Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.
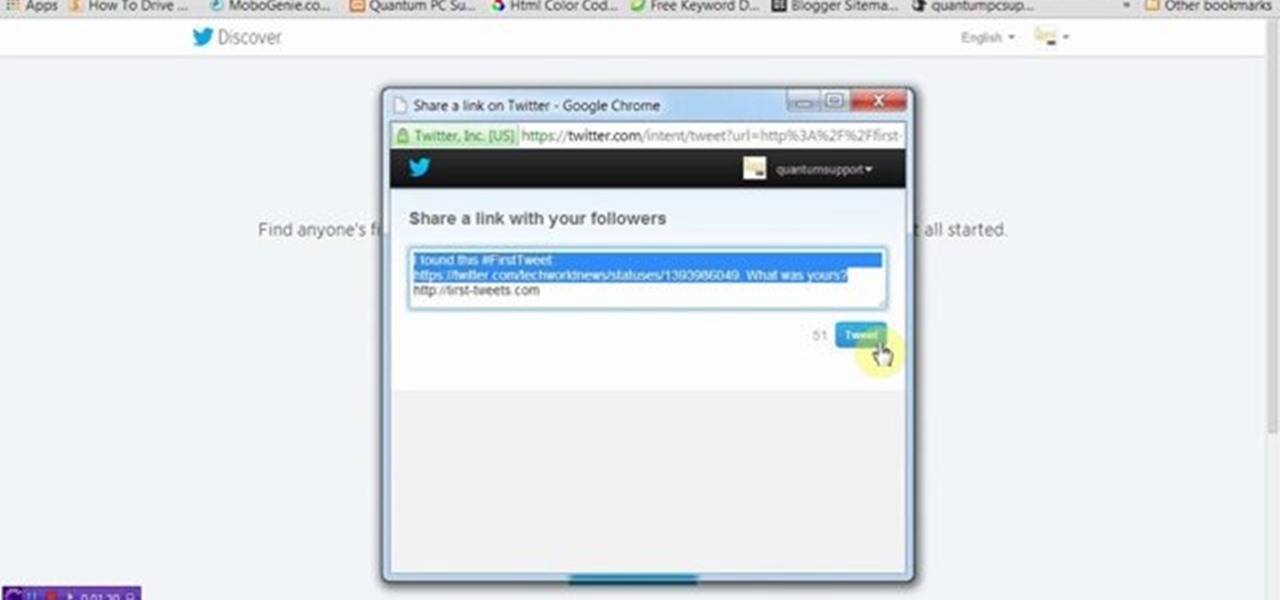
This tutorial video will show you how to find first tweet of any user in Twitter. You have to type first-tweets.com in address bar of your browser. The site will be redirected to discover.twitter.com/first-tweet page. Just type any user name and twitter will show the first twit of that user. Watch the video and try it yourself.

When it's most important for me to browse the web incognito, I always seem to forget to enable private browsing. If that sounds like you, it's time you stop making that mistake for good. Manually deleting the cache and browser history is a thing of the past, and as it turns out, so is manually switching to incognito mode.
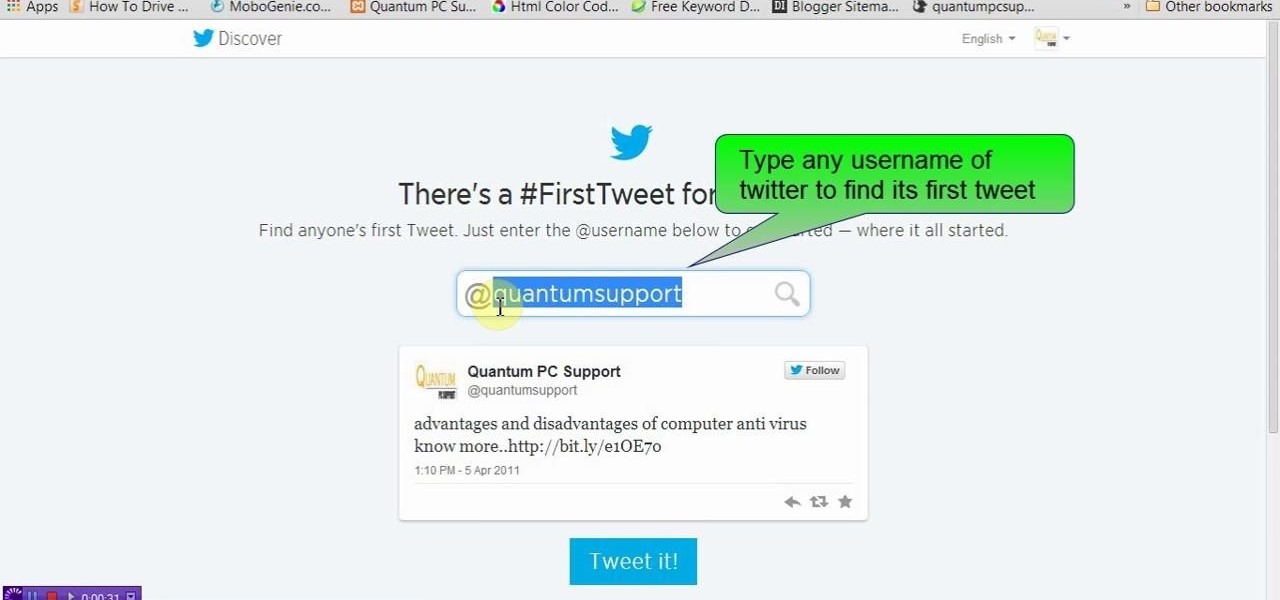
This video will show you how to see first twit of any user in twitter. You could type https://www.first-tweets.com in address bar and the site will be redirected to another place https://www.discover.twitter.com/first -tweet page. You have to enter the user name and twitter will fetch the first twit of that user. Watch the video and employ it yourself.

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.

There's a lot of personal information residing on your phone, possibly even more than on your computer, so it's only a matter of time before someone tries to access it.

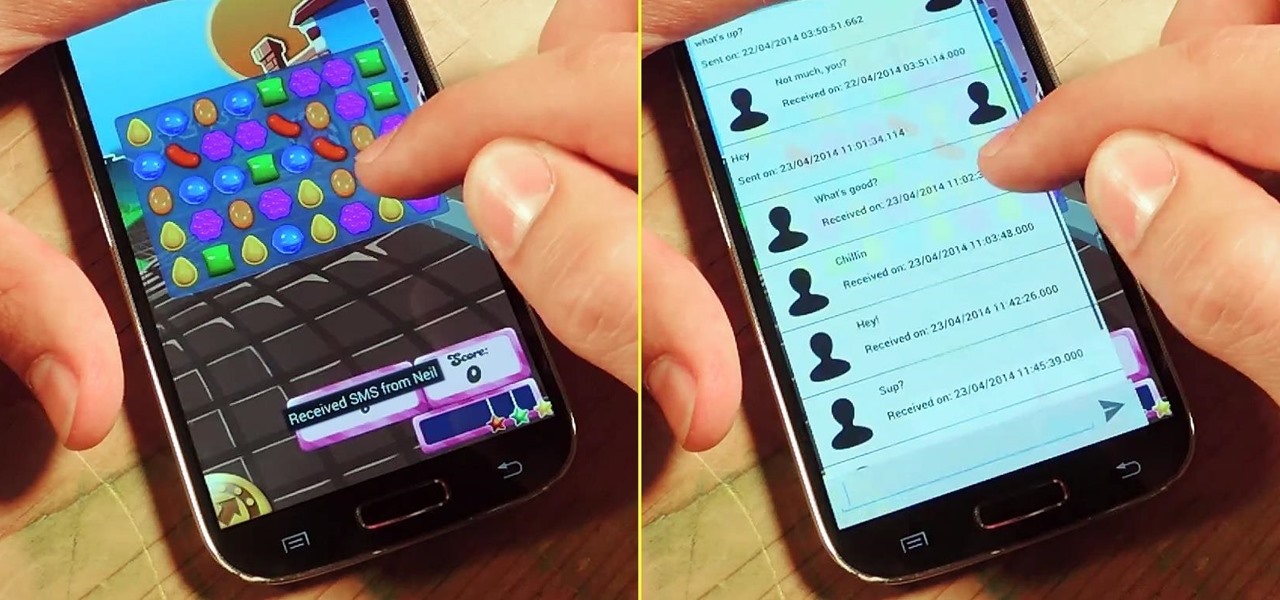
I'm a textaholic, as I've said many times before, but even textaholics forget to respond sometimes. When I'm watching a YouTube clip or devouring delicious snacks in Candy Crush Saga, I'll often ignore incoming texts and forget to respond later.

A long time ago, we recommended the Hover Zoom extension for Chrome as an easy way to blow up small image thumbnails without actually have to "click" on the images themselves. Over the past year, there have been reports that Hover Zoom now collects and sells your browsing data to third-party advertisers without your consent.

In spite of the degree of difficulty it is to install, CyanogenMod has steadily climbed the ladder to become one of the most popular third-party firmwares for Android devices.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

There are a ton of options available to Android users when it come to messaging, but the problem is that with all of these options, where is the go-to app? The one used by most people? The one that can offer a more unified approach?

I recently had my iPhone stolen at public park and did everything I could to locate it, but with Find My iPhone disabled (I know, what an idiot) and no exact address to give to the police, I had about a .00000001 percent chance of getting it back.

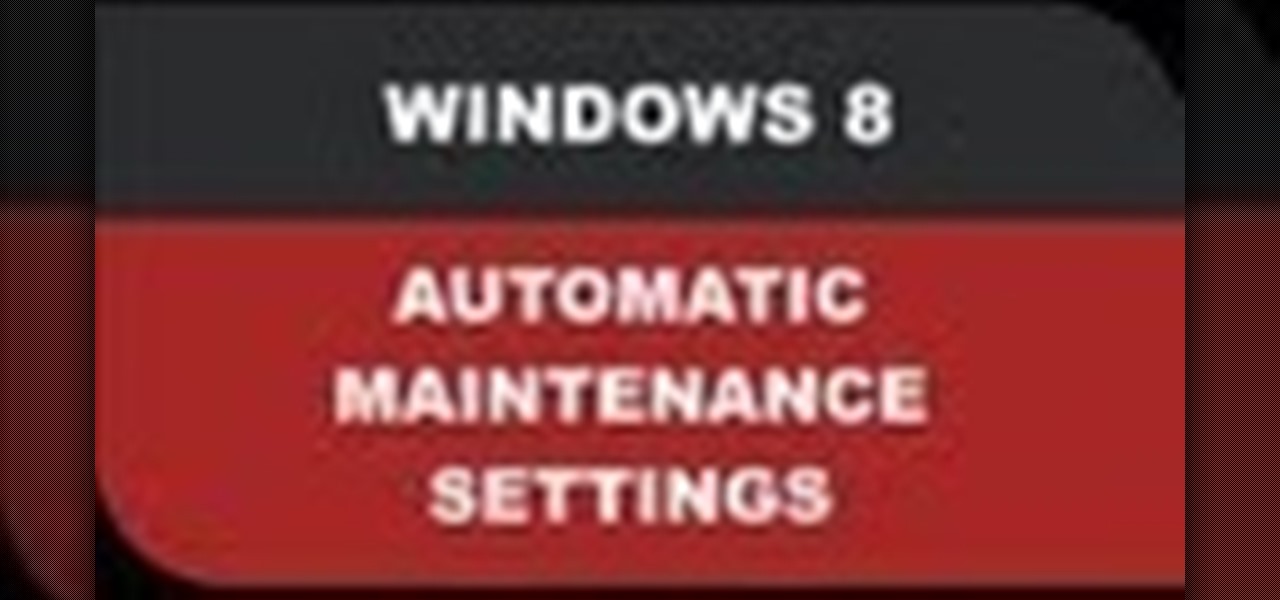
In this Windows 8 Tutorial I will show you how to adjust the automatic maintenance settings. The automatic maintenance settings deals with thing such as software updates, security scans and system diagnostics. If the settings in your automatic maintenance settings panel in Windows 8 are not set at a time your computer is on it want run the maintenance unless you set the option that to wake up your computer up at the scheduled maintenance time.

The U.S. Postal Service has been in trouble for quite some time. With more and more people choosing to go digital to take care of bills, legal documents, and pretty much all other forms of correspondence, they haven't exactly kept up with the times. I mean, let's be honest—when was the last time you sent snail mail?

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

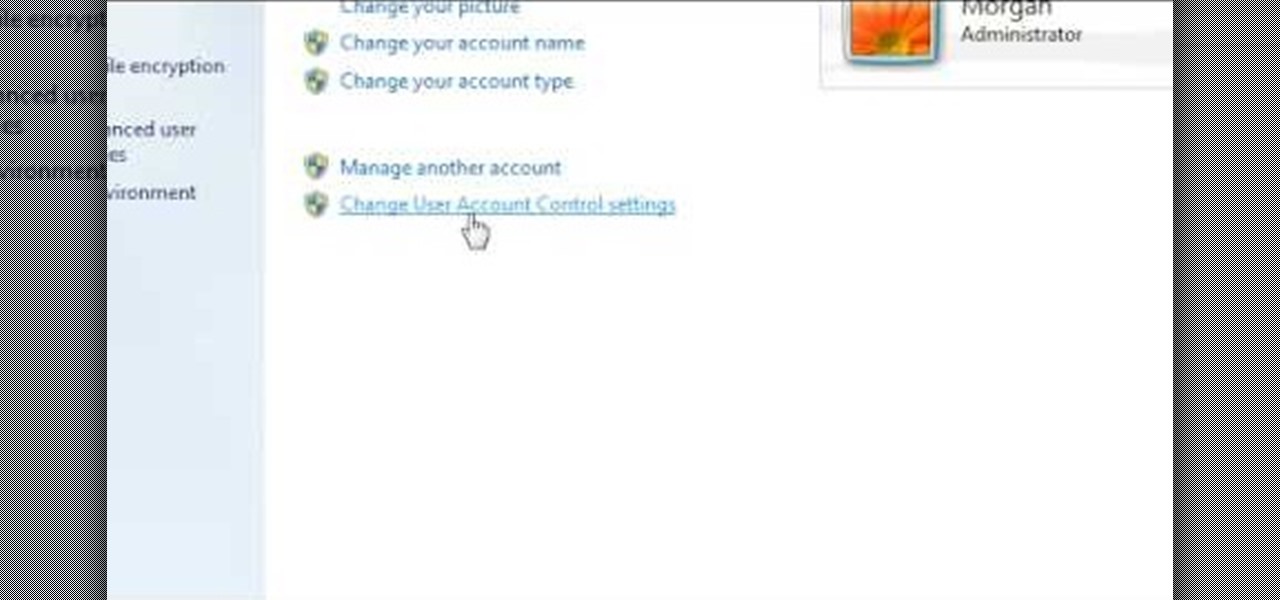
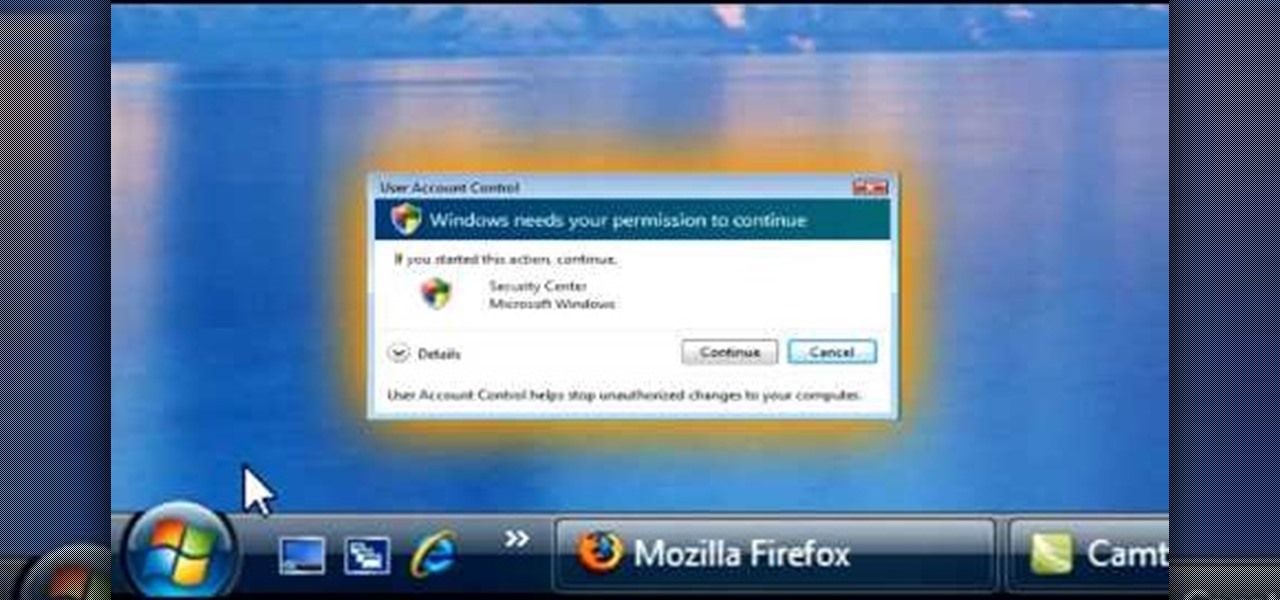
In this video, we learn how to turn off user account control (UAC) in Windows 7. First, go to your desktop and then the start menu. From here, go to the control menu and then user accounts. After this, go to change your user account control settings and a new window will pop up. From here, change the bar from the top to the bottom where it does not notify you, or wherever you want it to be that suits you the best. To finish, you will save this and then exit out of all the windows and your set...

Microsoft has released its latest rendition of the Windows operating system, Windows 7. Windows 7 succeeds Windows Vista and comes with many improvements and useful updates. To install the update one a personal computer running Windows, a backup of the user's personal files and data onto a detachable hard drive is recommended to prevent data loss during the update process. The ISO image of the Windows 7 OS is burned onto a DVD. A partition is optionally created on the user's computer to allow...

Revision3 Internet Television and Tekzilla Daily with Veronica Belmont demonstrate how to unlock Vista's super user mode. First, open the start menu and type CMD. Right click the command prompt and select the run as administrator option. Type the code net user administrator / active:yes. Hit enter. Your system should reply with the command completed successfully message. Then, the next time you restart your system, you'll see the administrator as an option in the welcome screen. If you use th...

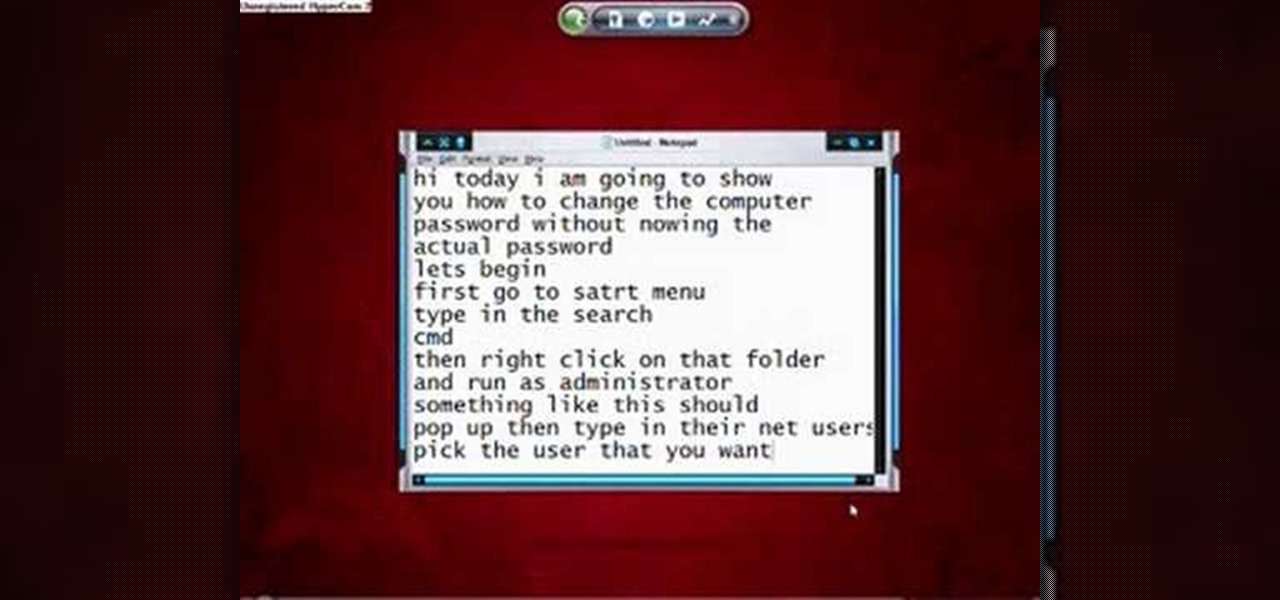
This video shows how to hack the computer password for Vista. We can change the computer password without knowing the actual password. First go to Start menu. Type in the Search "cmd". Then right click on that folder and run as administrator. Then we get a pop up. Type in their net users. Pick the user that we want to hack into. After picking the user type in net user the username and then * . After typing this hit enter key and it should say the command completed successfully and we have to ...

In this video tutorial, viewers learn how to negotiate with a credit card company. There are 3 main items that users can negotiate. The first item is the date of payment. Users are able arrange a more convenient date for payment. The second item is the annual fee. Users are able to work out a way to not have to pay an annual fee for using a credit card, which will help save money. The third item is the interest rate. Users can negotiate and try to lower the interest rate that they must pay. T...

In this video tutorial, viewers learn how to block certain users from seeing their Facebook account. Begin by logging into your account and go to your home page. Click on the Setting tab and select Privacy Settings. At the bottom of the page, under Block List, there will be a space for users to type in a persons name to block and click Block. Select the person from the list of people and click Block. This video will benefit those viewers who use Facebook, and would like to learn how to block ...

In this video tutorial, viewers learn how to clean the rear LCD on a camera. Begin by dry cleaning using Giottos Rocket Blower and nylon fine brush. Users will also need a isopropyl rubbing alcohol and microfiber cloth. Users may also need gloves to protect their hands from the alcohol. Begin by blowing off any dust and brush it with the brush. Now users will be wet cleaning using the isopropyl alcohol and microfiber cloth. Users are advised to clean weekly. This video will benefit those view...

1. To disable the UAC (User Account Controls), first click start button and type "msconfig" into the start search text box.

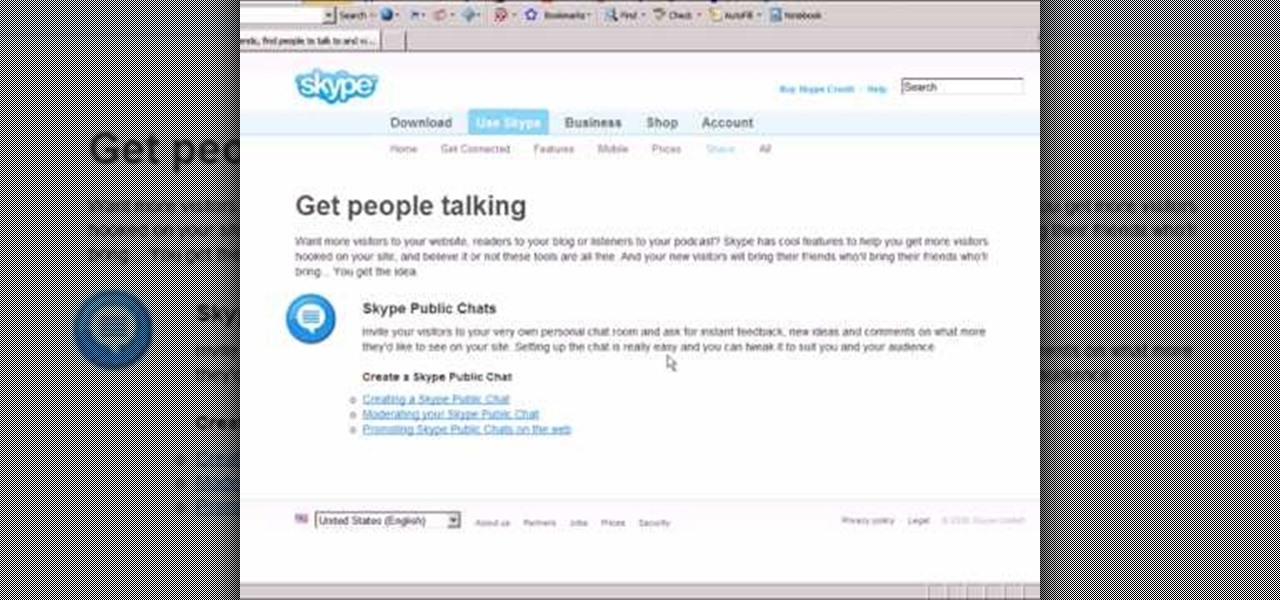
In this video tutorial, viewers learn how to use Skype. Skype is a software application that allows users to make voice calls over the Internet. It is very similar to MSN messenger. It allows users to communicate through instant messaging, voice chat or have a video conference. Users are able to communicate with others anywhere in the world who also have Skype. It is a free program. Users will need to make an account and download the program. This video is very descriptive and clearly explain...

This video was made to help users with disabilities use Windows XP more efficiently in their lives. Starting with entering the control panel the and clicking on the accessibility options the user will have an array of options to help customize their settings to their needs. The demonstrator showed that sticky keys are for those who have a difficult time holding down buttons at once for functions. The filter key eliminates double strokes for certain keys so you would need to hold down a key to...

In this video tutorial, viewers will learn how to make homemade beef jerky. Users will need meat in freezer for 20 minutes and a knife. It’s important to cut off the fat. Cut the meat into thin strips (like beef jerky). Users can press down on meat to make it thinner. Users may decide to add some flavoring and spices. Put the meat strips into a smoker grill. Users may also choose flavor of smoker wood to enhance flavor. Start the smoker and wait for 3-4 hours. This video will benefit those vi...

TheCondowit shows you how to put an SNES emulator on your R4/M3 card. The user says that the first thing you want to do is goto SNEmulDS homepage then scroll down when you get there and goto the green text. Next the user tells you to click on the R4DS / M3 Simply. The user then walks you through some more steps then shows you a live demonstration of the emulator in action to confirm that it works. After following all the steps the user provides, you should be able to put an SNES emulator onto...

This video tutorial shows you how to turn off USER ACCOUNT CONTROL in Windows 7. Step 1 : Go to START and select CONTROL PANEL .

OK, so visitors are coming to your website and they're even leaving comments! Now, with some simple PHP array programming you can find out what browser and OS they're using. This tutorial shows you how to create a simple and efficient user agent sniff script to get the information you want. Sniff, sniff. Is that Chrome running on OS X I smell?

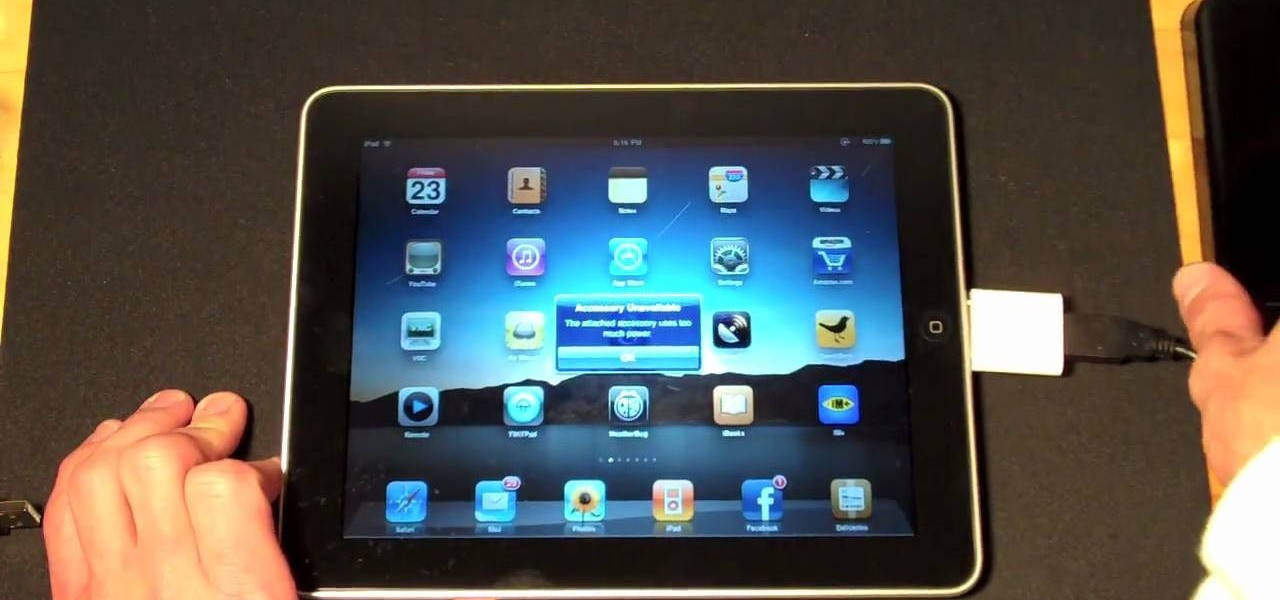
In this clip, you'll learn how to use external USB-powered peripherals with an iPad. Whether you're the proud owner of an Apple iPad or perhaps just considering picking one up, you're sure to benefit from this free video tutorial. For more information, including a detailed overview, watch this iPad user's guide.

In this clip, you'll learn how to prepare and format a USB thumb drive for use with an Apple iPad. Whether you're the proud owner of an Apple iPad or perhaps just considering picking one up, you're sure to benefit from this free video tutorial. For more information, including a detailed overview, watch this iPad user's guide.

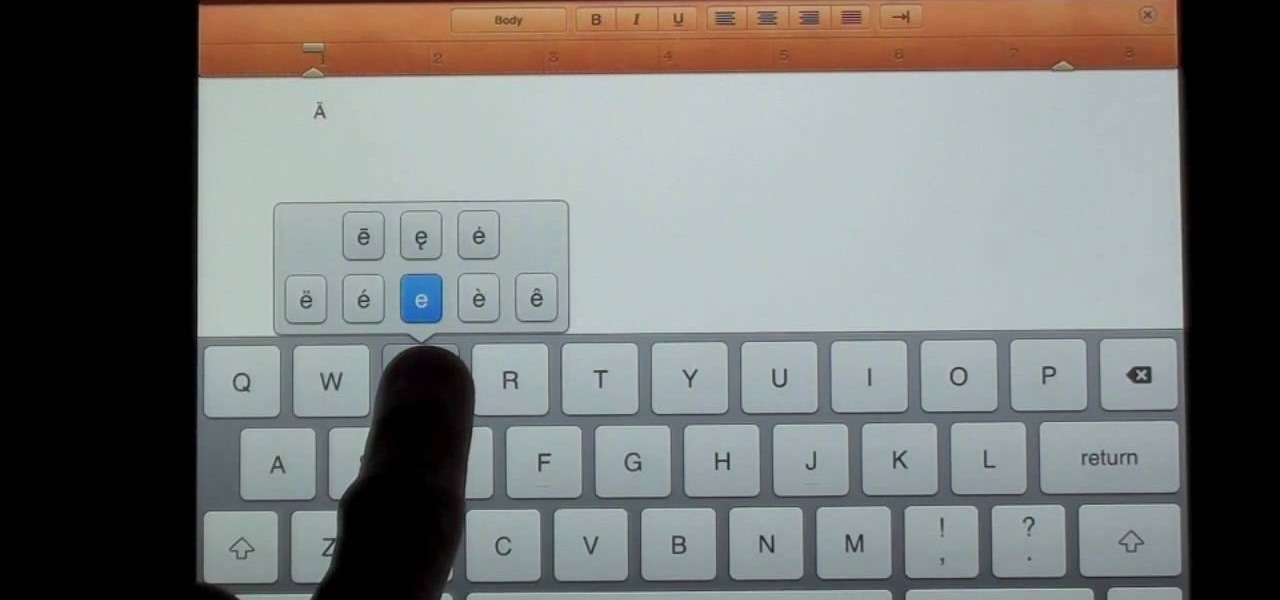
In this clip, learn how to access and use hidden and advanced functions on the iPad keyboard. Whether you're the proud owner of an Apple iPad or perhaps just considering picking one up, you're sure to benefit from this free video tutorial. For more information, including a detailed overview, watch this iPad user's guide.

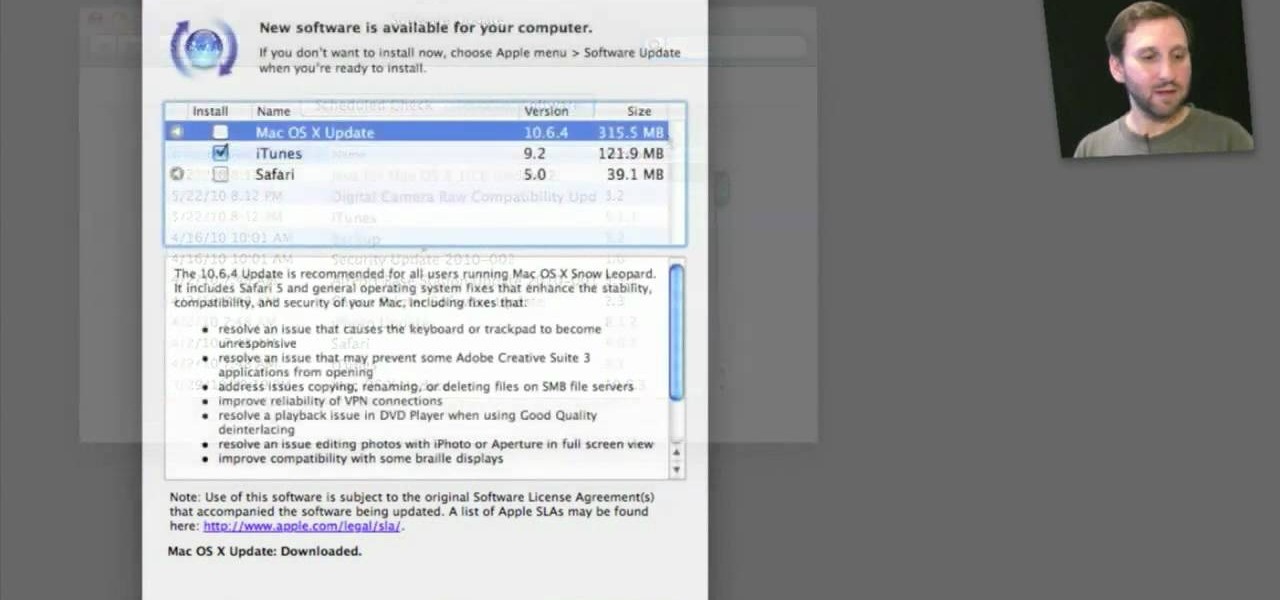
Need a primer on how to use the Software Update feature within all versions of Mac OS X? This Mac user's guide from the folks at Mac Most provides just that. For more information, including detailed, step-by-step instructions, and to get started automatically updating your software and OS with the Software Feature app, watch this video guide.

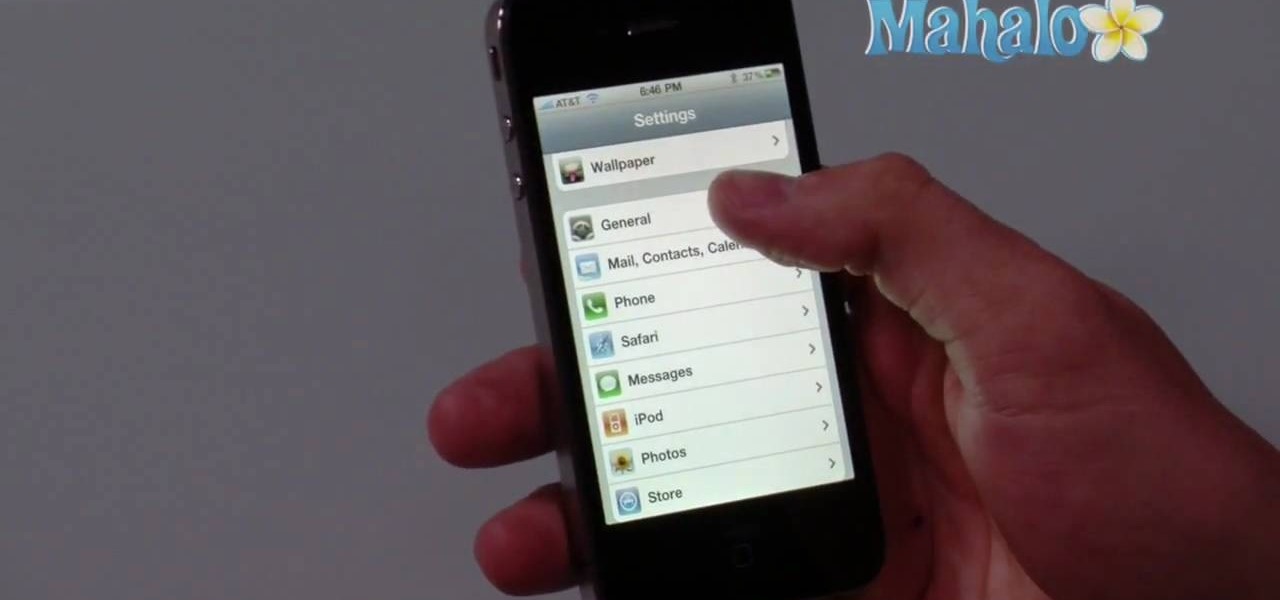
Want to use something other than Google as your default search engine? In this quick iPhone 4 user's guide, you'll learn how to change the phone's default search engine. Whether you're the proud owner of an Apple iPhone 4 or perhaps just considering picking one up, you're sure to benefit from this free video tutorial. For more information, including complete, step-by-step instructions, take a look.

In this quick iPhone 4 user's guide, you'll learn how to associate images with people in your contact list. Whether you're the proud owner of an Apple iPhone 4 or perhaps just considering picking one up, you're sure to benefit from this free video tutorial. For more information, including complete, step-by-step instructions, take a look.

In this quick iPhone 4 user's guide, you'll learn how to customize the Spotlight search application. Whether you're the proud owner of an Apple iPhone 4 or perhaps just considering picking one up, you're sure to benefit from this free video tutorial. For more information, including complete, step-by-step instructions, take a look.

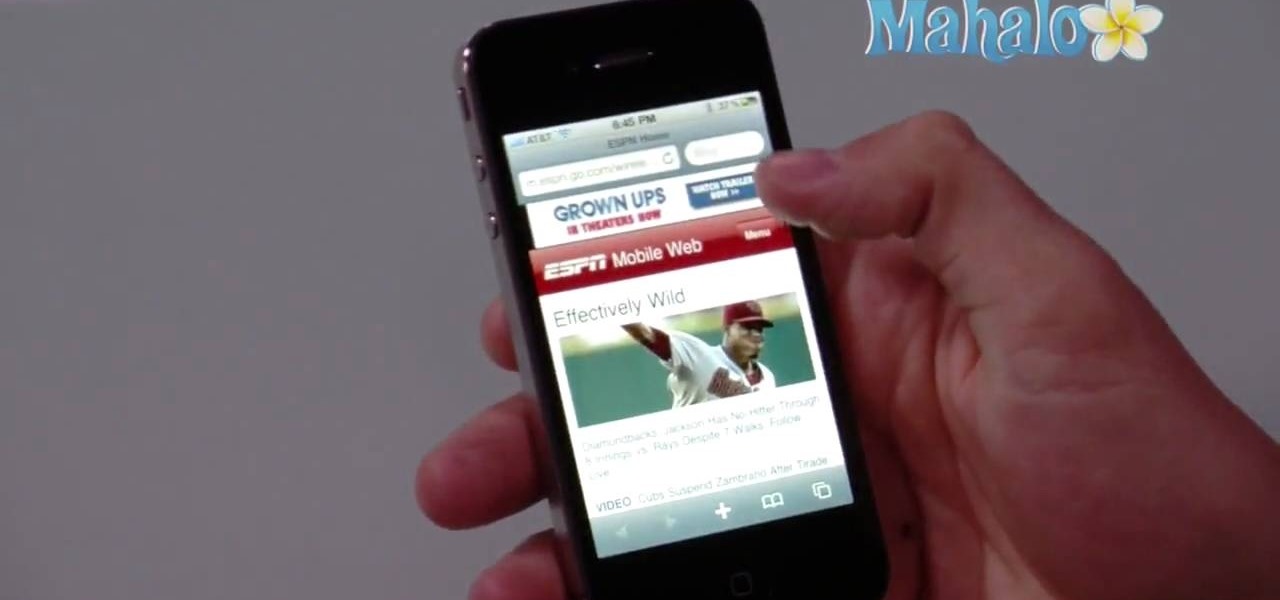
In this clip, you'll see how to use an iPhone 4G or 3G while making a phone call. Whether you're the proud owner of an Apple iPhone or perhaps just considering picking one up, you're sure to benefit from this free video tutorial. For more information, including a detailed overview, watch this iPhone user's guide.