How To: Get VPN Connection
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Automator takes the work out of common repetitive tasks in Mac OS X. One of my least favorites is resizing images for the web, so I created a drag and drop action to quickly do it for me.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.
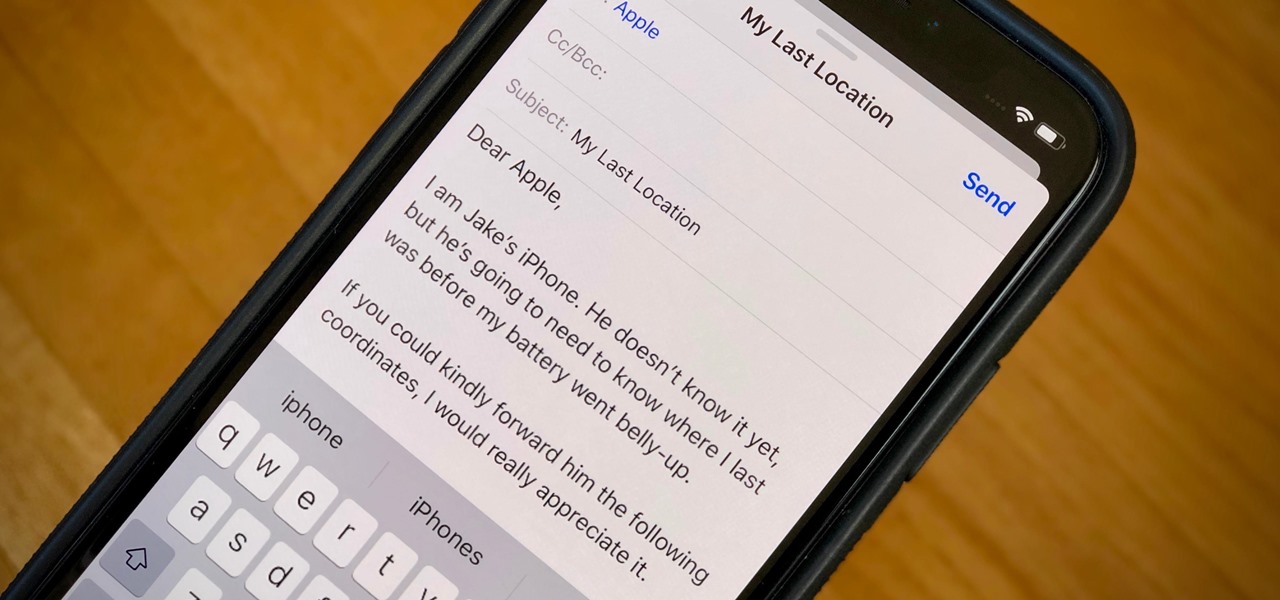
When your iPhone can't be found, Find My iPhone is a true lifesaver. When you use the feature, you can ping your iPhone and even see its current location on a real-time map. But what happens when your iPhone runs out of battery? Find My iPhone can't locate a dead iPhone, can it? You might be surprised to know it can, to a certain degree.

Welcome back, my amateur hackers! Many of you here are new to hacking. If so, I strongly recommend that each of you set up a "laboratory" to practice your hacks. Just like any discipline, you need to practice, practice, and practice some more before you take it out to the real world.

Android's permissions system is simple, transparent, and straightforward. When installing an app, you get a chance to review all of the permissions that the app has requested. These can range from accessing your location data to holding a "wakelock" in order to prevent your phone from entering sleep mode. But your only choice in this matter is to accept all requested permissions, or not install the app.

Keeping prying eyes off your device isn't always the easiest thing to do, especially once you lend somebody your phone to make a call. Seems that whenever someone is scrolling through your pictures or checking out your new phone, they always end up somewhere you don't want them be. You could always hover over their shoulder to make sure they're not getting into your texts or photos, but that isn't always possible.
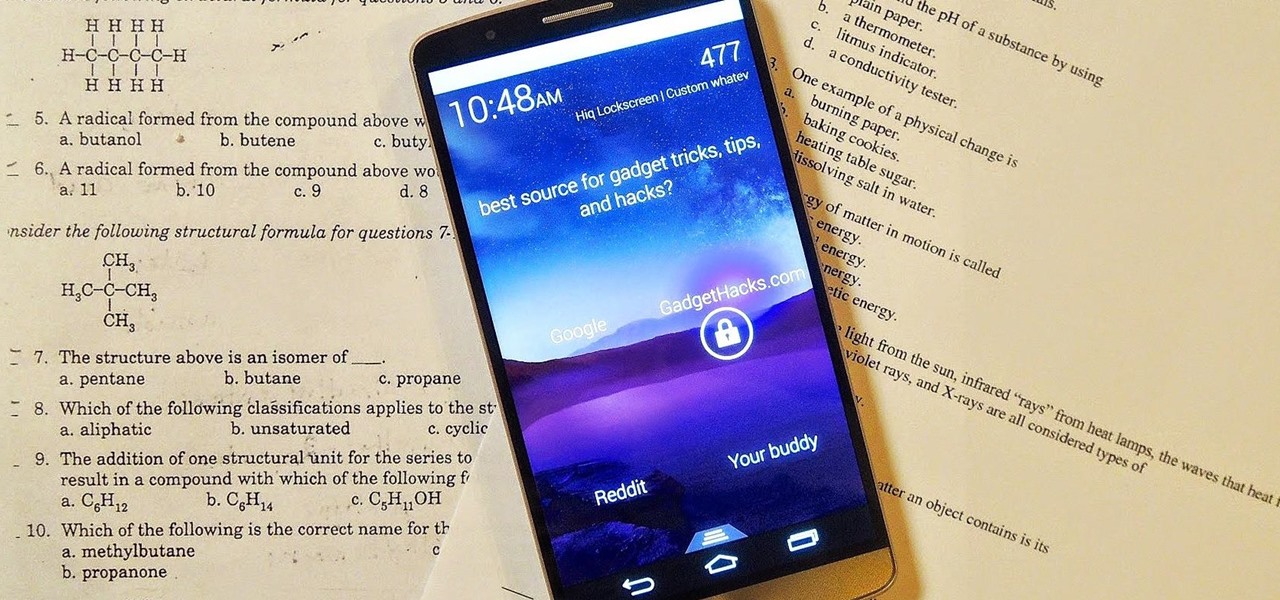
There are countless lock screens you can apply to your Android device, but very few offer more than just quick access to apps or advanced security functionality. Since you probably unlock your device a gazillion times every day, why not use this to your advantage and let it teach you something new?
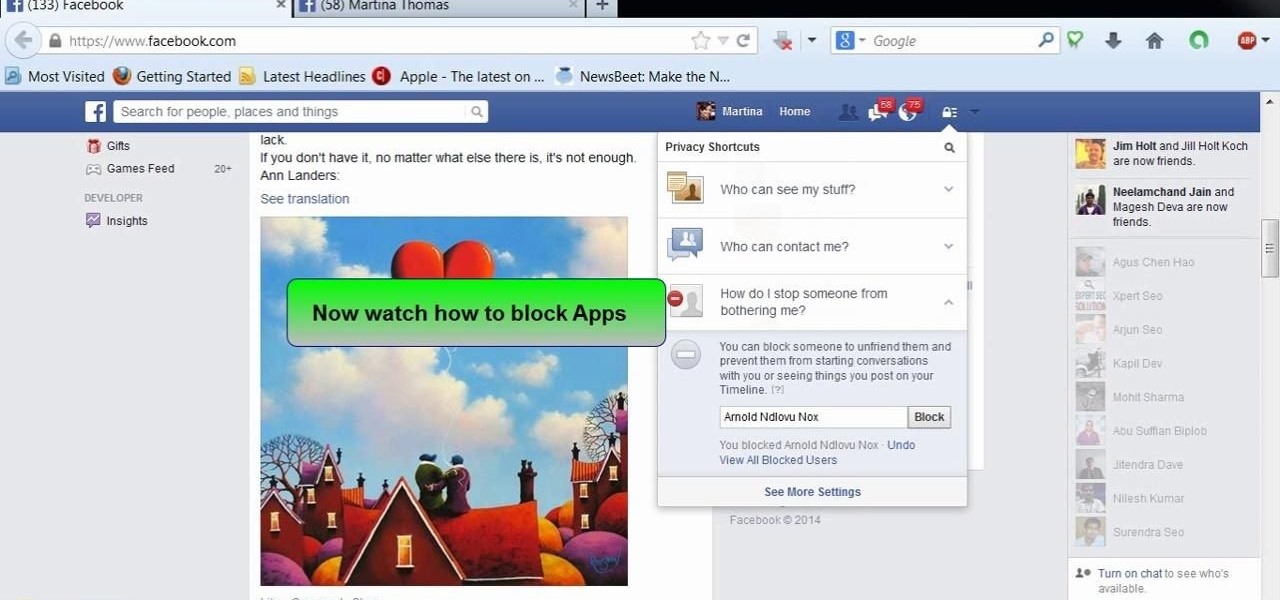
This video will show you how to block users and app invites on Facebook. You can also block apps from sending you notifications. If you accidentally blocked any user or app you intended you could unblock them easily. So please watch the video and employ the technique in your Facebook account.

Lock screen apps are a dime a dozen, but every now and then one pops up that defies expectations. We've already covered some good ones for the Samsung Galaxy S4, including Picture Password Lockscreen (which gives you secret unlock gestures), SlideLock (which improves notifications), and TimePIN (which gives you a more clever PIN).
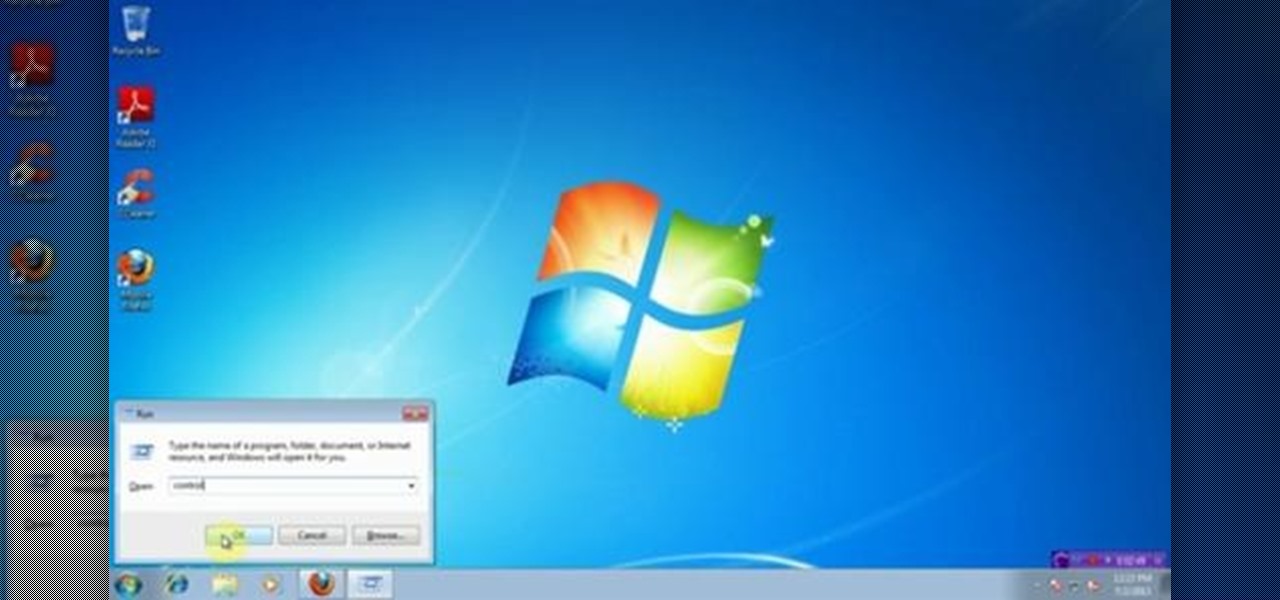
This video will help you how to disable user account in windows 7. This is very easy to employ. Watch the video and follow all the steps to disable user account in your PC.

Figuring out someone's password, pattern, or PIN isn't very difficult—simply watching over their shoulder or following the oil marks left across their screen is enough to figure them out and bypass whatever lock screen security they have.

Some of my favorites hacks are the ones that speed up the process of accessing my favorite and most-used apps. So, in this softModder guide, I'll be showing you a super fast way to open those apps straight from your Samsung Galaxy Note 3's lock screen.

If somebody really wants to gain access to your iPhone, they'll get in. Phone thieves (and mischievous friends) can easily figure out your passcode just from looking over your shoulder or tracing over the oily smudges on the screen. And if you're using popular passcodes, birthdays, and addresses on your iPhone, you might as well disable lock screen security entirely.

The lockout feature in iOS 7, which securely locks your device after a few incorrect passcode entries, can be a real pain in the ass sometimes.
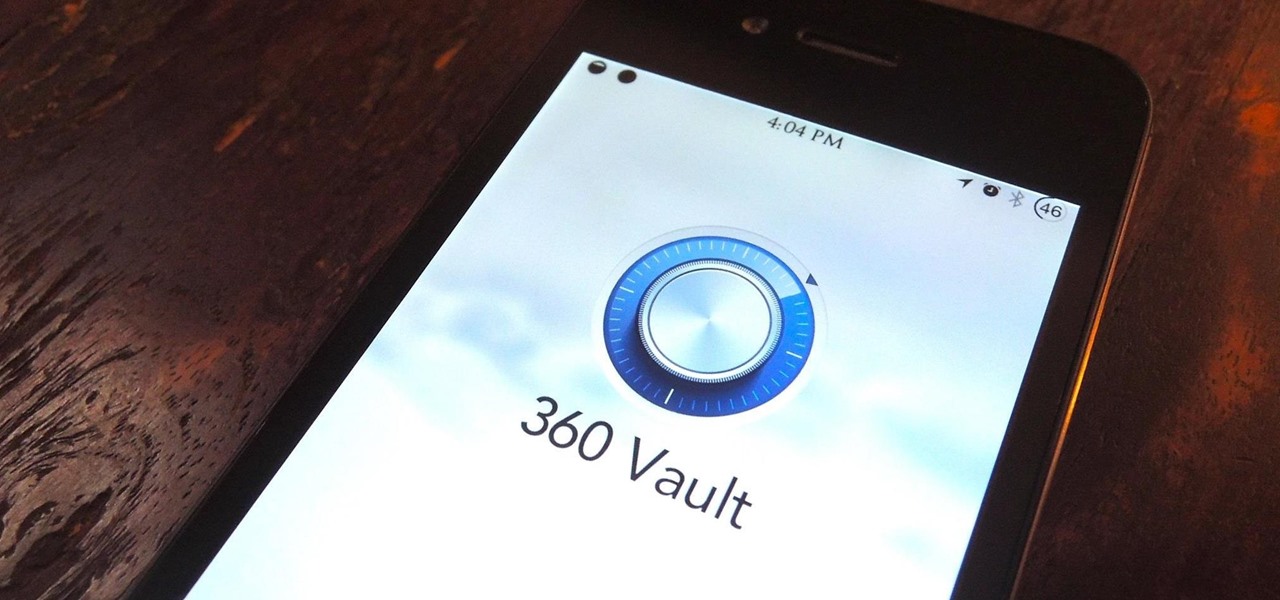
Let's be honest for a second; we all have sensitive material on our phones that we wouldn't want anyone else to ever see. Maybe it's to protect ourselves or someone else, or maybe it's none of your business why I don't want you to see pictures of my bachelor party. Regardless, sometimes we need to keep things hidden and safe.

Instagram recently released their new Instagram Direct messaging feature in their Android and iOS apps, which lets users share private photos and videos directly with individuals or groups of up to 15 users. However, there are no restrictions on who you can send private photos or videos to.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.
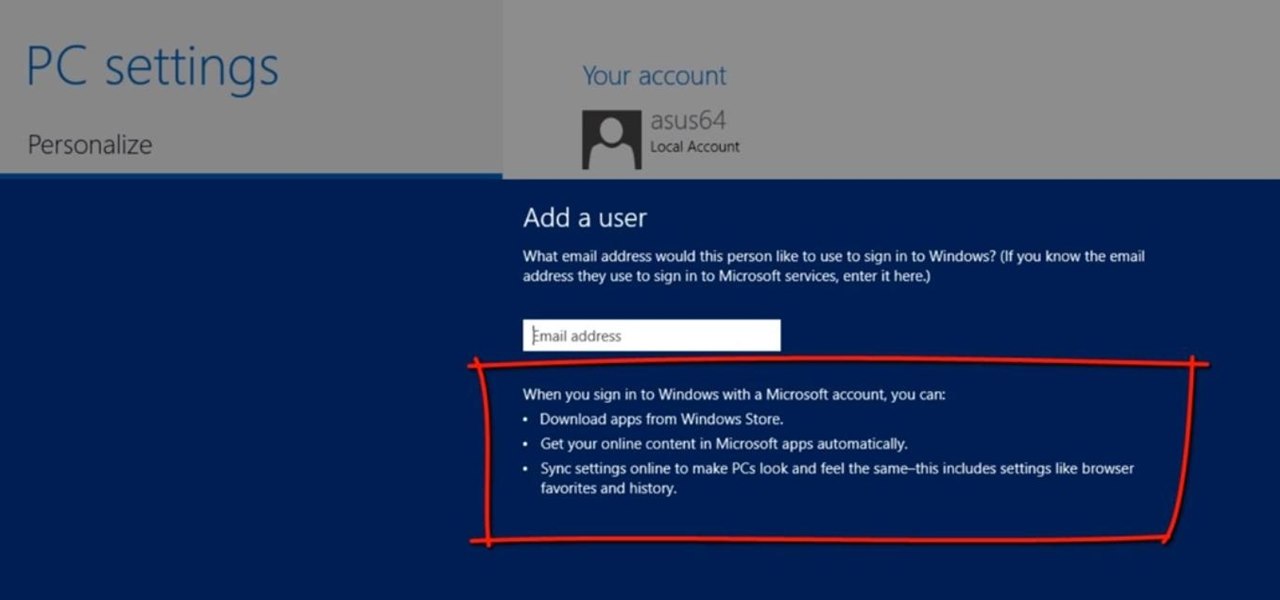
This Windows 8 tutorial will show you how to create a local user account on your PC. When you create a local user PC account, you will only have access to your account from that individual computer. A local Windows 8 user account uses a user name and password to login.

Samsung just concluded their live unveiling of the Samsung Galaxy S4! A more in-depth look can be found here.
How much time do you spend outside, as opposed to inside? Whether it's because you're working, studying or just have a bunch of errands to run, it may seem like the majority of your day is spent indoors. Ever wondered exactly how much time you spend indoors and outdoors? Now you can, thanks to this DIY Arduino-powered tracking device by Instructables user Gramsky.

Having all of your stuff in the cloud is super convenient if you want to access it on multiple devices, or if you want a backup in case it gets lost or wiped. The biggest downside with services like Dropbox, though, is security. With everything sitting there in one place, the last thing you want is for someone to break in.

UPDATE: A patch to fix the exploit has been released. Download it here.

If you use Ubisoft's uPlay browser extension, you should probably get rid of it right now. An Information Security Engineer at Google discovered that the plugin has a hole in it that allows programs to be installed through uPlay, essentially letting anyone who feels so inclined to take over your computer. How the Exploit Works

It used to be that you only had to worry about maids rummaging through your belongings in your locked hotel room. But now anyone with 50 bucks of hardware and some programming skills can hack their way in—as long as it's locked by keycard.

Most of the time, asking to borrow someone's car will elicit a really long string of excuses. But unlike letting your buddy use your car, which usually gets you nothing more than an empty tank, GM has found a way to make car sharing beneficial for everyone involved. If you're one of the 6 million people who have a GM vehicle that's connected to OnStar, you're in luck: according to an OnStar employee, you can make up to $1,000 a month just by letting other people rent out your car when you're ...
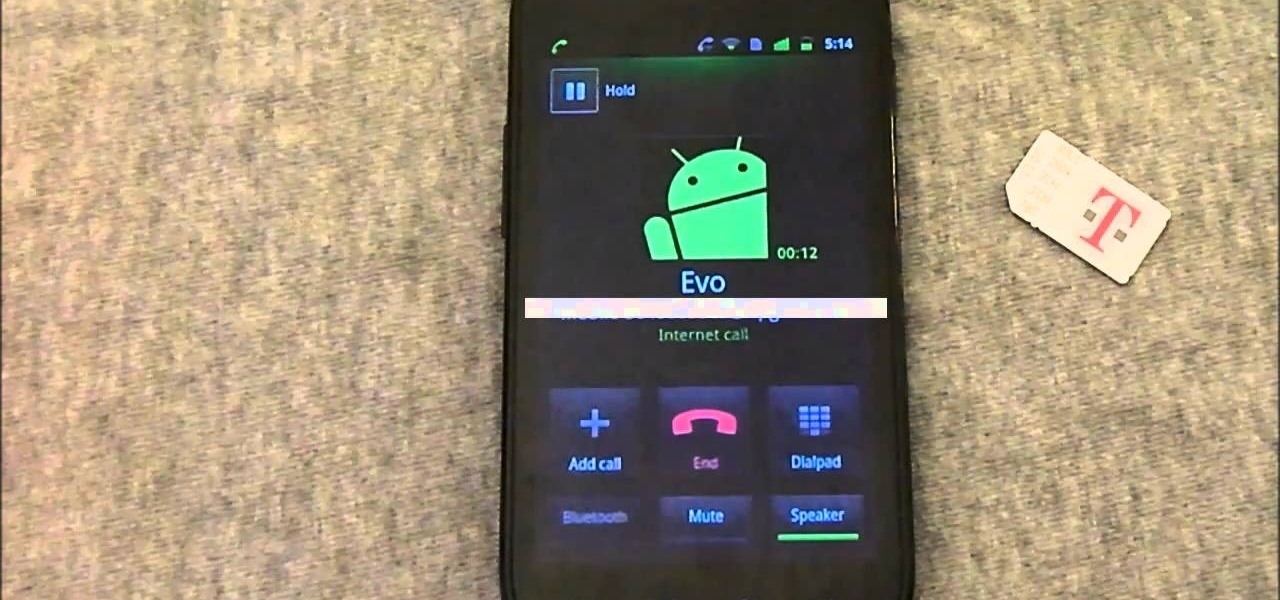
In this Android user's guide, we learn how to use the Internet calling feature new to the OS 2.3 (Gingerbread) release of the Google Android mobile operating system. For step-by-step instructions, and to get started using this feature for yourself, take a look!
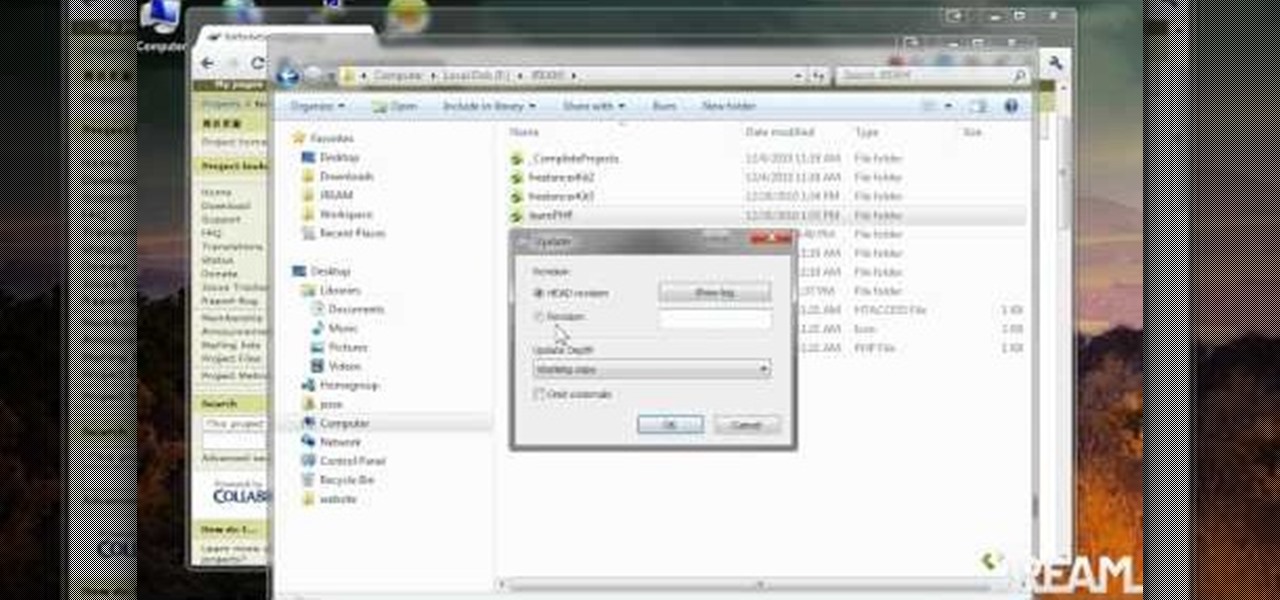
Tortoise is an incredibly useful tool for programmers and those who do write or are planning to write lots of software on a Windows machine. New users don't have to worry about getting an SVN, but more advanced users will appreciate the functionality.
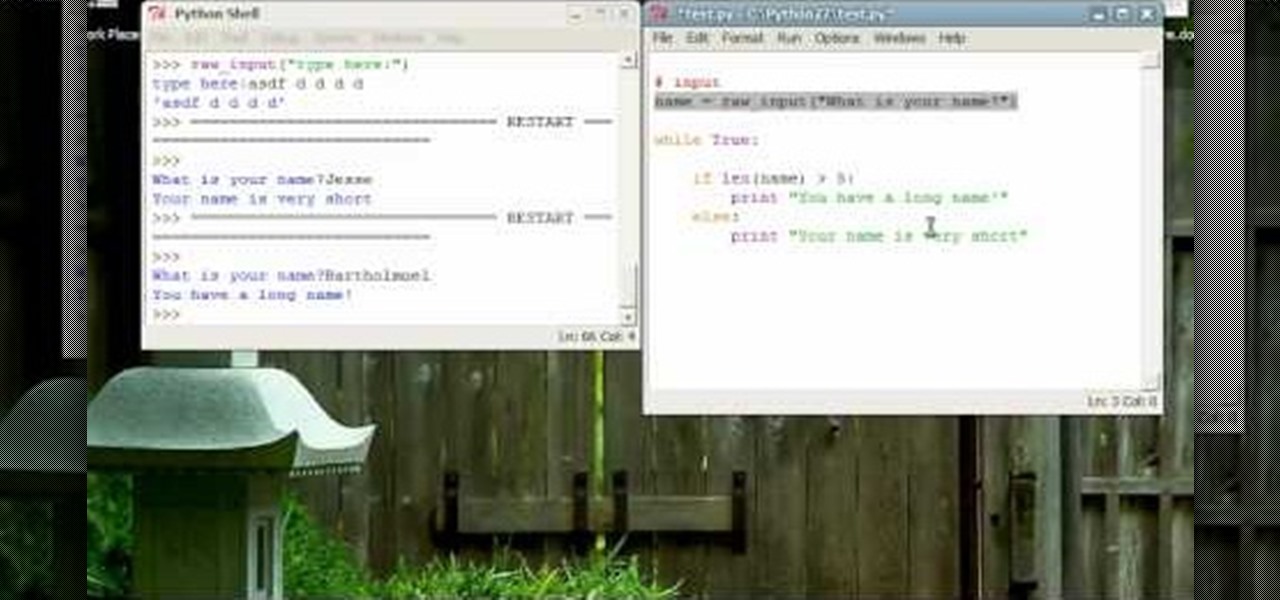
Now that you've mastered the nuts and bolts of Python, it's time to add in another layer of complexity - allowing for user input to your program. Write a small dice rolling program using all the principles you've studied so far.
Customize the colors of your homescreen icons on your HTC 7 Trophy Windows 7 smartphone! It's easy and only takes a few seconds. This WP7 user's guide will walk you step-by-step through the process. For more information, and to learn how to set up custom-colored icons on your own HTC 7, watch the clip!
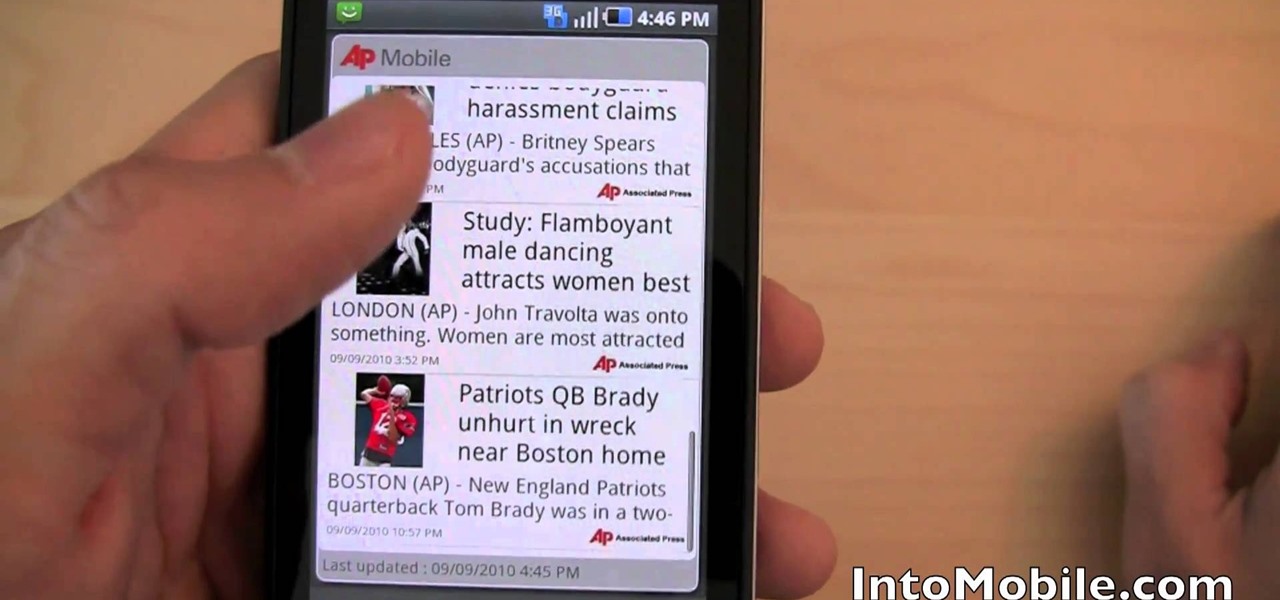
New owner of a Samsung Galaxy? Thinking of picking one up? In this Galaxy owner's guide, you'll learn how to get around this Google Android phone's user interface (UI for short) to do things like send and read messages, make and receive calls and surf the web using the phone's web browser.
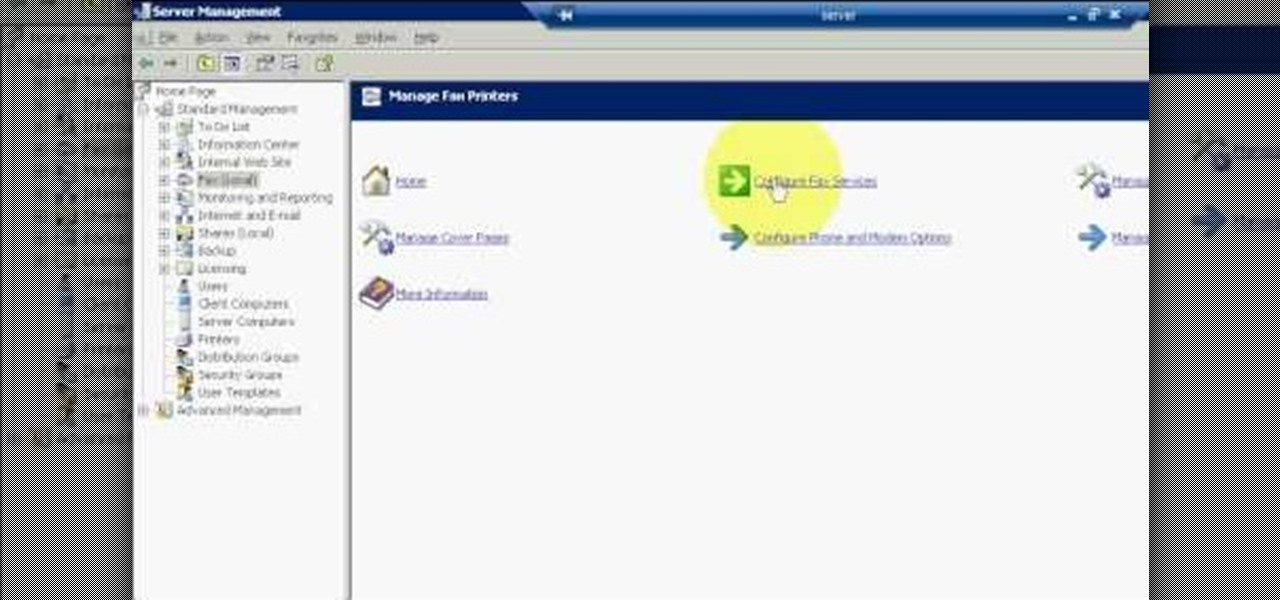
The first step to create a fax using Outlook 2003 and 2003 server. Using add/remove windows component make sure your fax equipment is properly installed. Under the start menu select the printers and fax option and select the share option. Then under administrator tools/users/new/users/fax to enter your password to turn our fax information transfer on. You must now select fax user and select advanced settings and double check to make sure the fax is able to see the object it needs to send the ...
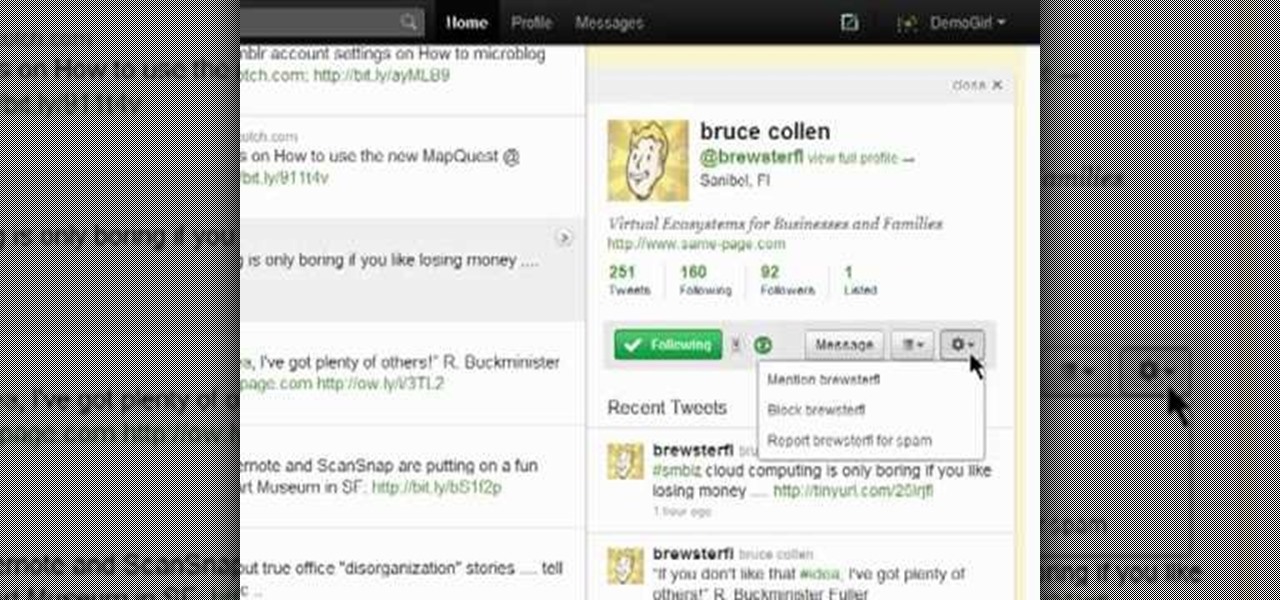
In this clip, you'll learn how to view someone else's user profile on Twitter. What do President Obama, the Dalai Lama and Justin Bieber have in common? Why, they're all on Twitter, of course. Join the party. Whether you're new to Twitter's popular microblogging application or just missed a few of the essentials along the way, you're sure to benefit from this free video tutorial.

In this free video programming lesson, we learn how to create an admin user CRUD in Ruby on Rails 3. Whether you're entirely new to Ruby on Rails 3 or are a seasoned developer merely looking to brush up on a few of the basics, you're sure to find much to take away. For all of the details, watch this quality video guide from the folks at Lynda.
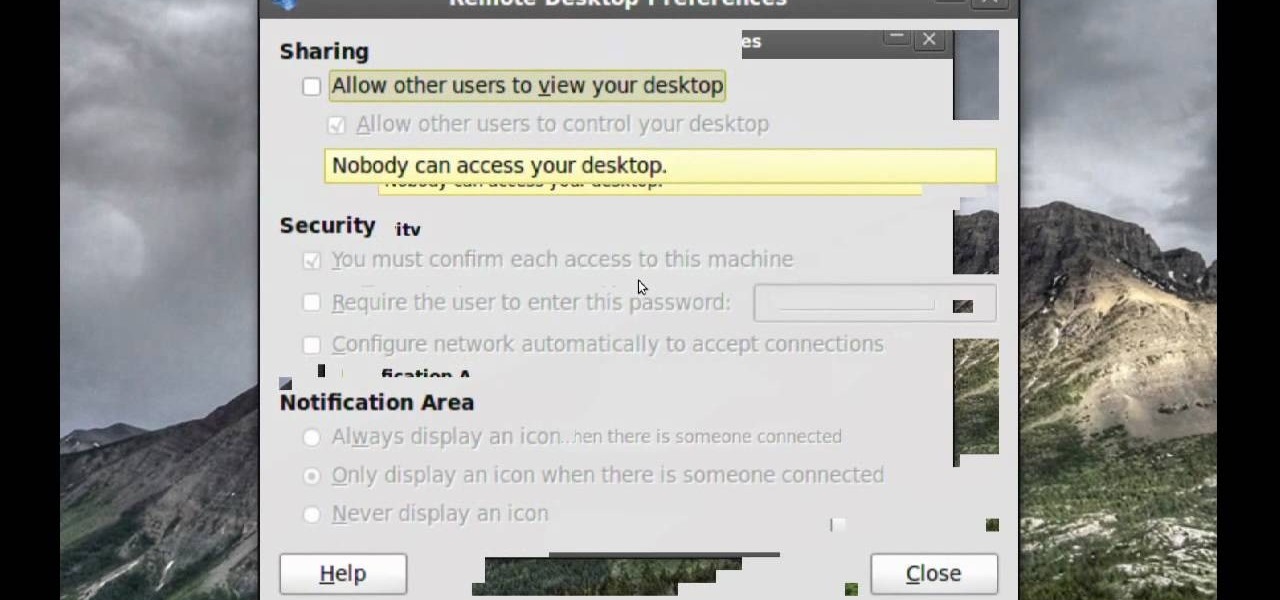
Remote assistance is a feature that, as its name suggests allows a user to remotely control another computer. The user can then use the remote computer in the same way as if the user is physically present there. Most modern operating systems support this feature.

Whether you're a Mac user or a Windows 7 user who has just installed Pro Tools on your machine, you can still find this tutorial useful. Take a tour of the Quick Start Menu and learn about all the different tools at your disposal when editing music in Pro Tools.

This video describes how to trash your Pro Tools user preferences, restoring them to their factory default setting, on an Apple Mac OS X 10.6 (Snow Leopard) computer. Whether you're new to Digidesign's Pro Tools 8 or simply looking to pick up a few new tips and tricks, you are certain to benefit from this free software video tutorial. For complete instructions, take a look.

In this video tutorial, we learn how to set up user permissions when using Joomla 1.5. Whether you're new to Joomla's popular content management system or are a seasoned pro merely looking to brush up on Joomla! 1.5, you're sure to be well served by this clip. For more information, and to get started employing the lessons imparted by this free video tutorial yourself, take a look.