Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Apple announced upcoming changes today to prevent third-party tracking of users and prevent autoplay, on Safari. Safari will prevent the recording (by anyone other than Apple) of users' browsing behavior, and by doing so prevent advertisers from targeting ads based on individuals' history.

When it comes to modifying Android, the single, most powerful tool available is TWRP custom recovery. It's even more capable than simple root access when it comes to changing the look and feel of your software, and you can even use TWRP to root your device in a few simple steps.

As we reported first here on Gadget Hacks, the Google Pixel and Pixel XL have unlockable bootloaders, with the exception of models purchased from Verizon. This means that once the TWRP custom recovery is installed, you can flash ZIPs and even root your device in a few taps—as long as you unlock the bootloader beforehand.

Greetings fellow students! I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers"

The first time a friend or family member asks if they can borrow your phone or tablet, you probably just hand it over without a second thought. But the second, third, and fourth times? Now it's starting to become a habit, and something probably needs to be done about it.

If you're completely new to Android, you're in for a treat with all of the software tweaks and customization options that your smartphone or tablet offers out of the box. But if you really want to take things to the next level, the ability to mod your device expands exponentially when you're rooted.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

Both the Galaxy S6 and S6 Edge have had root methods available to them before the phones were even released, but the problem with these existing root methods is that they would trip the KNOX counter on your device.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

When Google released Android 4.2, a new feature was introduced for tablets that allowed for multiple accounts to be used on a single device. In order to create a unique experience for each user, apps and personal data were kept separate, and switching between users became as simple as tapping your profile photo from the lock screen.

Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.

Configuring user accounts is extremely important for those with a family shared computer or anyone using a work computer. Assigning different accounts with their own distinctive accessibility, customizations, and applications is the best way to manage a computer with multiple users.

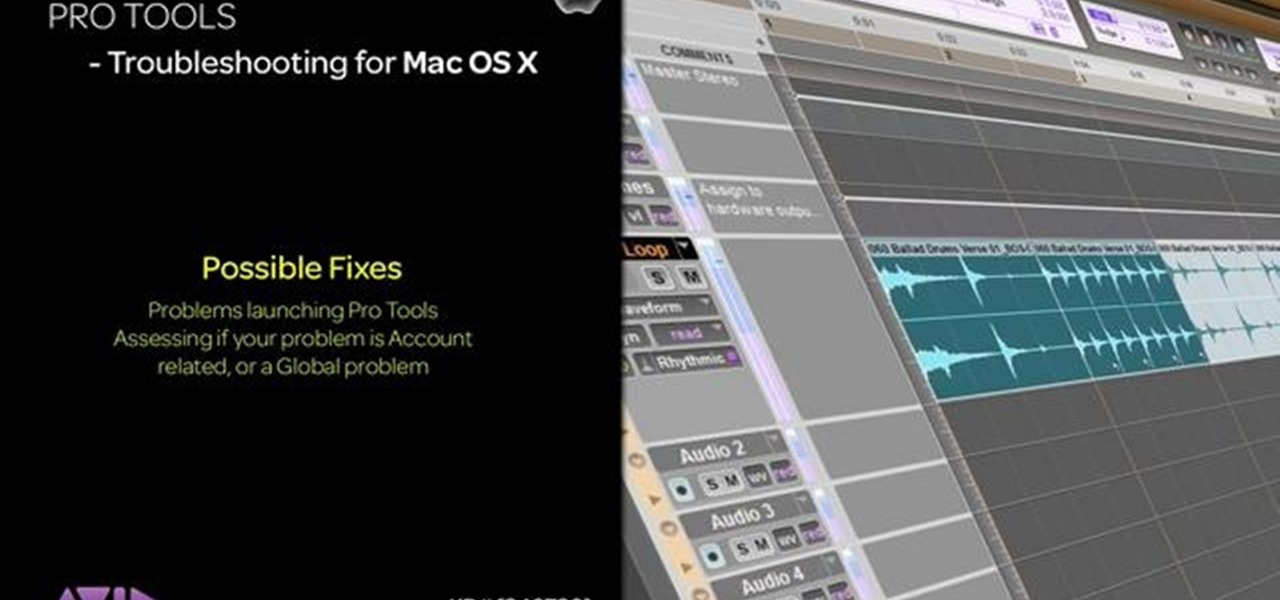
This video describes how to create a new user account on an Apple Mac OS X 10.6 (Snow Leopard) computer to tell whether your Pro Tools problem is user-specific or global. Whether you're new to Digidesign's Pro Tools 8 or simply looking to pick up a few new tips and tricks, you are certain to benefit from this free software video tutorial. For complete instructions, take a look.

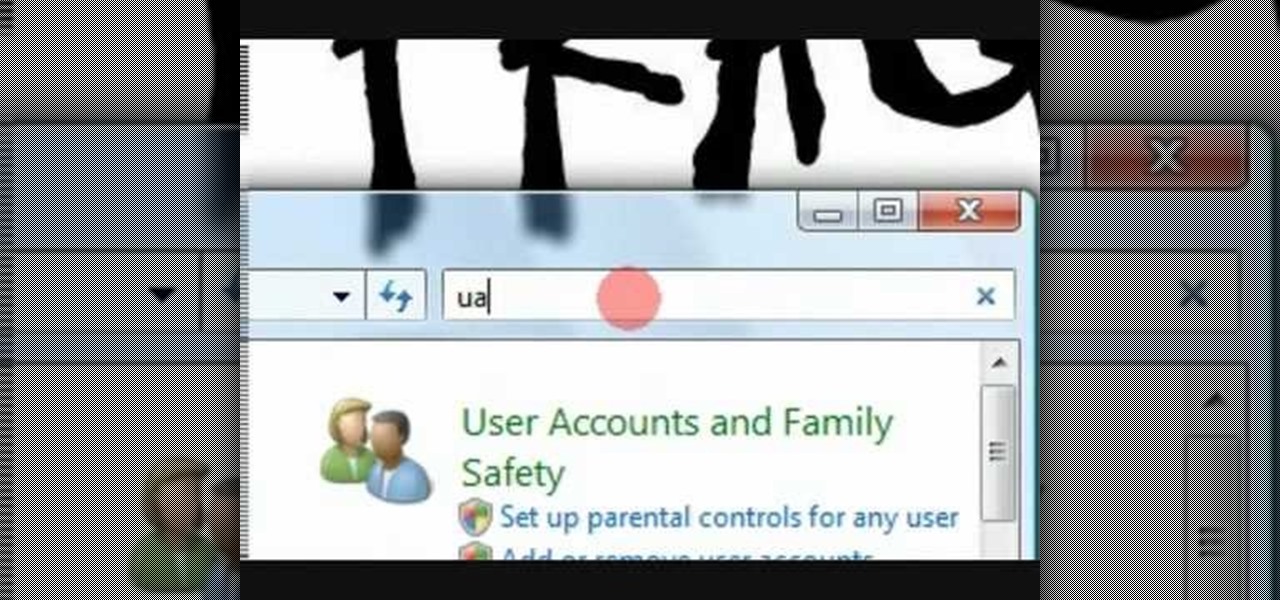
In this video tutorial, viewers learn how to disable User Account Control in a Windows Vista computer. Begin by clicking on the Start menu and select the Control Panel. Then type in "user account" in the search box and click on "Turn User Account Control on or off" under User Accounts. Now deselect the checked box and click OK. Finish by clicking on Restart when the Microsoft Windows window pops up to reboot the system for the changes to take effect. This video will benefit those viewers who ...

Want to keep other users from accessing certain applications, files or folders? This video tutorial will show you how it's done! It's easy! So easy, in fact, that this home-computing how-to can present a complete overview of the process in just over a minute's time. For more information, including detailed, step-by-step instructions, watch this Win 7 user's guide.

This Blender user's tutorial covers camera movement from camera view, the render panel, and the ambient occlusion panel. Whether you're new to the Blender Foundation's popular 3D modeling program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed instructions, take a look.

In this video Jesse Liberty demonstrates how to create user controls dynamically (at run time) and how these user controls can raise events to interact with the page that creates them. This is a step by step, extensive tutorial on exactly what you'll need to know when using Microsoft's Silverlight. This is a detailed, easy to follow video, to help you use the program, and all it entails.

Basically there are three quick ways to run a program as administrator. You can do that by clicking on cmd. We usually use this cmd prompt for finding your I.P. address and you can modify user accounts also. Another way is to click on start and type cmd in Run. Make a right click on cmd and click Run as Administrator. Final way to run program as an administrator by having right click on the program and select properties next select Compatibility, then select Operating System and finally, sele...

This video tutorial from Help-Vids shows you how to setup the automatic login in Windows XP so that you are automatically logged in as a specific user when you turn your PC on. Go to the start menu, select run and type the given command. When the user account dialog opens un-check the setting requiring the user to enter a name and password to use the computer and click apply. Fill in the user name and the password of the user that needs to be automatically logged in and click OK. Now when you...

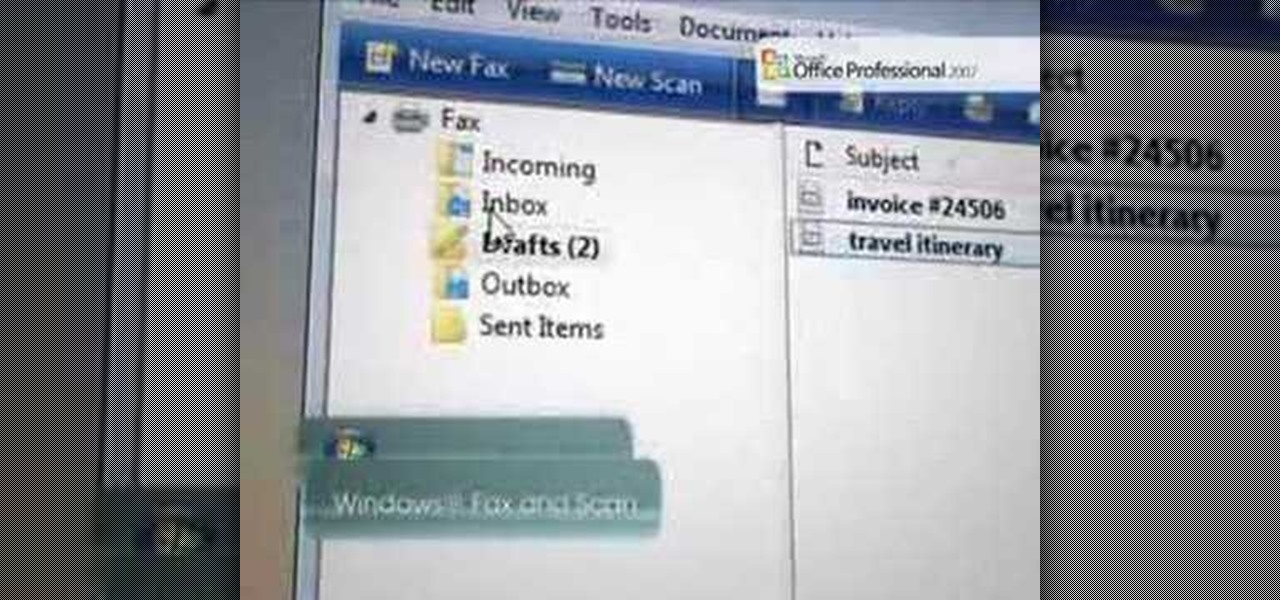
With Windows® Fax and Scan feature that works with the Windows Vista™ operating system makes it even easier to share fax and scanning capabilities with multiple users. Where previous fax and scanning programs allowed an individual user to send and receive faxes or scan documents with a locally-connected fax or scanner; Windows Fax and Scan provides a flexible system for multiple users to share local or network-connected scanners and fax devices. F

The User Dashboard in OnTime is a great way to look at items across types and edit them. See how to view and search through data regardless of its type (Defect, Feature, Task, Incident) by taking advantage of the User Dashboard. For detailed instructions on using the dashboard, watch this installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite.

Ever wish you could switch between users on your Mac without having to kill all of your applications (and losing all your data) in the process? In this tutorial, Molly Stanberry from MacMost.com Shows how to enable fast user switching in Mac OS X Leopard.

Maxon's CINEMA 4D allows users to add a module called HAIR, integrating custom hair control to 3D projects. However, sometimes users may want to export the HAIR geometry to non-HAIR users. The process, although easy, isn't necessarily obvious. Here's how you can do it, or at least one way to do it.

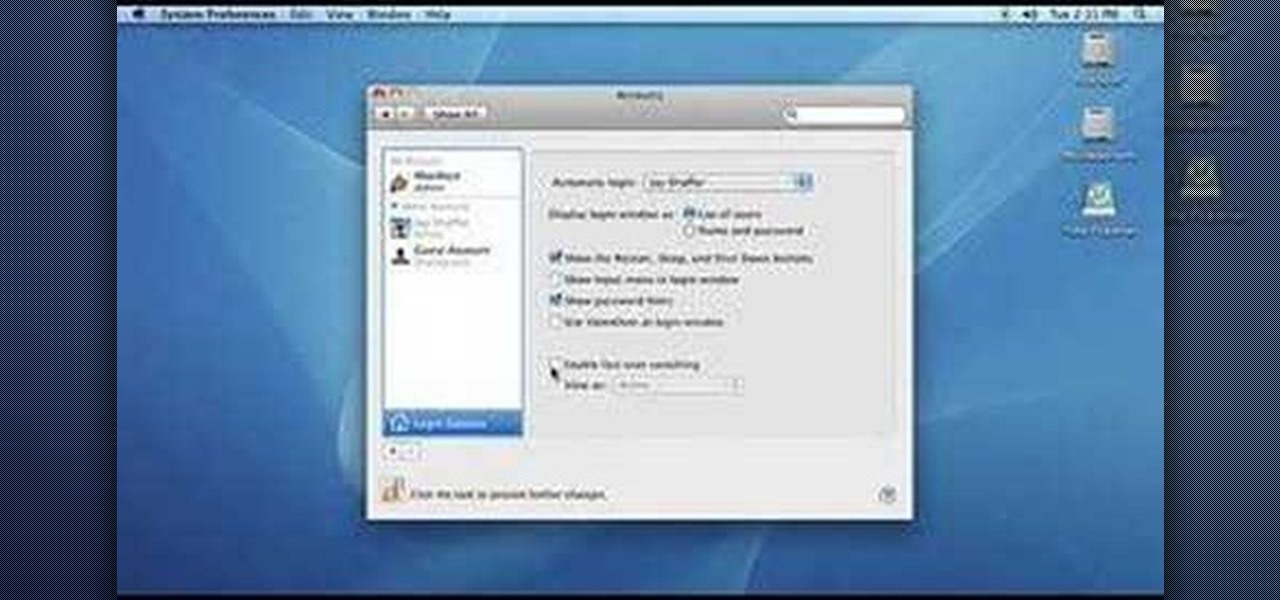
This video shows how to enable automatic login for Macintosh Operating System users: 1.Click on the Apple icon in the top-left corner and select System Preferences.

In this tutorial, we take an introductory look at node based compositing from the perspective of an After Effects user. If you are someone who has lots of experience with After Effects, and wants to get into using a program like Shake, Nuke, or Fusion, this will help you get on the right track. Whether you're new to Adobe's popular compositing application or are just looking to get better acquainted with AE and its various features and functions, you're sure to enjoy this free video software ...

In this video the instructor shows how to set parental controls for a user ID account in Windows 7. To do this go to the 'Start Menu' and go to 'Control Panel'. In the Control Panel window select the 'User accounts and Family Safety' link. There is an option called 'Set up parental controls for any user'. Select that link and it opens a window where it asks you to Choose a user and set up parental controls. There you are presented with some user accounts that are currently active on that syst...

This video shows how to delete a user account on Windows 7. Go to the start menu, the control panel, then user accounts. Click add or remove user accounts. Select the account you want to remove. Choose the option to delete the selected account. Windows will ask if you want to delete everything on the account or keep the information on your desktop while still deleting the account. This will be your choice. The narrator chooses to delete the full account.

This video describes how to create a new account on Windows 7. In this video it is shown the whole procedure and all you need to know to crate new user account.

This video demonstrates how users of the FileMaker Pro 10 software can easily start using this software from the quick start menu. It is demonstrated to users how to create a database or open an existing database from this quick start page. Also demonstrated is how users might be able to find further information using the "Learn More" option at the bottom of the menu. This option shows users the basics via videos, tours, and tutorials. A must see for those new to this software.

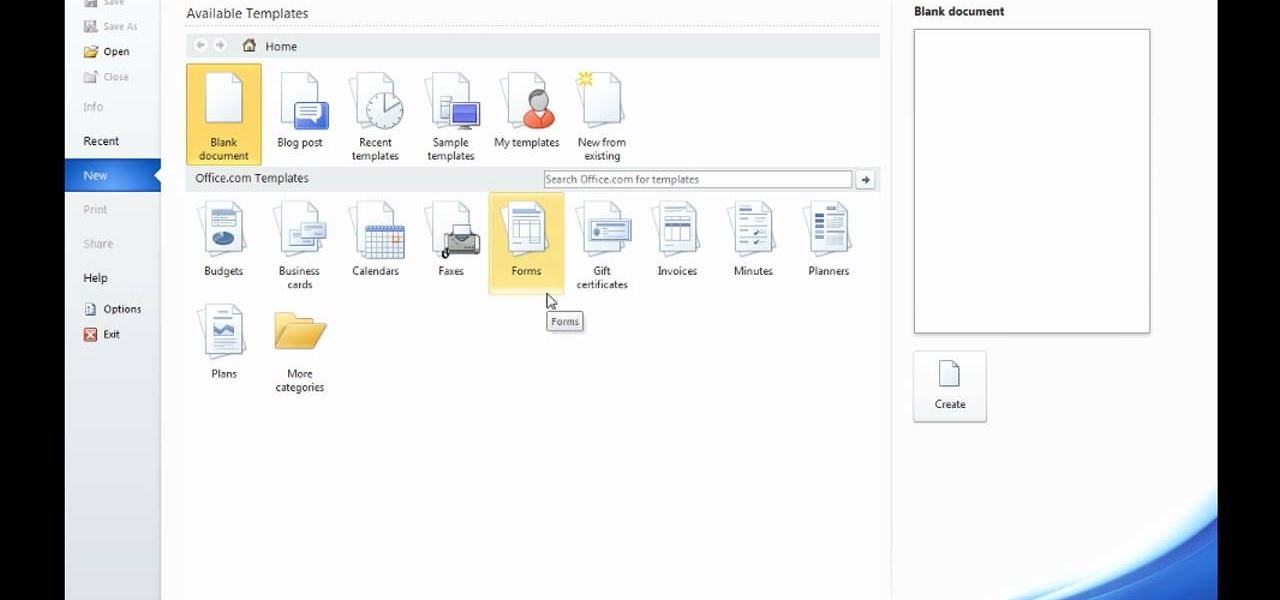
Microsoft Word 2010 prevails with new advancements. New options such as Backstage view allows the user to work efficiently and utilize new abilities when managing documents. It succeeds with new abilities that will allow the user to complete tasks quicker than before. Working with the newly enhanced ribbon allows the user to navigate with an easy, more personal customized environment. Now with more options and commands at your fingertips, it is evidently shown that Microsoft is gifting users ...

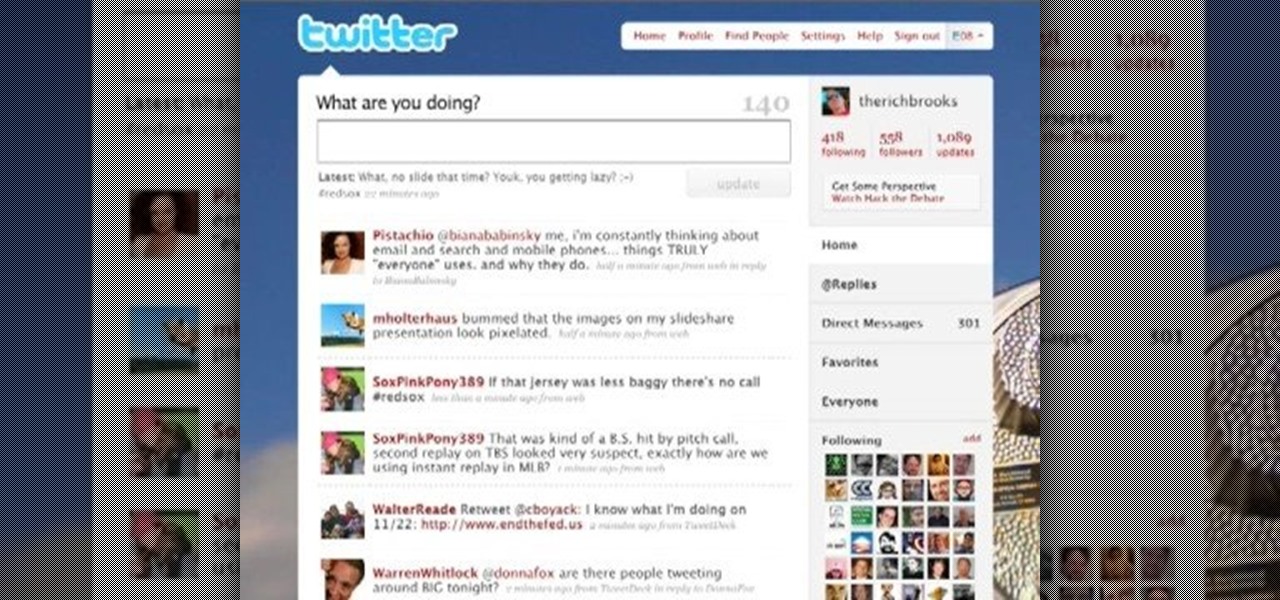
In this tutorial, we learn how to sign up and set up a Twitter account. Twitter is a social networking site where you have 140 characters to tell your friends how you are feeling, what you are doing, or talk to them! You can follow people and other people can follow you. You can choose who follows you, which will create and strengthen online relationships. You can even get business referrals from this! Just by getting yourself out there, this is a great tool. To sign up, you will simply go to...

In this tutorial, we learn how to remove pop up screens when Avira Antivirus updates. First, locate the installation folder for Avira, this should be in your computer programs. After this, locate the file "avnotify.exe". Next, right click this and go to the preferences option. Now, go to security, then edit, then click on the system option. Click "deny" on all the boxes in the bottom section, then save these. Now, the next time your Avira updates, you will not get a pop up box that tells you ...

This video tutorial is in the Computers & Programming category where you will learn how to secure your wireless internet connection. If you don't secure your wireless internet connection you are allowing others to enter in to your network. Open the set up CD and first change the network name from the default name to anything that you like. For this go to step 3 of 'naming your network', type in your network name and click 'next'. Then you enable security on the network by choosing 'WPA2'. Nex...