Did you know that you can use a USB flash drive to speed up a sluggish Windows XP computer? It's easy! So easy, in fact, that this free home computing how-to can present a complete (and somewhat talky) overview of the process in just over a minute's time. For specifics, and to get started speeding up your own Windows Vista computer, watch this PC user's guide.
Misplace your Microsoft Windows Vista Recycle Bin? Looking for instructions on how to replace it? It's easy! So easy, in fact, that this free home computing how-to can present a complete (and somewhat talky) overview of the process in just under a minute's time. For specifics, and to recover your own Vista Recycle Bin, watch this PC user's guide.

Want to speed up a Microsoft Windows Vista PC? Have a USB drive? This PC user's guide from CNET TV demonstrates how to take advantage of Windows Vista's Readyboost feature to convert your flash drive into extra virtual ram for your computer. For specifics, and to get started speeding up your own sluggish Vista PC, watch this handy how-to.

In this video tutorial. viewers learn how to change the size of text and icons in a Windows 7 computer. Begin by clicking on the Start menu and open Control Panel. In the Control Panel window, click on Appearance and Personalization. Then click on Display. Now users are able to select the size of text and icons to Smaller - 100%(default), Medium - 125% and Larger - 150%. If users select one of the larger sizes, some of the items will not fit on the screen. Once users have select the setting, ...

In this video tutorial, viewers learn how to do math with an ice cube tray. Users will need a ice cube tray and counting coins. Users can also substitute the coins for any kind of small counting item that will fit into the tray. There are several ways for the child to do math with the tray such as the teacher directed activity where the teacher gives out an amount of a number and the child would have to count that much using the tray. Users can also use flash cards to solve numbers and simple...
Twitter is a powerful social networking website which can be used to update you friends on what you are doing. To send different messages through twitter you will need a twitter account. Twitter account can be registered for free. Log in to your twitter account and go to your home page. There is a text box provided at the top with the text 'What are you doing?'. Enter the message you want in the text box provided. Click update and this message will be shown to all the people that are followin...

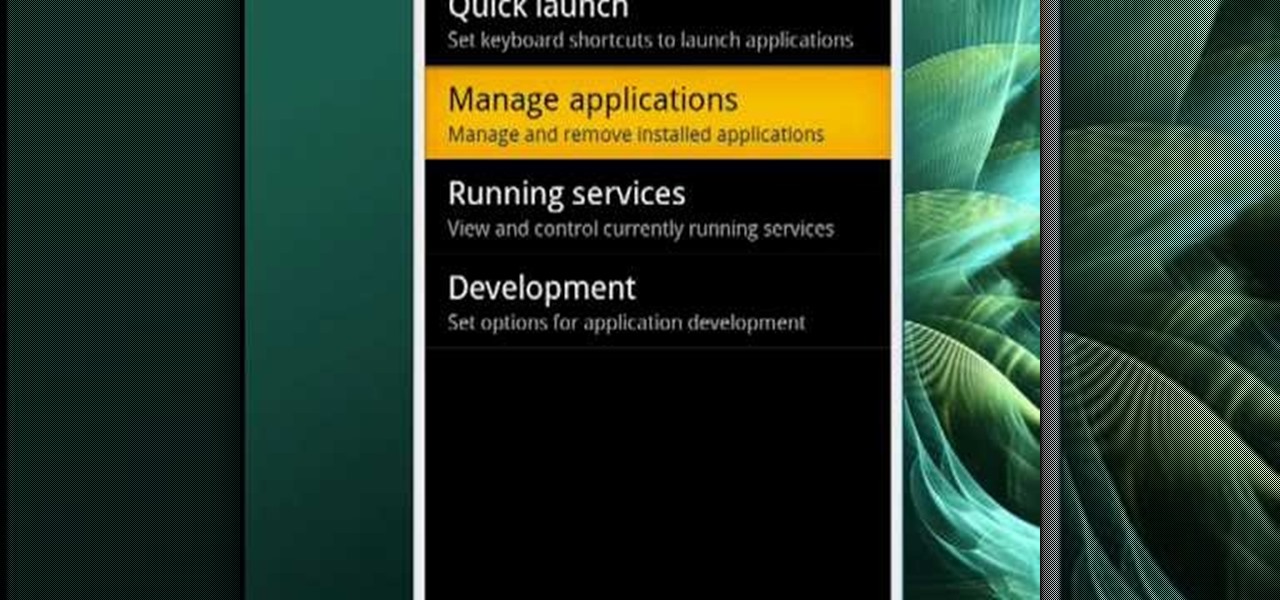
In this video tutorial, viewers learn how to uninstall the program on an Android phone. Begin by clicking on Settings and select Applications. Click on Manage applications. Now users will be revealed a list of all the applications that are installed on the phone. Simply scroll through the applications and select the unwanted application(s). Users will now see the information about the application, click on Uninstall. Now click OK and click OK again when the application is finished uninstallin...

In this video tutorial, viewers learn how to perform hanging knee ups. This exercise targets the abdominal muscles. Users will need to use a smith rack for this exercise. Begin by hanging on the top of the smith rack. Users should have a bar behind the rack that will support the back area. While hanging, users will point the chin down and bring the knees up. Then raise the chin up and bring knees down. Continue performing this movement in a series of sets and repetitions. This video will bene...

If you are new to Trapster, and wish to help your fellow users by submitting a speed trap, check out this quick clip. In it, you will learn how to submit a trap to the application so everyone in your area gets an alert. This app depends on users helping other users, so stay informed and join the Trapster revolution.

Apple released the newest update for iPhone, iOS 14.5.1, today, Monday, May 3. The update (build number 18E212) is the first since iOS 14.5, which Apple made available one week earlier on Monday, April 26.

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

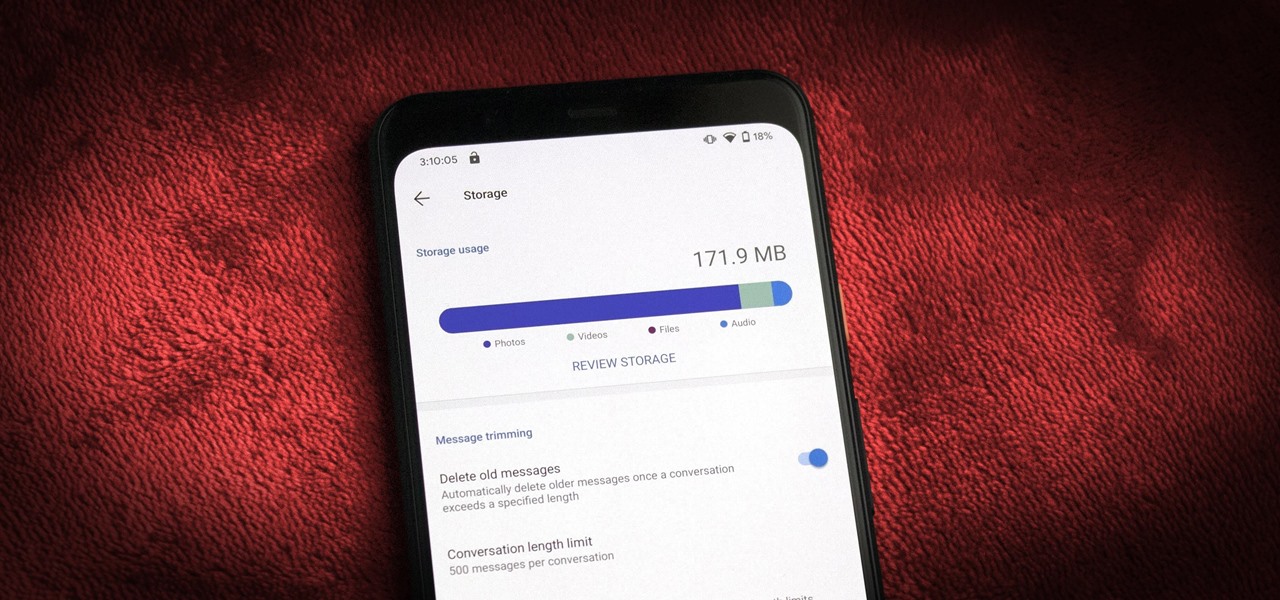
Thanks to backups, Signal conversations can span over multiple years and multiple phones. These archives can get rather large as you share photos, videos, and other files with friends. But between the other apps and large files on your phone, you might not be able to afford to keep all those messages.

The developer who gained notoriety for his What Disney Are You? augmented reality filter on Instagram is striking again while the iron is hot.

This time last year, Snap CEO Evan Spiegel and his company were faced with an erosion of its user base that cratered its stock price. This year, on the strength of Snapchat's AR camera effects, the company has reversed course. And that's why Spiegel tops the NR30, our annual list of the leaders in the AR industry.

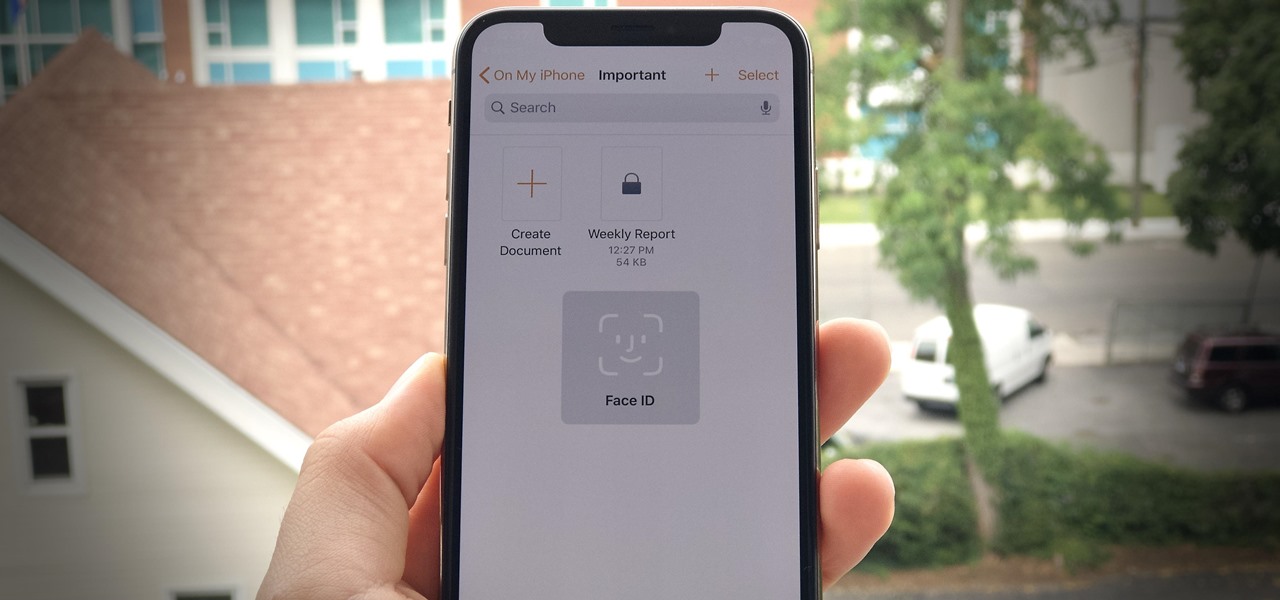
Your writing is just that — yours — so the work you do in Apple Pages should remain private until you choose to share it. Apple seems to share this sentiment. As another symbol of its dedication to user privacy and security, the company includes a feature in its word-processing app for iOS that allows you to lock documents behind a password, as well as with Face ID or Touch ID.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

It may take practice to get to Carnegie Hall, but a new mobile app gives the average iPhone or iPad owner the experience of walking on stage with a live orchestra.

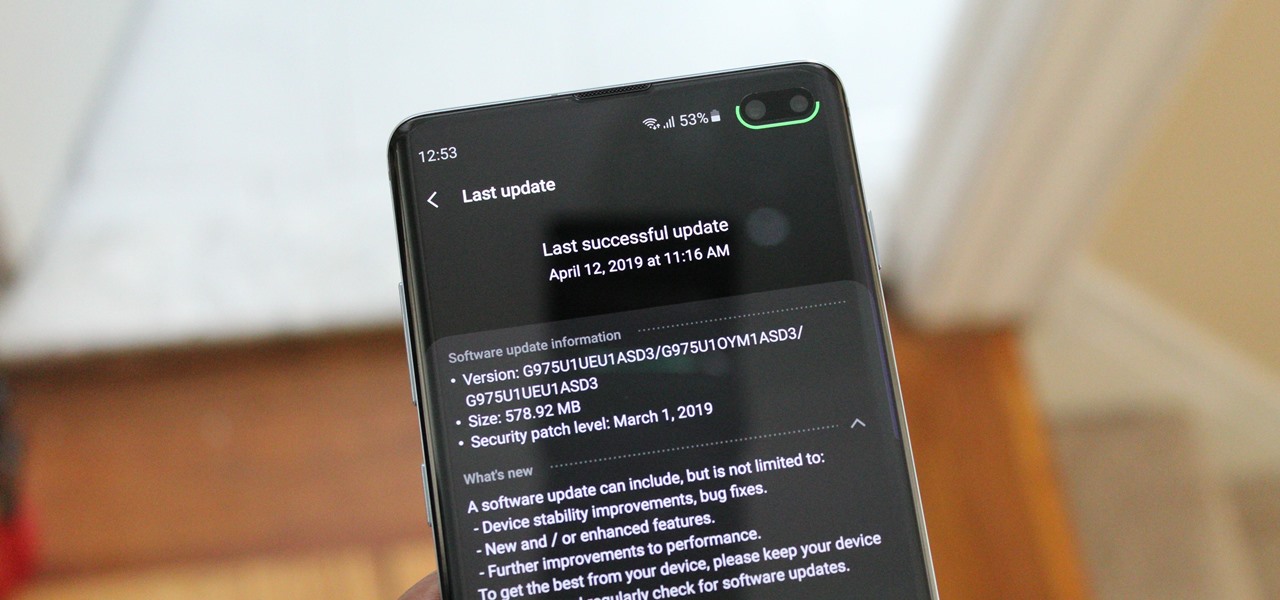
The Galaxy S10 is one of the best phones in years from world's largest smartphone OEM. With its astonishing display, new UI, and top-tier cameras, there isn't much to complain about. The one major gripe we've had is the in-display fingerprint scanner and just how slow it is. Thanks to a recent update, it just got a whole lot faster.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

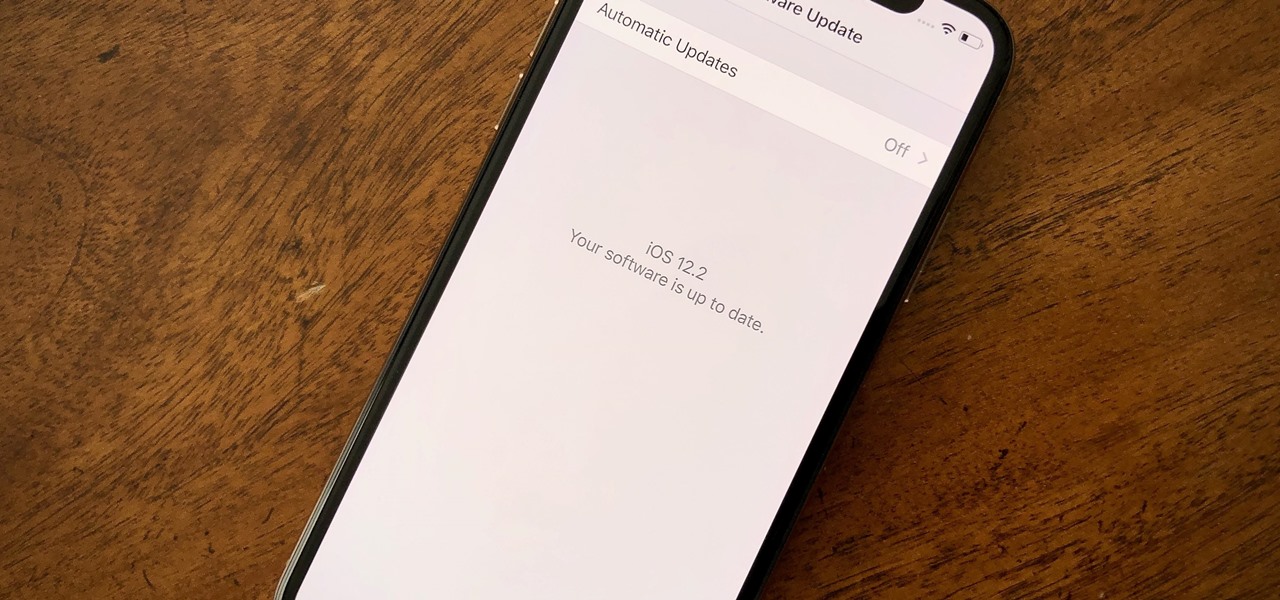
While developers received iOS 12.2 beta 3 on Feb. 19, public beta testers had to wait one extra day, following suit with previous iOS 12.2 beta releases. The third beta update includes fixes for Group FaceTime and the missing date on the lock screen, as well as a few tiny app updates.

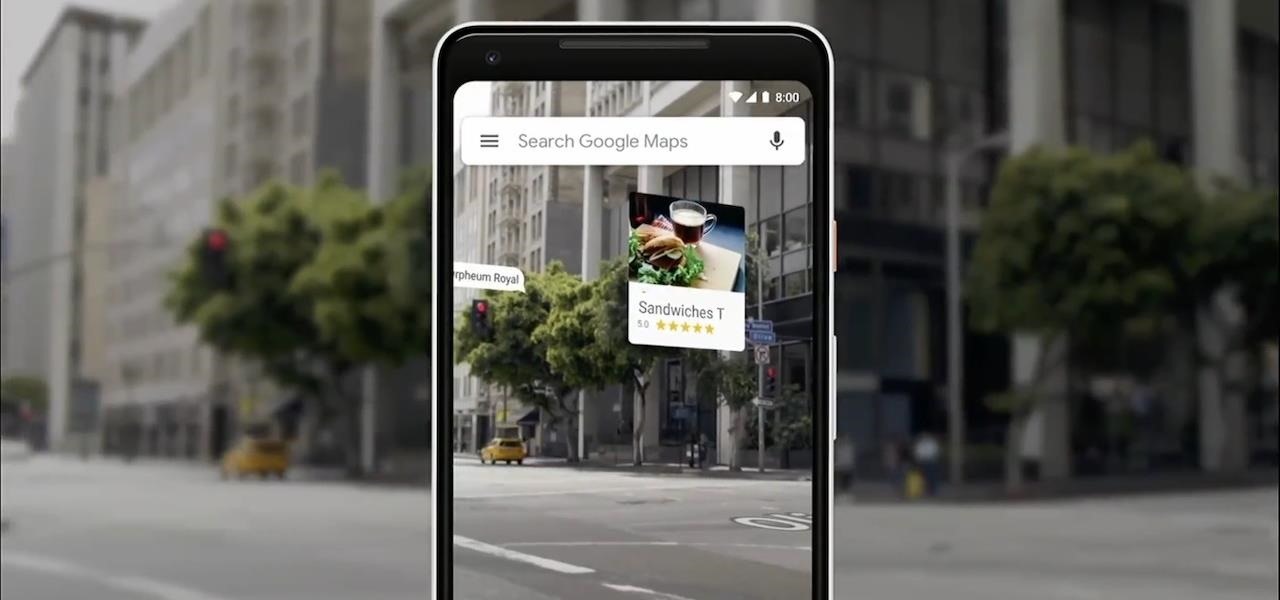
The augmented reality walking navigation mode for Google Maps appears to be closer to an upcoming release for the general public.

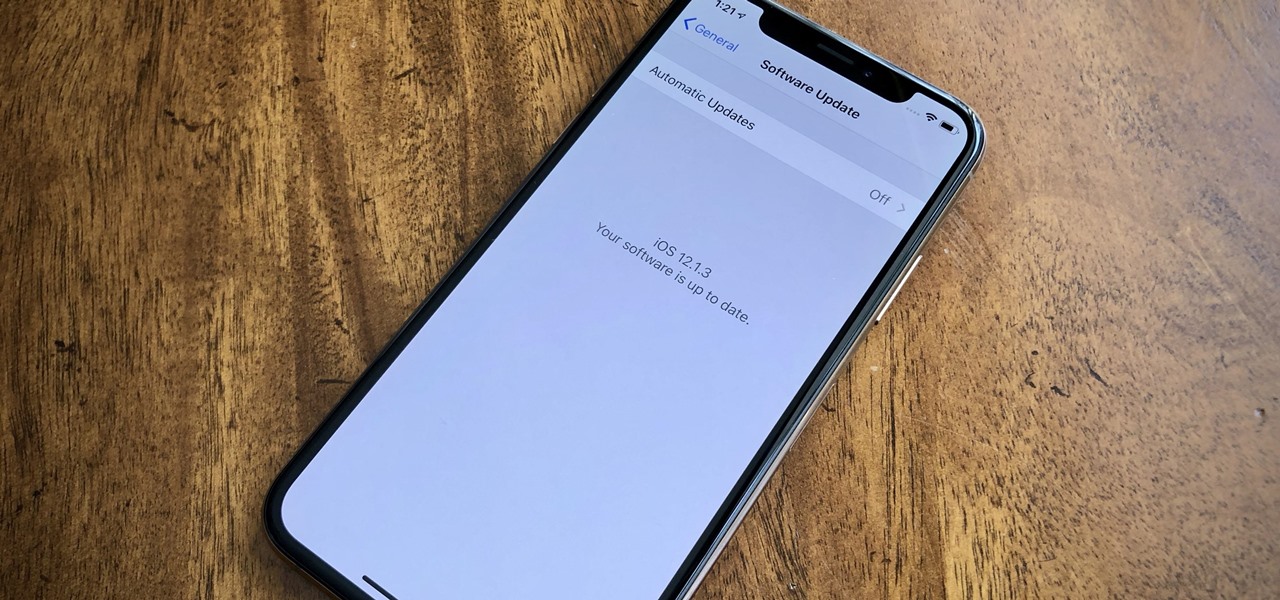
Just after a month of testing, iOS 12.1.3 has been released for iPhones. Like the previous iOS 12.1.2 update, there's not much to get excited about. There are no new features discovered yet, but there are a few fixes for issues with photos in Messages, imperfect pics when using the share sheet, and disconnecting CarPlay.

For the entirety of its existence, Snapchat has lived on mobile, but in its quest to lead the augmented reality industry, the company is now bringing those mobile AR experiences to desktops.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

In a surprise twist, Apple released iOS 12 public beta 8 to software testers on Thursday, Aug. 23, right alongside iOS 12 dev beta 10. The release comes as a bit of a shock, as the company released iOS 12 public beta 7 just three days earlier. The official build of iOS 12 now feels closer every day.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

One of the best parts of the BlackBerry KEYone and KEY2 is the iconic physical keyboard. There is one major downside, though: By default, the virtual keyboard appears on these devices even when typing on the physical keyboard. Luckily, there's a way to change that.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

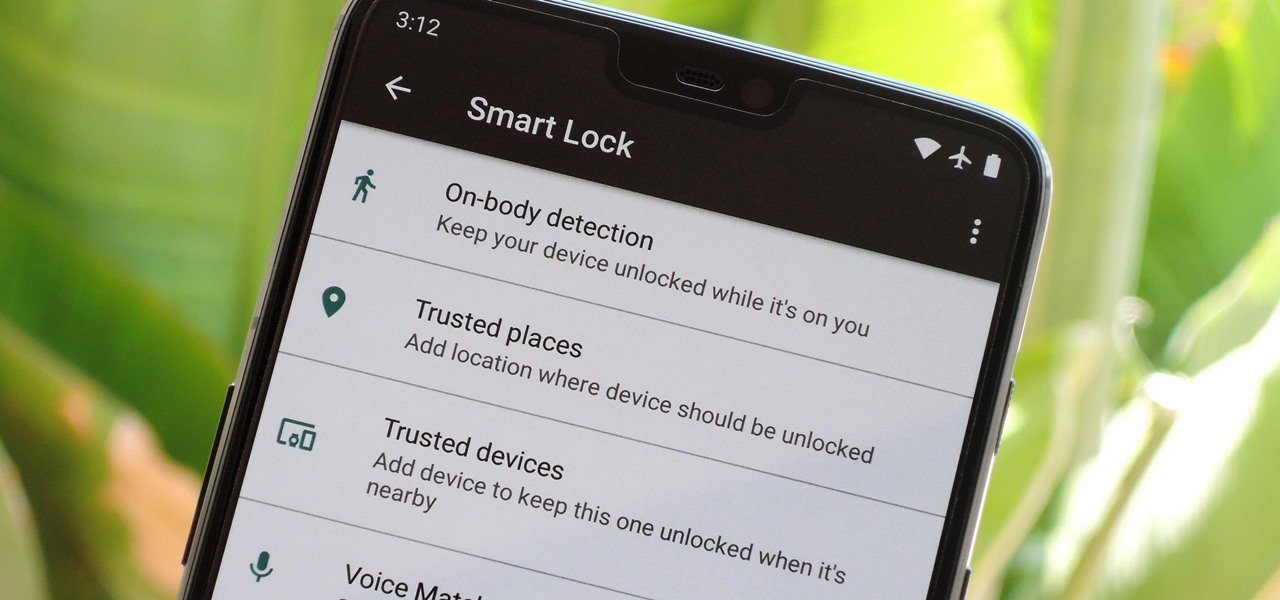
When it works, Android's Smart Lock feature is incredible. There's no need to enter your PIN when your phone "knows" it's in your hands — just unlock and go. But Smart Lock, particularly its Trusted Places feature, can be finicky sometimes.

Augmented reality avatars that mimic facial expressions are no longer the exclusive province of Animojis on the iPhone X or AR Emojis from Samsung. Camera app Snow has added its own alternative to Apple and Samsung's features, which it also calls AR Emoji, for iOS and Android.

When it comes to augmented reality apps, visually immersive experiences are plentiful, but audio experiences are somewhat underrepresented. A new app for iPhones and iPads seeks to shift the AR paradigm toward the latter.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

For social media platforms like Facebook, augmented reality represents a whole new art form with which users can express themselves online. Now, Facebook is giving those users a new brush.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

When you visit a website in Safari, it's most likely keeping tabs on your browsing activity. It could be keeping track directly, or its third-party content providers and advertisers can be spying on you. All three could happen simultaneously. This enables them to serve you content that's tailor-made for you, but it can also feel like an invasion of privacy.

A Swedish digital artist has developed an app for the iPhone X that creates mind-bending 3D illusions that correlate to the user's point of view.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

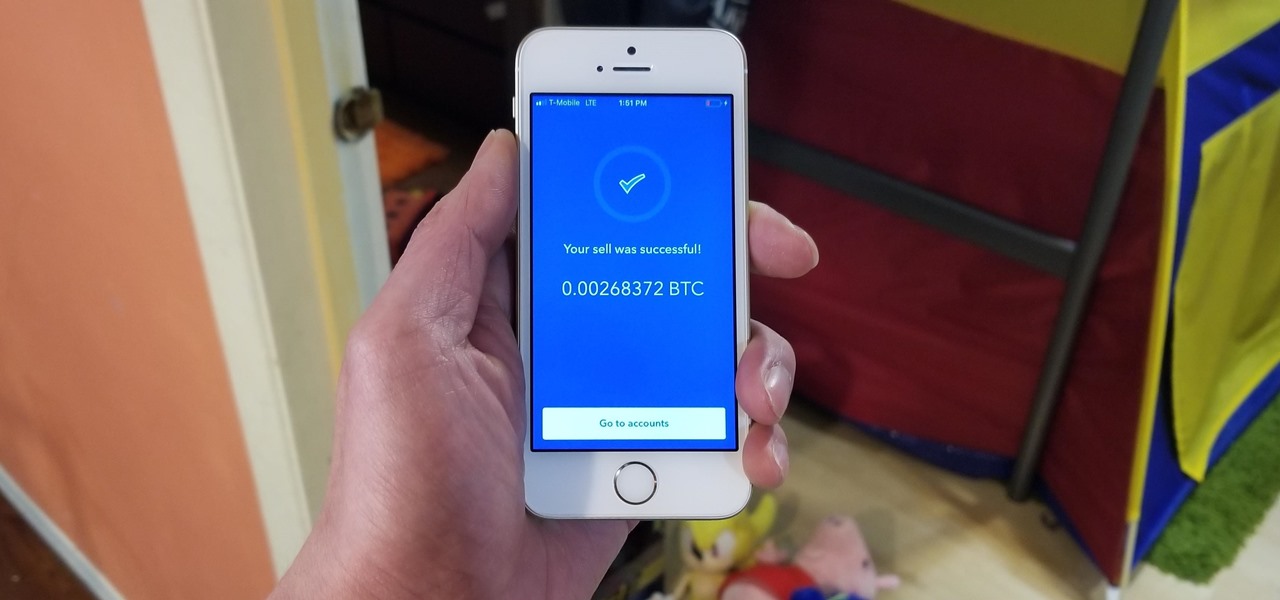
Coinbase has become the most popular mobile wallet app due in large part to its user-friendliness. The app takes the hassle out of buying and selling Bitcoin (BTC), Bitcoin Cash (BCH), Ethereum (ETH), and Litecoin (LTC), letting Android and iPhone users alike trade their favorite cryptocurrency in a few easy steps.