register and your Pixel won't connect to your carrier network. That's what happened to me and several other Pixel 3 owners. The good news is a fix is coming, the bad news is Google doesn't have a date for that fix.

After getting confirmation from Tim Sweeney, CEO of Epic Games, we now know Fortnite Battle Royale will not be available on the Play Store when it's finally released for Android. Instead, users will have to download the APK directly from Epic Games' website — and quite frankly, this is a bad idea.

Its official: On May 8, T-Mobile finally released the Android Oreo update for the LG V30 and V30+. Now, every major US wireless carrier has pushed the update. For me, this update is a big deal. Not only does Android Oreo bring some new tools and features, but LG has also included a few additions as well.

Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.

Before you go ahead and delete your Facebook — don't lie, you've been thinking about it — consider this. Facebook offers users a wide variety of privacy options to mess with, which can help you find a little control over your information. We're not saying this solves Facebook's privacy crisis, but it might be a more reasonable option than throwing in the towel entirely.

Accused of violating whistleblower and age discrimination laws by its security director, Magic Leap has taken an internal situation to the US District Court to clear its name of the allegations.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

The first big update to iOS 11 since its release in mid-September just came out, so check your iPhone for a software update to iOS 11.1, because there are a few things you'll want from it. While there's no sight of Apple Pay Cash or Messages in iCloud, there are some significant improvements you'll need to know about.

Taking a cue form Snapchat, WhatsApp Status lets you share updates that come in the form of GIFs, photos, videos and good old text. This awesome feature is available for both iPhone and Android users, and it even lets you choose which contacts to share with while disappearing after 24 hours.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Our smartphones are full of personally-identifiable information. So much of what we do with these devices is tracked and recorded to make our experience more streamlined and personalized. For many users, that's a fair trade — but for privacy-minded folks, it's a raw deal.

A groundbreaking new Android feature called seamless updates was announced at Google I/O 2016. No longer would we have to wait for updates to download and install — instead, they'd be applied silently in the background, and the new Android version would be waiting on us the next time we restarted our phones.

There have been a number of rumors about the iPhone 8 over the past couple of months, but the latest speculation about the device's dual FaceTime camera, that could take 3D selfies, has definitely grabbed our attention.

Hackers are good at what they do—some can even use the way you move your phone to guess a 4-digit PIN in five attempts or less. That's why most of us with compatible hones use the fingerprint scanner. It's just much more secure. Or is it?

If you were a particularly good little girl or boy this year, Santa might have finally brought you that cool new smartphone you've been wanting. Or perhaps you just took advantage of a great sale and treated yourself to a new gadget this holiday season—totally justifiable, and surely a well-deserved gift.

The beauty of Nexus devices is they receive firmware updates faster than any other Android phone, and keep getting updates for years longer than most of the competition. This means that you can always use the great new features that come along with an Android update, and even more importantly, your phone gets monthly security patches to keep hackers and malware at bay.

Starting with version 6.0 Marshmallow, Android now supports fingerprint scanners natively. This change has effectively opened the floodgates, and now almost every flagship Android device includes a fingerprint scanner out of the box.

Google Maps, in conjunction with the Android operating system, is a powerful tool for navigation that is often underutilized. While it's no secret that it can get you to wherever you're going and back, some of you might not know that you can use Google Maps without even having to touch the screen. Not having to touch your display means you can concentrate on other things, you know, like driving or eating that jelly-filled donut.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.

Keyboard shortcuts can make using your Mac faster and easier, and leave your mouse feeling archaic. With just a few taps, you can save files, open new tabs, or play a movie—all without using your mouse even once.

Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock:

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.

Welcome back, my hacker novitiates!

The Galaxy S6 Edge comes with a useful feature called Information stream that allows you to view quick tidbits of info with a quick back-and-forth swipe on the edge of your display while the screen is off. Apparently, Samsung left the door open for third-party plugins to use this feature, and now we're starting to see an influx of useful additions.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Aside from being able to change the wallpaper and add shortcuts, the Galaxy S4's lock screen doesn't offer much in the department of personalization. The lock screen is efficient and practical, but it's also a little bland.

I don't know of a pain greater than of the one felt after cracking the screen of your phone. After I managed to crack my screen, rendered unusable, I immediately began to panic as to how I was going to recover all of the photos, videos, and documents stored on my device. After a few hours of searching, I came upon a thread by Mohamad Sabra that showed exactly how to alleviate my problem.

It started in Australia, and now seems to have made its way statewide—hackers are remotely locking iOS and Mac devices, holding them for a $100 ransom. Users awoke to the loud "lost iPhone" ringtone, with a message on their lock screen stating that "Oleg Pliss" has hacked their device, and that "they" will unlock it after being sent $100 through PayPal.