
How To: Get your PSP onto the BGSU wireless network
This video includes instructions on how to get your PlayStation Portable (PSP) onto the BGSU wireless network.


This video includes instructions on how to get your PlayStation Portable (PSP) onto the BGSU wireless network.

Adding a peephole to your front door is a cheap and simple way to improve home security. This how to video shows you what to consider and how to install a peephole.

How to Hide IP from Hackers. Hide your IP address to get more security. Hotspot Shield (free) change your IP address and your location. To see the changes visit http://www.ip-adress.com/ before and after running program.

Watch as Karen's password is retrieved - both by hypnosis and with the help of technology. Plus, learn how to improve your password security.

The latest software update for iPhone has a few new features you should know about, including an enhanced security feature to protect your Apple ID account from phishing and other attacks. Keep reading to see everything new that's included with iOS 16.3 for iPhone.
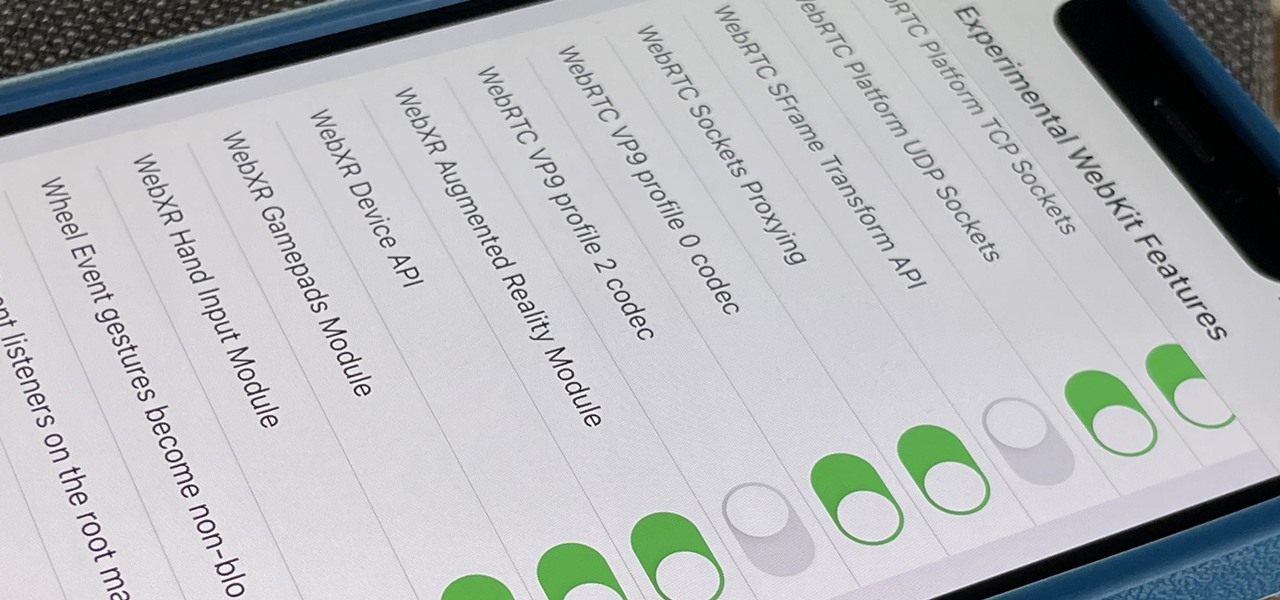
Safari's advanced experimental features give you access to new browser initiatives, upcoming web tools, element changes, behavior adjustments, and other preliminary feature tests in development by Apple. If you use them on your iPhone, you can either improve your Safari experience or wreck it. Resetting the flags provides a fresh start.

Apple just rolled out the of iOS 14.5 to developers and beta testers, and one of the headlining features is the ability to keep your iPhone unlocked when your Apple Watch is nearby. As these things tend to go, Android has actually had this same feature for years, though it isn't quite as polished.

If you're interested in joining the increasingly popular and lucrative world of ethical or "white hat" hacking, you're far from alone. More and more coding and programming pros are turning to this field thanks to the high pay, countless opportunities, and exciting work environment.

Although Facebook has some questionable privacy and security practices, you'll find it still offers you ways to protect the information that's important to you. One of those ways is locking Messenger behind biometric authentication protocols such as Face ID and Touch ID, ensuring that no one else can access your private chats.

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.

Getting files from an Android device to a Mac or iOS device is not always easy or convenient, and the same goes for transferring content from a Mac or iOS device to an Android device. But we're here to tell you there is a better way than using USB cables, email, and cloud storage, and it gives you the look and feel of AirDrop.
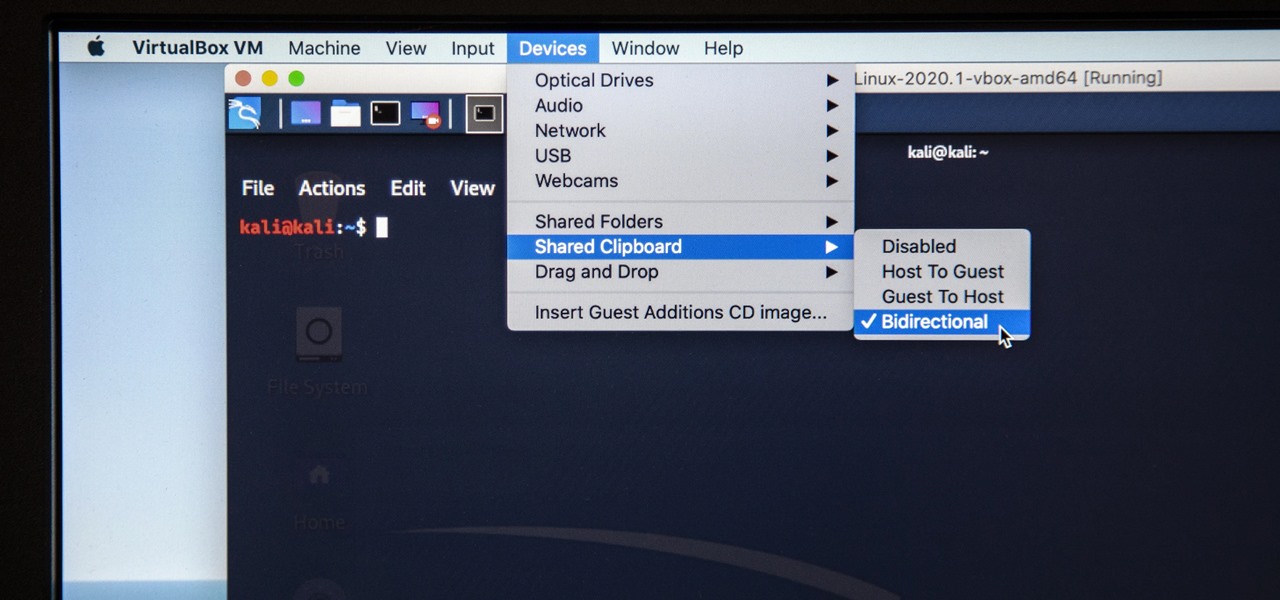
Last week, I updated VirtualBox on my computer since I had skipped a few versions, then I could no longer copy text or paste text from my Kali virtual machine to my host OS and vice versa. Installing the Guest Additions didn't seem to do anything, and the bidirectional shared clipboard was enabled, but there was one thing that did work for me that may help you out too if you experience the issue.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.
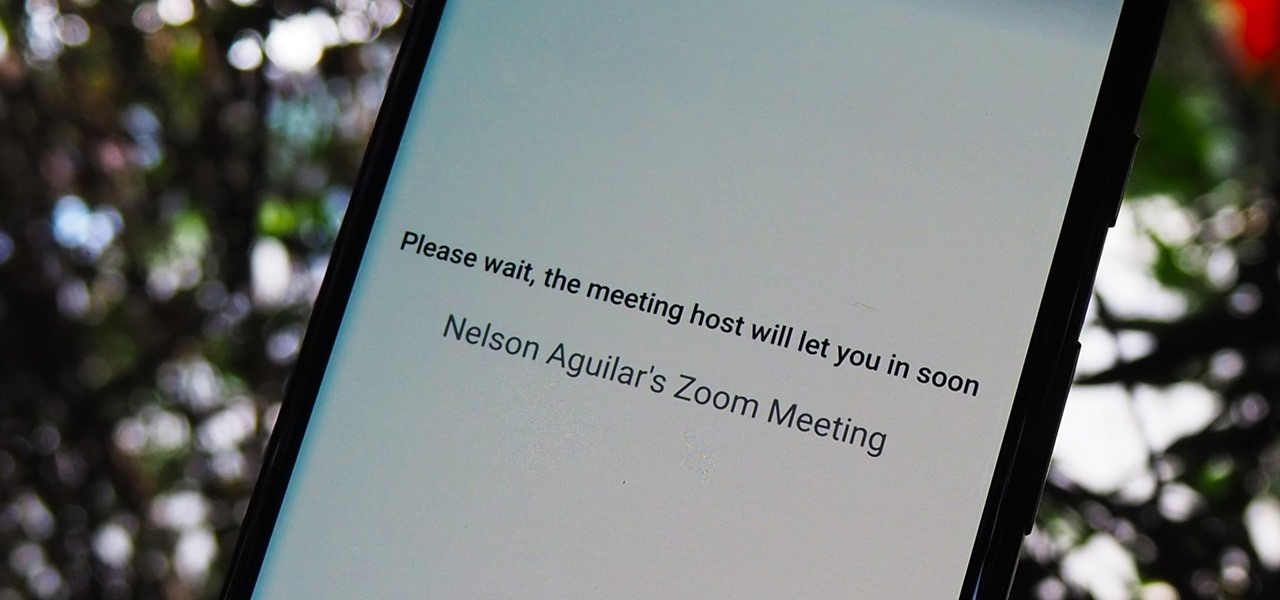
The "Zoombombing" trend is still strong on the Zoom video meetings service, despite security measures Zoom put in place to stop it. That's why it's up to you, as either a host or co-host, to be proactive about preventing Zoombomber harassment, as well as stopping it whenever it slips through the cracks.
When you're stuck working or learning from home, video meetings can help you stay connected to employers, coworkers, schools, students, and more. And Zoom is the hottest video conferencing service at the moment. While Zoom is easy to use, it does have a fair share of sketchy features you should know about, such as attendee attention tracking.
The powers of the Nreal Light continue to increase incrementally with each passing week. Now, the latest feature added to the device is possibly the most requested feature for anyone who has tried the Nreal Light: hand tracking.

While holographic Whitney Houston is hitting the road, a new mobile app is bringing volumetric captures of up and coming performers directly to the iPhones and iPads of fans.

Though Microsoft has had trouble keeping up with the demand for HoloLens 2, the company has been able to supply modified headsets to the US Army.

One of the worst-kept secrets in the tech world is Apple's plans for consumer-grade AR smartglasses, still unconfirmed publicly and only recently corroborated through a leaked account of an internal employee meeting.

As augmented reality continues its collision course with mainstream adoption, the technology will now have a role in one of the most anticipated boxing matches of the year.

The "what (blank) are you" augmented reality filters on Instagram have become so popular that more and more Hollywood giants are following the augmented reality-powered social media meme train, with the latest example coming via Snapchat.

The international profile of augmented reality startup Nreal continues to quietly rise thanks to gradual updates and various strategic branding opportunities.

In recent years, Google's Arts & Culture project has been leading the way in terms of innovating the practice of using technology to preserve landmarks and great works of art via digital 3D copies. Increasingly, these efforts are also giving history buffs the chance to experience classic works and spaces with unparalleled intimacy through the wonders of augmented reality.
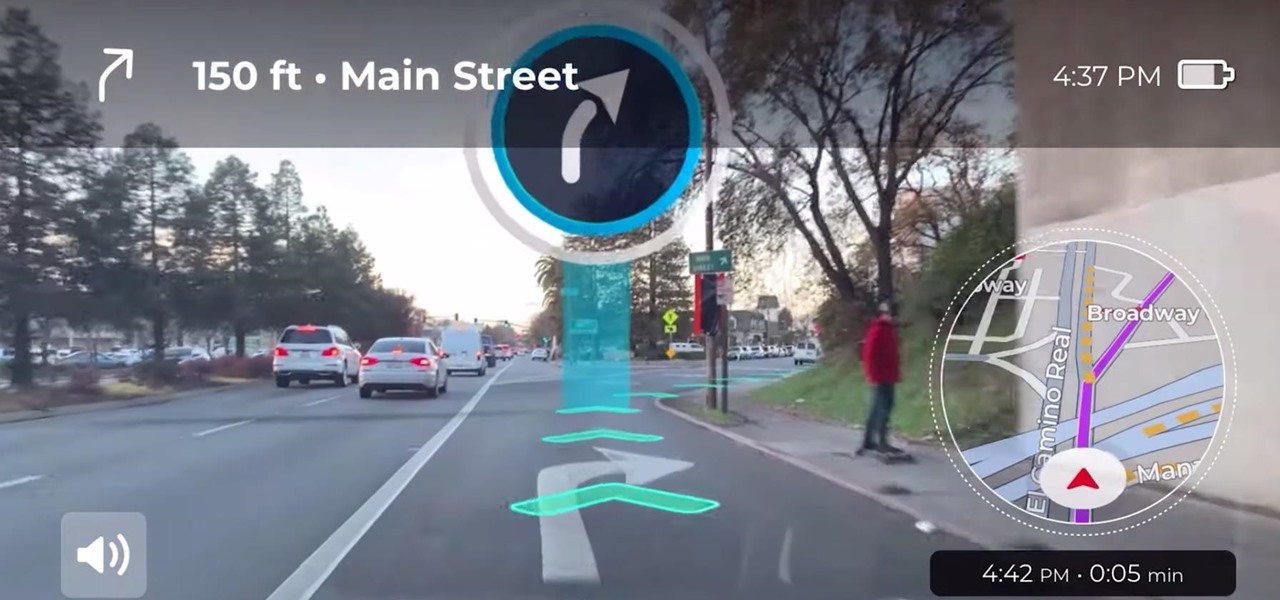
Google pushed a new kind of augmented reality walking navigation to the mainstream last year, and now startup Phiar is hoping users will use its AR app in the same way for driving navigation.

We might never truly know all of the colors behind old and classic black-and-white photos, but thanks to technology, we can get a pretty accurate colorization. Although Photoshop is a popular way to colorize these images, you can now use your iPhone, along with a nifty shortcut, to transform and give new life to vintage photos.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

Despite the fact that over 600,000 Snap Lens filters have been created since Lens Studio debuted in 2017, and Facebook is reporting that more than a billion users have interacted with its Spark AR filters across Facebook properties, social augmented reality filters get a bad rap in the AR industry.
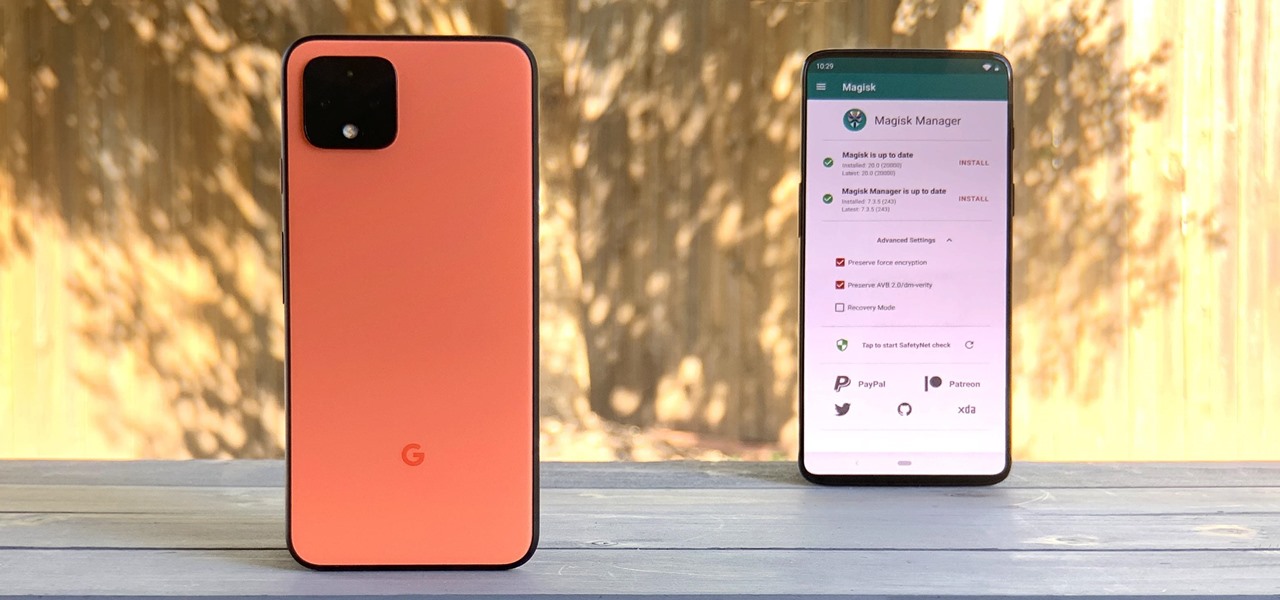
According to a study done by Kaspersky, 7.6% of Android users root their phones. That may not sound like a lot, but with over 2 billion Android devices out there, the math works out to over 150 million rooted phones — more than the total population of Russia, Mexico, or Japan — so root nation is an important demographic that deserves being catered to.

Homemade Halloween costumes that exhibit the maker's creativity are always better than off-the-shelf versions. It turns out that the same is true with virtual costumers.
You watched the live stream, pored over the specs, and are now super excited for the Google Pixel 4. But specs don't tell you everything. After using the Pixel 4 XL for over a week now, we've found several things you wouldn't know without getting your hands on the phone.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

We have seen Kickstarter-launched wearables before, but this one is particularly unique and may even have you blinking a bit in wonder when you see how it functions.
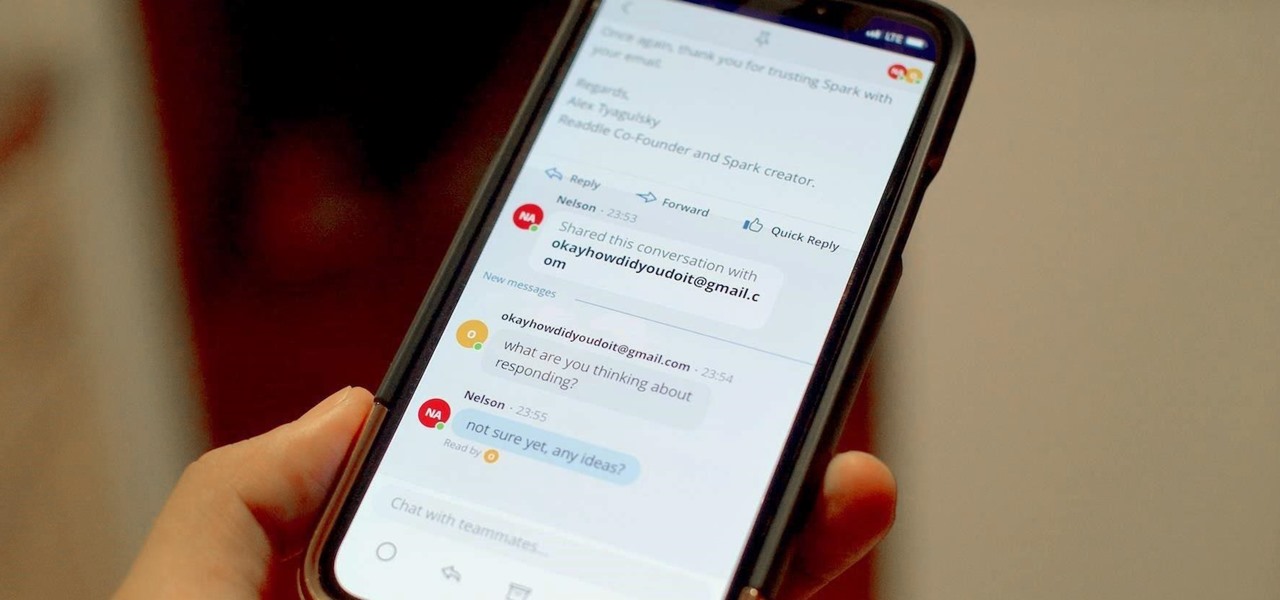
You usually reply to emails on your own ... unless it's related to your work. You may want input from coworkers or higher-ups, and while forwarding works, Spark offers an easier way to discuss important emails with others. Using Spark for Teams, you can easily share an email with your team and discuss it privately.

While Magic Leap World gets its share of fun apps for playing with Porgs, watching TV, and exploring the ocean's depths, developers are making a strong business case for the Magic Leap One as well.
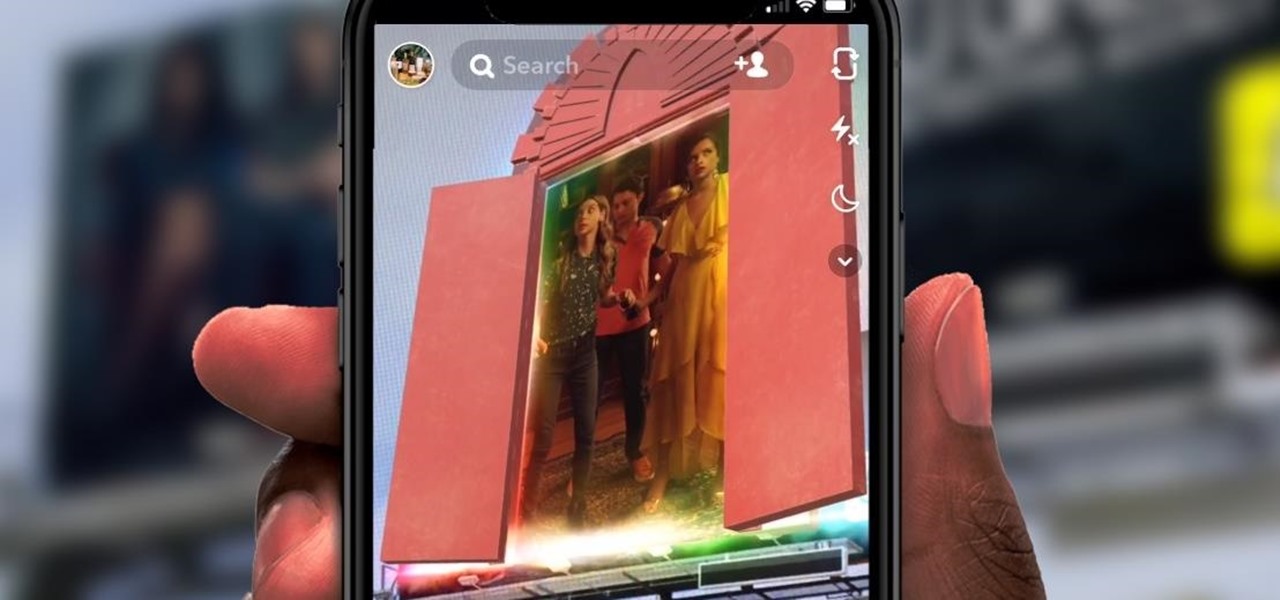
It looks like Snap's foray into augmented reality billboards last year was successful, as the company has returned with two more outdoor advertisements for its Snap Originals series.

The company that supplied some of the technology behind the Star Wars Jedi Challenges AR playset now has its own headset to offer.

Augmented reality as a storytelling medium can do some extraordinary things words and images alone can't convey -- such as transporting readers 400 years into the past.

As Microsoft works toward fulfilling its $480 million contract to supply modified HoloLens 2 headsets to the US Army, Airbus is preparing to supply advanced augmented reality apps for the device.
Although early attempts at consumer smartglasses have employed trackpads and handheld or wearable controllers for user input, its the gesture control interfaces of the HoloLens 2 and the Magic Leap One that represent the future of smartglasses input.

Imagine sitting on your patio, scrolling through your phone's photos, reminiscing about the past. Now imagine being able to see those photos floating in the air, at the exact vantage point from where they were taken a year ago.