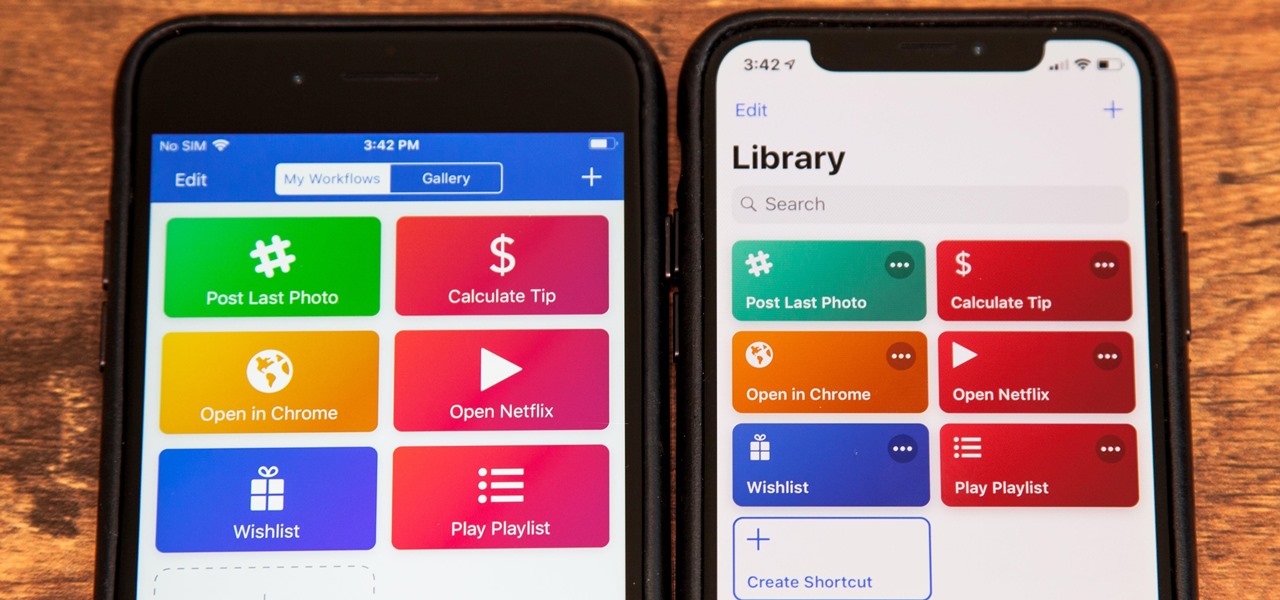
You have an online store ready to go… almost. You still have to deal with getting the perfect shopping cart to go along with your e-store. Matt Winn from Volusion walks you through what to consider when choosing a shopping cart software for your online store. From what type of software exists in the market, to the required features, to security levels (PCI certification), to the type of support you may need.

This video shows us how to install a ceramic soap dish in our bathroom shower. In this demonstration the instructor already had a slot in the shower tiles for the soap dish to go. Attach a long strip of masking tape on the edge of the soap dish. Mix some grout and place this on the part of the soap dish you are attaching. Be generous with the amount so you know it will stay. Place the soap dish in the slots and use the tape that you attached to be extra security that your dish will not fall. ...
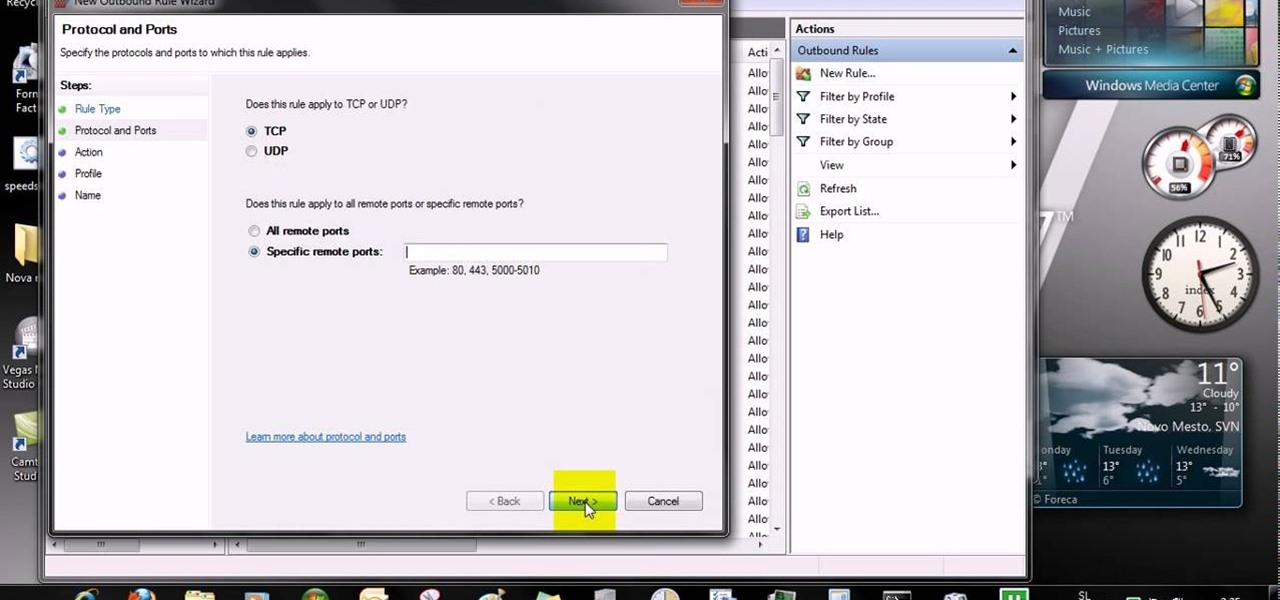
This video tells us the method to open ports in Windows 7. Click on myu icon and go to 'Preferences'. Copy the port number from the resulting window. Go to 'Start', 'Control Panel' and 'System and Security'. Go to 'Windows Firewall' and 'Advanced Settings'. Go to 'Inbound Rules' and 'New Rule'. Click on 'Port' and select 'TCP' and 'Specific Local Port'. Type the port number in the text box. Click 'Next' and 'Allow Connection'. Press 'Next' twice and put the name in the space provided for it. ...
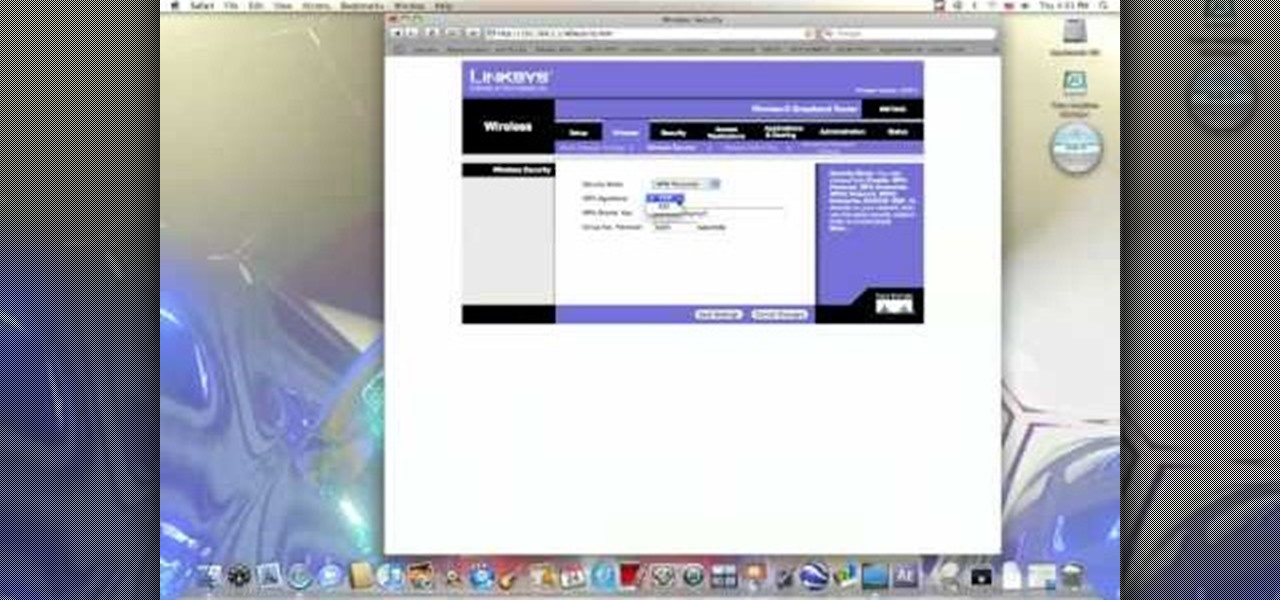
In this video from benjamoon we learn how to secure a linksys wifi network from a Mac. First type in your IP address in your browser bar which is 192.168.1.1 then press enter. If it asks for a password it is admin. Click on Wireless and here you can edit your name and who can access your wifi network. Under wireless security, go to WPA personal from the drop down menu. When you make your password, make it very challenging. He recommends just banging your hand against the keyboard, as long as ...
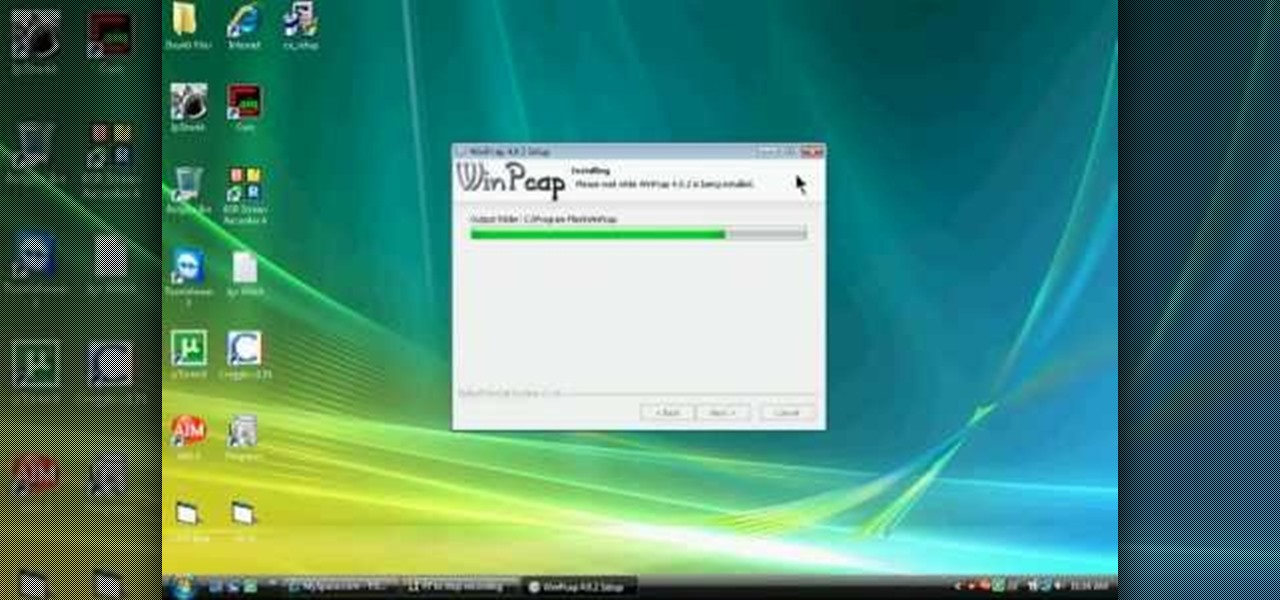
First you have to install program, called 'Cain and Abel'. Then, you will be automatically asked to install 'Win Pcap' and you should do that. After installation you have to click on 'Cain and Abel' program icon with right mouse button and start it as administrator. Then push blue plus sign to scan Mac addresses. After scanning go to the bottom of program window and press APR tab. Then push blue plus icon again. When table appears push first option in first square and first option in second a...

Watch this video to learn how to get Aircrack on your iPhone or iPod touch. You can use Aircrack on your iPhone or iPod touch to recover wireless network keys. The program runs directly on your iPhone or iPod touch device. It is installed as any other third party iPhone app, easy to launch and speedy to set up. Aircrack can be used as a security testing tool. Use it to verify that your network is attack immune.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hack a SharePoint site.

Check out this instructional con video that demonstrates how to pick a Wafer lock. They are commonly used in thefts. Regardless of the security level, the picking technique is the same. Follow the simple instructions outlined in this tutorial video and learn how to pick a wafer lock. Start picking locks like a pro!

Puzzles include multiple pieces each with a designated pattern so that when a user regroups the pieces, a picture or a particular image is presented, which provides practice to the coordination of the user's concept to space and structural relationship between pieces. However, no matter how large the quantity of the pieces is, puzzles only provide user's spatial concept in two dimensions. To enhance spatial concept and increase entertainment to the user, building blocks are promoted so that u...

Ethical hacking is a useful skill that can make you stand out in the field of cybersecurity. Whether you're just entering the field or are already established and are looking to stay current, learning the fundamentals of the white hat is an essential skill for your professional development.

Up until April 2020, the iPhone XR was, for many new users, the first entrance into the world of Apple because it was the cheapest iPhone model since the original iPhone SE. Now, the second-generation iPhone SE has shown up at the same initial starting price as its predecessor, giving budget-friendly buyers another choice.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

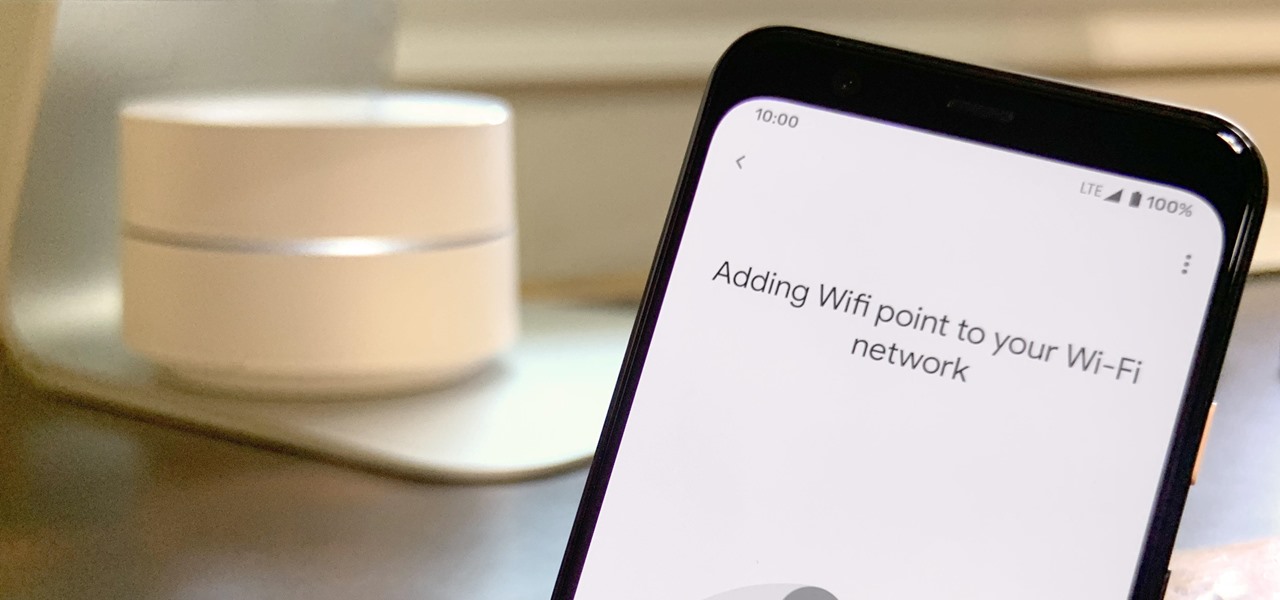
Google is known for merging older products into a new one's ecosystem for ease of use. The transition can take time, and that's the case with the old Google Wifi system now that Nest Wifi is out. Google is working on phasing out the dedicated Google Wifi app in favor of using the Google Home app for all your IoT needs.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

Apple seeded the official version of iOS 13 to compatible iPhones on Sept. 19. Since then, we've seen two major updates — iOS 13.1, which, by our count, introduced 22 new features, and iOS 13.2, which also added 22 new features. Today, Dec. 10, Apple introduced the third major update: iOS 13.3.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

Who's ready for another beta season? We beta testers have had quite the break: Apple released the fourth public beta for 13.2 on Oct. 23, and since then, two full weeks have gone by without a shred of beta news. It seems this Wednesday, Nov. 6 is our lucky day, as Apple just released the first public beta for iOS 13.3.

In recent years, the US military has been utilizing augmented reality as a training tool, giving officers and soldiers an opportunity to train and hone their decision-making, tactical efforts, and weapons accuracy via virtual scenarios.

While the eyes and ears of the iPhone world are singularly fixated on iOS 13 and its suite of over 200 new features, Apple was actively piloting iOS 12.4 in tandem with the big iPhone update, in preparation for the release Apple Card. Today, Apple has finally seeded iOS 12.4 stable, 116 days after its first beta version, and there's still no concrete evidence that Apple Card itself will show its face.

For Snapchat users wondering if that selfie is ready to send to their crush, independent Lens Studio creator Andrew Mendez created a handy tool called the Smile Rater.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.

With the growing list of products Apple offers, the number of devices connected to your Apple ID can get quite extensive. Having all those devices connected to your Apple ID helps you keep track of them, but when it comes time to part ways with an Apple TV or Apple Watch, those devices can still be attached to your Apple ID. In some cases, this could affect the overall security of your account.

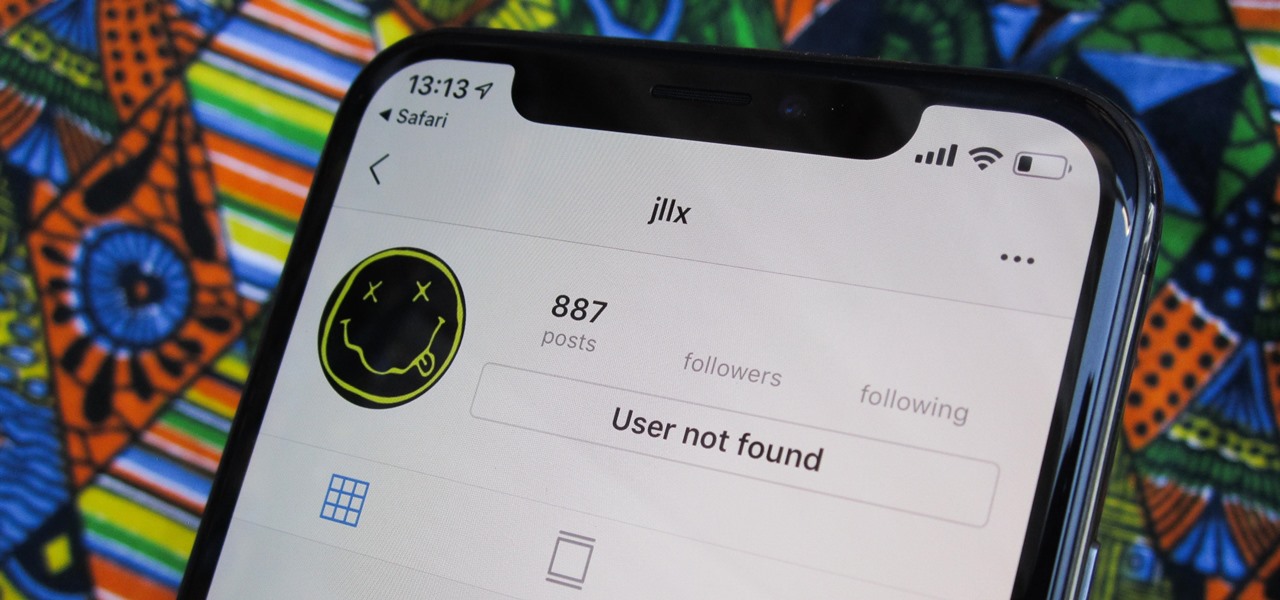
When you don't want certain friends viewing your account or just need to take a break from social media, Instagram lets you do so. While you can completely delete your Instagram account, then start over when you're ready again, it makes much more sense to just disable your account temporarily. Doing so will hide your profile, photos, comments, and likes from everyone, including your friends.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

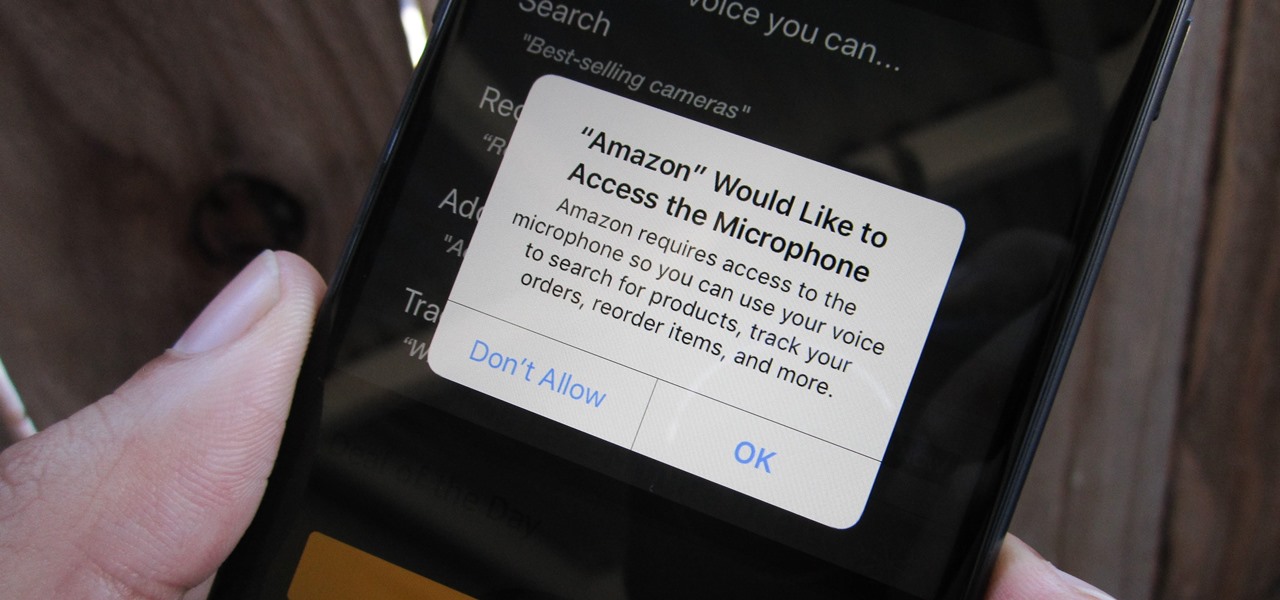
Any app on your iPhone could potentially listen in on your conversations and use that information to target you with tailored ads. Although most companies, including Facebook and Apple, have come out and vehemently denied these claims of spying on consumers, who's to say they're telling the truth? The only way to be sure you're safe is to take matters into your own hands.

As great as passcode and biometric security features like Face ID are for preventing unwanted access, they aren't needed 100% of the time. When you're at home with a locked door between you and anyone you wouldn't trust with your phone, they really only serve to slow you down. Android has long had a solution for this, but a new Cydia tweak has now brought a similar solution to iPhones.

If you're looking into buying shoes from DSW on Black Friday, then you can save an extra 20% — but only if you smile more.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

The "controversial" Pixel. No phone in the history of Google's Pixel lineup deserves this title more than the Pixel 3 XL. For some (including myself), the design is a welcome change that embodies the modern design of 2018 flagship phones. For others, it has an ugly huge display notch that destroys symmetry.

It wouldn't be iPhone season without a new controversy. Chargegate, Apple's latest PR nightmare, is the name being used for charging issues on some iPhone XS and XS Max devices. If you plug in your iPhone at night — or whenever — then wake up or come back later and see that your iPhone has even less battery power, you're affected. But there is a fix you can implement right now.

With iOS 12, iCloud Keychain has become a more useful password manager for your iPhone with strong password suggestions, password reuse auditing, and Siri support. However, before you jump ship from your current password manager, you should consider all the reasons why iCloud Keychain doesn't make sense as your primary password manager.

If you want the best two-factor authentication app out there, our pick is Authy. A close second is LastPass Authenticator. If neither of those is to your liking, try Duo Mobile or Microsoft Authenticator. But if you're fine with missing out on great features, then and only then should you look at using Google Authenticator.

Apple released the tenth iOS 12 developer beta unexpectedly Thursday afternoon, Aug. 23. The update comes only three days after the release of iOS 12 developer beta 9, a surprising move for Apple, even with the irregular releases the company has made in recent weeks.

Apple's testing a new app for iOS 12 called Shortcuts, and it has a lot of overlap with their existing Workflow app. So much overlap, in fact, that Workflow won't be sticking around for much longer.

Apple released the third beta of iOS 12 for developers on Tuesday, July 3. The update comes exactly two weeks after the release of the second developer beta, which introduced a variety of fixes as well as new issues, and just one week after the release of the public beta. Public beta testers received this iOS 12 update on Thursday, July 5, labeled as public beta 2.

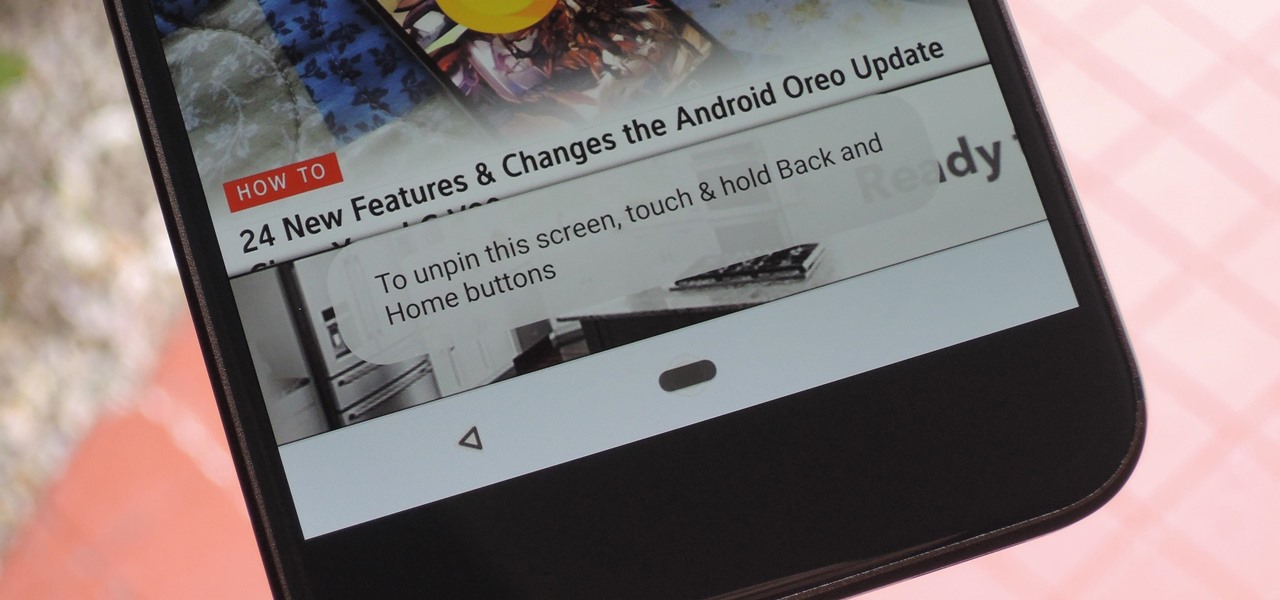
Screen pinning is a fairly unknown feature despite the fact that it's been around since 2014. It's a helpful security tool that limits access to your device to only one app — perfect for those times when someone asks to borrow your phone. While previous versions kept this feature exactly the same, Android 9.0 Pie's new multitasking UI changes the way it works.

Apple released the third beta for iOS 11.4 on Tuesday, May 1. This update comes exactly two weeks after the release of the second beta, which, in addition to adding a new wallpaper, fixed issues with AirPlay, Music, and Keychain. The only noticeable change in beta 3 is a fix for unresponsive 3D Touch.

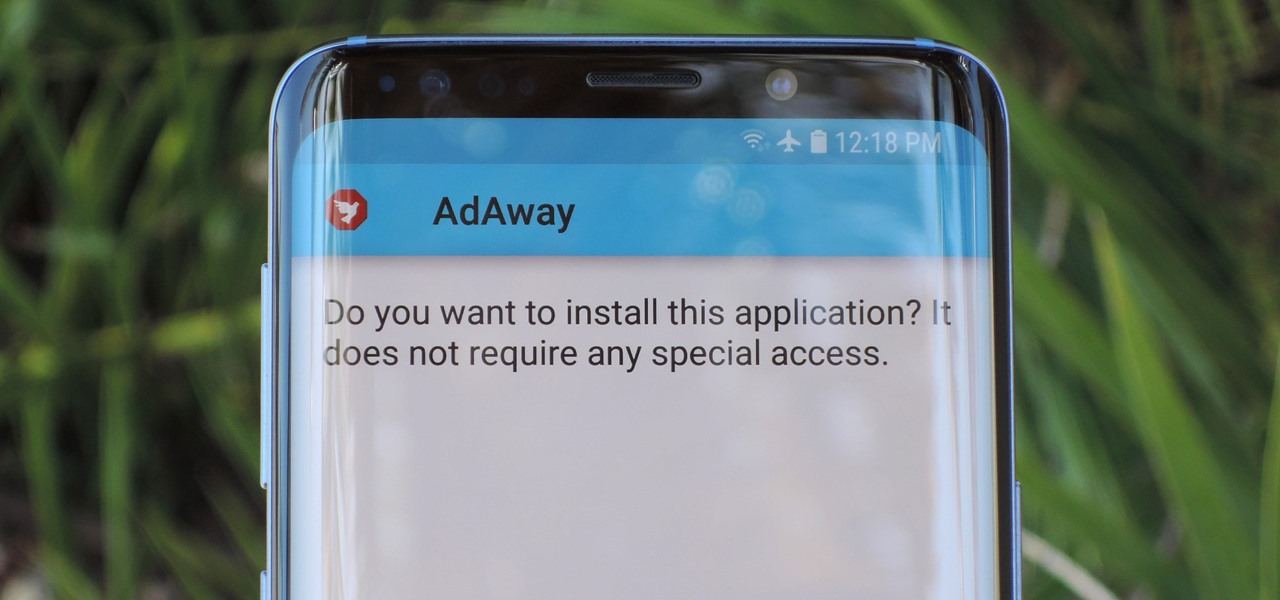
Starting with Android 8.0 Oreo, the process of sideloading apps has changed dramatically. Google removed the old "Unknown Sources" setting and replaced it with a permission that you have to grant to individual apps. It's really an interesting security feature.

If you've ever connected your iPhone to a computer before, you know iOS prompts you to "Trust" the computer and enter your passcode to confirm. According to Apple, trusted computers can "sync with your iOS device, create backups, and access your device's photos, videos, contacts, and other content." That's a lot of permissions to hand off, especially if the computer's not your main laptop or desktop.