Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

Ever use an open hotspot on your Note 3, only to find out that it's severely restricted to what sites you can access? While getting online with free Wi-Fi is great for those who have a limited data plan, when that one site you absolutely need to visit is blocked, you're left frustrated and sent back into the Wi-Fi menu for another access point.

A security analyst has discovered a flaw in Chromecast's initial setup process that allows would-be hackers to assume full control over the online streaming device.

Copy and paste keyboard shortcuts are beautiful gifts from the gods, and any website that blocks such an offering can burn in hell. But really, Cmd+C and Cmd+V (Ctrl+C and Ctrl+V for Windows folks) are second nature to most of us, so it's very frustrating when sites like PayPal don't let us use them.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Update: June 2nd, 2014 Over the weekend, someone snuck in to Apple's presentation dry run, and grabbed a quick video of the new iPhone will look like.

Adding to the recent recent slew of bugs and issues within iOS 7, it now seems that emails sent with attachments are not encrypted, despite Apple's claims that they are.

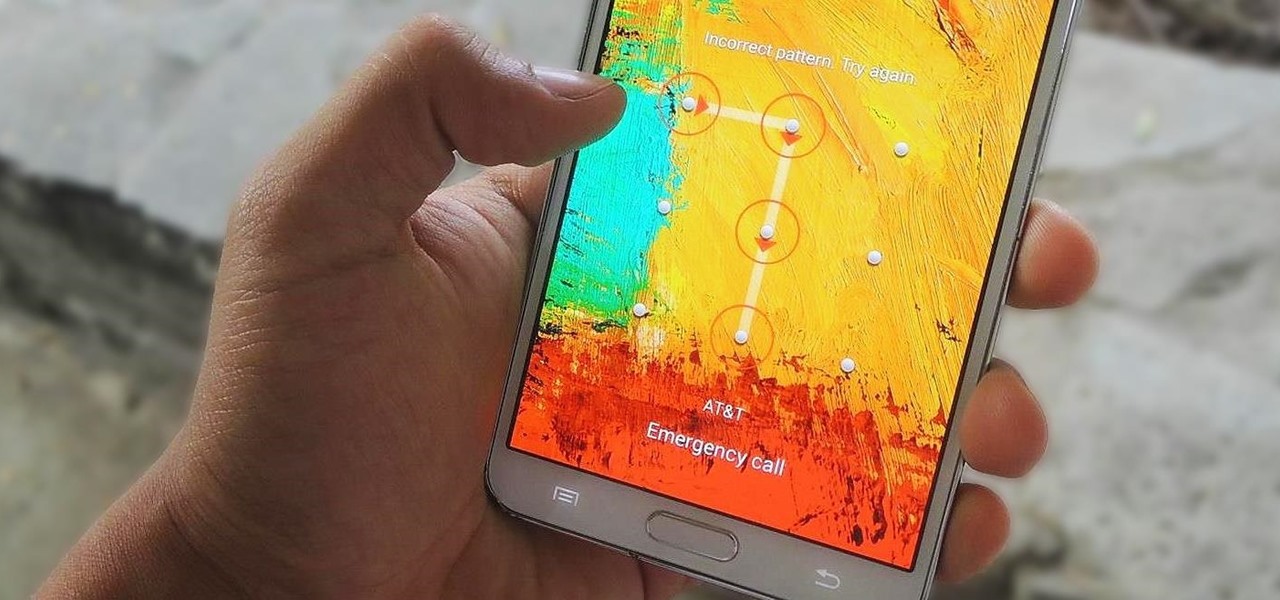
Lock screen security provides a means of safety when it comes to keeping others from breaking into our smartphones and snooping around on or stealing private information like documents, emails, photos, and videos.

There are countless mods and apps for Android devices that give them an iOS-style look, but maybe it's about time we take some notes from Android, especially when it comes to the iOS 7 lock screen.

Starbucks' app is the most used mobile payment app in the U.S. because it's well-designed and convenient. But if you use the iOS version on your iPhone, your username, email address, password and location data could be compromised because the app stores them in plain text.

I've said it before, but there are few things quite as annoying (or embarrassing) as having your smartphone go off at a time where it just shouldn't happen. Imagine a nice, intimate evening with your significant other; you dim the lights, snuggle up, and "this classic" comes on. Or, your phone goes off in a meeting, and your boss gives you that look.

While Siri came up on the scene with hardly any competition back in 2011, Google Now has not only caught up to Apple's intelligent personal assistant, but also excelled in certain areas—with its ability to quickly answer questions, give recommendation, and even deliver information that it predicts a user will want.

About a year ago, Abode decided to discontinue support for Flash on the Android platform. With its security concerns, it's understandable why some people would want to disable Flash on their devices, but there are still some things you can't do without it. Amazon Instant Videos is one thing you can't do, giving you nothing but a "Flash Player is not installed" warning.

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.

The beauty of free apps is that, well, they're free. But as we all know, there is no such thing as a free lunch. Sometimes these "free" applications are only feature-limited mini versions, or they're so littered with ads that opting to pay for it is the only way to actually enjoy it.

Spammers are the bane of every email user. No matter what you do, junk mail always breaks through the spam filters. And some of the best ones seem to come from legit companies, and that's because they aren't legit companies— they're spammers masquerading as legit companies.

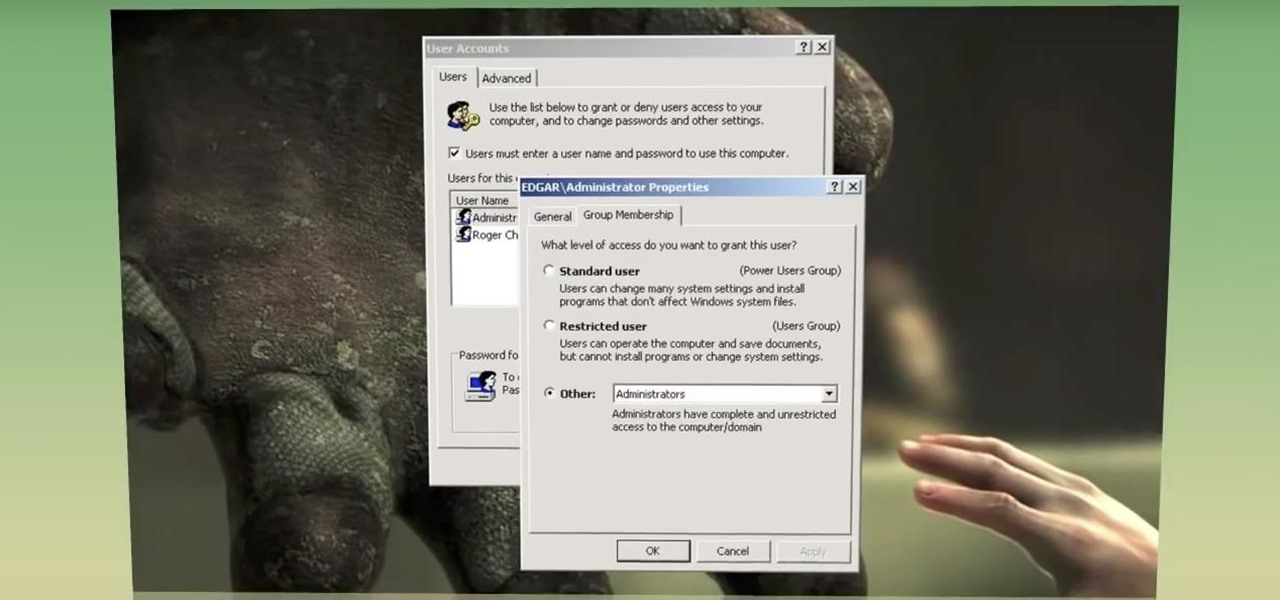
Admin accounts are given special privileges to change the system (like installing programs) that user accounts are not. This tutorial shows you a quick way to check using Windows 7's calendar, and also how to go through the Control Panel to find out if you're an Admin or general User on your computer.

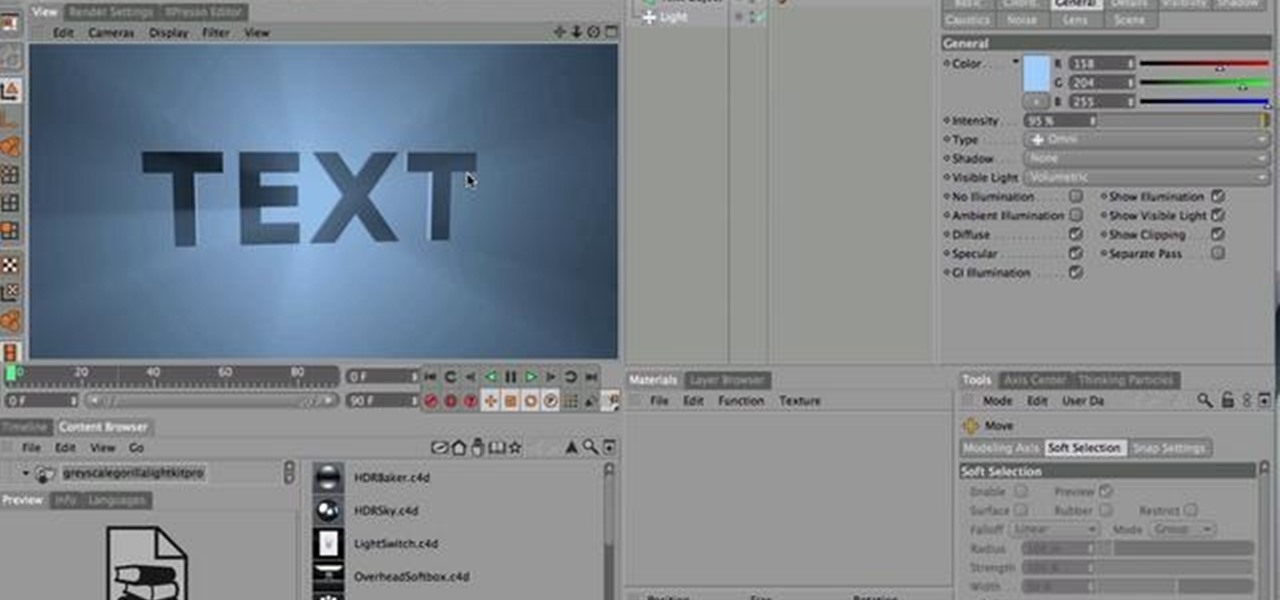
In this C4D user's guide, see how to create and employ volumetric lighting. Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more information, and to get started using this trick in your own Cinema 4D projects, watch this 3D modeler's guide.

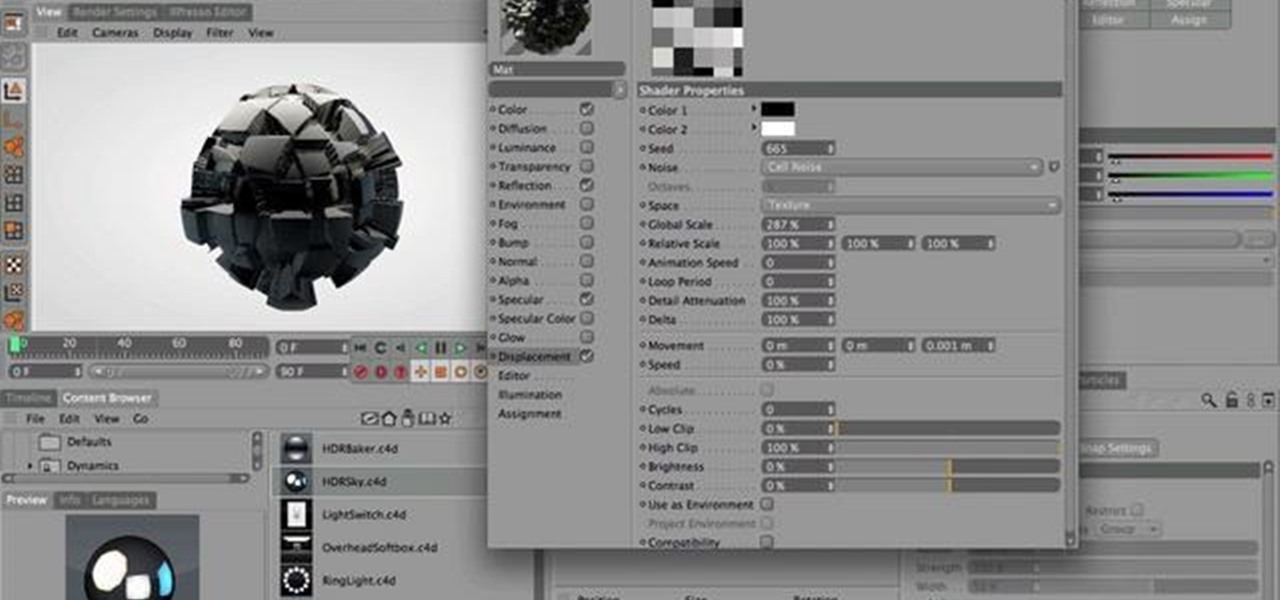
In this C4D user's guide, you'll learn how to use sub polygon displacement in your projects. Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more information, including complete instructions, watch this 3D modeler's guide.

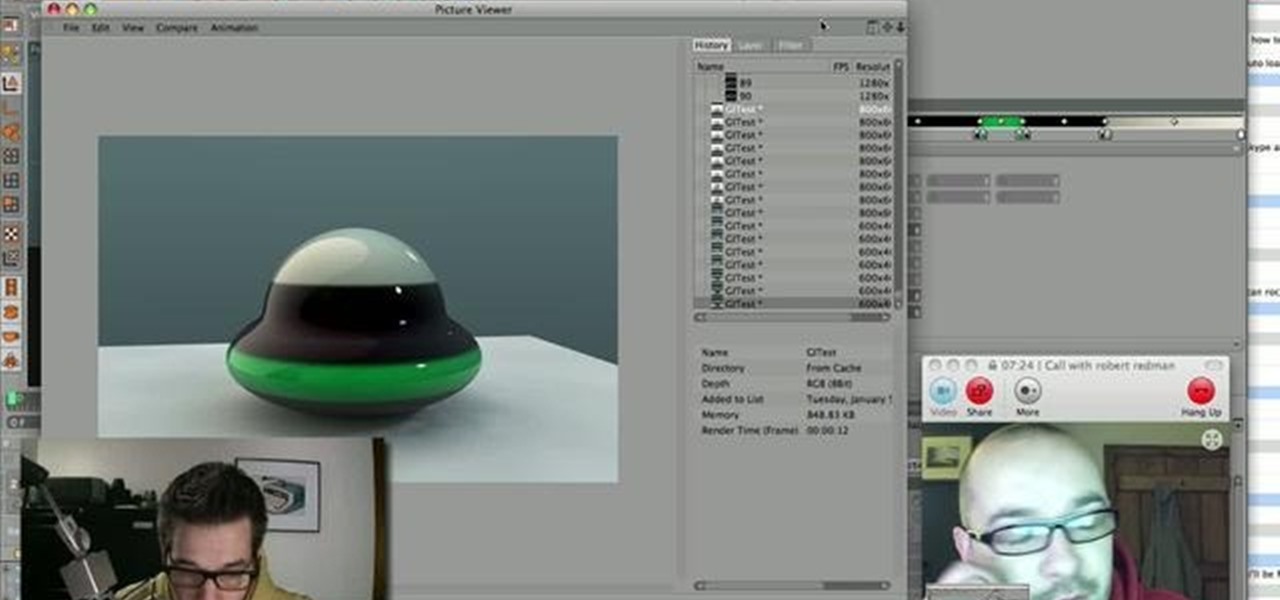
Learn how saving an irradiance cache can save time on rendering in this C4D-user's guide. Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more information, including complete instructions, watch this 3D modeler's guide.

If you're working on a website and want users to use it repeatedly and form a community on it, you should probably give them a way to create an account and log in to your site. This video will show you how to create an AJAX login script using AJAX with jQuery, which will allow your users to do exactly what I described above, making your website much more professional and a much better place for people to stay and click on ads or whatever else you want them to do.

In this video tutorial, viewers learn 4 different hacks that will make typing easier in Windows. Begin by clicking on the Start button and select Control Panel. Then click on Ease of Access Center and select "Make keyboard easier to use". Now users are able to configure the keyboard options for easier use such as: turning on/off the mouse keys, sticky keys, toggle keys and filter keys. All the features have more specific settings for self-adjusting to the user's liking. This video will benefi...

Flash and Actionscript can be used together to create damn near any sort of animation or website feature that you could want. This video will teach you how to do just one thing: generate a random frame using Flash CS4 and Actionscript 3. This is handy if you want to create a button that will link to several different objects randomly. Fun if you want to add the zest of unpredictability to your user's website experience.

In this video tutorial, viewers learn how to browse web pages without a mouse. Users will need to use the Mozilla Firefox browser. When you're in the Firefox browser, press F7 or click on Firefox, click on Preferences and select the Advanced tab (Mac OS X). Now check "Always use the cursor key to navigate within pages". This will activate character browsing, allowing the user to use the arrow keys to move up and down the page. Holding Shift will allow users to select a text. This video will b...

In this video tutorial, viewers learn how to make custom drawer icons for their stacks in Mac OS X. Users will need to go to the site provided in the video. There users will need to follow the instructions and download the icon sets. Once downloaded, place the icons into the appropriate folders. Users may need to restart the computer. Once restarted, the icons will be neatly overlapped in drawer icons. To add a folder to Stack, simply drag it to the dock. This video will benefit those viewers...

In this video tutorial, viewers learn how to remove/change the arrow on the shortcut icons in Windows. These arrows allows the user to know that the icon is only a shortcut. Users will need to download the program, Vista Shortcut Overlay Remover. The program allows users to display an arrow, light arrow, custom arrow or no arrow. This program also provides an option to disable the " - Shortcut" extension on any shortcut icon. This video will benefit those viewers who use a Windows Vista compu...

In this video, learn how to hack your HTC EVO 4G and root it for "Super user" access. Once you have rooted your device you can install custom ROMs, apps, overclock the CPU and a whole lot more. So, follow along with this step by step demo and root your phone to discover the possibilities!

Network mapping lets PC users organize multiple computers into a system that provides informational data access. This video tutorial shows how to set file sharing permissions and assign users designated privileges within a network. Establishing a network provides functionality within a workplace and facilitates virtual communication among users.

Follow along as we are shown how to set a password for a new user in Windows 7. -First, go to the Start menu.

Is Windows XP just not customizable enough for you? Well, it was made that way so you don't eff up any of the settings to the point of no return. However, if you are confident in your computer expertise then modifying user accounts may be something of interest to you.

When you're a Windows OS user it's very easy to send out attachments on emails as .doc documents, made in Microsoft Office or Excel. But just because you're a Windows user doesn't mean your friend or coworker is. Or say that you're a MAC user and your friend keeps loading you with Microsoft Office documents. What do you do, other than telling him to stop already?

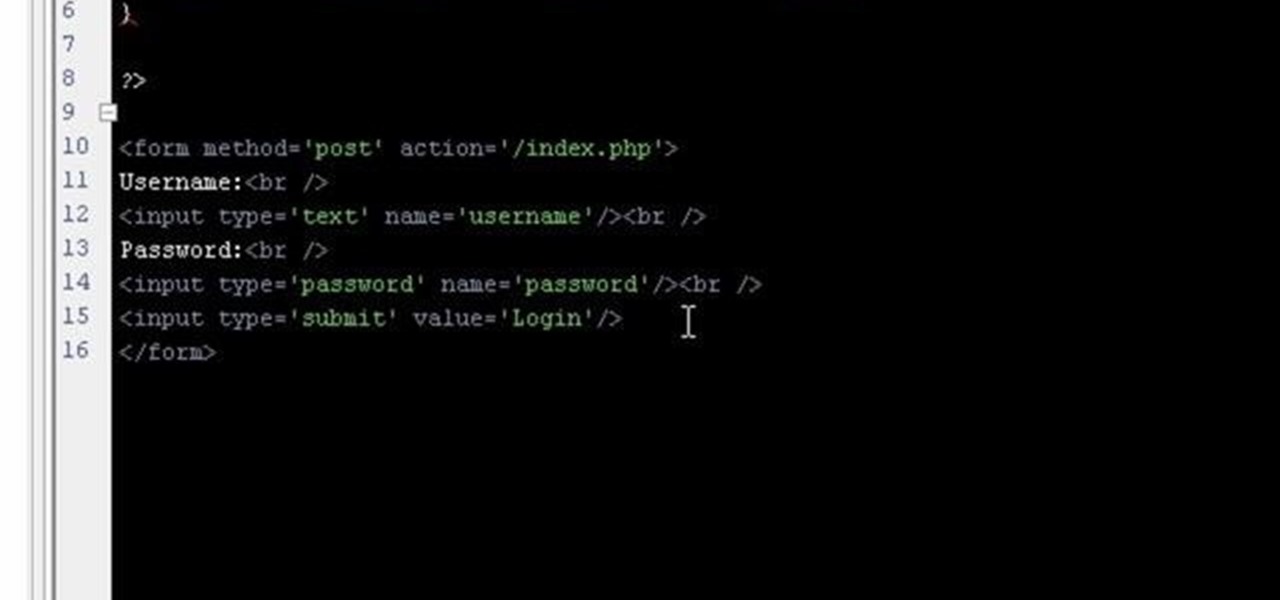
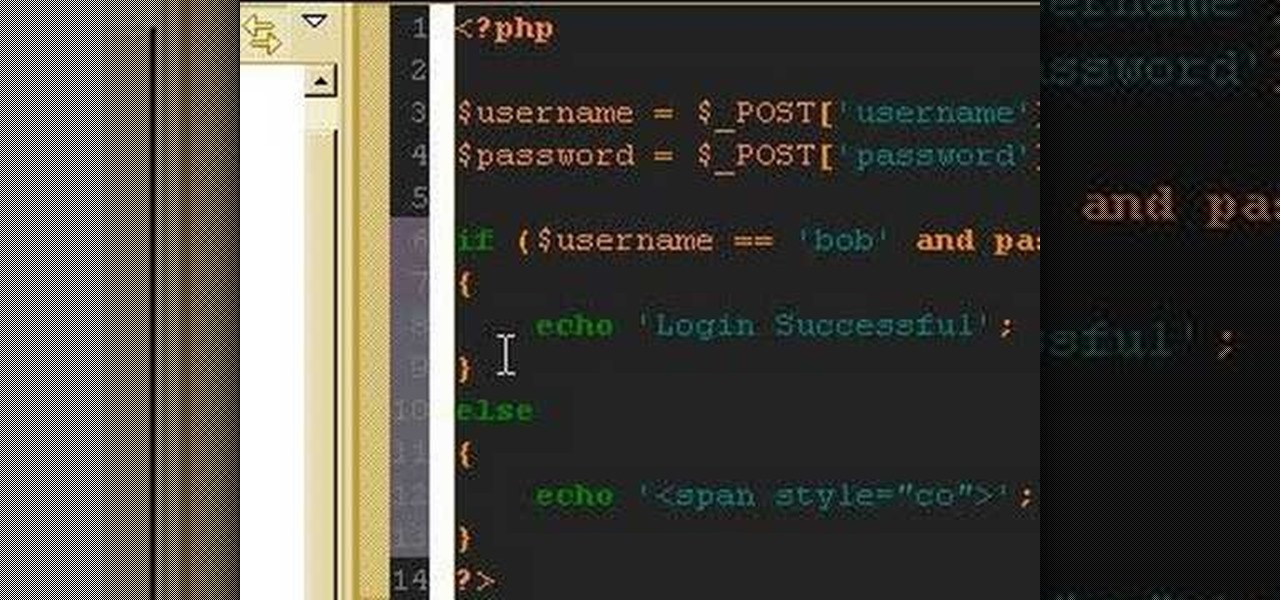
Using PHP & HTML to generate a user login form and authenticate the user.

In this video tutorial, viewers learn how to use Flickr photos in their screen-saver. This task can only be done on the Windows computer. Users will need to download the program from the website provided in the video. Once downloaded and installed, there is an option in the Screen Saver Settings. Users are able to take photos from specific users or groups, or can search through tags and contacts. Further options include selecting the size of the photo and delay between switching the photos. U...

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

After months of waiting, it looks like HMD has finally answered the call. Nokia's parent company is finally releasing a true flagship phone — one that isn't just an enhanced version of a previous phone and actually brings something new to the table. That phone is the Nokia 9 PureView.

Switching phones has never been easier. Google backs up most of your app data on the cloud, which can then be restored onto your new phone. Sadly, Signal doesn't use this feature since it could compromise your security. Instead, Signal stores encrypted backups locally, requiring a bit of work to restore these messages.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.