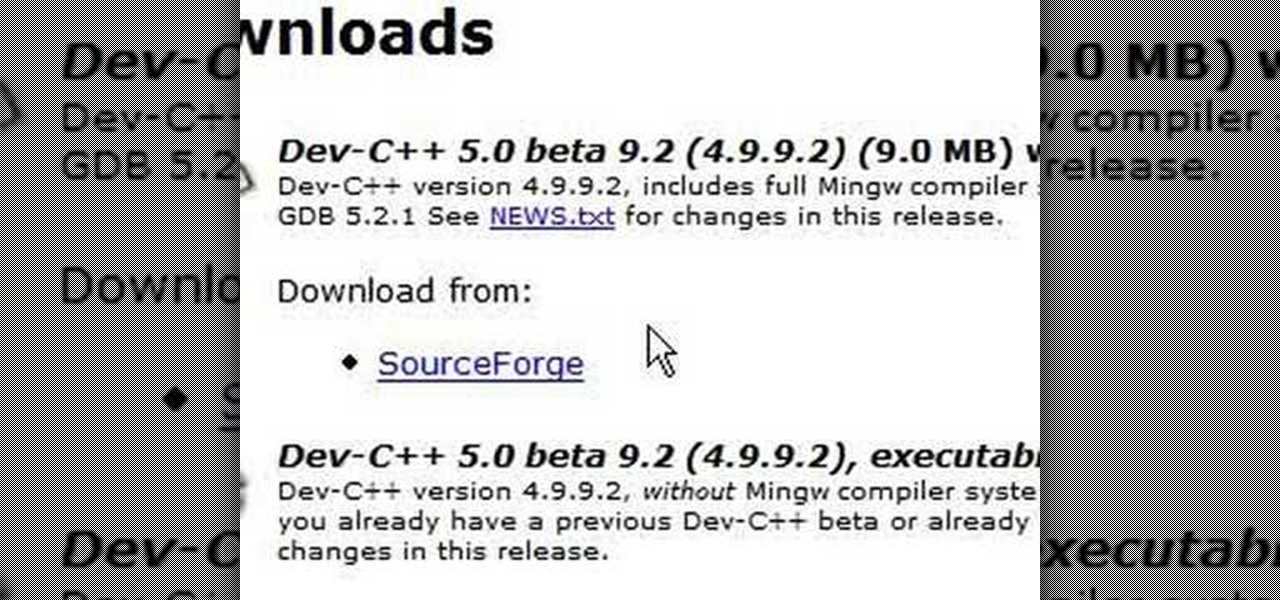
C++ is one the most powerful and fundamental languages commonly used to computer programming. If you've ever wanted to get started using, then please watch this video series. It's 29 parts will teach you everything you need to know about coding in this magnificent language, allowing you to create your own fairly full-featured computer programs. Honestly, if you have any questions about C++ at all, or want to learn it and don't think that you can because you've tried programming before and fai...

While Magic Leap World gets its share of fun apps for playing with Porgs, watching TV, and exploring the ocean's depths, developers are making a strong business case for the Magic Leap One as well.

There may be a time when you want to run a program for 24 hours straight. If that app happens to quit unexpectedly, you have some options to get it going again without having to manually reopen it. Check out this video on how to restart a crashed program automatically on Windows. You need WatchDOG.
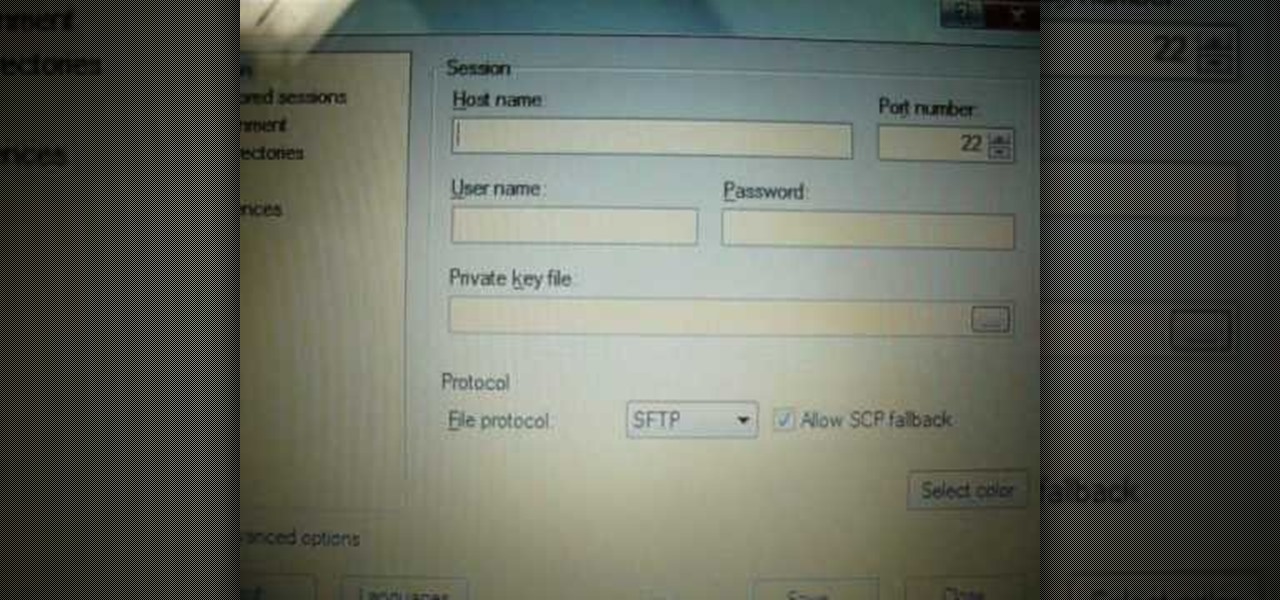
iPodTouchedMaster shows how one can easily SSH into their iPod Touch with all firmware! To SSH is the ability to hack into your iPod Touch's file system. First, your iPod Touch must be jailbroken. Next, you'll have to open Cydia. Click "Featured Packages" or search for the terms "Open SSH" (it will be listed under Console Utilities & Daemons). When you have OpenSSH click on it and click 'Install' and 'Confirm'. After this is finished, click return to 'Cydia'. This may take a lot of battery po...

Watch this video tutorial to learn how to calculate your carbon footprint. A carbon footprint is an equation that estimates just how much you, personally, are contributing to global warming—and all you have to do is plug some info into an online calculator. Figuring out how to make your footprint smaller, of course, is another matter.

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.

This educational safety video is geared toward public and private utility workers and linemen who need to remove pole tops while dealing with high-voltage electrical cables and electrical insulators. It discusses the proper pole topping removal procedure and demonstrates effective procedures for removal.

Steve with Eikenhout Educational Video Series and Paul Griggs with PGriggs Construction demonstrate how to install new windows during a new construction application. You will need a level, a utility knife, a caulk gun and a hammer to install the windows. First, cut the house wrap away from the area where the window will be placed. Next, properly flash the opening to protect it from water by starting at the window sill. Next, verify that the sill is level. Next, caulk around the window opening...

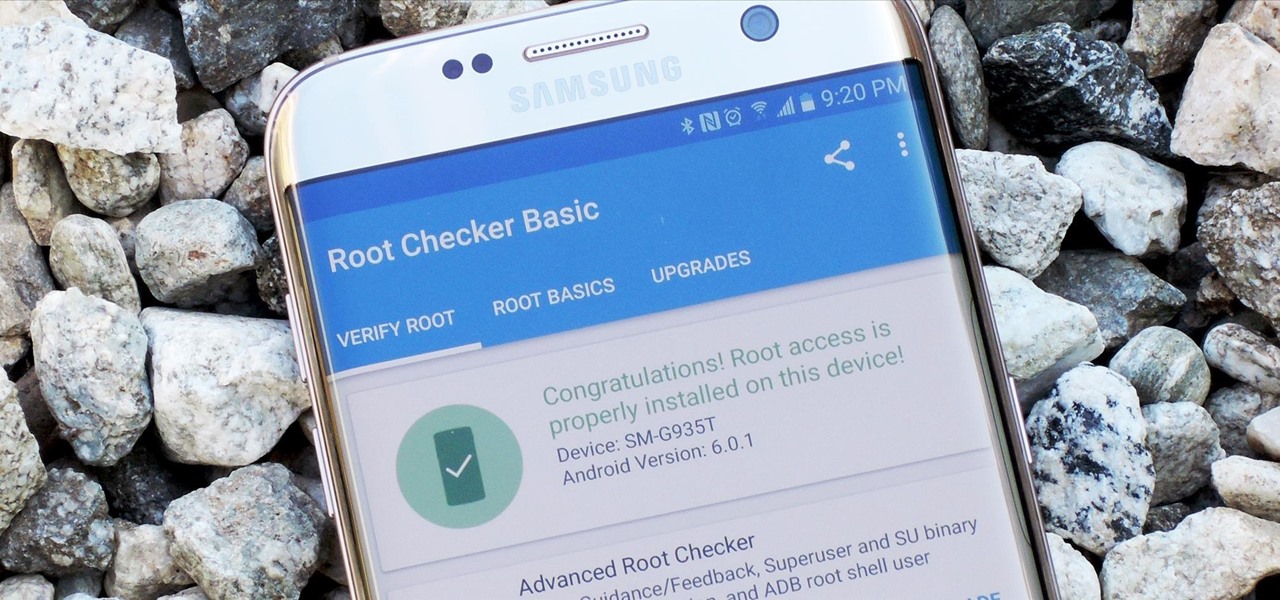
Samsung's 2016 flagship devices are some of the most beautiful, powerful smartphones ever made. And amazingly enough, thanks to legendary root developer Chainfire, the Samsung Galaxy S7 and Galaxy S7 edge are about to get even more powerful.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

Let's get one thing straight: CyanogenMod is one hell of a ROM. They've got a great community, a great product, and getting it on your HTC One couldn't be easier with their CyanogenMod installer, which does all the hard rooting and bootloader unlocking for you.

Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be.

The SAW lead is the most recognizable sound in hardstyle and hardcore electronic music, sounding like a swarm of bees attacking with the precision of an honor guard. Watch this video to learn how to program a patch for a SAW (or sawtooth) lead on a MicroKorg.

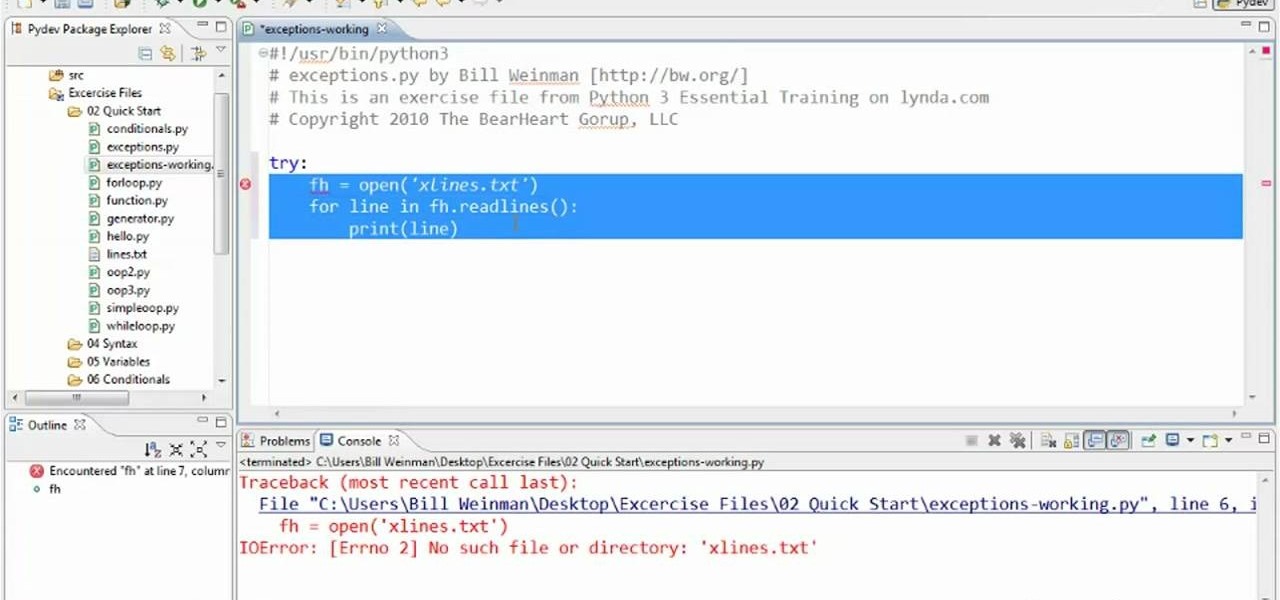
In this clip, learn how to use exceptions to handle errors when programming in Python 3. Whether you're new to the Python Software Foundation's popular general purpose programming language or a seasoned developer looking to better acquaint yourself with the new features and functions of Python 3.0, you're sure to benefit from this free video programming lesson. For more information, including detailed, step-by-step instructions, watch this video guide.

Object-oriented programming (OOP)is a school of programming that considers a computer program a group of interacting objects rather than a sequence of tasks. This makes more sense to many people than the more more old-fashioned vector model, and if you want to get started in programming, then this video is for you. It will teach you all of the basics of OOP and tell you why you should use it.

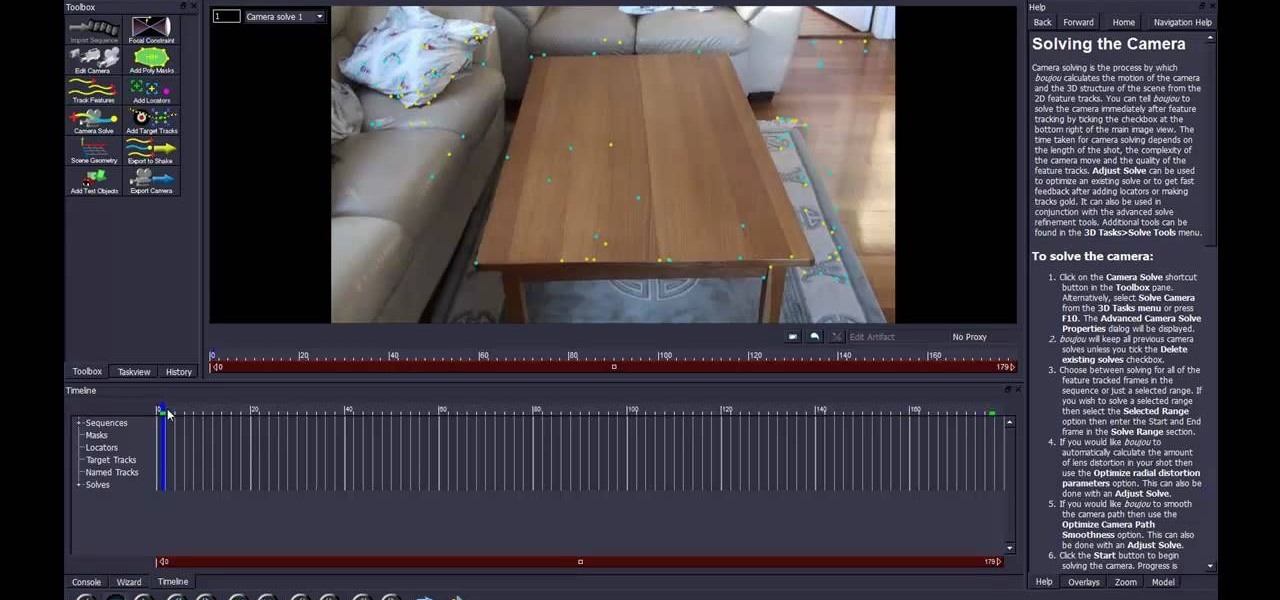
Most of the 3D modeling tutorial videos out there work within one program or at most two, often Photoshop in conjunction with a 3D modeling program like Maya. This video will walk you through a complete project using four program: 3DS MAX for modeling, Boujou for 3D tracking, Photoshop for texture editing, and finally After Effects for compositing. If you have all of those programs and want to create a seriously good-looking image, look no further.

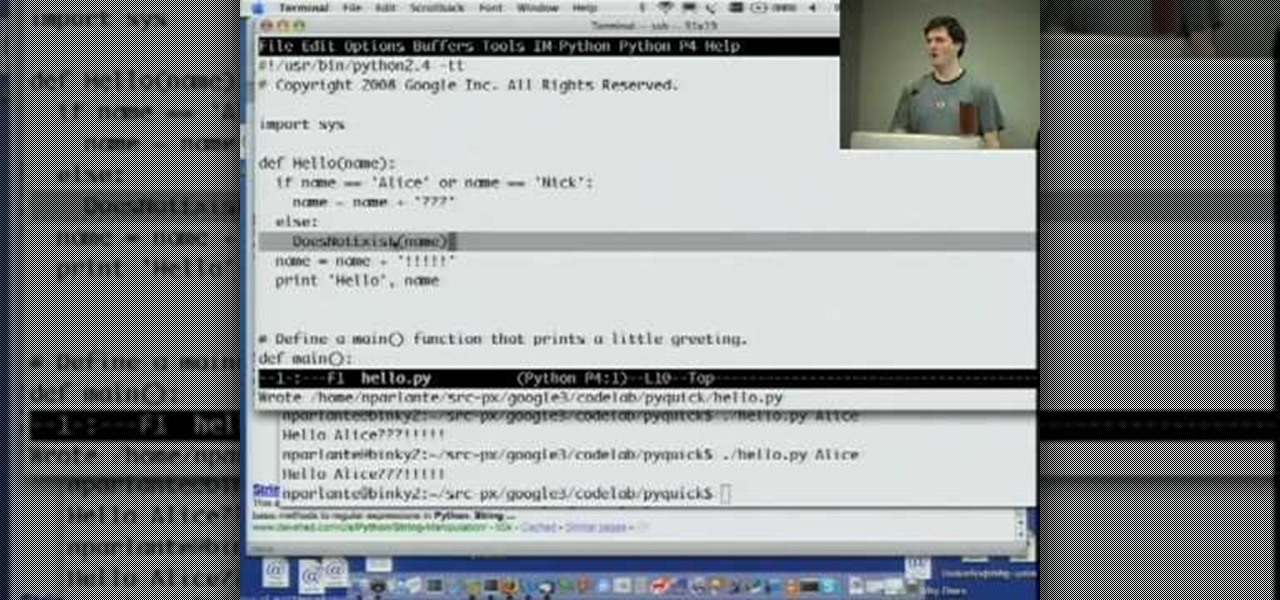
Welcome to Google's Python Class – a seven-segment, two-part free virtual class for people with a little bit of programming experience who want to learn Python. The class includes written materials, lecture videos, and lots of code exercises to practice Python coding. The first exercises work on basic Python concepts like strings and lists, building up to the later exercises which are full programs dealing with text files, processes, and http connections. The class is geared for people who ha...

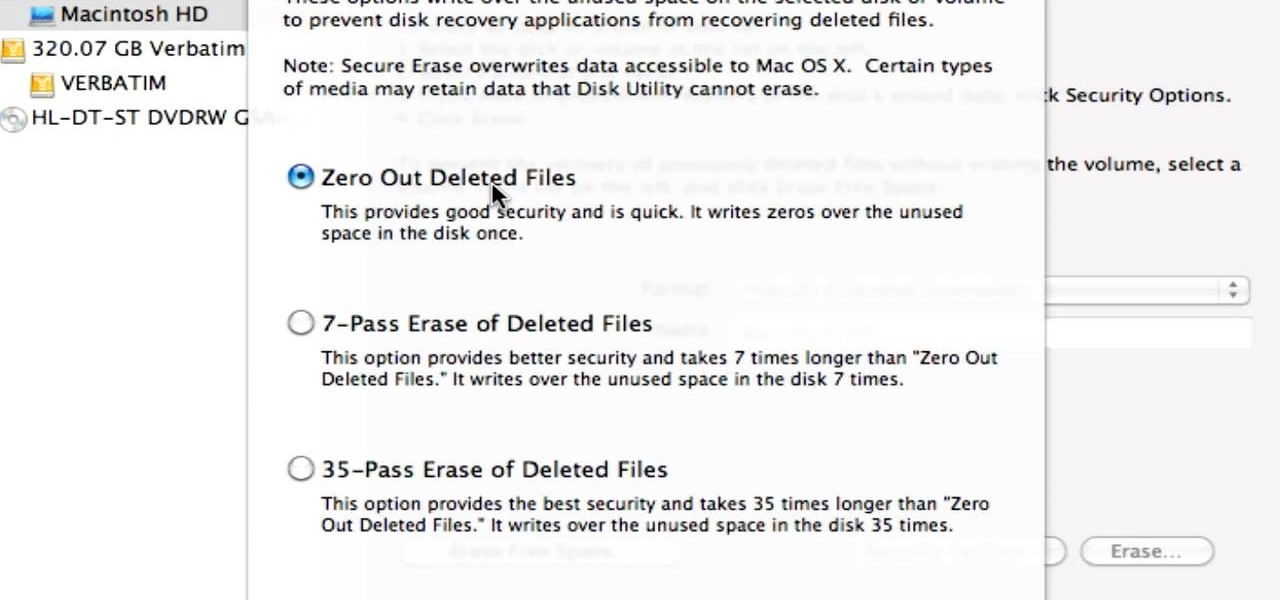
Did you know that even after you've emptied your Mac's trash can, the data still has not been permanently removed from your system? Anyone who knew where to look could easily unearth this data. You can prevent this by using the secure empty trash option on your Mac. Whenever you put something in the trash, instead of pressing delete, go into 'finder' up top and press 'secure empty trash'. What this will do is replace the data that is left behind on your hard drive with random ones and zeros. ...

In the age of digital cameras and instant gratification, make the simplest camera ever invented using just a light proof box, a hole, and paper. Check out this Howcast video tutorial on how to make a pinhole camera.

In this video tutorial, Wess does some research and builds a steady-cam for under fourteen bucks. Hooray for no more motion sickness!

In this video tutorial, Chris Pels shows how to use the ASP.NET IIS Registration Tool to configure ASP.NET. First, see how file extensions are mapped to ASP.NET in the IIS Manager on a global and web-site-by-web site basis. These script maps provide the basis for configuring individual ASP.NET applications to run under a specific version of the .NET Framework. Next, see how aspnet_regiis.exe, the IIS Registration Tool command line utility, is specific to each version of the .NET Framework and...

If you've ever had a little trouble trying to program your calculator, you may find a little relief with this four-part video tutorial. Here, a Texas Instruments (TI-84 Plus) calculator will be used to explain the programming process. The four parts include:

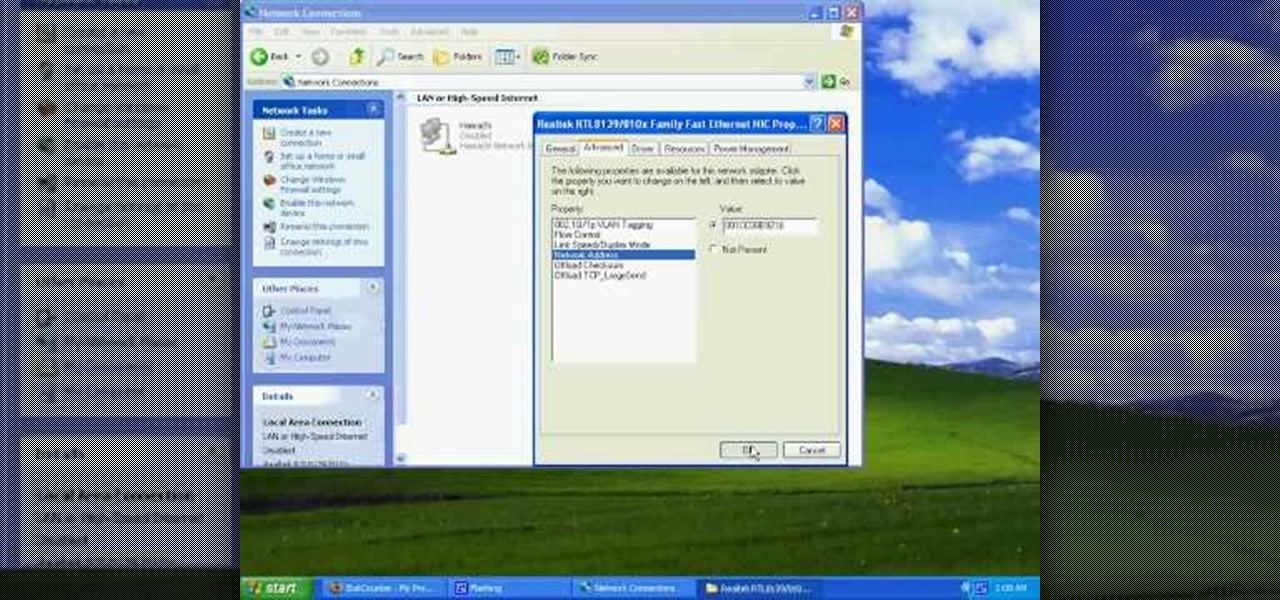
This video tutorial from tarunkumarsinghal shows how to change Mac address on Windows XP. Click Start menu and then Control Panel. Make sure control panel window is in classic view mode. If not, change it to classic from the left pane.

This video tutorial from bobby93macboy shows how to install Mac OS Leopard operating system and make it bootable.

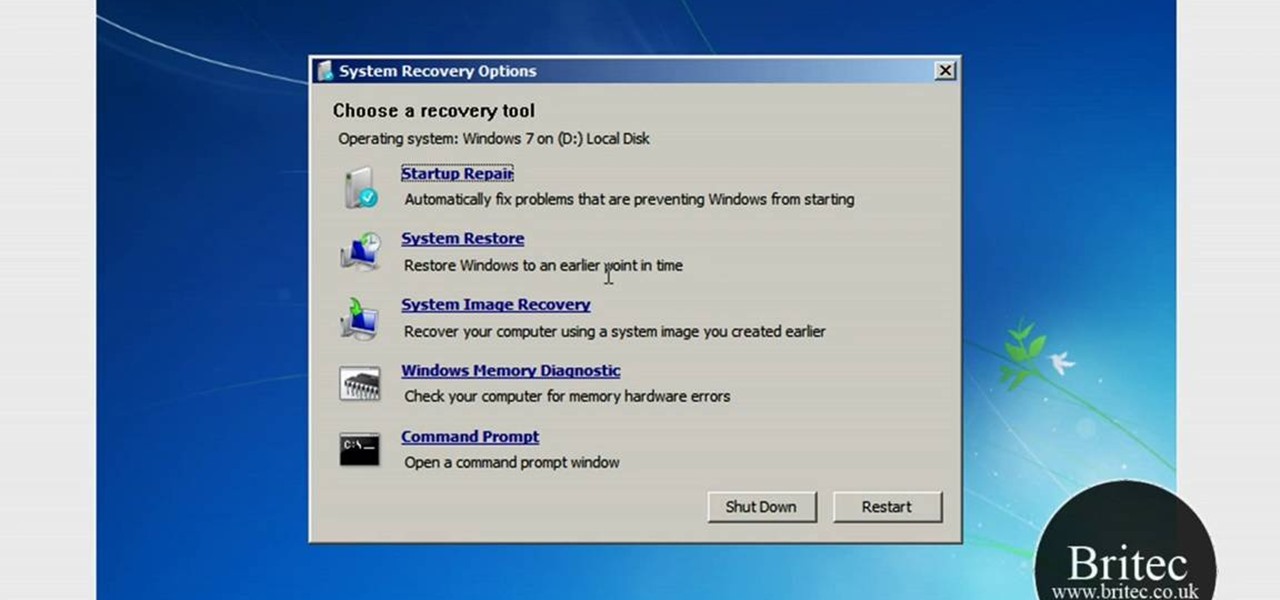
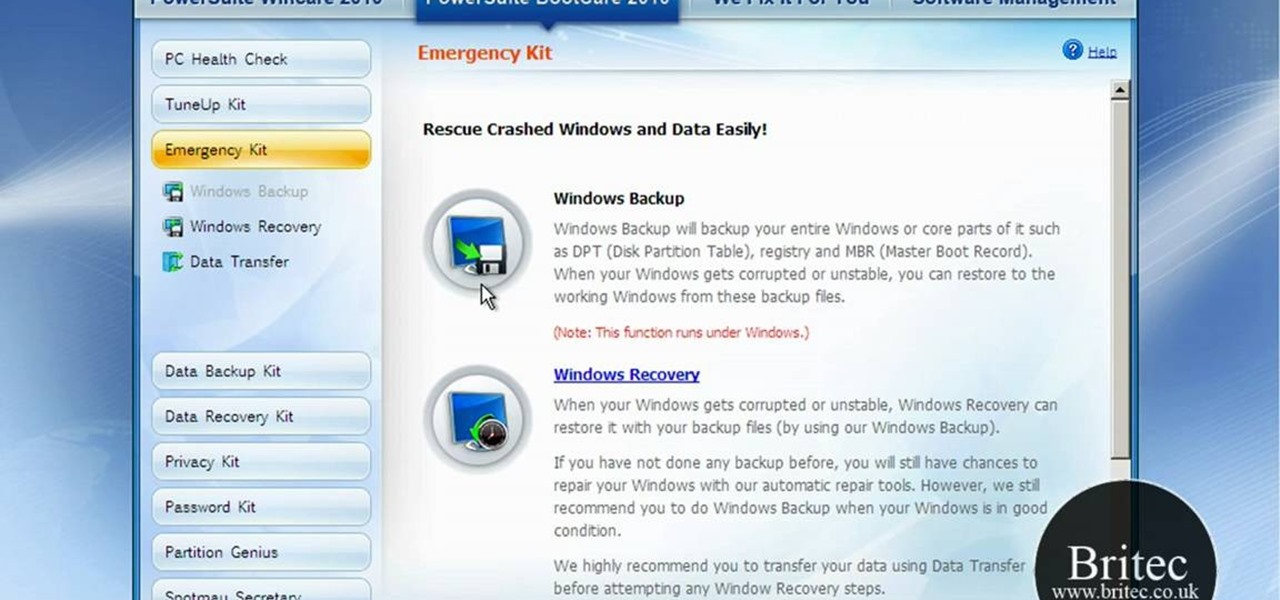
This video tutorial from Britec09 presents how to backup and restore Window 7 registry.First, press Start button and enter regedit command into Start Search area.Registry editor window will open, click File-Export.This option works on all Windows operating systems.Type file name - registrybackup and click Save. You can save it wherever you want, but in this video it was saved to Desktop.Next step is to reboot to Windows DVD. Insert you Windows DVD and reboot computer.Press any key to boot fro...

Video demonstrates tutorial of how to hide the logical drive icons in Windows. In the demonstration there is two partitions C and D and also there is a DVD drive, DVD Rom and DVD Writer. Here drives C, D and F from My computer is going to be hidden with help of utility called “No Drives Manager”. If you don’t want your young ones to access some of your important data you can hide it. It will just be hidden. This means if go to the address bar and types the name of the drive you can go to that...

If you've received the "hal.dll is missing or corrupt" error message from your Windows machine, then you're in luck! This video will show you how to correct that problem with the Recovery Console tool that comes with the Windows 2000 and XP CDs.

To remove a fiberglass shower pan you will want to start by removing excess water in the drainpipe. Take a turkey baster and put it down in the drainpipe to siphon out the water. Use a knife and cut along the edge of the fiberglass panel where it meets the linoleum. Put a rag in the drainpipe to keep any sewer gas from coming up. Next you want to drill the rubber flange material that is around the drainpipe out so that you loosen it up and allow the fiberglass pan to come loose from the drain...

Cut out the old caulk with a utility knife. Trim along the sink where the old caulk was located. Scrape out stubborn caulk with a putty knife or a paint scraper.

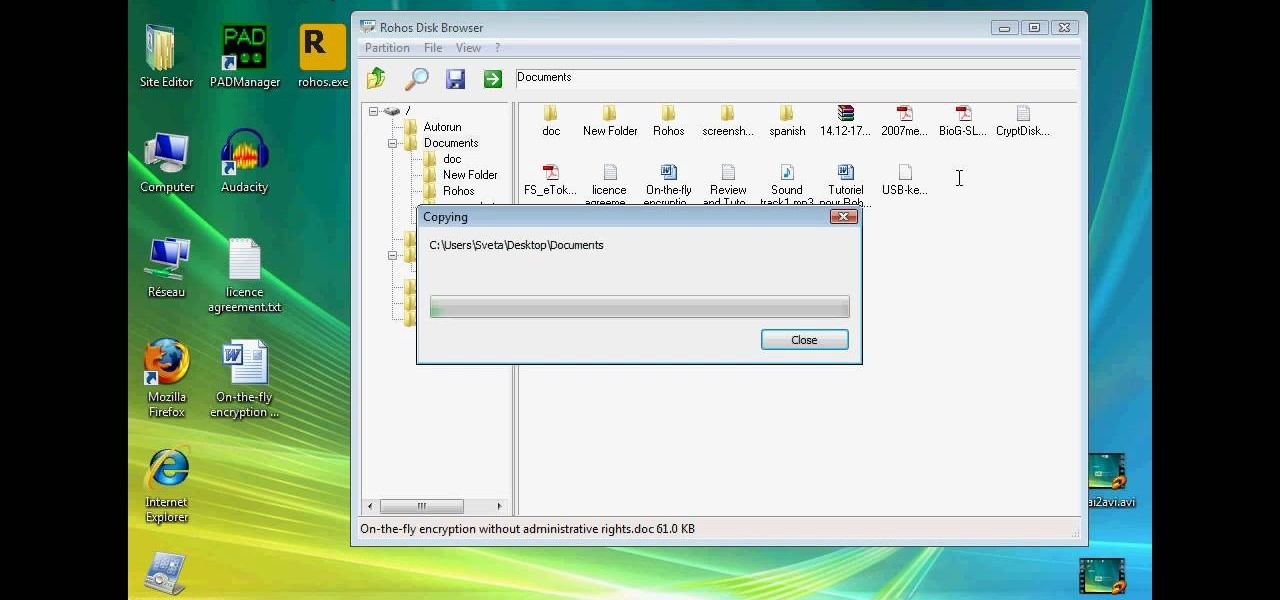
This technical video will show you all about the Rohos Mini Drive. See how you may work with an encrypted partition on a PC without admin rights using this free portable encryption solution. It securely protects your portable data on any USB device. Portable utility Rohos Disk Browser gives you opportunity to work with your sensitive data on a USB drive in the usual way on any PC (even at an internet cafe, where you don’t have admin rights).

If you've ever eaten a thinly sliced vegatable, there's a good chance that it was cut using a mandoline slicer! Learn how to use this utility effectively.

While drywall is an inexpensive building material, it's not the sturdiest. Luckily, repairing the inevitable holes is a quick and easy process.

Breaking a lease is almost always considered a legal breach of contract, even if a tenant has a good excuse. Here are some exceptions to the rule

Preserving the environment is not only the right thing to do—it can result in significant cost savings for your business.

Spread the word: It's easy to reduce energy consumption! By sharing these tips, you'll help friends and family use less energy and save money.

Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they a...

Augmented reality productivity software maker Upskill has expanded the reach of its Skylight platform with support for Microsoft HoloLens.

While Vuzix is beefing up the processing power of its next-generation smartglasses with the Qualcomm Snapdragon XR1, the company will also give its devices an upgraded display engine.

Although retailers like Mac Cosmetics and Zara have been celebrated for deploying innovative in-store augmented reality experiences in their brick-and-mortar locations, a new report throws cold water on the practice.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.