Speeding tickets suck, and I don't know a single person that can tell me otherwise. But the reality is, most of us will break the speed limit for one reason for another, regardless of the pricey risk.
This is a how to to change any user password on a windows 7 computer. If you forgot your password you can change any account password even if you are locked out of your account.
Hey everyone, this will be a quick post. Facebook does not use HTTP Strict Transport Security (A header that tells the browser to only use HTTPS when communicating with the server) on subdomains of facebook.com. That means, if someone uses facebook in a different language, the browser will attempt to connect using HTTP first. An attacker can intercept that request and serve a different page, including a fake login one.

The first White Hat Award for Technical Excellence tutorial contest ended last night at midnight! We had many excellent articles submitted, once again re-affirming what an incredible community we have here at Null Byte! We had quite a flurry of great articles in the last few days. Thanks to all of you who submitted such high quality material to our community. Your efforts are appreciated and you have the undying gratitude of our community. We will not forget your efforts. I'll be reading and ...

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.

Many users across the web have reported issues with receiving notifications from the Gmail and Hangouts apps on Android. The problem is most prevalent with users running Marshmallow, and the gist is that notifications from these apps are extremely delayed or don't come through at all.

If you're a developer looking to get some exposure for your high-quality app, or if you're a user hunting for new apps and would like a chance to win a paid app at no cost, then Jack Underwood's new Promo Codes app may get you there, which you can install for free from the Google Play Store.

Another series I am now starting, might have to slow down on all of these series, but why tf not. What Is CMD?

Some things never change. You'd think that with all the focus on web security, people might take the slightest precaution to keep their online activity private. Maybe there are more people suffering from Paula Poundstone's password troubles than we'd like to believe.

If you left your iPhone sitting unlocked, or have friends and family that like to play pranks, you may be stuck with an overly orange screen out of the blue. Or worse, your screen is normal most of the time, but seems to randomly change its tint in certain parts of the day.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

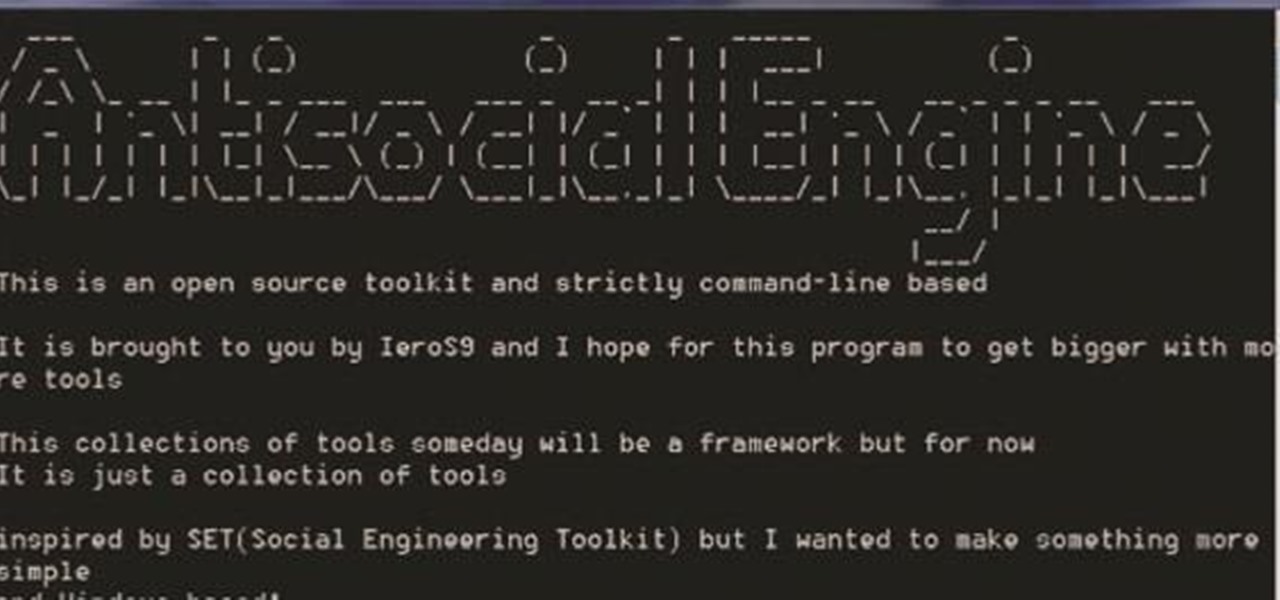
A.E Hi again this is my second post on nullbyte. The first one was on how to make a remote screenshot captor, now I will give you a presentation for a project of mine(I have named It Antisocial Engine) that It is not something extraordinary but will help many guys.

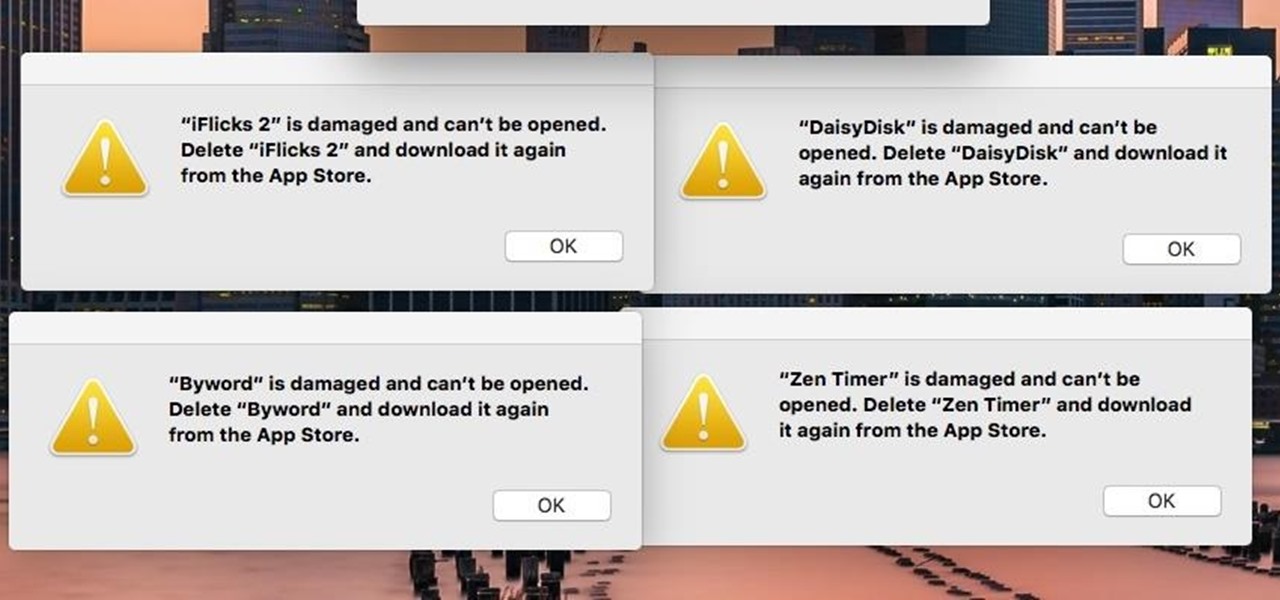
If you're seeing "damaged" apps on your Mac, you're not alone. A huge digital rights management blunder in Apple's Mac App Store on Wednesday, November 11th has rendered some apps unusable. When opening certain apps, the following message could be displayed:

Welcome back! In the last iteration of how to train your python, we covered loops, today we'll be covering something that I wish I had learned about much earlier in my scripting career, errors. We all run into them, and they can be frustrating, but there is also a silver lining to them. Today, we'll be discussing why some errors are unavoidable, and what we can do when we run into them. Also, this article will be more of a concept and less of writing actual code, but the information is equall...

The Start menu has definitely seen many changes over the years—from the traditional menu that was present from Windows XP to 7, to the Start screen in Windows 8, to the hybrid of the two in Windows 10. And while the return of the Start "menu" has received near-universal praise, there are still some aspects old Windows 7 users will miss. Namely, the User folder and content folders (like Documents, Downloads, Music, Pictures, and Videos).

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

Last week, NowSecure security researchers revealed that nearly 600m Samsung mobile devices are vulnerable to a type of MitM attack.

Snapchat has built upon the photo-sharing service it once was to become a money-sending, commercial-shelling, video-messaging giant. They improved their user experience by adding Stories, Geofilters, and even the rarely-used Snapcash feature, but why isn't there something as simple as color filters? Yes, they have filters for black and white, saturated, and sepia, but that's it as far as color goes.

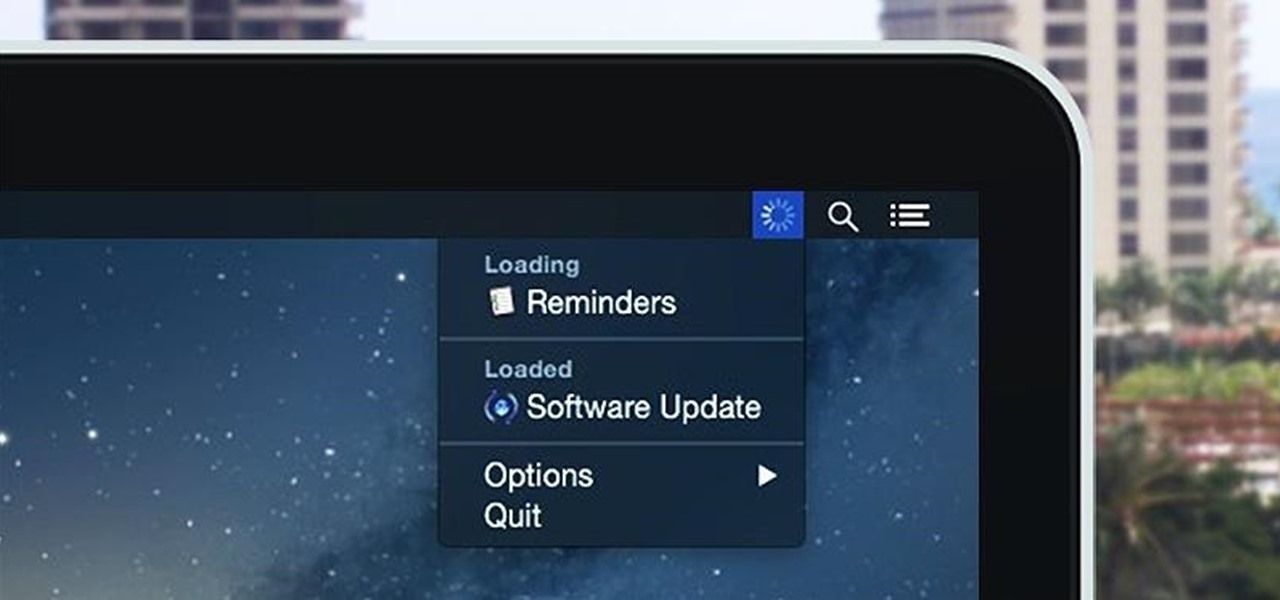
Monitoring your Mac with widgets can be the first step in identifying bandwidth issues, but finding the root of the problem can be a completely different story. Usually you will have to open up Activity Monitor in Mac OS X to look for apps hogging your bandwidth, but with Loading, you can get a detailed data usage report right from your menu bar.

There's a recently discovered flaw by iDownloadBlog that lets thieves reset a stolen Apple Watch without a hitch, which is the result of Apple not including the Activation Lock feature that iPhones have had since iOS 7.

No one is perfect, and this goes double for software developers. All of the quality assurance testing in the world does nothing when you put a new OS in the hands of everyday users, since we all use our devices in different places and for different reasons. Recently, Cyanogen released their version of Android Lollipop, Cyanogen OS 12, and with it came a whole lot of great features, but some bugs also slipped in.

CyanogenMod has been building upon open-source AOSP apps for many years now. They've made improvements to apps like the stock SMS client, the stock Audio Mixer, and a whole slew of others.

I've used the flashlight feature on my iPhone more times than I can count. It's an invaluable tool that's super easy to activate; just pull up the Control Center and hit the flashlight icon. However, turning it off isn't always as easy, especially when you're on the lock screen.

Are you a lawyer who's married to a computer programmer? Chances are you might not have even dated if you first met online.

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.

Being fixated on all of the great additions to Android 5.0 Lollipop, it can be a little difficult to take notice in the features that went missing. For instance, lock screen widgets. It's speculated that the lack of practical use for lock screen widgets and the implementation of the revamped Lollipop lock screen may have lead to their departure, but some of us want them back!

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

Apple's keyboard has a set of media controls to navigate the music playing on iTunes, allowing you to play, pause, skip, and replay songs and videos. Unfortunately, these controls are exclusive to iTunes; if you're playing music from Spotify, Pandora, or the myriad of other online web-based services (Amazon, Rdio, SoundCloud, etc.), you're out of luck.

Yosemite brought a new, Alfred-like Spotlight search to our Macs, but at times I still find myself wanting more out of it. However, after stumbling upon Flashlight by developer Nate Parrot, I am now able to perform Google searches, look up weather, and even enter Terminal commands straight from Spotlight's search bar.

Amazon is currently offering over $80 in free Android apps in the Amazon Appstore, but only for Friday and Saturday, so make sure to grab them quick before they all go back to normal price. Highlights include the Fleksy Keyboard (normally $3.99), Oxford Dictionary of English with Audio (normally $24.99), and EasyTether (normally $9.99).

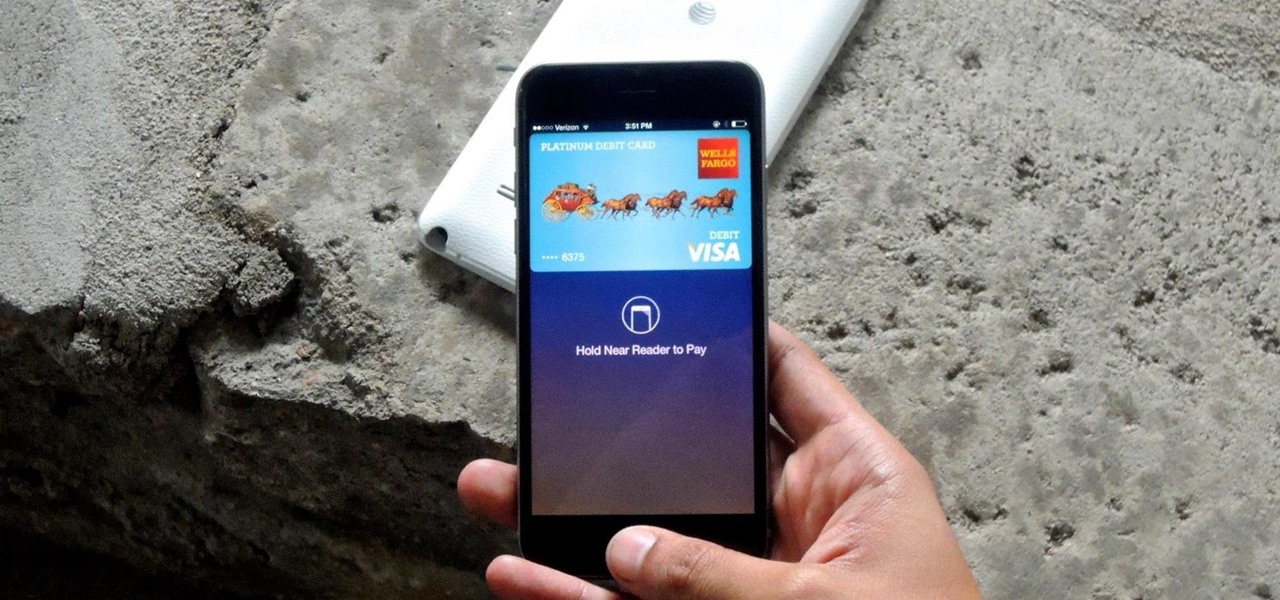
Apple Pay is ready for use at over 220,000 outlets across the United States. By using your iPhone 6 or 6 Plus, all you have to do is point your device at any NFC-enabled point-of-sale system compatible with Apple Pay, press your fingerprint on the home button, and voilà—you've just paid for something with your card. As a matter of fact, the store doesn't even need to have Apple Pay compatibility to work with your phone. If their machines have NFC-technology, they'll recognize your device (unl...

Although sleep mode and screen savers contribute to the security and energy preservation of my MacBook, it can become a nuisance when they initiate unwelcomely. Yes, I could just change these settings in System Preferences, but to do this every time I momentarily leave my Mac unattended would be tedious, to say the least.

Automator takes the work out of common repetitive tasks. I don't enjoy compressing videos for quick sharing or uploading to the web, so I created an Automator action to handle the process for me.

The Touch ID fingerprint scanner on the iPhone 5S was one of the phone's biggest selling points. Now, the Touch ID system can do more than just unlock your phone, like pay for stuff, and is even present on the new iPads (as well as iPhone 6 models, of course).

Accumulating approximately one million downloads on the Google Play Store in less than 72 hours from its initial release, TouchPal instantly became a favorite among Android users.

This year's Google I/O brought the announcement of Android L, as well as the Preview builds of L for the Nexus 5 and Nexus 7 (2013), installed using either ADB on Windows or fastboot on any computer. Unfortunately, those of us without a Nexus device are out of luck—but not entirely.

Last week, I showed off a deeply buried accessibility feature built into iOS 7 and 8 that lets you disable screen touches in certain apps. While useful for many reasons, I found it most helpful for preventing nosy family and friends from swiping through the Camera Roll when showing them a photo.