There are certain ingredients that chefs regularly use to elevate their food beyond the status of what us mere mortals can create. Shallots are one. Good, real Parmesan cheese is another. And the rind of that real Parmesan cheese just so happens to be one of the culinary world's biggest kept secrets.

Poor chickens. Bacon fat is revered (and justifiably so), and duck fat is a staple at most fine grocers. Marbles of fat make a steak divine, and goose fat is the holy grail of fatty goodness. Yet chicken fat is usually thrown away.

The next time you finish that last pickle spear, don't pour the leftover green juice down the drain. You can use your leftover pickle juice in cooking, in cocktails, and as a post-workout performance shot.

Like most people who cook in a small kitchen, I'm very wary of adding anything to my drawers and cabinets unless I'm sure it's going to be essential to my cooking arsenal or that it can be used in multiple ways.

As far as wallets go, mine is as full as they come; think something like George Castanza's overstuffed wallet on Seinfeld. I've got receipts, pictures, and tickets jammed inside, but what takes up the bulk of the space are all of the cards—credit, debit, gift, rewards, customer loyalty... I've got pretty much any card you can think of squeezed in. While it is a strain on my rear end, there's nothing I can do besides keep some of the cards elsewhere. However, looking for them when I need them ...

If you have satisfying memories of slurping up the sweet milk left in the bowl after eating your cereal, then this cereal-infused milk will make you feel like a kid again. Although people have technically been enjoying cereal milk since the invention of cereal, it was recently made popular as a standalone drink by the playful and quirky Momofuku Milk Bar in New York City. Created by pastry chef Christina Tosi, it's a "recipe" that is both simple and brilliant. The original Momofuku brand cere...

Garlic isn't just a food, it's a legend. It's been found in the pyramids of Egypt and is referenced in the Bible. Hippocrates, the father of Western medicine, prescribed it regularly, and it was given to the first Olympic athletes in Ancient Greece to enhance performance (take that, Lance Armstrong). And, of course, it's famed for its ability to ward off evil, whether it's in the form of vampires, demons, or werewolves.

"Cooking" with liquid nitrogen seems like one of those activities that should be strictly limited to pros who are appearing on Top Chef, but it's the only way you'd ever be able to make Dippin' Dots at home. If that isn't enough of a reason for you to get some LN2 for your kitchen, check out this dose of pretty:

There is very little in this world that tastes as good as a glass of fresh-pressed juice. The flavors in fruit and vegetables are more clean and immediate on your palate, while the chlorophyll and nutrients seem to zip right into your bloodstream. A really great glass of fresh juice makes you feel more alive and the pasteurized versions on supermarket shelves just can't compare. However, as much as I love a glass of fresh juice, if I had to do it all over again, I wouldn't buy a juicer. The o...

Flavored extracts may seem like they'd be complicated to make, but there's a lot less to them than you'd think, and will cost you less in the long run.

The battery in the Samsung Galaxy S4 may pack 500 more milliamps per hour than the old S3 battery, but that doesn't necessarily mean more battery life. High-powered devices need lots of juice, and the S4 is definitely more powerful than its predecessor. The new battery can handle a third more in standby days, and over twice as much in talk time hours. But, when you live on your phone all day long, that means nothing. You're battery is still going to have a hard time keeping up with you.

In this video tutorial, viewers learn how to draw a skull. Begin by selecting a skull image to draw from. Then draw a circle and sketch a few lines to position the eye sockets, nose and mouth cavities. Now erase the guidelines and re-sketch the drawing. Then start toning the eye sockets and nose cavity by shading. Now tone the other parts of the skull. Finish by shading the background. This video will benefit those viewers who are interested in drawing and art, and would like to learn how to ...

In this tutorial, learn an important safety tip for the next time you head out camping or hiking. In this video, you will get advice on how to make a Swiss seat rope harness. You will learn to utilize a length of rope to make a field expedient rappelling harness, that is similar to the seat used by the military. With practice, you can tie this Swiss seat in 90 seconds or less. Essentially, this is a high speed, low drag way to make your own harness. This harness is useful for rappelling or ex...

This step-by-step video tutorial will have you building metal riffs in no time! Andrew Wasson of CreativeGuitarStudio has written a short two-part riff using the harmony from a popular scale out of the style called Phrygian dominant. For the riff, Andrew uses a series of open strings, eighth note triplets, hammer-ons, and pull-offs. Because a lot of progressive metal utilizes different time signatures, Andrew changes the time signature for the last measure of the riff. Don't forget to downloa...

Teresa Richardson from the crochet-mania blog will be teaching us how to crochet a left handed seed stitch scarf. In her video, she is going to be guiding us through the process of crocheting single and double seed stitches as well as providing us with step by step instructions on how to make the scarf. Teresa designed this tutorial with beginners in mind, so newcomers are more than welcome to utilize and learn from it as well. Be sure to have a crochet needle and some yarn handy prior to wat...

Learn how to design a defense to stop dribbling penetration or passes to the middle. If you're a basketball coach, you'll definitely want to utilize this two-three zone defense.

The US Department of Treasury isn't generally known for being on the very edge of technology innovations (see the current hubbub around crypto), instead usually waiting until certain tools have been battle-tested in the mainstream or enterprise sector.

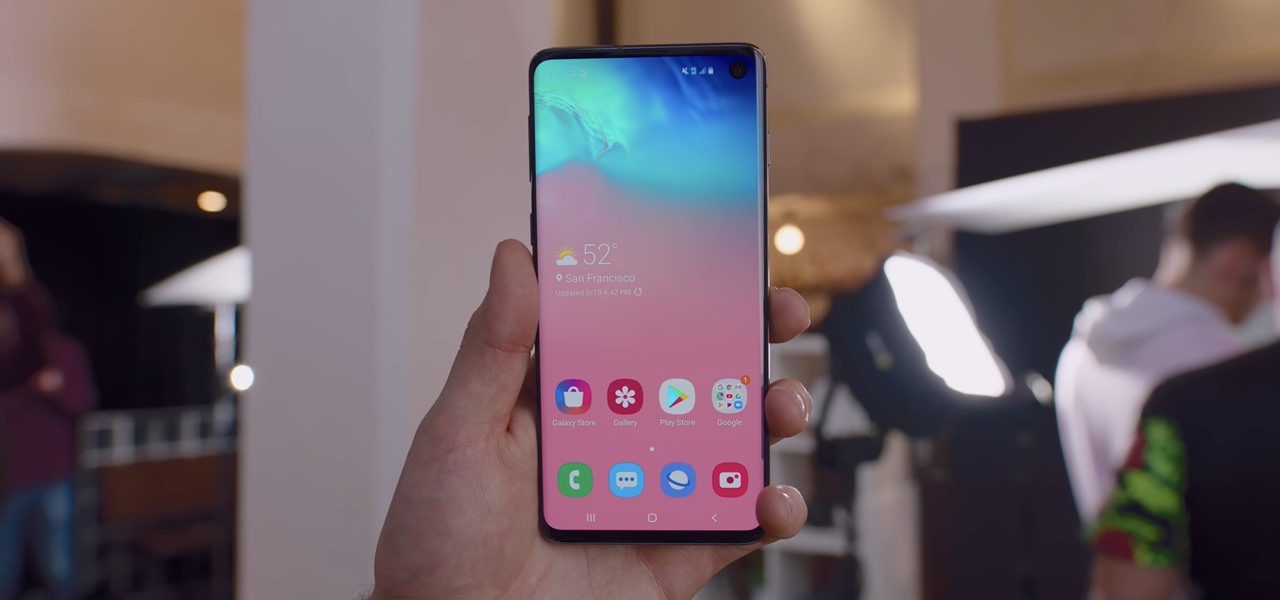
The Galaxy S10 has finally been revealed to the masses, and it certainly doesn't disappoint. As the flagship to herald the tenth anniversary of the venerable Galaxy S line, the S10 has kept popular and familiar design elements like the immersive Infinity Display while employing new features like more advanced cameras to set a new standard for other OEMs to follow.

Chef Elvis "Gator" Hillard will show you how to prepare the water and add the salt, cook the pasta, chop the fennel and garlic, and strain the pasta. Elvis will also show you how to cut the asparagus, sauté the fennel and garlic, add the Romano cheese, incorporate the sauce, and add the cream and the peas.

Sure, Snapchat AR Lenses can be fun, but they can help communicate complex issues as well. While our Facebook news feeds were filled with references to 311 Day, March 11 is also World Kidney Day, the United Kingdom's National Health Service Blood and Transplant (NHSBT) used the occasion to educate its constituents about organ donation.

In older Android versions, you could flood your status bar with a wall of notification icons. But starting with Android 9, Google made it to where you can only see four icons by default, and it was mostly done to accommodate phones with notches. But Google's only notched phone is the Pixel 3 XL, so what if you have literally any other Pixel?

It was a long time coming, but we finally have a meaningful conclusion to the legal case against augmented reality startup Meta Company.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

Face ID does an excellent job with keeping your iPhone safe, boasting a million-to-one odds against unauthorized access when compared to Touch ID, which is 20 times less secure. However, it's far from being truly hands-free, as you still need to swipe up the lock screen once it detects your face to access apps. But if you have a jailbroken iPhone X, this issue can easily be remedied.

After launching its first augmented reality title for Angry Birds on the Magic Leap One, Rovio has doubled back to the platform that made its franchise famous.

When you think of companies that represent pillars like "privacy" or "security," Facebook is pretty far from the top of that list. However, the social media empire is making strides — small strides — to win trust with how it handles your user data. One of those efforts involves a way to prevent Facebook from tracking your iPhone or Android phone's location when you're not using the app.

The HoloLens has made enough of an impact on the healthcare industry for Microsoft technology partner Medivis to convince investors to pledge $2.3 million in funding for its surgical platform.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Augmented reality content makers often position the technology as a new storytelling medium. And who loves stories more than children?

Magic Leap has already entered the realm of entertainment and enterprise, but on now it has blazed its way into a new augmented reality frontier: fashion.

After building its business on virtual reality, Jaunt is leaving the technology behind to focus on building tools for creating augmented reality content.

Do price tags on mobile games give you pause? We get it. With so many freemium games out there, it's tough to justify spending three or four dollars on a game for your iPhone or Android device. That's why you wait for moments like this one, as both "Reigns" and "Reigns: Her Majesty" are aggressively on sale.

Less than three weeks after Rovio Entertainment announced the game, the augmented reality adaptation of Angry Birds is now available for the Magic Leap One.

A Series B round of funding, totaling $30 million, will enable Helsinki-based startup Varjo to launch its industrial-grade augmented and virtual reality headset capable of "human-eye resolution" before the end of the year.

The iPhone X ushered in the Swiss Army Knife-like Side button, which can perform numerous functions, such as summoning Siri and opening Apple Pay through click gestures. This has carried over into the iPhone XS, XS Max, and iPhone XR, so if you've upgraded to one of these devices from a Home button-equipped iPhone, you'll have to learn how to shut down your new device.

Location-based gaming pioneer Niantic has offered a preview of its augmented reality cloud platform that could change the immersive content game yet again.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

On Wednesday, June 6, the people at Magic Leap finally (FINALLY) decided to give the public a dedicated, slow, feature-by-feature walkthrough of the Magic Leap One: Creator Edition. How was it? About as good as it gets without actually getting to see what images look like through the device when wearing it.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.