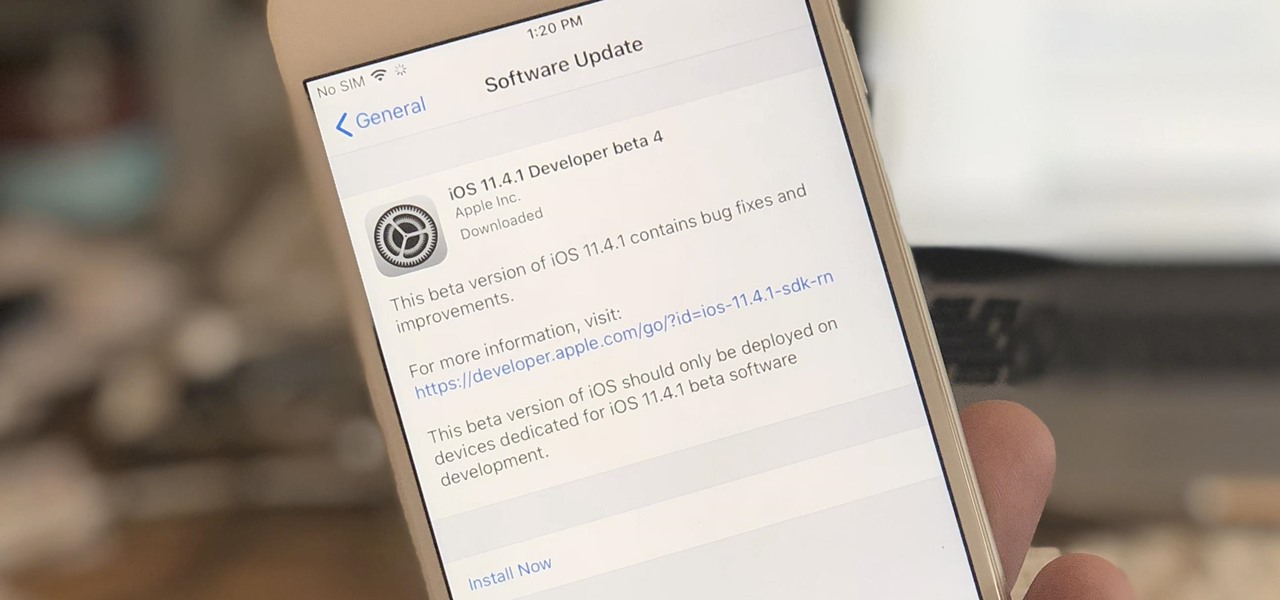
Check your Settings, software testers — Apple released the fifth iOS 12.1 beta on Monday, Oct. 22, just seven days after seeding the fourth beta to both developers and public testers alike. While this initial update is only for developers, we expect Apple to subsequently release the public beta within hours of this post.

Just six days after the release of dev beta 3, developers now have their hands on the fourth iOS 12.1 beta. While Apple has recently followed a lengthy and inconsistent release schedule with its beta software, the company seems to want to keep testers happy with 12.1 — beta 4 might have come less than the standard seven days after beta 3, but at least it's here quickly.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.
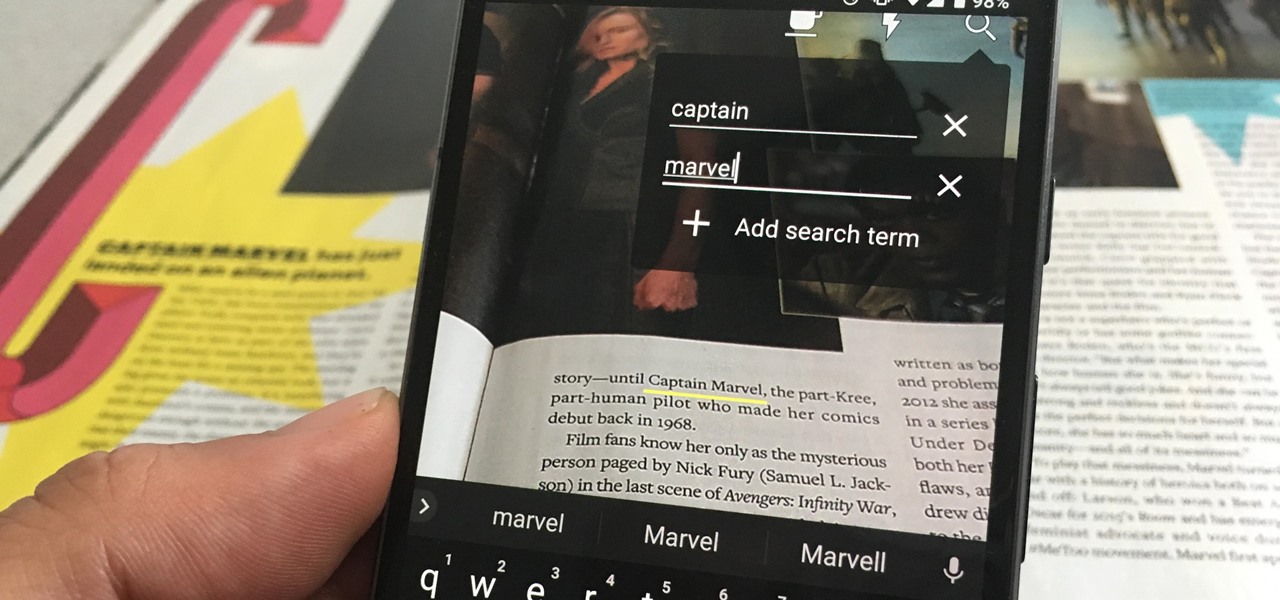
One of the neatest tricks available in Google Lens, an app that can identify and interpret real world information, is the ability to copy text from the app's camera view and paste it into a digital document.

RIP Touch ID. Apple's fingerprint sensor on iPhone and iPad models with Home buttons is about to become phased out on Wednesday, Sept. 12. While Touch ID will remain an integral part of models from the iPhone 5S to the iPhone 8 Plus, as well as the iPad Air 2 through the sixth generation iPad, Face ID will completely take over as the default security method for unlocking future iOS devices.
Apple released the eleventh developer beta for iOS 12 to registered software testers on Monday, Aug. 27, only four days after the company unexpectedly released both dev beta 10 and public beta 8. Apple has ramped up its beta release schedule as of late, offering minor updates twice a week in the lead-up to iOS 12's official debut in a few weeks.

On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.

Apple's on a roll with once-every-week releases for the iOS 11.4.1 beta. Exactly seven days after beta 3 came out, beta 4 has been pushed out to developers and public beta testers on Monday, June 25. Just like before, there are no new features or any known enhancements or bug fixes. Apple confirmed that iOS 11.4.1 is for under-the-hood improvements only, since iOS 12 beta is already out.

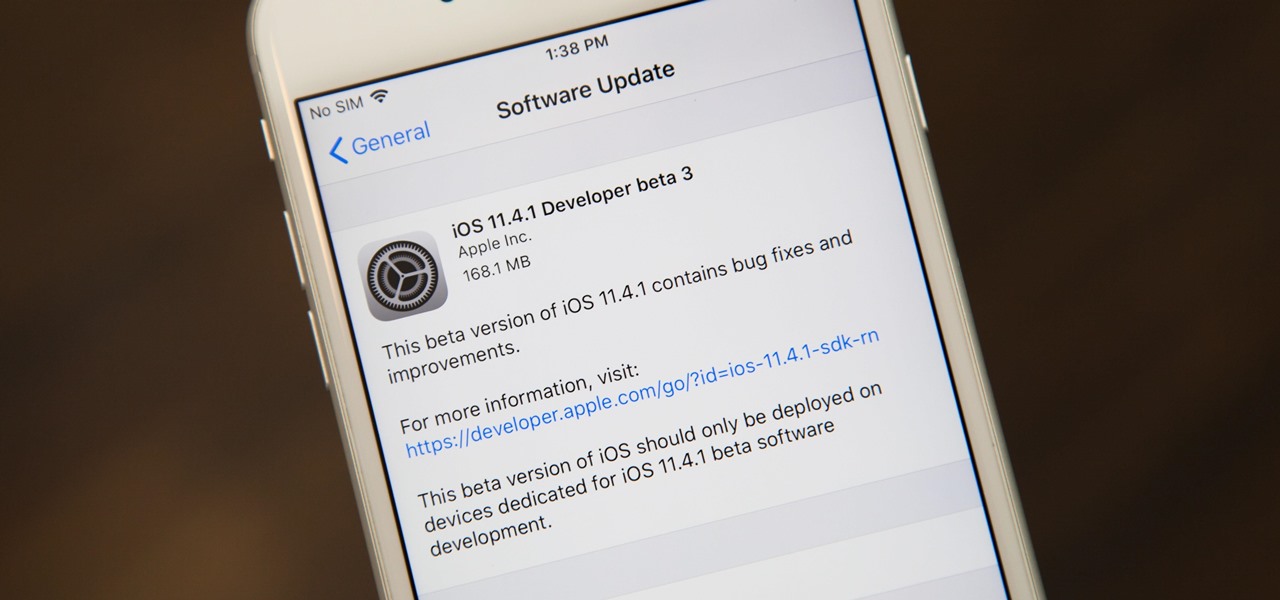
Another beta for iOS 11.4.1 was released on Monday, June 18, exactly one week after iOS 11.4.1 beta 2 was pushed out. Like the second beta, iOS 11.4.1 beta 3 has no new features or any known enhancements or bug fixes. It's likely Apple is simply using iOS 11.4.1 to add under-the-hood improvements only, since iOS 12 beta is already out.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

One of the best-received features of the OnePlus 5T was the relatively secure face unlock, which made it quick and easy to get into the phone. Unfortunately, this feature wasn't included with the slightly older OnePlus 5 at first, but now, face unlocking is finally out of beta and available to everyone with a 2017 OnePlus.

In January, ZTE announced they would be conducting an Oreo beta program for Axon 7 users to test Android 8.0 before the masses. Since then, no additional information was released — until today, when ZTE finally opened up the Oreo beta to US customers.

Back in November, Essential opened the Android Oreo Beta Program for all users of their PH-1 flagship. We even wrote up a full guide on how to install the beta, if you're interested. They followed the Oreo beta with a Reddit AMA, where they mentioned the second beta software would arrive very soon. That update has just gone live, so you can grab it right now in a few easy steps.

Bitcoin Cash (BCH) has officially arrived on Coinbase, which means you can now easily buy, sell, send, and receive the digital currency without having to manually set up a wallet or trade on an exchange like Poloniex. This addition has boosted the price of BCH, which is currently trading at around $3,400 a coin.

Mozilla's Firefox has always been a highly praised internet browser. Since it's open-source, users know what they're getting without any secrecy. It's got plenty of features that are unmatched by any of its competitors on mobile. However, speed and performance have always been a pain point for Firefox, but Mozilla went back to the drawing board to solve this problem with the release of Firefox Quantum.

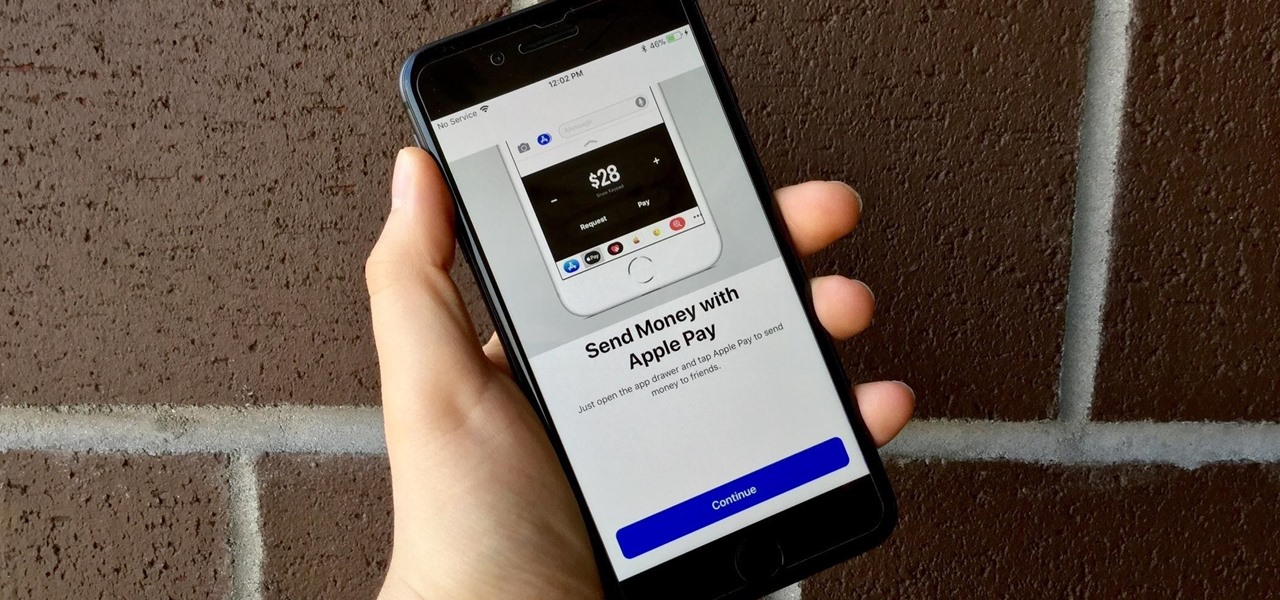
Move over Venmo, Apple Pay Cash is here, and it's built right into iMessage. If you're like us, you've been eagerly waiting to give this new feature a try on your iPhone ever since Apple announced it during WWDC 2017 back in June. While it was never released in the main iOS 11 update, it finally showed up in iOS 11.2.

For Apple Pay users, the iPhone X, XS, XS Max, or XR will be an adjustment. Gone are the days where you could rest your finger on the Home button and hold your device within range of a contactless reader. Without Touch ID on the iPhone X, this isn't possible. But have no fear, Face ID is here.

The Galaxy S8's Always On Display is a fantastic feature that gives you a brief overview without having to wake up your phone. But AOD now has a virtual home button, which kinda ruins the sleek look and can even cause screen burn-in.

Signal, the encrypted messaging app, has seen 1.4 million downloads in just the first quarter of 2017—roughly twice the downloads it received in the same period last year. Rani Molla at Recode attributes this to Donald Trump's inauguration, as the private messaging service saw a 40% increase in US downloads between Election Day and the end of the first quarter of 2017.

TrueCaller is sharing your phone activity by revealing the last time your phone was used to contacts. The application used to identify unknown callers launched in 2009 and has faced a wealth of privacy concerns before.

We've seen plenty of good, bad, and weird things that have come out of the worldwide augmented reality game Pokémon GO, including murder and location-based bans, but nothing on a large scale. That was, of course, until Iran decided to ban the game country-wide.

If you want to make some money from catching bugs and are sick of pentesting Facebook, Google, and Microsoft's products, Uber may be your new favorite playground.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

It sounded great on the surface when Microsoft announced that existing Windows 7 or 8 users would be able to upgrade to Windows 10 for free, but the execution so far has left a lot to be desired. Upgrading from an existing installation is relatively easy, but when you start with a clean install of Windows 10, you run into some problems.

You would think that with each major iOS update, there'd be fewer ways to bypass the lock screen. Unfortunately, Apple's developers have consistently failed every year since 2013 in this department, leaving open lock screen exploits for iOS 7, iOS 8, and now the latest iOS version, iOS 9, with each exploit being discovered within days of the OS release.

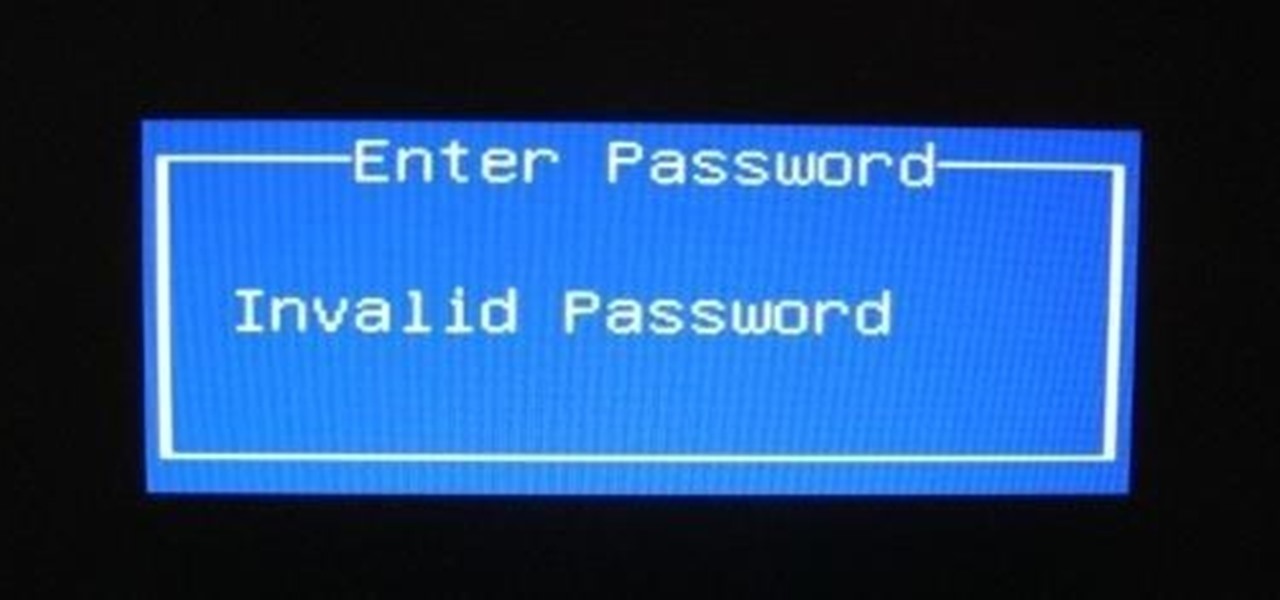
So i ran into a problem few days ago and it seemed to be very annoying one. I got hands on ASUS X55A with broken HDD. So i changed HDD and woo enter bios password. I hit enter and got into bios where uder security tab was shining ADMINISTRATOR PASSWORD INSTALLED. There was no user password but administrator password was set and it led to that i wasnt able to boot anything. At all.

Welcome back, my rookie hackers!

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Sitting at home alone on Friday night, I'm often in the mood to watch something more recent than the offerings on Netflix, Hulu, or Amazon Prime Video. And since the demise of video rental stores, that leaves me with browsing through the Redbox catalogue, then strolling down to the nearest 7-Eleven to pick up my movie.

With countless images and messages packed into one small device, security is always a high priority amongst iPhone users. For this reason, we've previously shown you how to make your iPhone's passcode match the current time, which made figuring out your passcode a lot more difficult for wandering eyes.

Apple has been one of the biggest trolls when it comes to adding new features to their software. Whether its adding a new boot screen and not letting all devices use it, or adding Dark Mode and making it a hassle to toggle on and off, there is always to be a caveat attached to each new addition.

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

Welcome back, my apprentice hackers! As many of you know, I have been hesitant to adopt the new Kali hacking system from Offensive Security. This hesitancy has been based upon a number of bugs in the original release back in March of 2013 and my belief that BackTrack was easier for the novice to work with.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Update: The installation process for Xposed Installer is now dead simple—check out our updated guide!