A new app called Roadie now makes life a little easier by connecting users to people who can transport their stuff. The app allows users to transport anything from dogs to getting rid of your ex's things. Furthermore, anyone can register as a sender, or become a driver to make an extra buck. The app is very easy to use: simply download (the app is available on both iOS and Android) and register using an email address or with Facebook. Using the profile you've created, users then select whethe...

Google Assistant has introduced tappable shortcuts on the Google app for Android, iOS, and Google.com this week.

A development team in Silicon Valley is nearing early access release of a new hardware-independent augmented reality platform called Phantom AR.

We live in a marvelous age, a time where technology is driving us forward as a species at a rapid pace, and tech-driven miracles are becoming more and more commonplace. While the human race may not be focused on building the largest wonders of the world, as it once was in history, the current order of wonders are much smaller in scale—even internal.

An interesting new use-case for the Microsoft HoloLens appeared in a YouTube video from Washington-based DataMesh last month. In it, you can see the HoloLens working in conjunction with the Microsoft Surface Studio, Surface Dial, and Surface Pen for 3D model detailing and visualization in real time.

Starting in October, many Nexus 6P users have been experiencing a bug that causes their phone to completely shut down, even though there was 20% or more battery life remaining. At first, it was thought to be a direct result of the recent Android Nougat update, but a combination of factors indicate that this isn't necessarily the case—or, at least, it's not the only problem.

With the recent news that New York County's District Attorney's office is trying to get into over 400 locked iPhones for use in criminal investigations, you can see why it's important to keep other people away from your personal data. The fact that it can and will be used against you in a court of law is just one reason to protect your phone, because even if you make sure to stay above the fray, identity theft and bank fraud are still very real threats.

According to multiple users on Reddit, the Pixel and Pixel XL's camera can have some serious auto-focus issues if you're using a certain type of case with Google's new flagships. When the problem occurs, your camera app will refuse to settle on a focus point, making almost everything in the frame blurry. Redditor HeshoMike uploaded a video of the phenomenon, and you can see it in action here:

The Google Chrome browser for Android is packed with many great features, but it definitely has a bad rep for being slow and laggy on low-end or midrange devices. Without a top-notch processor, you'll likely notice some stutter with choppy scrolling, and pages can take too long to load in general.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

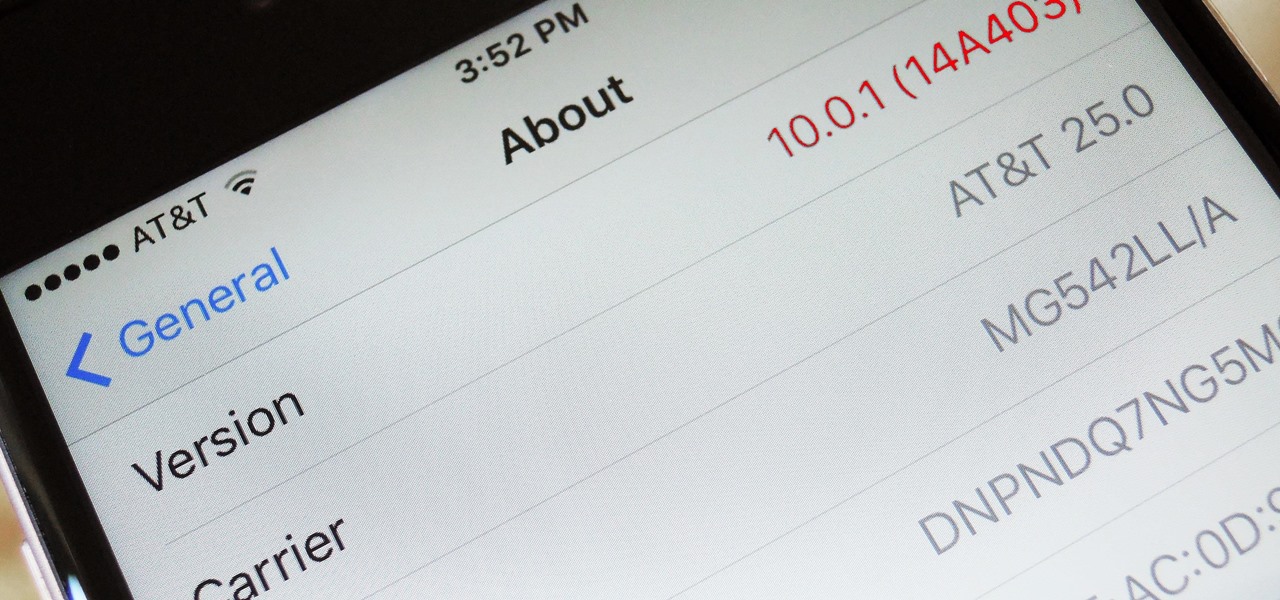
When a new version of iOS comes out, everybody gets caught up in the craze of finding features and playing around with new functionality. But this generally leads to a lack of coverage on the finer aspects of the update—things like bugs, minor tweaks, and pain points that users discover along the way.

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

Nobody's supposed to know where the Batcave is, but as most everyone thought, Batman's underground lair lied below the estate of his secret identity, Bruce Wayne, in Gotham City.

You can use the F1 key to notably dim your Mac's display, but sometimes that just isn't dark enough. If you're working in pitch black conditions, have a migraine or tired eyes, or just want a more comfortable environment, you might want your screen even darker—without making it pitch black.

We're so used to seeing things in particular ways that anything different just doesn't make sense to our brains. Culturally, we like to read things from left to right, and from top to bottom. Change that and our brains struggle to adjust.

To serve as a framework for the "Nexus Imprint" feature in their new Nexus 5X and Nexus 6P smartphones, Google added native fingerprint scanner support to Android 6.0. Sure, Android devices have had fingerprint scanners in the past, but this is a unified, system-wide implementation that all devices can use—meaning that in the near future, we may finally start to see apps that let you log in to your account with your fingerprint instead of a password.

Just last month, Microsoft announced plans to take away a huge chunk of storage from the free tier of their OneDrive cloud service, and users are understandably quite upset. At the same time, they reneged on an offer to give Office365 users unlimited OneDrive storage, and instead, will only be offering 1 TB of storage.

This year, Google released two Nexus phones to glowing reviews, and as we've grown to expect, the Android community wasted no time in coming up with a root method for both. In fact, legendary root developer Chainfire even devised an entirely new "systemless" method for rooting that should make updating a bit less complicated, along with a few other benefits.

In general, the fingerprint scanner in Samsung's 2015 flagship phones is quick and accurate, but when you get that "No Match" message while trying to unlock your phone, it can be incredibly annoying. To help curb these issues, I'll go over three tips for speeding up the unlocking process that should work wonders on your Galaxy S6, S6 Edge, S6 Edge+, or Note 5.

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

Windows 10 is the most cloud-oriented version of Windows to date—yet, while this means you get some nifty new features, it also means some of your personal data is being shared with Microsoft's servers.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

From laptops to tablets, technology is taking over classrooms. Elementary schools offer kids tablets, and college students are bringing laptops into lecture halls, leaving their notebooks behind. Today, many students prefer putting their fingers to a keyboard rather than pen to paper, but are these helpful devices truly beneficial?

Google I/O is like Christmas for Android enthusiasts. Every year, this conference showcases new and upcoming features for the world's leading mobile operating system, and this year's was no different. Shortly after announcing Android M, Google released a preview version of the upcoming firmware for Nexus devices.

Samsung has a long-standing reputation for packing their devices with lots of added functionality, and the Galaxy S6 Edge is no exception. It comes with a nifty feature called "Information stream," which allows you to get quick, at-a-glance information by swiping the edge of your screen back and forth while the display is off.

Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

As far as wallets go, mine is as full as they come; think something like George Castanza's overstuffed wallet on Seinfeld. I've got receipts, pictures, and tickets jammed inside, but what takes up the bulk of the space are all of the cards—credit, debit, gift, rewards, customer loyalty... I've got pretty much any card you can think of squeezed in. While it is a strain on my rear end, there's nothing I can do besides keep some of the cards elsewhere. However, looking for them when I need them ...

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Coffee shops are a relaxing place to get work done on your laptop; there's free Wi-Fi, fresh coffee, and people generally leave you alone. Inevitably, those cups of coffee will go straight through you, resulting in a much-needed bathroom break. But while you're attending to your bodily functions, who's attending to your MacBook?

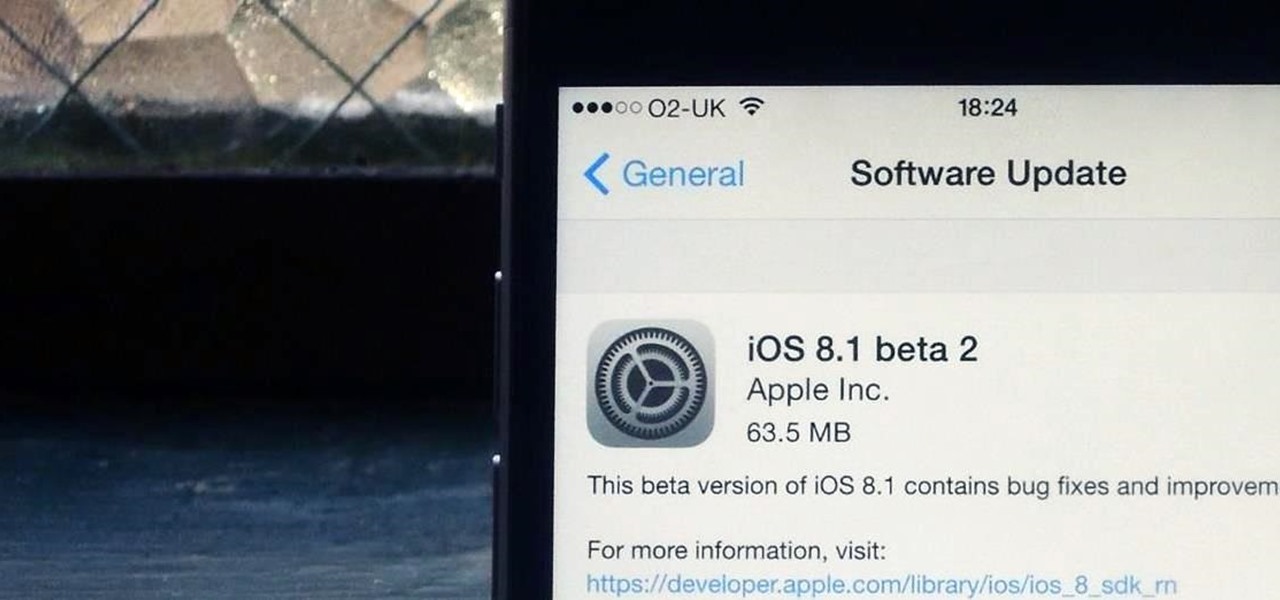
Shortly after Apple's iOS 8.0.1 update fiasco ruined many iPhone users' cellular reception (which was fixed with iOS 8.0.2), developers were treated to the first beta release of iOS 8.1, which will be the next big update for iPad, iPhone, and iPod touch.

We live in a time where privacy is rare and our files can be easily accessed by just about anyone. Having your phone protected by a passcode is great, but if someone figures it out, they can easily access anything on your phone.

Most times when you take your smartphone out of your bag, pocket, or purse, you probably know exactly what you're going to do with it. Make a call, send a text, take a selfie, browse viral videos on YouTube, or one of the other many things a smartphone can do nowadays.

The Galaxy S5 is a flagship-level device with some pretty advanced features, like its 4K video recording capability, water-resistant casing, fingerprint sensor, and KitKat running out of the gate.

Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by developing your scripting skills.

Whether you've been fully converted or just want a little Apple with your Android, adding your iCloud email to your Galaxy Note 3 is a fairly simple task. Usually, Apple and Android don't play nice, but your iCloud address can be added to your stock email app just like any other email account.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.