If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

My friends can be pretty shitty sometimes, but they're my friends nonetheless. On various occasions, they've secretly taken my device and made me look foolish by posting crude and embarrassing posts to Facebook, Instagram, or Twitter. With friends like these, who needs enemies, right? And it's because of these types of friends that we need to substantially upgrade the app security on our devices.

Whether it's because you have nosy family and friends or you're just cautious about losing your device, having a passcode on your Android smartphone is essential for protection. However, you don't always need or want a passcode, especially when you're home alone or in your car on the way to work.

If you've been using Google's hidden App Ops to lock down and prevent some of your Android applications from exposing your privacy, then think twice before updating to the new Android 4.4.2 software.

There are a gazillion lock screen apps available on Google Play, but the majority of them are subpar and not worth your time. However, in my opinion, there is definitely one out there worth your time—one that constantly learns and adapts to what apps you use when and where to determine which shortcuts to give you.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

A few weeks ago, Bluebox Security uncovered a bug that could potentially effect 99% of Android devices. Bug 8219321, dubbed the Master Key bug, works by allowing applications with modified code to pass Android's signature verification system, thereby bypassing security measures that normally wouldn't allow these apps to be installed.

Mac OS X has convinced many traditional PC users to switch platforms. While Windows 7 may do something to stem that tide, a lot of you PC users reading this have probably thought about switching right? If you have, watch this video. It will give you a PC-user centric rundown of OS X and allow you to make a more informed decision about what operating system is best for you.

In this Flash and ActionScript video we will learn how to change the user's mouse cursor to a piece of artwork we made and then make it explode when a users clicks on a certain area of the stage. Also, see some helpful tips on basic Dynamic text. The exploding cursor is a great way to start learning ActionScript and Flash 8.

Kip "Kipkay" Kedersha is known for his intriguing and clever how-to and prank videos, even when he teams up with MAKE Magazine. He will show you how to tweak, hack, mod, and bend any technology to your hacking needs. No electronic device, gadget, or household item can stand the test of Kipkay's hacks and mods.

If everyone in the world properly secured their email account there would be no spam. But yeah… never going to happen. That's more of a reason to encrypt and digitally sign our emails, but isn't using p2p security really expensive and really hard? Nope. It's actually free and easy with GnuPG. It's demonstrated on Mac OS X, but it's just as easy with Windows.

In this video tutorial, viewers learn how to protect their privacy online. Some information that is exposed every time you visit a website are your I.P. address, operating system and browser. To view what information that you are revealing to a website, visit the site provided in the video. This site will give you all the information that you are exposing in a website. This video will benefit those viewers who visit a lot of websites, and would like to learn how to view the their exposed info...

Don't fret too much if your watermark is barely noticeable when you're finished with this project - the less obvious it is, the better a job you've done. Watermarkers are present in many types of paper, especially the monetary kind. If you hold up a ten dollar bill you'll see a watermark of Thomas Jefferson's face on the right, proving the bill is real.

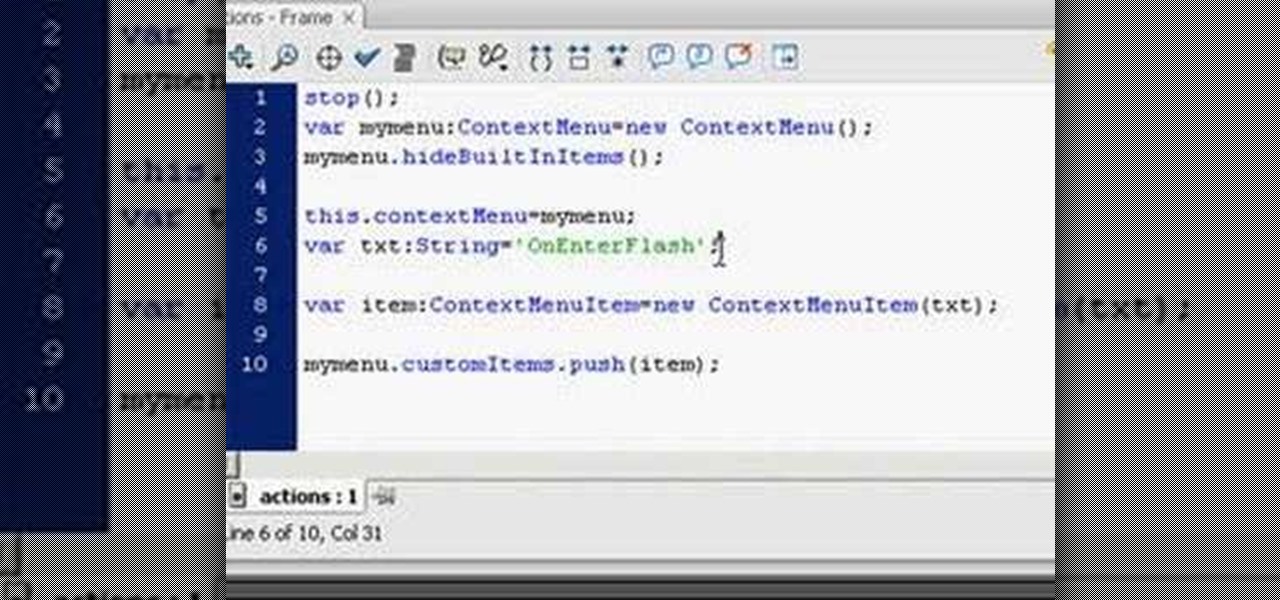
Web users are for the large part nosy, spoiler-loving folks who refuse to let websites and other users keep secrets from them. Thwart these trolls! This video will teach you how to use Actionscript 3 to hide the context menu from your site's users, preventing them from skipping to further parts of your slideshow or game and ruining the continuity of your work. You will also learn how to create a link that will show up in user's context menus when they right-click on objects. These two tools w...

Use Microsoft Windows 7? Miss the old Ctrl-Alt-Delete log-in prompt? It's easy to restore. So easy, in fact, that this home computing how-to from the folks at CNET TV can present a complete overview of the restoration process in just over a minute's time. For more information, and to get started restoring this useful security feature on your own Windows 7 PC, watch this free video tutorial.

If you move around a lot, you may notice that you can't play the same DVDs from country to country. The world is separated into different regions, and not all movies will play in all places. There are ways around this security measure, however, if you follow this tutorial.

The PhotoshopUniverse team effectively teaches a method of adding a watermark to an image, as a security feature to make it harder to copy or steal. Instructions are simple and easy to follow, using as an example a photo of two girls that one might have in his or her family album. Using Photoshop, the text that will become the watermark is added, rotated and patterned across the entire image. To finalize the watermark, the opacity is edited to a desired value so that it does not interfere wit...

This video shows you how to make a security device out of a door bell. The concept is that most thefts happen when people are away from home. To make sure of this the thief rings the door bell to make sure that nobody is home, if nobody answers then they will break in. A lot of people have dogs and alarm systems which will scare off the thieves, but this alarm system combines both. To make this devise you have to buy a speaker system that connects to your door bell. When the door bell rings i...

Check out this RESIDENT EVIL 5 Chapter 2: Gigante walkthrough from Machinima.com The behemoth from RE4 returns with some new tricks up his sleeve.

There are two ways to properly lock your seat belt. You can use the childlock auto adhjustment. Or you can recline the seat, but then push forward to make your seat belt very tight. You don't want to be flopping around in the car. The bottom of your wrist is on top of the steering wheel and your shoulder is in the seat. It will loosen up when you get on the track.

Check out this Mahalo video walkthrough of Savannah in Resident Evil 5. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

This video will show you how to fake a RAM, Flash, or entire memory clear. Lots of teachers and test administrators go around and clear your calculator so students don't cheat. This is any easy way to subvert the teacher's security measure. This is a good thing to know if you want to cheat on your GED, SAT or ACT test / exam.

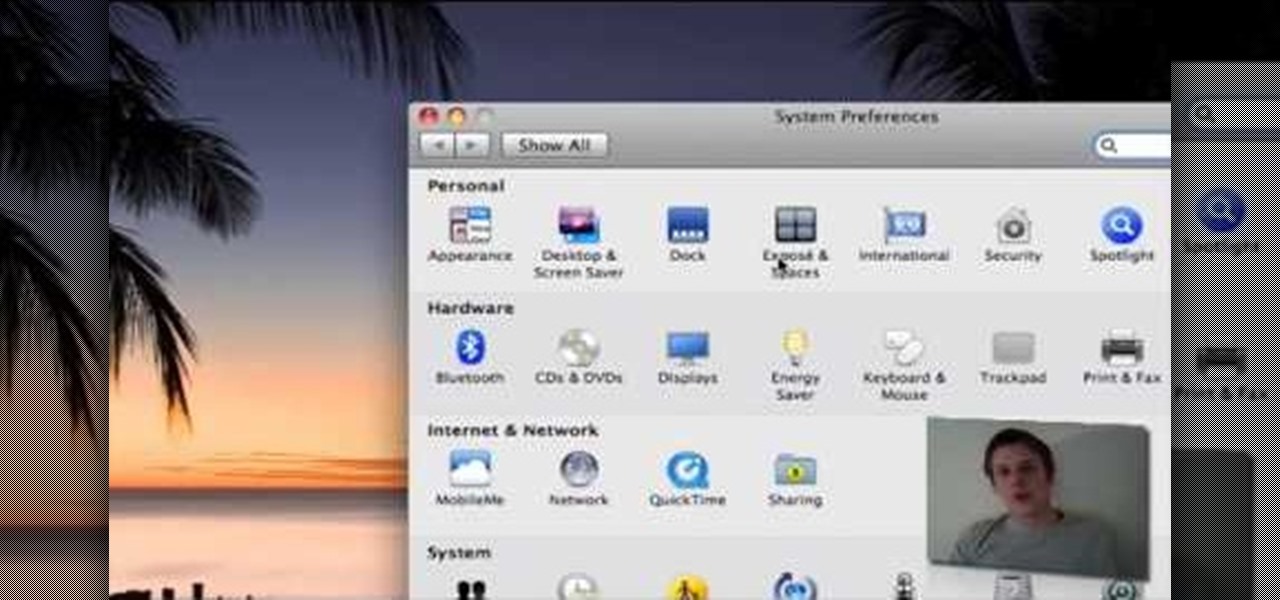
You can create a multiple user accounts and enable fast user switching. To do this go to system preferences and open accounts. Now authenticate yourself by clicking the lock icon to be able to make changes. Now click + button

This video tutorial belongs to the software category which is going to show you how to convert a Word document to a password protected PDF file with NovaPDF. Go to NovaPDF and download the program and install it. It is a paid program. Select the word document that you want to convert and select print option. Under the name of the printer you will find novaPDF option. Select this and click 'preferences'. Now click on 'security' and select high level encryption. In the document permissions, sel...

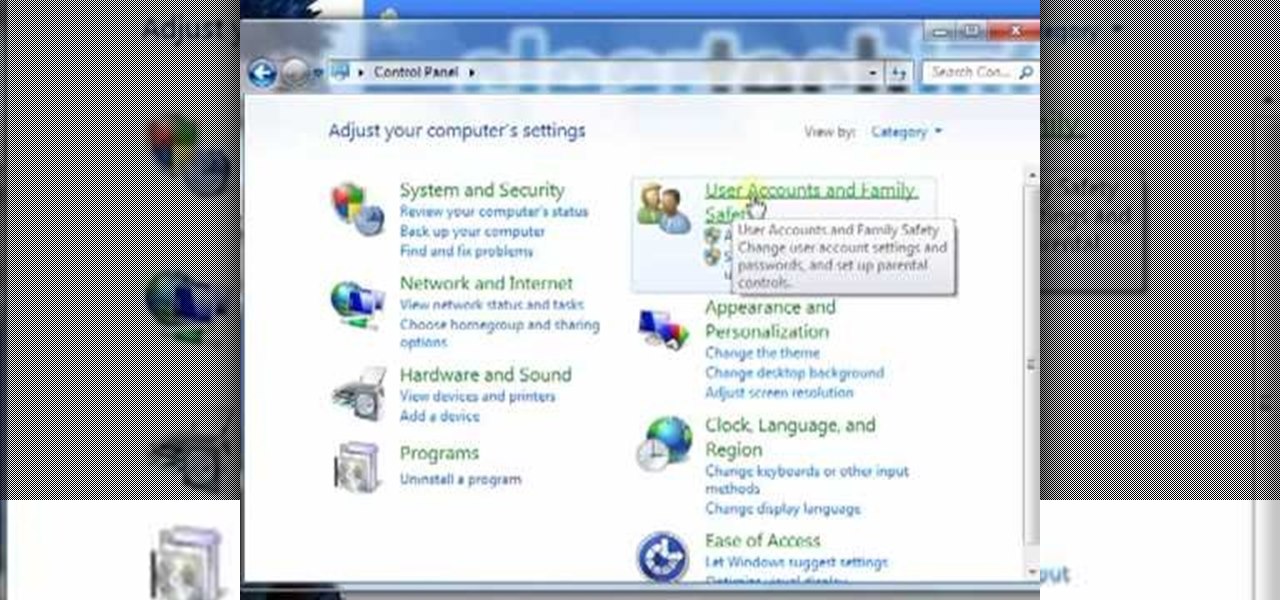
In this video tutorial, viewers learn how to create a new standard user and administrator account. Begin by clicking on the Start menu and select Control Panel. Then click on User Accounts and Family Safety and click on User Accounts. Now select the "Manage another account" option and click on "Create a new account". Users are able to name the account and select the account type (Standard or Administrator). Finish by clicking on Create Account. Users are then able to make changes to the accou...

This video contains instructions about how to disable or enable the user accounts on Windows Vista. It is very simple; just go to control panel -> user accounts and safety -> user accounts. You can click the check box on or off to disable or enable the user accounts. This can also be done by using command line. Open run and type the following command:

In this video tutorial, Chris Pels will demonstrate how to create a custom user control in ASP.NET that can be used throughout a web site or across many web sites. Start out by learning the basics of creating a user control that will be used in multiple pages including validation, controlling formatting using style elements, and loading/saving data for the user interface elements. Throughout the video considerations for building user controls that can be easily maintained and used across mult...

How to program a user registration using php, sql and phpmyadmin. Part 1 of 3 - How to Program a user registration with PHP.

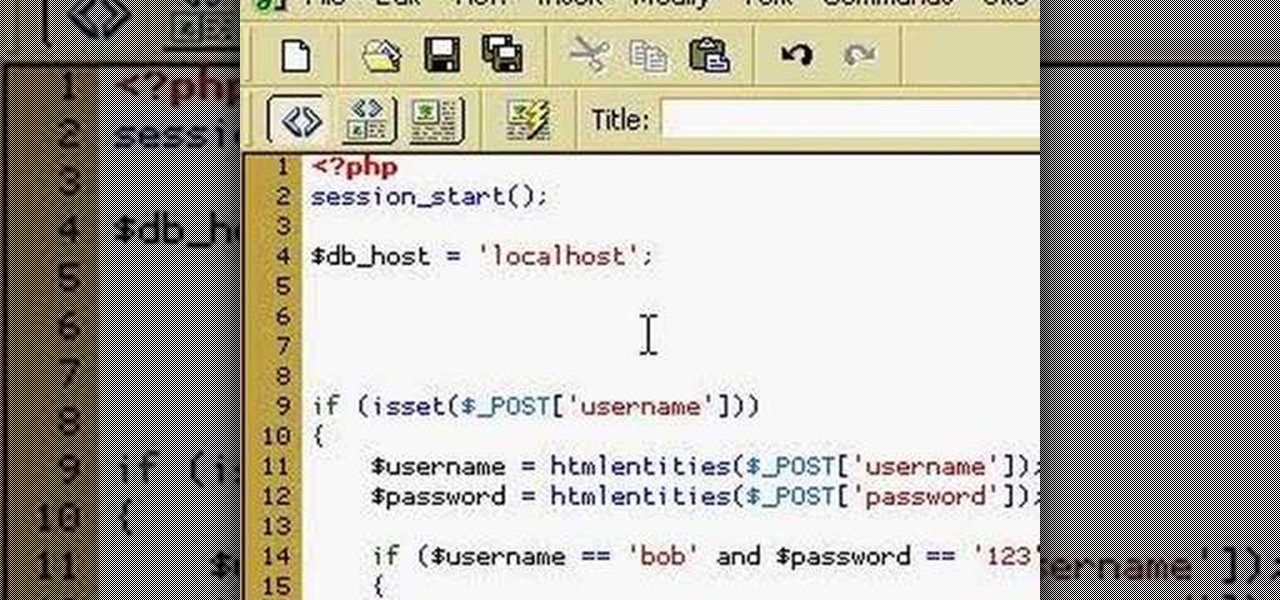
How to manage user logins by creating a MySQL user login database with PHP. Part 1 of 3 - How to Create a MySQL user login database with PHP.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

Despite Samsung's long running support for Wi-Fi Direct, most users still struggle to transfer files between their devices. Whereas Apple has AirDrop, Samsung's previous solution wasn't so obvious. With the Galaxy S20 and Galaxy Z Flip, Samsung hopes to correct this with "Quick Share," a file transfer system that still uses Wi-Fi Direct but makes it easier to use.

When Facebook launched its first hardware products last year, the Portal and Portal+ smart displays, the company mostly touted its video-calling features as it faced off against Amazon and its Echo Show.

Apple has seemingly always made it a priority to show how much it cares about user security and privacy — enough that it has a page dedicated to it, proclaiming that "privacy is a fundamental human right." It's true that there are few issues more important than user privacy when it comes to technology, and Apple only makes things better in iOS 13.

As Microsoft continues to bask in the glow of its HoloLens 2 unveiling and begins ramping up the hype to launch, Nreal and Vuzix are carving out their own niches in the AR hardware landscape.

It looks like it's cuffing season for AR hardware makers and telecommunications corporations. With AT&T aligned with Magic Leap as its exclusive wireless retailer on the high-end AR side, Verizon has also reached a master reseller agreement with Vuzix, according to a filing with the Securities Exchange Commission.

Public software testers can now run the fourth iOS 12.1.3 beta. Apple seeded this update to testers on Thursday, Jan. 10. Just like with beta 3, public beta 4 includes two resolved issues — a VoiceOver fix for ECG and Irregular Heart Rate notifications, as well as audio improvements for iPad Pros.

Users are often the weakest link when probing for vulnerabilities, and it's no surprise they can be easily fooled. One way to do this is called clickjacking. This type of attack tricks the victim into clicking something they didn't mean to click, something under the attacker's control. Burp Suite contains a useful tool called Clickbandit to generate a clickjacking attack automatically.

Apple released iOS 12.1.3 public beta 2 for iPhones on Wednesday, Dec. 19. Yes, that's confusing, since there was no first beta for iOS 12.1.3, but it indicates that it's the actual successor to iOS 12.1.2 public beta 1. Apple dropped iOS 12.1.2 unexpectedly to fix major issues but did not include everything in the beta, so we're picking up right where we left off.