Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

For a photo- and video-sharing app based around privacy, Snapchat sure has a lot of security holes floating around. At one time, you were able to take screenshots of Snapchats in iOS 7 without the sender knowing, which is something that you can still do on rooted Android devices.

Sprint has announced that it will be the first U.S. carrier to release Jelly Bean 4.1 for the Samsung Galaxy S III. The over-the-air updates have already started, with users receiving a notification on how to update on their phone. The reason Jelly Bean has garnered so much attention is due to several, well-known features like Google Talk, Project Butter and expandable notifications.
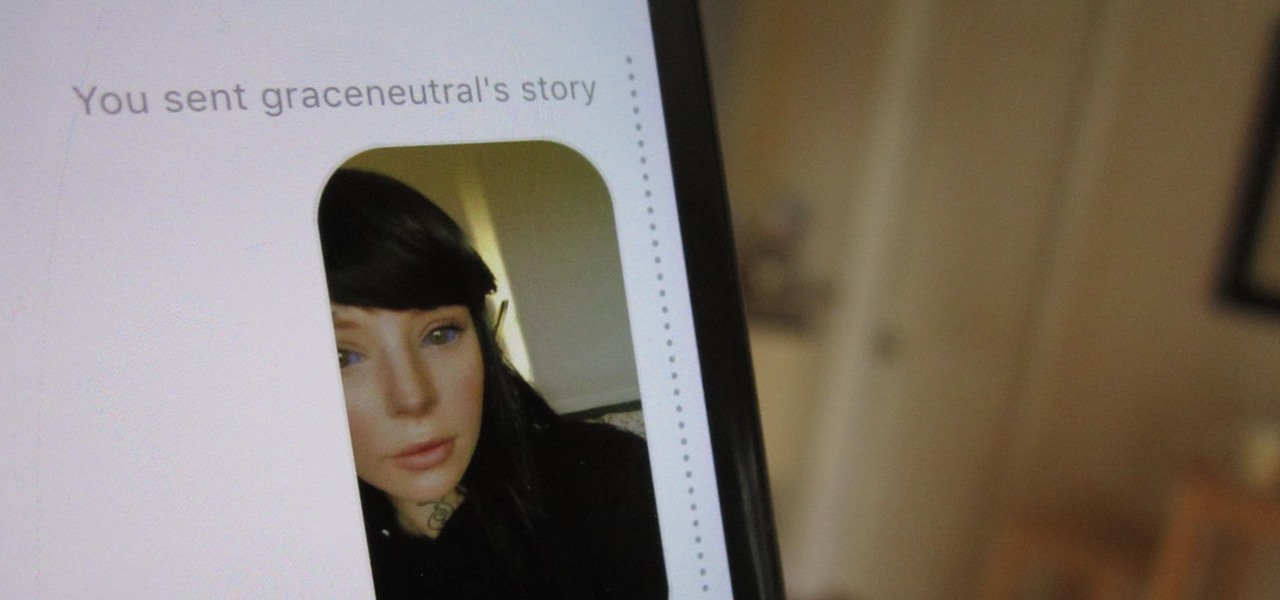
Instagram introduced a new feature in September 2018 that lets you share other users' Stories via Instagram Direct, the app's private messaging tool for solo and group messages. Problem is, it works both ways, so whenever you add to your ephemeral Story, everybody that sees it can share it directly with anyone else.

The peaceful, pastel and doily-filled world of Pinterest is my oasis. My account conveys who I want to be and what I want to accomplish, so the idea of someone hacking it and ruining my favorite escape for me is heartbreaking. Fortunately, Pinterest has updated its security, implementing three new features to hack-proof your account.

In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent.

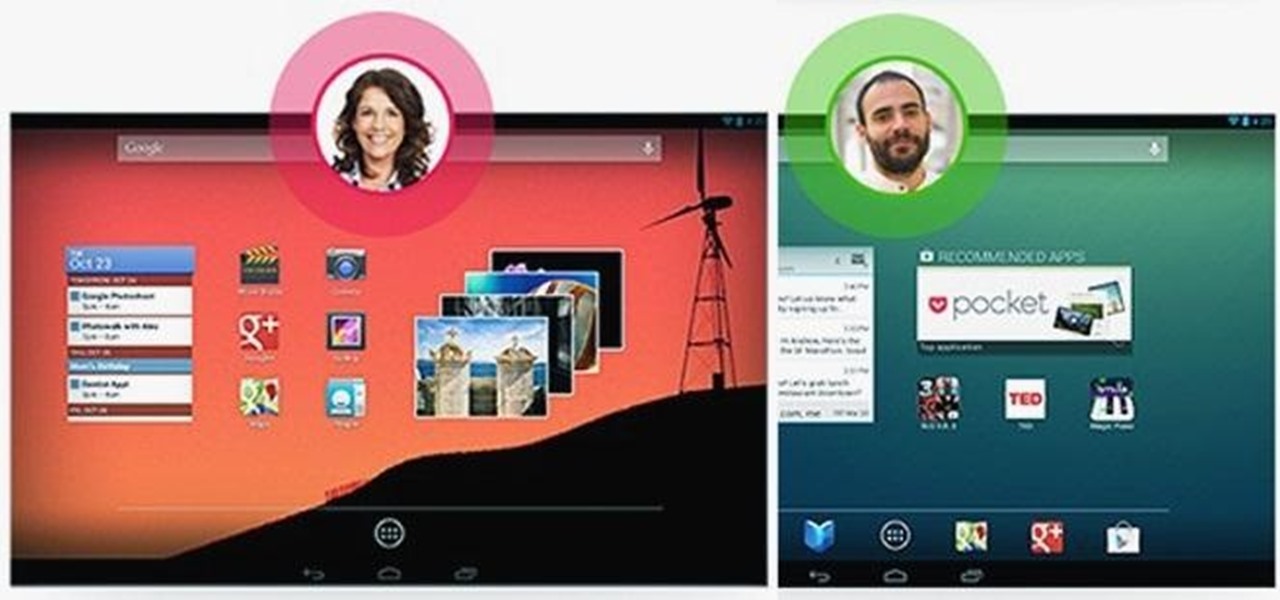
The most recent update for Android's Jelly Bean has some pretty cool new features, like better panoramic photos, gesture typing, and wireless sharing. From a security standpoint, though, the best new feature is the ability to add multiple users to one device. You can create up to 8 different accounts on Android tablets like the Nexus 7 or Nexus 10, so besides saving time hiding or protecting sensitive data, it could also save you some money. You can share a device with your family, kids, or s...

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

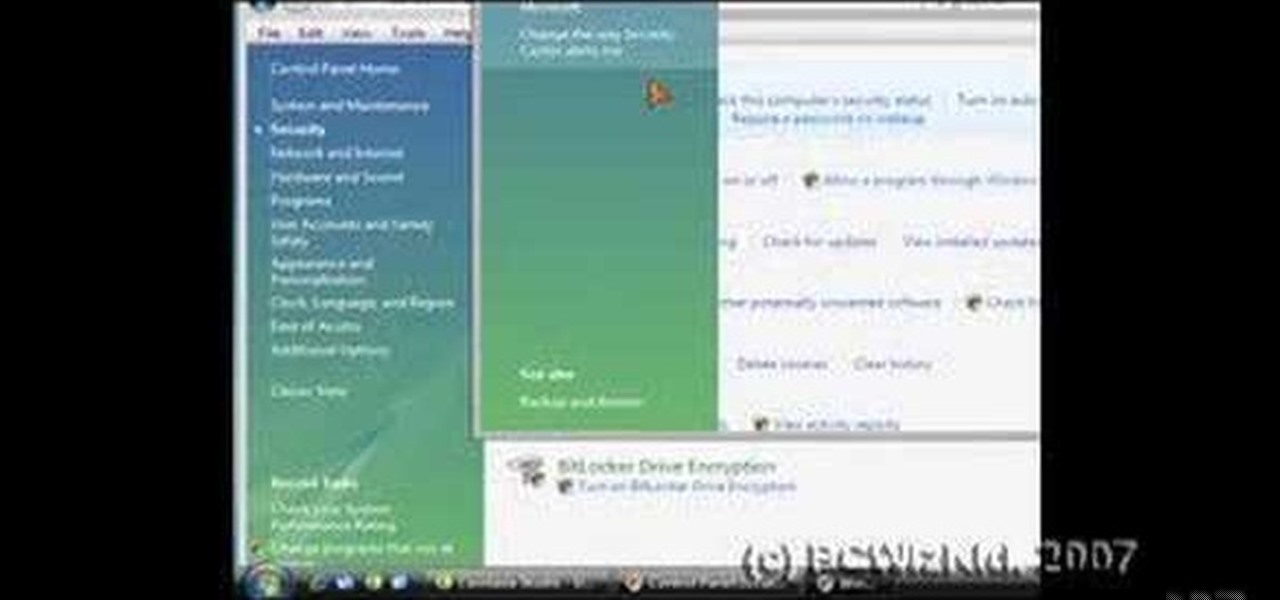
Windows Vista is jam-packed full of new security features, which could be a good thing, but they're just so obtrusive it's not really worth it. If you want to learn how to stop all of the annoying security alerts, this video will walk you through the process of disabling these security notifications in Windows Vista.

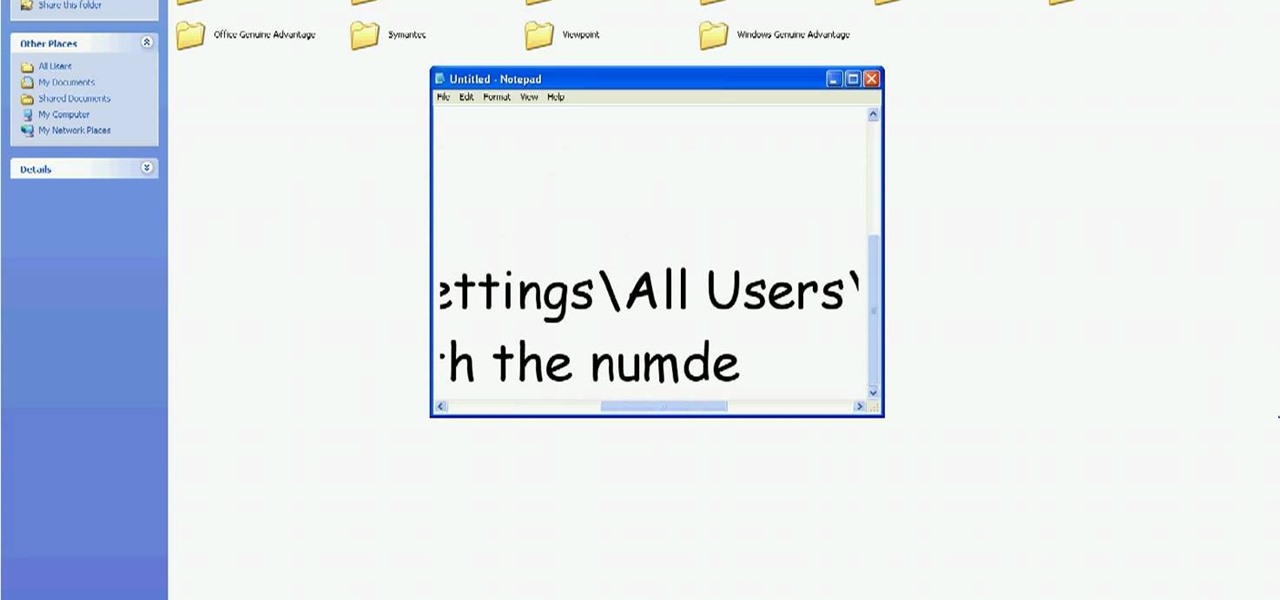
In this tutorial, we learn how to delete Security Tool from your computer. First, you will need to restart your computer. After this, go to your documents on your computer. Then, type in "Type C:/Documents and Settings\All Users\Application Data". After this, delete the file with all of the numbers. If you now get an error that says "access denied" then restart your computer again. Once the starting screen appears, press "F8", then select safe mode and redo the steps that you just took. After...

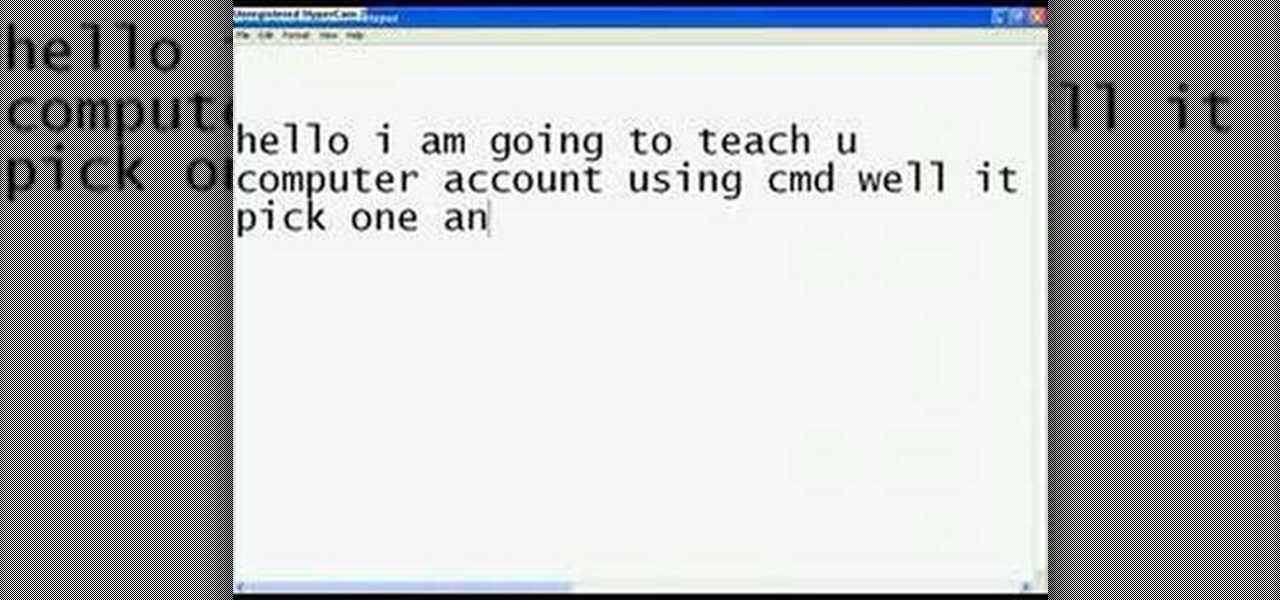
This video teaches you how to change your computer's account password using the DOS command prompt. The first step is to get to the command prompt, you can do this simply by clicking run in the start menu and typing "cmd." You next type "net user" which will show you all of the user accounts on the computer. Choose the one you would like to change the password for and type "net user (account name)." It will then ask you for a new password, you may type anything you like here keeping in mind t...

Installing security lights outside of your home can make for a great addition, but they also create new problems with regards to maintenance and cleaning. Having lights outside exposes them to all of the elements that mother nature can throw at them. This video will show not only how to install security lights, it will also show the proper measures to take so they will keep working with minimal maintenance and care.

This is a lock picking video which demonstrates how to pick a tumbler lock. Of course the only way to really open locks is to practice. But this is the basic info to picking locks. This lock picking tutorial also covers security pins and clear instructional animations to demonstrate. Learn how to pick a lock and use this video to understand lockpicking, security pins, skill tension, and bump keys. See all about how to pick a tumble lock & understand lock security pins.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

New updates to the journaling app Day One include more security for journal writers' data. For example, users can now enable end-to-end encryption. The encryption does not happen automatically; however, users must go to Settings — within Journals — then select each journal they want encrypted.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

As it turns out, your Android apps are pairing together to share your data without asking for your permission first. Researchers from Virginia Tech developed a tool called DIALDroid to monitor exchanges of data between Android apps over the last three years, and what they've found is quite alarming.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

If the recent "state sponsored" Yahoo hack wasn't enough motivation for users to stop using their services, the latest news about Yahoo should be. Joseph Menn, a reporter at Reuters, just revealed that Yahoo created a custom email wiretap service for the US government.

A human rights activist from the United Arab Emirates recently stumbled upon three gaping security loopholes in iOS that work by enticing you to tap a link sent to your iPhone. Ahmed Mansoor received a text message from an unknown number roughly two weeks ago, but instead of following the link it included, he sent the message over to a security researcher at Citizen Lab.

Update 1: Evad3ers have released a statement to the jailbreak community, claiming that the safety and security of their users is the most important thing to them and that all speculations about malware being encoded into the jailbreak is simply not true. You can read the full letter over at Evasi0n's site.

In order to secure a PDF with a password when opened in Adobe Acrobat 9 Pro, press the secure button and go into password security settings. Here you can change on what versions of this software the file will run on, the next option asks which portion of the document is to be encrypted when a password is placed. Further below here is where you actually choose the password, this ensures that only people who know the password will be able to see the contents of the document. Below this is the d...

Lock picking can be difficult with some security features. This instructional video shows you what happens when you encounter them and what to do. Break into a lock when you've forgotten your keys, but please don't sneak in anywhere you don't belong. Watch this video lock-picking tutorial and learn how to detect security pins.

With the new screening protocols and their full body x-ray scanners, the TSA is taking constant criticism from unhappy travelers. Between the nude images the scanner produces and the awkward pat downs, air travel will never be the same. That's why it's important to make sure you're prepared for your flight and the TSA security checkpoints.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your computer, access hidden files, reset your passwords, and more. Root access gives them the ability to do anything they want.

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

Google's monthly Android security updates are generally welcome—at the very least, they provide a feeling of security that our device is now somewhat safer than it was 30 days ago. Vulnerability patches, slight enhancements to performance, and overall bug fixes are generally included in the monthly OTAs, but as it turns out, they're not always for the better.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

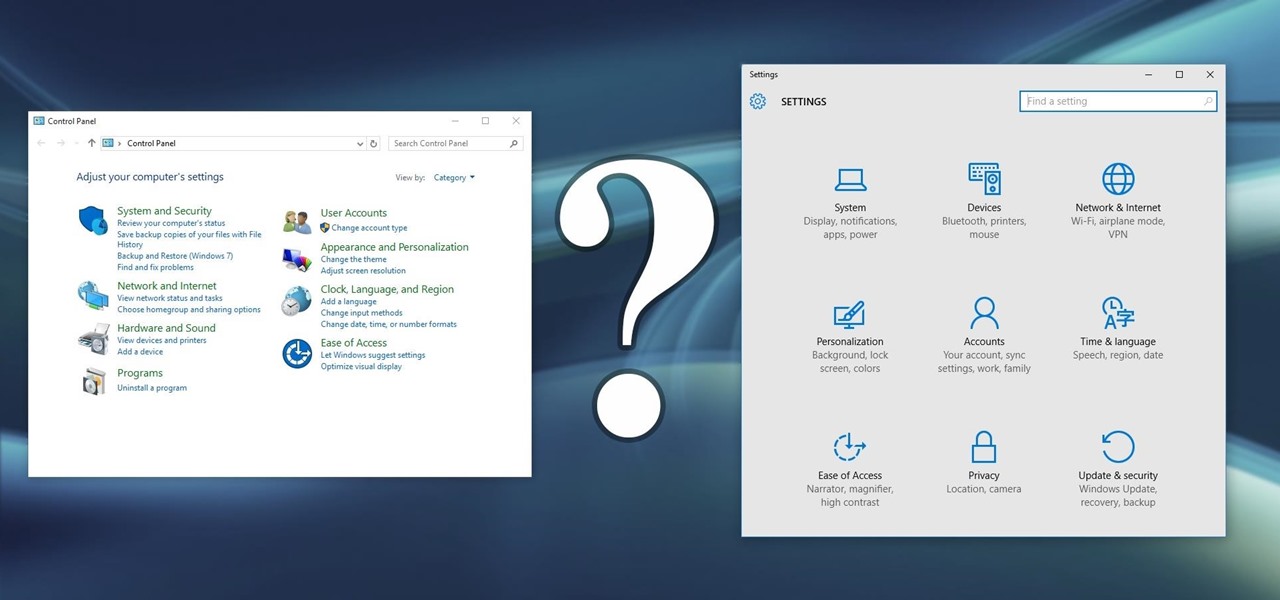
Slowly but surely, Microsoft is pushing more and more options out of the Control Panel and into a new menu simply called Settings. This new Settings menu debuted with Windows 8 and mainly focused on touchscreen-related options, but starting with Windows 10, you'll find quite a few general options residing here as well.

In this clip, you'll learn how to quickly set a security pattern on an LG Droid Ally Google Android smartphone. For more information, including a complete demonstration and detailed, step-by-step instructions, and to get started setting up your own security secreen, watch this helpful video guide.

Want to test the security of your WEP WiFi wireless network? In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Learn how to configure the features in F5's FirePass v7 SSL VPN Endpoint Security. Peter Silva shows some of the new Endpoint Security features in the recent FirePass v7 release. Watch how to create policies, enforce host checks and other protective measures for your Remote Access deployments. For more information, and to get started configuring your own installation of FirePass v7, take a look.

If you live in a hurricane prone area, it is a good idea to protect your windows with security film. This video will teach you how to install hurricane security window film on your own and protect your home and assets.